The Good | Authorities Dismantle XSS.is Cybercrime Forum & Release Free Phobos/8Base Decryptor
After a 12-year long run, XSS[.]is (formerly DaMaGeLaB) faced major disruptions this week with the arrest of its suspected administrator as part of a joint operation led by French and Ukrainian authorities. The Russian-speaking cybercrime forum had been active since 2013 with nearly 50,000 users and acted as a popular hub for stolen data, hacking tools, and ransomware services. Authorities also seized its clearnet domain.

The suspected administrator, also linked to the private messaging site thesecure[.]biz, is believed to have earned over €7 million from advertising and facilitating criminal transactions. Europol reports that the admin had been active in the cybercrime scene for nearly 20 years, maintaining their ties to prominent cybercriminal groups over the decades. XSS[.]is also featured an escrow system and encrypted communications, reinforcing its reputation as a key platform for non-Russian-targeted cyberattacks alongside other forums like Exploit.
Japanese police have released a free decryptor for Phobos and 8Base ransomware victims, allowing those affected to recover their encrypted files. Phobos, active since 2018, operated as a ransomware-as-a-service (RaaS) platform while 8Base launched in 2023 using modified encryptors with double extortion tactics. A major international crackdown on Phobos last year led to the arrest of key members and the seizure of 27 servers, enabling creation of the decryptor.
The decryptor is available on the Japanese police’s website with instructions in English and on Europol’s NoMoreRansom portal. It supports extensions like .phobos, .8base, .elbie, .faust, and .LIZARD, but law enforcement say that it may also work with others. Users are encouraged to test it, as it may decrypt additional variants.
The Bad | Lumma MaaS Rebuilds Operations After Takedown, Evading Detection with New Tactics
After major law enforcement action taken back in May, Lumma infostealer operations are steadily regaining momentum despite disruptions to its infrastructure. Although the takedown significantly impacted the malware-as-a-service (MaaS) platform, Lumma never fully shut down. Its operators quickly addressed the disruption on cybercrime forums, asserting that their central server had not been seized (though it was remotely wiped) and that restoration was already underway.
To date, security researchers note that Lumma is nearly back to pre-takedown levels, with telemetry data confirming a rapid rebuilding of its infrastructure. Latest updates to this second wind include a shift from Cloudflare to Russian-based provider Selectel, presumably to evade future takedowns. However, the MaaS continues to use legitimate cloud infrastructure to disguise malicious activity.
Lumma has resumed their operations through four main channels. First, fake software cracks and key generators are being promoted via malvertising, leading users to deceptive sites that fingerprint devices using Traffic Detection Systems (TDS). Using ClickFix, Lumma is using compromised websites that now display fake CAPTCHA pages to trick visitors into executing PowerShell commands, which inject Lumma directly into system memory to avoid file-based detection.
Another distribution method involves Lumma attackers setting up GitHub repositories filled with AI-generated content advertising fake game cheats with the Lumma payload is hidden in executables or ZIP archives. Finally, YouTube videos and Facebook posts advertise cracked software, linking to external download sites. Some of these are hosted on trusted platforms like sites.google.com to lend credibility.
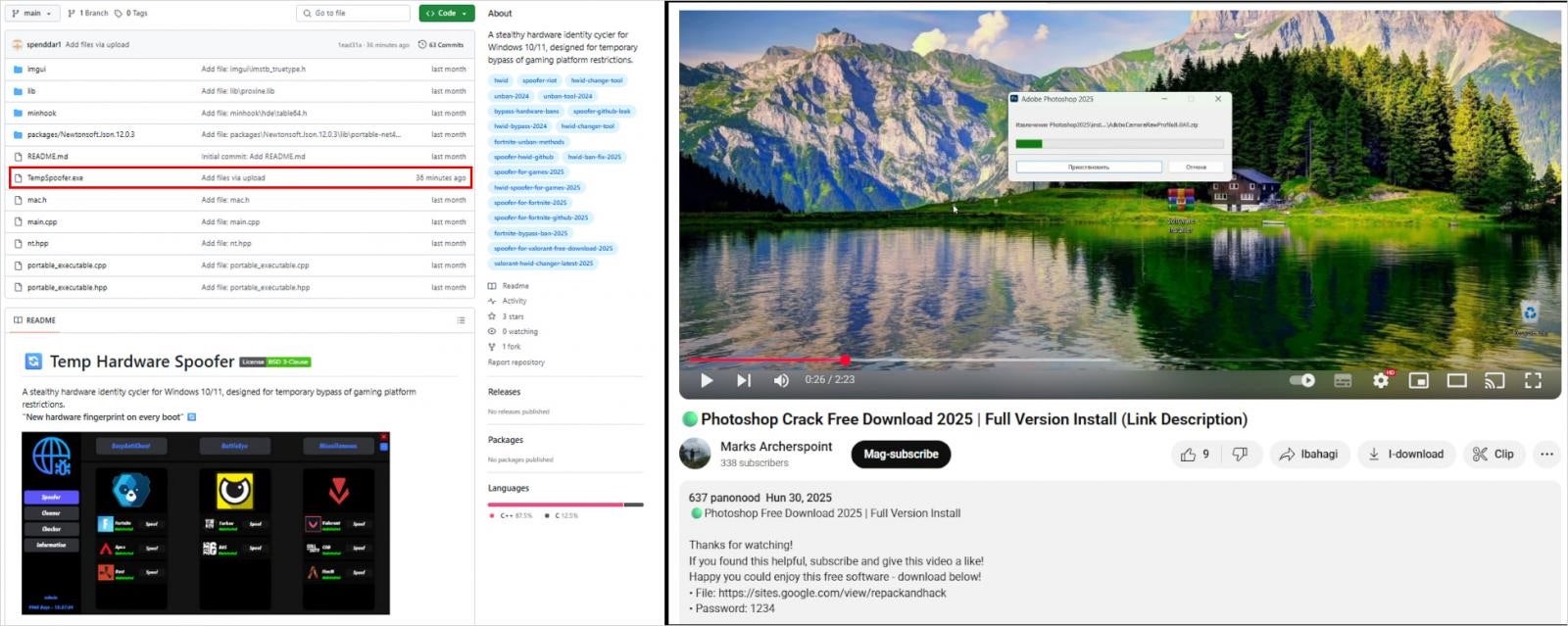
Lumma’s re-emergence reflects how infrastructure seizures alone are insufficient. Without arrests or indictments, the cyber war machine keeps turning, and threat actors will continue to treat such takedowns as temporary disruptions to an otherwise profitable enterprise.
The Ugly | CISA Orders Urgent SharePoint Patching As Microsoft Confirms ToolShell Exploits
Last weekend, Microsoft confirmed active exploitation of a zero-day vulnerability in on-premises SharePoint Servers, dubbed “ToolShell” (CVE-2025-53770), along with a bypass variant tracked as CVE-2025-53771. These flaws, along with earlier patched bugs (CVE-2025-49704/49706), form an unauthenticated RCE chain that focus on exploiting the /ToolPane.aspx URI via a crafted POST request. Emergency patches have been released for SharePoint Subscription Edition and Server 2019, with updates for 2016 pending.
While the initial wave of attacks were initially targeted, broader exploitation is expected as PoC code circulates. SentinelOne’s report on the attacks noted actors setting up honeypots and sharing tooling, signaling growing threat actor interest. Now, CISA has added the CVEs to its KEV catalog, citing confirmed exploitation, and ordered federal agencies to remediate affected systems immediately. Microsoft has since linked the ToolShell attacks to suspected China-based threat actors, including Linen Typhoon and Violet Typhoon, who began targeting on-premises SharePoint servers as early as July 7.
Update: See newly added info to our #ToolShell Alert. We’ve included info on ransomware deployment, new webshells involved in exploitation, & detection guidance 👉 https://t.co/Y37FHSeAL0 pic.twitter.com/C5aMXNOmAU
— CISA Cyber (@CISACyber) July 24, 2025
Given the severity of ToolShell, organizations are strongly advised to adopt a layered defense strategy. Key recommendations include isolating on-prem SharePoint servers from public internet access to reduce exposure, enabling Antimalware Scan Interface (AMSI) in full mode to support endpoint detection, and applying Microsoft’s latest patches without delay. Detection should also be enhanced by integrating ToolShell-specific indicators of compromise (IOCs) into EDR/XDR and SIEM systems, and deploying custom rules to monitor SharePoint directories such as `LAYOUTS`.
CISA is continuing to coordinate with Microsoft, federal agencies, and local partners to assess the full scope of impact. So far, approximately 400 organizations, including government agencies, have reportedly been compromised, pointing to the urgent need for rapid mitigation.


