The Good
Thankfully, law enforcement is giving cybercriminals plenty to reflect on again this week with more arrests in the Ukraine. Five members of the so-called “Phoenix” hacking group, living in Kharkiv and Kyiv, were arrested by the SSU (Security Service of Ukraine), which continues to do great work harvesting bad guys.
The Phoenix operation specialized in acquiring remote access to accounts of mobile device users and stealing credentials for their e-payment or bank accounts. The criminals would then sell obtained data and account details to interested buyers. The group employed tried-and-tested phishing templates to lure device users into giving up their credentials. Fake Apple and Samsung login portals are a common example of said lure. In addition, the arrested individuals also reportedly contracted out their hacking services to other parties for as little as $100 to $200 a time.
The five individuals will be subject to charges under Article 361 of the Criminal Code of Ukraine.

These arrests are just the latest in a series of law enforcement actions against cybercriminals in the Ukraine. The country has been cracking down on ransomware, money laundering and DDoS attacks recently, and long may it continue!
The Bad
Earlier this week, users of Microsoft Defender for Endpoint got an unfortunate surprise. Following the installation of recently released security updates from Microsoft (KB5007206 and KB5007205), some systems were left with a non-functional install of Microsoft Defender on Windows Server Core, finding that after the patch was installed, Microsoft Defender services failed to startup, potentially leaving machines at risk.
At the time of writing, there is no official fix or workaround for this issue, should you encounter it. That said, Microsoft has been quoted as stating “We are working on a resolution and will provide an update in an upcoming release”.
Meanwhile, a novel malware has been discovered that embeds its payload in crontabs, thus earning itself the moniker “CronRAT”. The RAT (Remote Access Trojan) is specific to Linux and is engineered to detect and skim credit card data from relevant payment servers.
According to researchers, this RAT makes use of crontabs with dates that will never execute to hide and obfuscate malicious code. The payloads are further obfuscated via base64. Once reconstructed, the payload is able to execute the code generated from the specially-crafted task names, then contacts the C2 and runs additional commands.
Once active, the RAT essentially allows full control of the host. The SentinelOne platform is capable of detecting and preventing malicious behaviors associated with CronRAT.
The Ugly
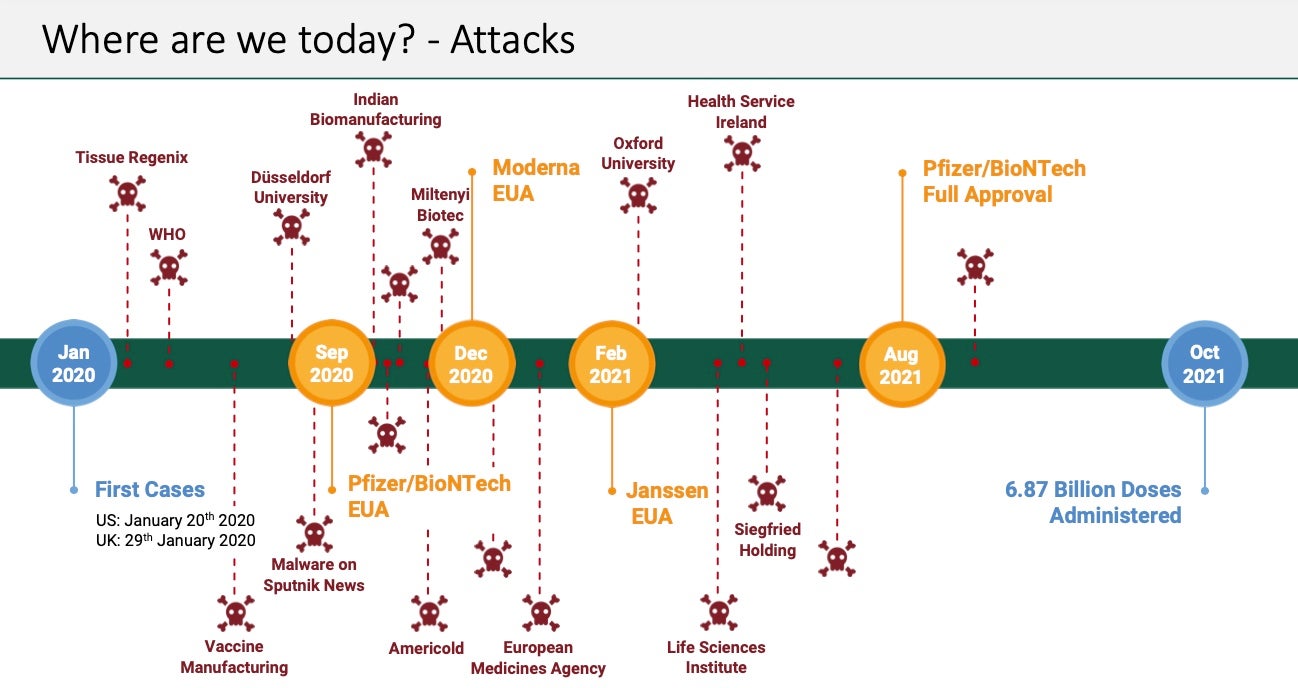
High-value bio-manufacturing targets are at the heart of this week’s ugly story. Reports of a new malware dubbed “Tardigrade” have emerged, which appears to be part of active campaigns hitting bioeconomy facilities.
According to reports from BIO-ISAC, one incident involving Tardigrade occurred in the Spring of 2021 and another in October 2021. The targeted facilities were not named. Attributed to an unknown APT actor, these attacks are just the latest targeting the bioecomomy. The researchers say that attacks are ongoing and that they disclosed details of the campaign to help the industry protect itself.
The Tardigrade malware loader (similar in some ways to Smoke Loader) was used to distribute and launch ransomware within the target environment. The Tardigrade loader allowed the attackers to establish access and move laterally as needed. The malware communicates with its C2 via encrypted channels and can automatically spread to adjacent network resources. When environments are targeted with Tardigrade, any destructive payload can be employed very rapidly. Phishing is the main vector for attack, with some indication that USB devices may be employed for physical penetration of air gapped systems.
BIO-ISAC has released recommendations which include phishing awareness training, reviewing network segmentation, testing of offline backups, and using behavioral detection. The researchers point out that “While many malware systems are polymorphic, this system seems to be able to recompile the loader from memory without leaving a consistent signature”.
The SentinelOne platform detects and prevents behaviors and artifacts associated with the Tardigrade malware.