The Good
As organizations around the world continue the rapid transition to remote work, one educational institution in the UK managed to deliver a 5-year digital transformation plan in a single week. Going from a mere 100 remote users pre-Covid-19 lockdown to 22,000 in the space of a week may seem like an impossible task, but that didn’t phase the University of Sussex’s IT team. The feat was helped along by the fact that they had already begun work on the plan due to physical constraints at the university’s single-site campus long before anyone had ever heard of the coronavirus. However, what really made the difference was executive buy-in once the impact of the virus became apparent. With senior leadership on board, turning the long-term plan into a short-term business deliverable started to look genuinely achievable, and achieve it they did.
For other businesses still working through the details of how to move a large workforce to fully remote, the story of how SentinelOne successfully managed such a rapid transition should also prove insightful. As with University of Sussex, the keys to success lie within your organization rather than without.
The Bad
Researchers this week revealed details of a new botnet they have dubbed ‘dark_nexus’ that, while currently small, is under rapid and active development and has some interesting tricks up its sleeve.
Along with standard DDoS attacks, the botnet has the ability to disguise an attack as normal browser traffic in the hope of evading detection. The code also contains a ‘killer module’ which attempts to identify processes that may be a potential threat to itself, such as rival botnets. Among a number of persistence techniques, dark_nexus attempts to prevent device reboot by stopping the cron service and disabling other executables that could reboot the device. In common with Mirai and other botnets that specifically target IoT devices, dark_nexus uses a list of hardcoded credentials to attempt to brute force other machines on the network with such timeless classics as “admin:admin” and “user:user” as well as known defaults for Zhone and Dlink routers, among others. Fortunately for enterprise, Security 101 will keep organizations safe from this and other IoT botnets: ensure your IoT fleet is managed properly and that default credentials are changed.
The Ugly
There’s no shortage of stories on the shortage of cybersecurity professionals, and there’s greater focus on this now more than ever after CISA declared that those in cybersecurity are essential workers. But as ever, there are those that will look to exploit any situation to their own advantage in order to make a quick buck. This week’s Ugly starts with a complaint from a LinkedIn user who was offered an unethical means of gaining a certified ethical hacking certificate.
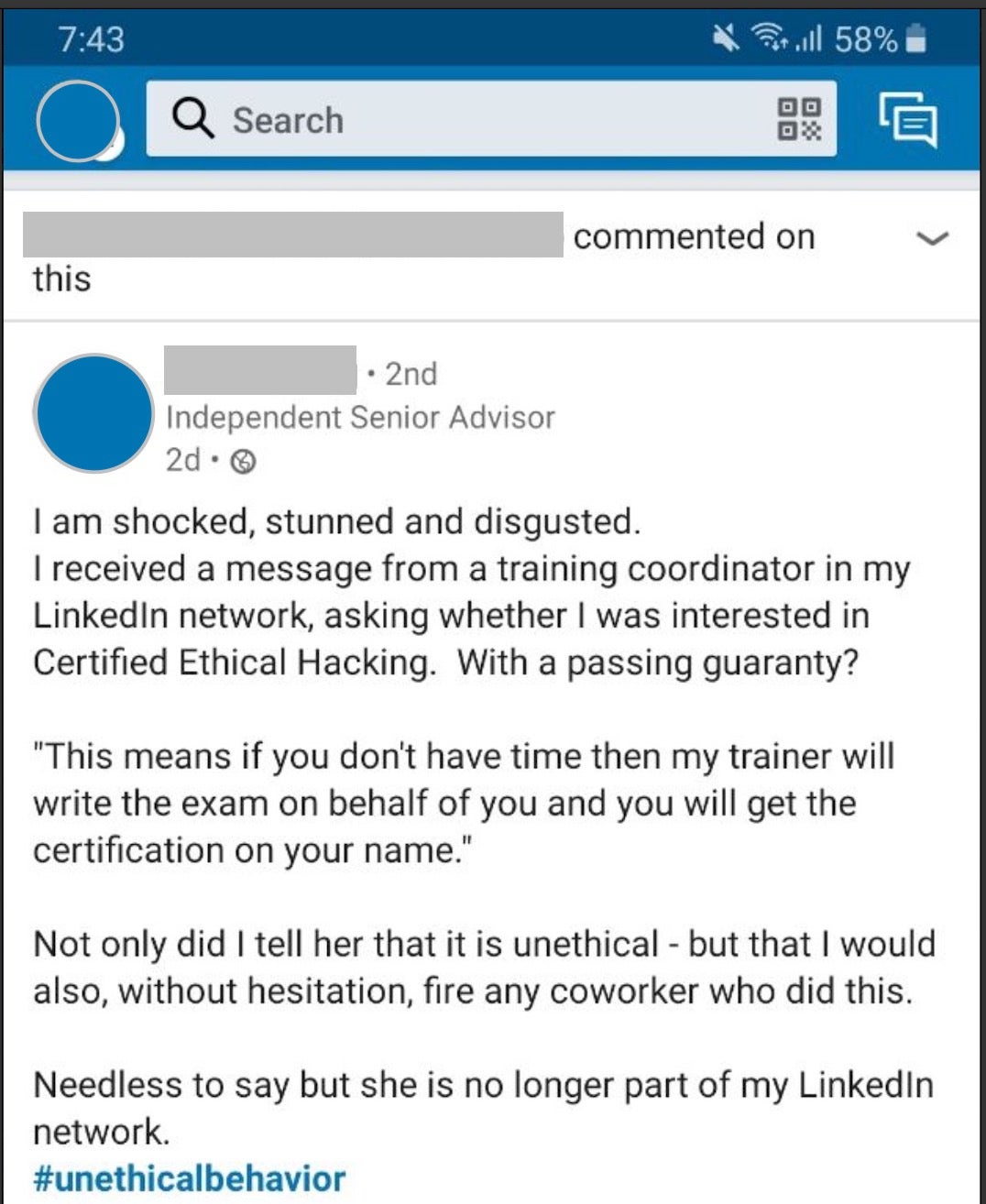
Unfortunately, this isn’t an isolated case. With cybersecurity skills in high demand and paying high salaries, so-called ‘exam substitution’ services, whereby someone else offers to take the exam in your name, are not hard to find. One such site advertises “EC-Council Certification Without EC-Council Exam Or EC-Council Training. 100% Pass-Guaranteed or 100% Money Back!”. Potential buyers are told that they “no need take exam”, “no need training” and “no need to go anywhere”. Just pay your money and “we’ll deliver the certification right at your doorstep within next 5 days”. The cost? In this particular case, a one-time, up-front payment of $2800.
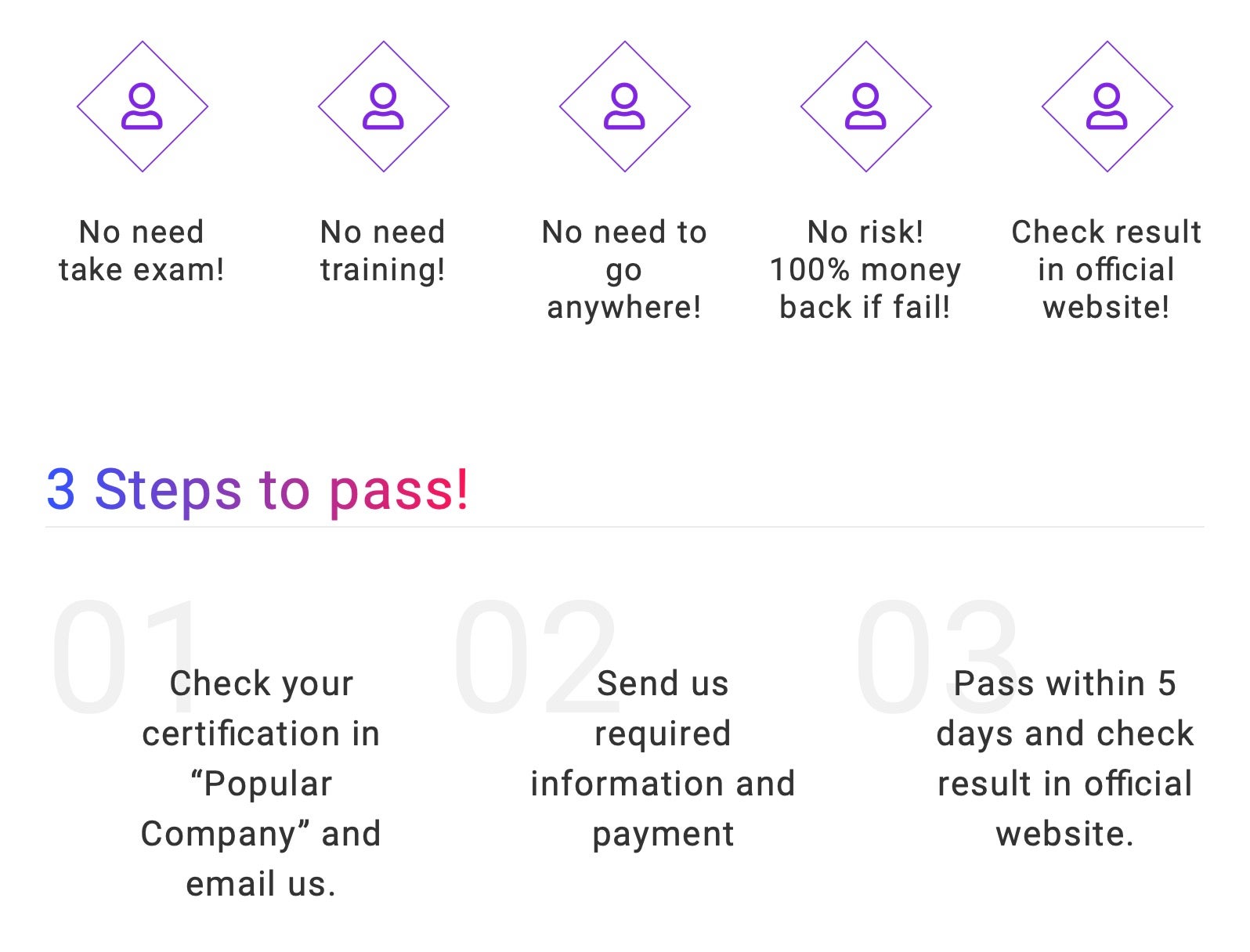
Such sites have “Scam!” written all over them, and we can’t help feeling that anyone finding themselves empty-handed or receiving a patently phoney “certificate” after trying to unethically obtain an ethical hacking certificate is not only unfit for our profession but also got a rich dose of what they justly deserved.