The Good
User education is possibly one of the most powerful tools in the world of breach prevention or attack evasion, particularly when it comes to phishing attempts and the like. The more confident and aware users are in regard to their cyber hygiene, the better off they are generally speaking. This week GCHQ and The National Cyber Security Centre (NCSC) joined forces and established a new user-awareness campaign dubbed ‘SERS’, the Suspicious Email Reporting Service. This is part of a broader ‘Cyber Aware’ campaign to arm the public with better email security guidance in the light of a rapid increase in scams since the Coronavirus outbreak. The new service, a joint effort with the City of London Police, enables the public to directly submit suspicious and potentially malicious emails to [email protected]. When users submit messages to SERS, the validity of various aspects of the message are interrogated and validated. Domains and hosts of the sender, for example, are tested for validity and any sites found to be phishing scams will be removed immediately. In one day of operation, over 5000 reports were sent in and 83 online phishing campaigns were shut down as a result. Nice work!
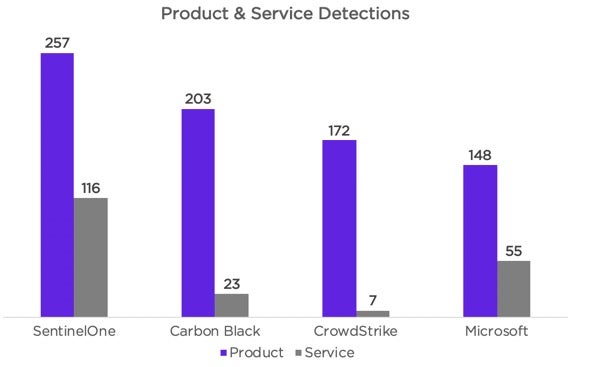
On another positive note this week, the results for the latest round of MITRE ATT&CK evaluation were released. MITRE’s focus for Round 2 was “APT29” and the tactics, techniques and procedures relevant to this notorious Russian-backed threat actor. This year we are proud to highlight SentinelOne’s leading results for the round. SentinelOne achieved the lowest number of overall missed detections, as well as reaching the highest number of combined high-quality detections with the highest levels of correlation. That being said, we applaud and congratulate all of the participants that tested alongside SentinelOne. We are all working together toward the greater good of a more secure world.
The Bad
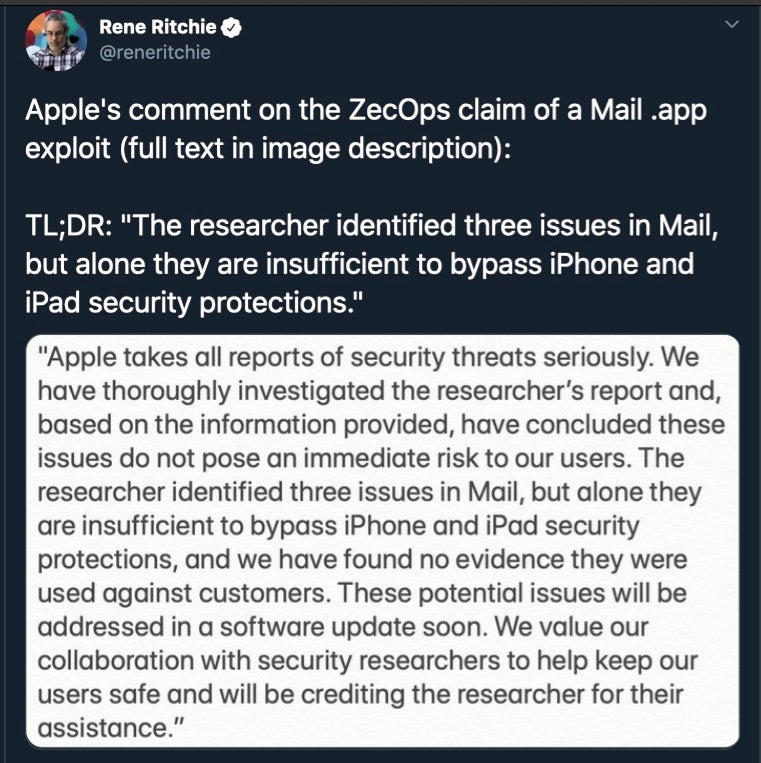
Researchers claim to have found critical vulnerabilities within Apple’s Mail app on iOS this week. The remote code-execution vulnerability appears to have been present in the OS since 2012, iOS 6 being current at the time. It is reported that the flow specifically affects iOS 6 through iOS 13.4.1. This flaw is especially critical due to the compete lack of user input. Typical email-bourne threats at least require the target to open the messages, or click a link, or even open attachments. In this case, the Mail.app need only receive a maliciously-crafted message to invoke the exploitable conditions. The flaw is due to a pair of heap-overflow and out-of-bounds write conditions that can be invoked by an attacker whilst composing the weaponized message.
The discovering party (ZecOps) also reports that they are aware of attackers attempting to exploit this vulnerability in the wild. However, Apple have contradicted that claim, stating that they “have found no evidence they were used against customers”. The issues have apparently already been addressed in a beta build of a forthcoming iOS update. Other email clients on the platform such as Chrome or Outlook are not affected and offer a potential workaround for concerned users in the meantime.
The Ugly
This week the Maze Crew (actors behind the Maze ransomware) set their sights on global MSP and consulting firm Cognizant. APT groups and highly-sophisticated cybercrime operators alike have been targeting MSPs as they are considered high-value targets. MSPs (Managed Service Providers) typically manage and host massive amounts of network environments and users. Attackers focused on MSPs potentially have the ability to disrupt the operations of all entities under the MSP’s scope or control.
![]()
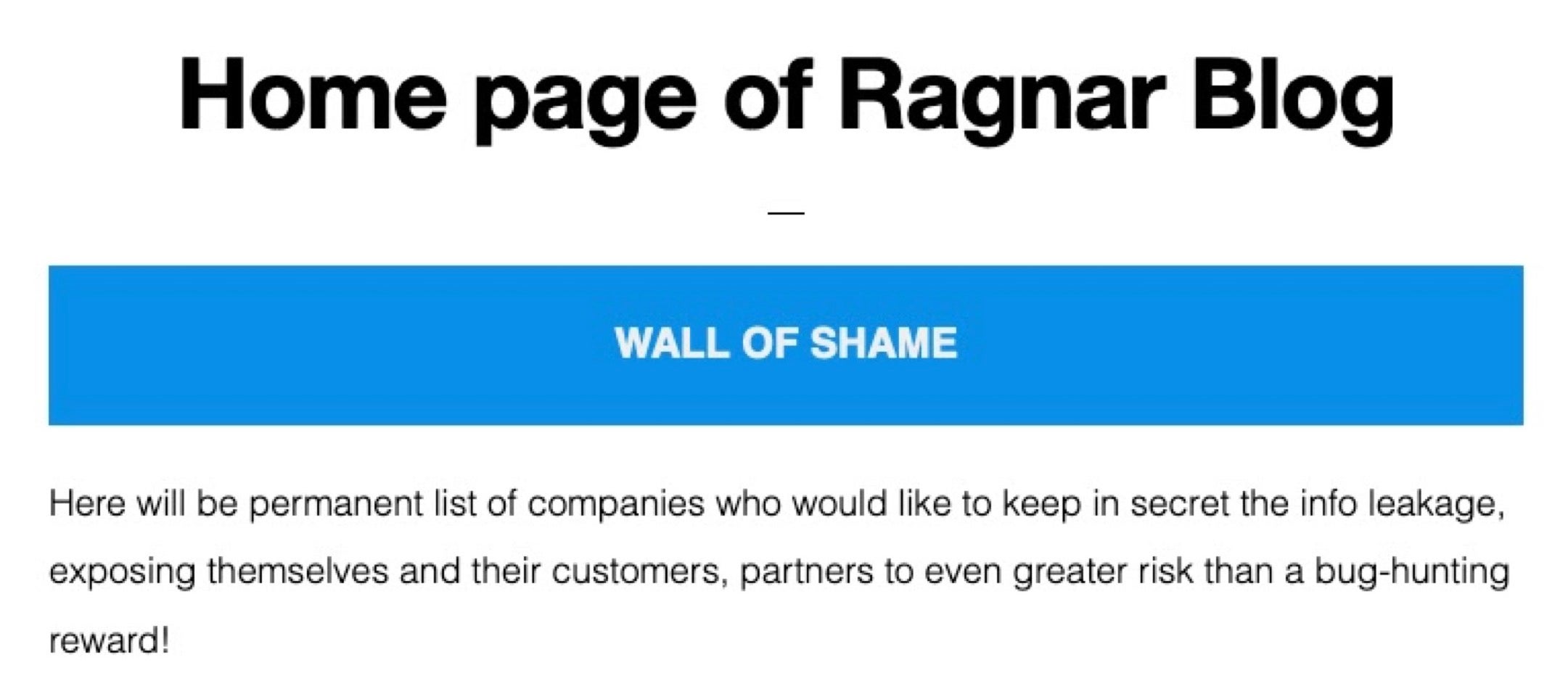
That aspect of the attack alone is cause for alarm. However, this being a Maze attack adds yet another possible consequence to the compromise. Maze, like many other malware families of late, also steals data from targeted environments. They increase impact by threatening to publicly release the data pilfered from their victims. Having to consider any modern ransomware attack as essentially a full-scale breach is a scenario that more and more enterprises are facing these days. Maze alone has publicly posted data belonging to approximately 100 of their victims. Other ransomware families like DoppelPaymer and Sodin / REvil are not far behind. More recently, families like Ragnar and Netphilim have been actively posting victim data and threats as well.
These attacks are currently on the rise, and the threat of leaking sensitive information is far from empty. Taking the time to understand your exposure, adjusting your security posture, and adopting necessary measures to mitigate risk is critical. Knowledge and powerful technological controls together go a long way to reduce our exposure to data-robbing cybercriminals.


