The Good
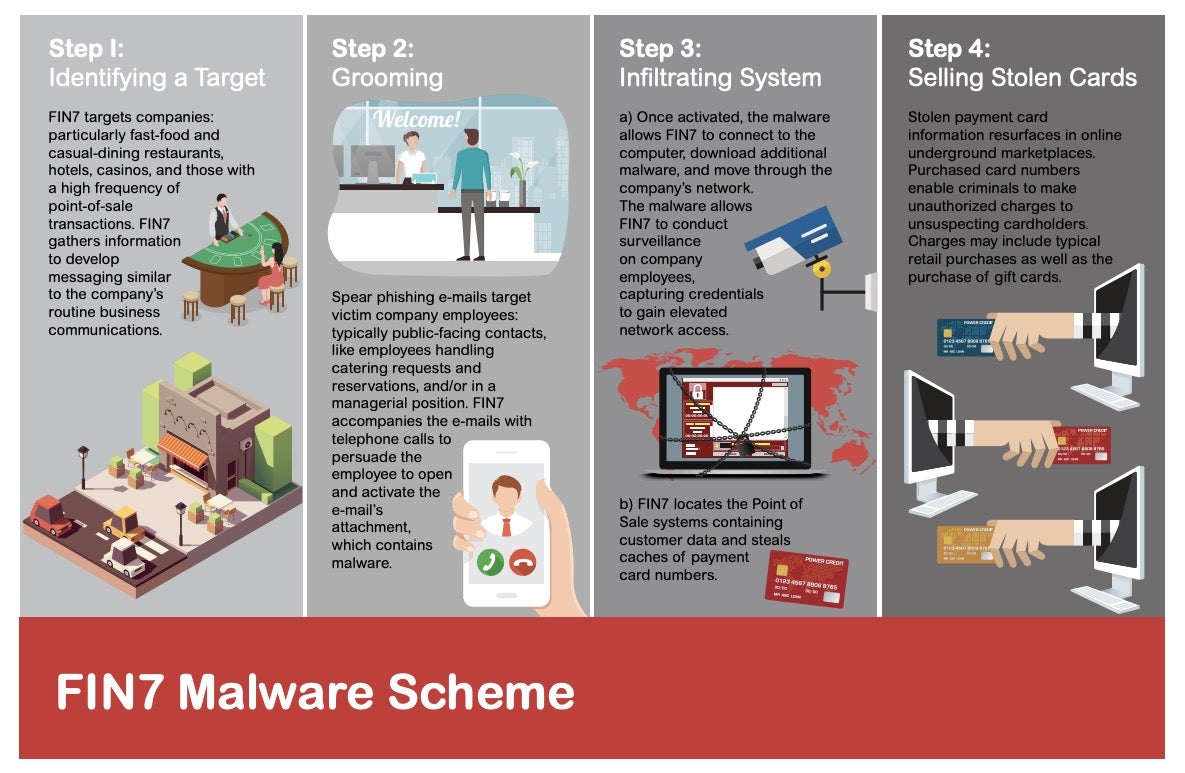
Notorious card-stealing and financial crime gang, FIN7, have had a busy time in the news this week. Former sys admin for the 70-strong gang of thieves and fraudsters, Fedir Hladyr, has been handed down a 10-year prison sentence for conspiracy to commit wire fraud and conspiracy to commit computer hacking. Prosecutors say Hladyr, a Ukrainian national, was responsible for maintaining the gang’s network of servers and controlling their encrypted communication channels. He was also involved in aggregating stolen card details and supervising other members of the criminal organization.
The gang are believed to have compromised millions of financial accounts and are said to be responsible for over a billion dollars of loss to U.S. businesses and individuals. A statement from the FBI noted that thanks to international cooperation among law enforcement agencies, “these fraudsters are not beyond our reach and cannot hide from the law”. Threat actors of all stripes take note.
Among FIN7’s arsenal of tools is a malware family known as ‘Carbanak’. According to MITRE, the same malware is used by a different group who are tracked separately to FIN7 as the Carbanak group. Because of their similarities, both were used in the latest round of MITRE Engenuity evaluations, which aim to provide independent evaluation of enterprise security products.
The results of the latest round of testing were released this week and speak for themselves (spoiler: SentinelOne was the only one of the 29 vendors evaluated that had zero missed detections and 100% visibility. But you don’t have to take our word for it, see what MITRE Engenuity had to say!). That’s good news for SentinelOne customers and good news for businesses looking for an independent evaluation of enterprise security solutions.
The Bad
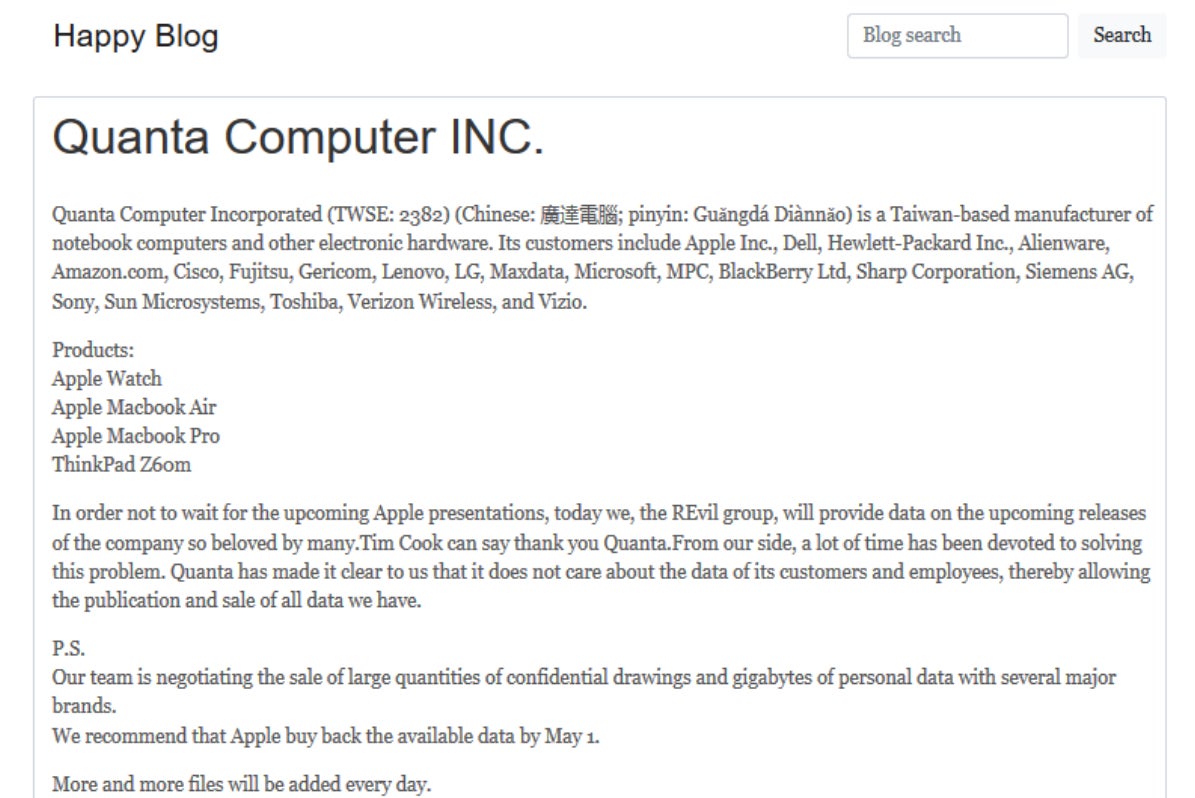
When it comes to bad news, if it’s not ransomware, it’s a supply chain attack, and sometimes it’s both. Such is the case this week with what appears to be another high-profile victim of the REvil ransomware group. The RaaS operators, or one of their affiliates, appear to have compromised Quanta, a Taiwanese-based company that manufactures products for, among others, Apple. However, their initial attempts at trying to extort the victim fell flat, so instead the crew decided to go after Apple directly.
The gang says that since Quanta did not seem to “care about the data of its customers and employees”, it would release “large quantities of confidential drawings and gigabytes of personal data”, which – it is claimed – include data of “upcoming releases” of Apple products. The threat actors have publicly given Apple until May 1st to pay an undisclosed sum to prevent the leak. Previously, the same group had demanded $50 million from laptop maker Acer, and it is believed that a similar or higher sum is being demanded of Apple.
As we’ve seen over the last 18 months or so, ransomware gangs have branched out from simple encryption to data theft and extortion of victims. This case, however, appears to be the first in which threat actors, having failed to persuade the primary target to pay, have then gone on to try and extort money directly from clients of the victim. We don’t expect it to be the last.
The Ugly
Remember SUPERNOVA (well, it’s easy to forget with so many new malware families being foisted upon us these days)? As suspected some time ago, it appears that there’s more than one APT threat actor leveraging SolarWinds Orion vulnerabilities. This week, CISA gave details regarding a second actor that has been enjoying long-term compromise of an enterprise network by exploiting vulnerabilities in SolarWinds Orion and dropping the SUPERNOVA malware to gather credentials.
What makes this particular case more worrisome than usual is the threat actor’s initial point of ingress. It appears that from around March 2020 or earlier until February 2021, the attackers used residential IP addresses in the U.S. to connect to the victim’s network via a Pulse Secure VPN appliance, masquerading as remote WFH employees. It is not known how the attacker gained the initial credentials, but it is known that they were not MFA enabled. Once logged on to the VPN instance, the attackers moved laterally to the victim’s SolarWinds Orion appliance and installed the SUPERNOVA malware.
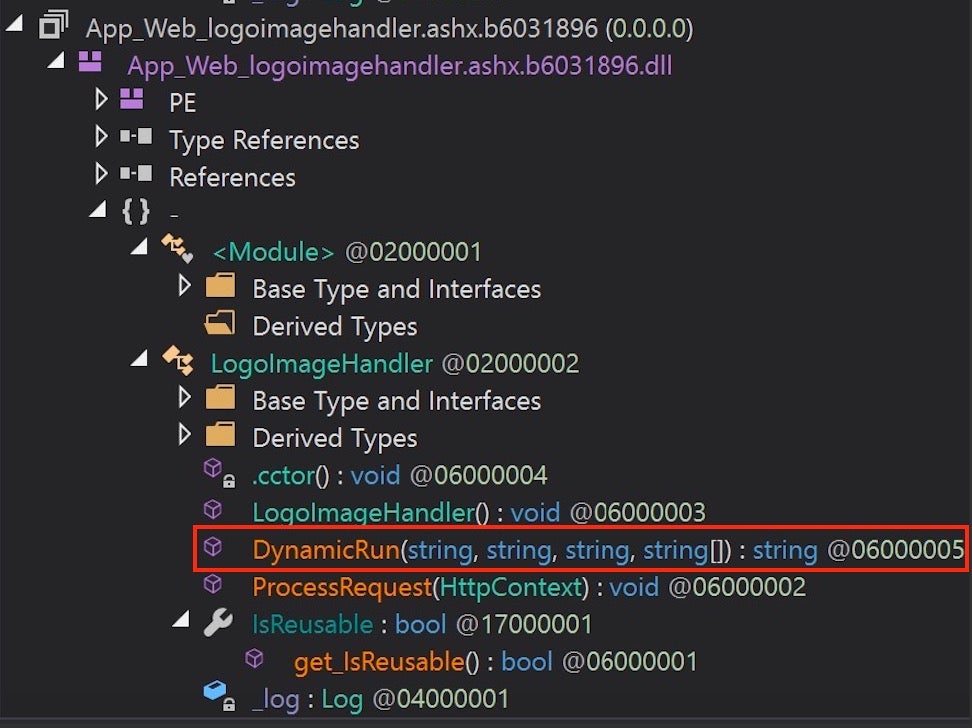
SUPERNOVA, you may recall, is a web shell implant that can compile and execute C# code in memory on exposed hosts. The implant uses a trojanized copy of a legitimate DLL .NET library, App_Web_logoimagehandler.ashx.b6031896.dll.
Although unconfirmed due to the removal of logs by the attacker, CISA believes the threat actor also likely exploited an authentication bypass vulnerability in SolarWinds Orion API (CVE-2020-10148 ) to allow execution of API commands remotely.
Lessons to be learned? Ensure your VPN has MFA enabled for all accounts, and ensure you have a security solution that keeps logs in the cloud, well out of reach of attackers’ meddling hands. Further details and recommendations from CISA are available here.