Threats abound, but people are out there trying to deal with them. Organizations continue to fall behind, finding it increasingly difficult to identify and respond to threats in a timely manner. Security Megatrends 2019, a SentinelOne commissioned report, delves into several areas of concern today including cloud security issues, SecOps frustrations and tools, the Internet of Things, data sharing and leakage, DDoS, endpoint security, and artificial intelligence.
Here’s some of the challenges and perceptions that enterprises, midmarket companies, and SMBs are facing as we move into 2019.

Budgets
On the whole, IT budgets have been on the increase, but manufacturing and healthcare/pharma/medical are significantly below average, with budgets in these two verticals around half the average.
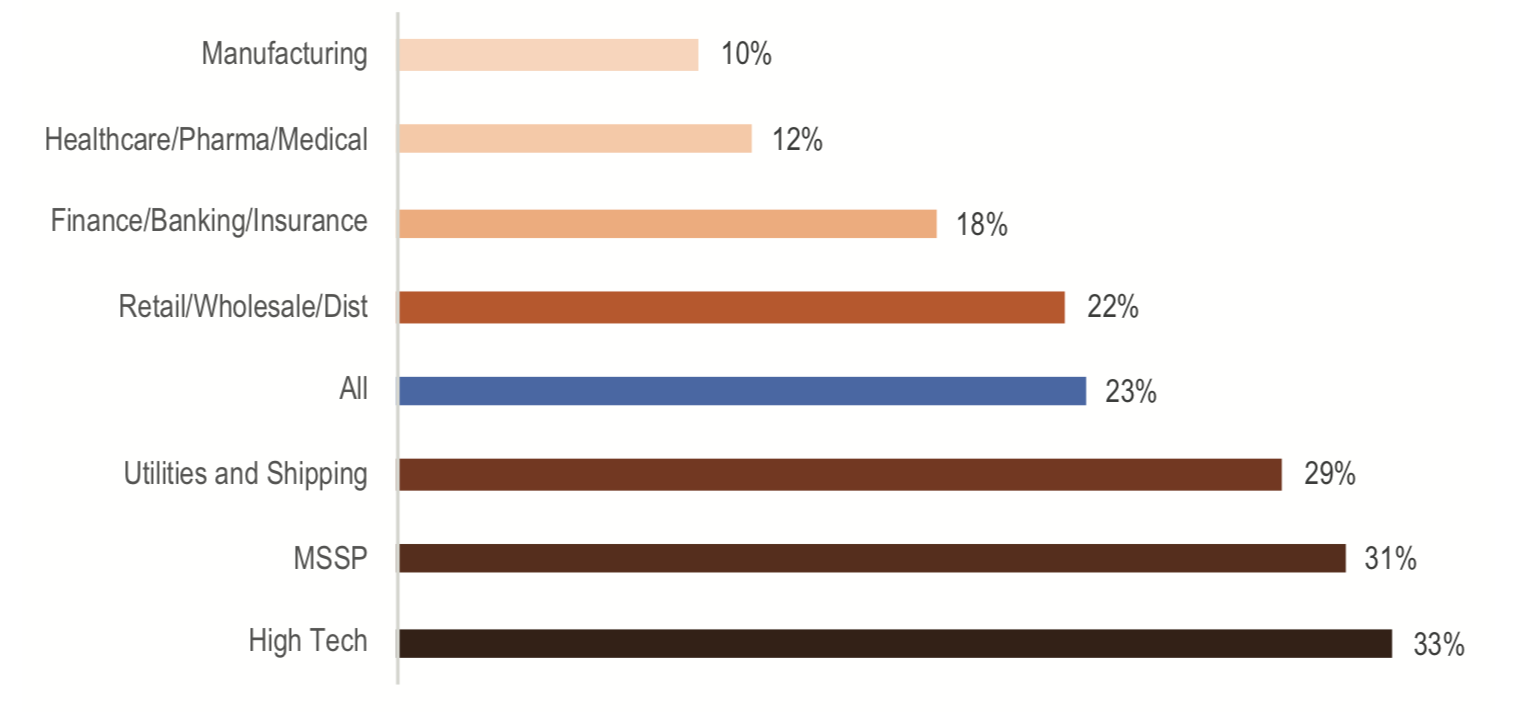
The issue with manufacturing and healthcare/pharma/medical is a significant one. Those verticals have consistently lagged in IT and security, and now hackers target them. Personal health records (PHR) are the most sought-after records. They continue to drive the highest price on the black market because they can be used for the broadest range of theft from opening new credit accounts, to purchases, and even full identity theft. Manufacturing is a target due to the rise in industrialization in developing countries. The theft of cutting-edge manufacturing techniques is huge business, especially for competing companies in places like China and India.
SecOps Frustrations
One of the key areas of frustration among security professionals is alert fatigue. Alert fatigue stems from the large volume of alerts presented to analysts that they are required to validate, identifying whether they are really high severity or at the other extreme—if they are false positives that are really nothing to worry about. In many environments, there is highly insufficient context for the systems to properly judge the criticality, so over 95 percent of the tickets that come in are classified as the highest priority.
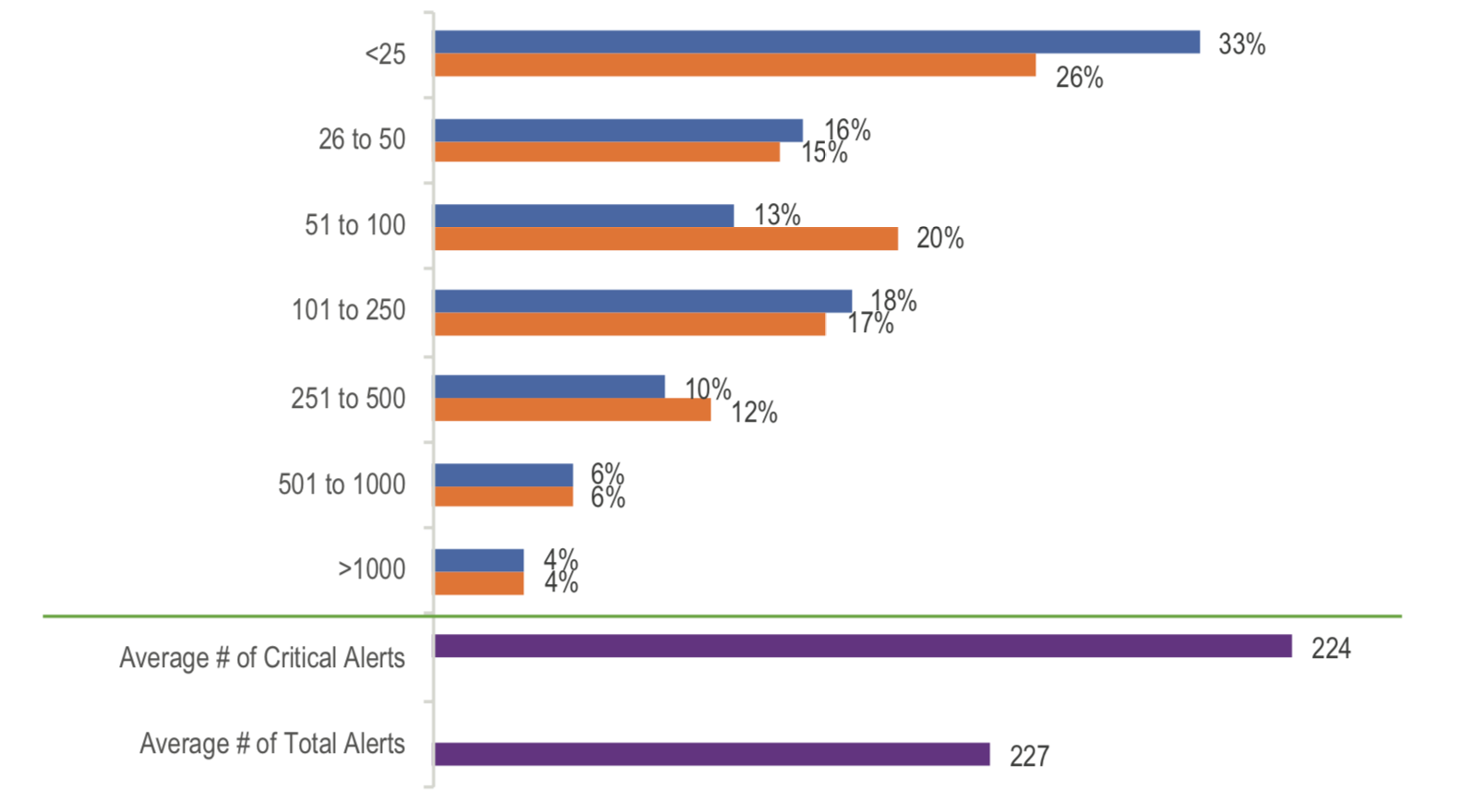
A major area of frustration covered in this report is inter-team handoffs. Seventy-six percent of respondents identified some level of impediment when trying to resolve an incident requiring inter-team handoffs or support.
When trying to investigate and resolve an incident, security analysts are often required to engage members of other teams for one or more phases of the incident prior to closing. These frustrations are encountered at some level daily, which leads to job dissatisfaction. After enough frustration, personnel leave.
Consolidation and Integration
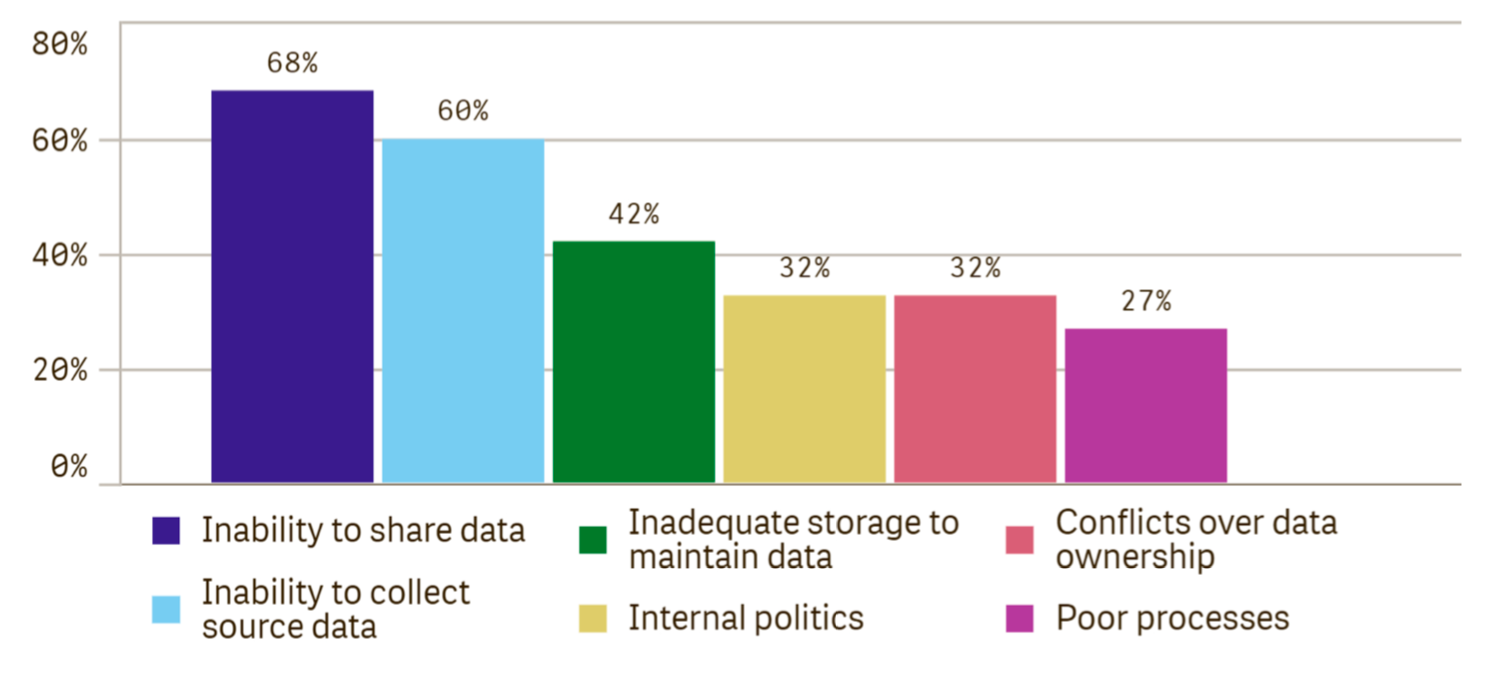
There are over 1,400 different vendors that supply cyber security tools, and SecOps typically have between 10 and 22 management interfaces to get the security job done. As a result, SecOps teams are actively trying to reduce the number of interfaces they deal with. When queried about the most important security management features to meet their business requirements, the majority of respondents said that integration with other IT management products was first order
Endpoint Protection
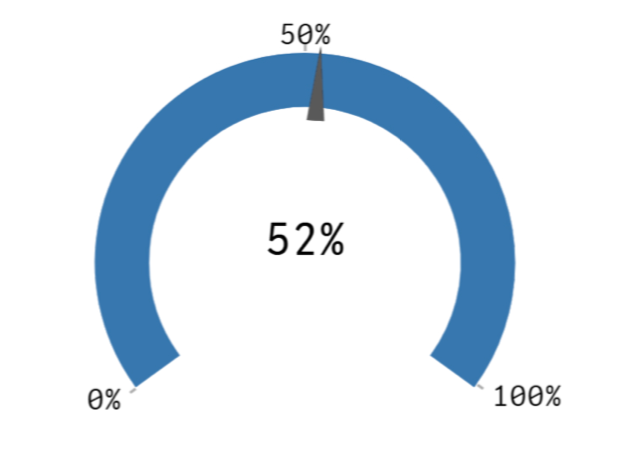
The battle for the endpoint is raging. Across antivirus, detection, prevention, and all combinations thereof, there are approximately 50 companies operating in the endpoint defense space. Seventy-three percent of respondents have been affected by some form of endpoint attack, and only 58 percent of organizations are highly confident they could detect an important security incident before it caused significant impact.
Among the salient points indicated in the endpoint research were these:
- Ninety percent of respondents that experienced an attack causing significant to severe impact believed an advanced endpoint solution would have performed better than traditional AV.
- Moreover, all of the respondents who experienced severe impacts from a malware attack indicated they now intend to replace their traditional AV product with an advanced endpoint solution.
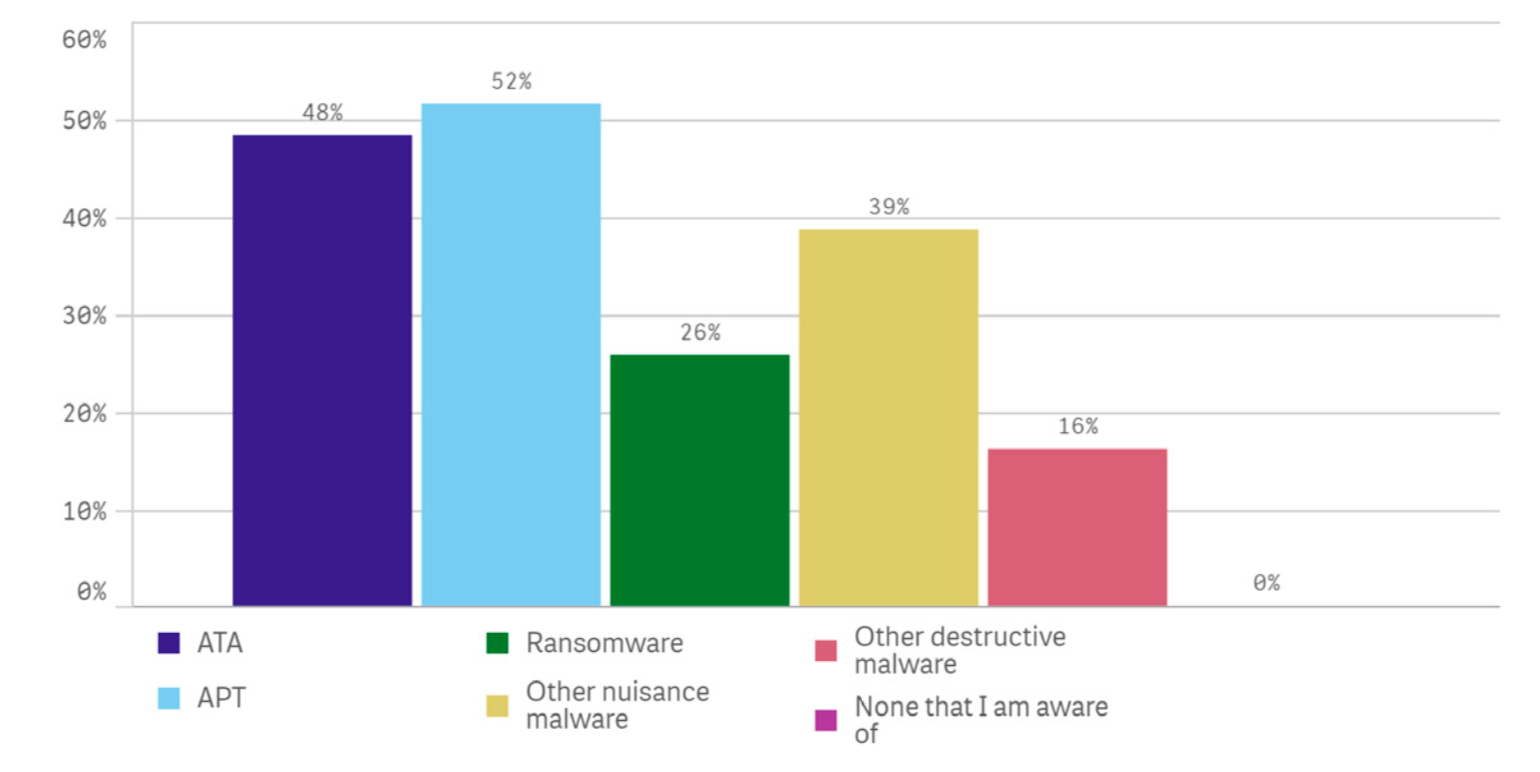
Conclusion
Security Megatrends 2019 is a comprehensive SentinelOne-sponsored report covering security issues and challenges facing organizations of all sizes and industry verticals today. The report looks across SMBs, midmarkets, and enterprises as well as multiple industry verticals to understand the commonalities and divergence in trends. Ultimately, the report will help readers understand how to handle threats better, no matter where they stand now.


