The Good | Top LockBit Ransomware Admin Charged & Ordered to Pay Restitutions
Russian-Canadian cybercriminal Mikhail Vasiliev has been sentenced to nearly four years in prison for his involvement in the LockBit ransomware operation. Initially arrested in November 2022, Vasiliev has pled guilty to eight charges, including cyber extortion, mischief, and weapons-related allegations.

Within LockBit, Vasiliev held a significant administrative role, participating in numerous high-profile attacks totalling over $100 million in ransom demands, which primarily affected businesses across Canada. Alongside a four-year sentence, he must pay $860,000 in restitution to his Canadian victims and faces extradition to the United States for further charges. American prosecutors have Vasiliev lined up to receive up to five years in a US prison for conspiring to intentionally damage protected computers and transmitting ransom demands.
LockBit, a notorious ransomware-as-a-service (RaaS) operation, has extorted at least $120 million in ransom payments from over 2000 victims in the last 3 years alone. The gang experienced major setbacks just last month, though, when a joint law enforcement operation seized its main infrastructure and arrested key affiliates. While the group quickly resumed operations on new leak sites to maintain activity, analysis suggests that most data leaked post-operation belonged to victims from before the takedown, indicating the threat groups’ struggle to regain momentum.
Currently, the Department of State is offering rewards up to $15 million for information that could lead to the arrest of other LockBit key leaders and affiliates. Two suspected members of LockBit, Ruslan Astamirov and Mikhail Matveev, were also apprehended in 2023 though only Astamirov has been officially charged for deploying LockBit ransomware. Matveev remains at large facing cyber sanctions and a 20-year prison term in the event of arrest and conviction.
The Bad | Almost 13 Million Authentication Secrets Exposed on GitHub
Threat actors are increasingly exploiting GitHub and repositories as a conduit for malicious activities. In a recent report detailing the issue of secrets sprawl, the findings show that in 2023 alone, GitHub users inadvertently exposed a 12.8 million authentication and sensitive secrets across over 3 million public repositories, with only 1.8% of users rectifying the issue upon receiving alerts.

These exposed secrets include critical data such as passwords, API keys, TLS/SSL certificates, OAuth tokens, and encryption credentials – all of which, if obtained by a threat actor, lead to unauthorized access and costly data breaches. This data corroborates another report from summer of 2023 pointing to compromised credentials as the root cause of 50% of recorded attacks in the first half of last year.
Just this week, security researchers observed a new phishing campaign that delivered remote access trojans (RATs) like VCURMS and STRRAT via a malicious Java-based downloader. The attackers behind these RATs are employing sophisticated tactics, leveraging public services such as GitHub and Amazon Web Services (AWS) to store malware and evade detection.
Millions of organizations rely on source code management platforms like GitHub for software development, version control, and continuous integration and deployment (CI/CD). The abuse of such platforms speaks to a concerning trend where threat actors leverage public infrastructure for malicious purposes.
Securing DevOps platforms and open-source code repositories involves implementing access controls, updating dependencies, and enforcing strong authentication. Threat intelligence and security monitoring tools help detect and respond to suspicious activities, while solutions like XDR offer comprehensive protection against cyber threats and infrastructure abuse.
The Ugly | One-Day Flaws Exploited by Money-Hungry ‘Magnet Goblin’ Threat Actor
A financially motivated threat actor dubbed ‘Magnet Goblin’ has been exploiting one-day vulnerabilities in public-facing servers to distribute custom Linux malware. Magnet Goblin’s adoption of the flaws has been quick: Security researchers confirmed cases where the one-days were already being leveraged to gain initial entry.
In one instance, Magnet Goblin integrated an exploit for the Ivanti Connect Secure RCE bug (CVE-2024-21887) just a day after a proof-of-concept (PoC) was published online. This exploit facilitated arbitrary code execution, enabling the group to compromise systems that had not yet patched to the latest updates. Magnet Goblin’s exploits extend beyond Ivanti, targeting platforms like Magento (CVE-2022-24086), Qlik Sense (CVE-2023-41265, CVE-2023-41266, and CVE-2023-48365), and potentially Apache ActiveMQ.
The group is currently deploying custom remote access trojans (RATs) and backdoors, including variants of the Nerbian family such as NerbianRAT and MiniNerbian. Upon execution, NerbianRAT establishes communication with a command-and-control (C2) server, allowing malicious activities like executing commands, modifying connection intervals, and updating configurations.
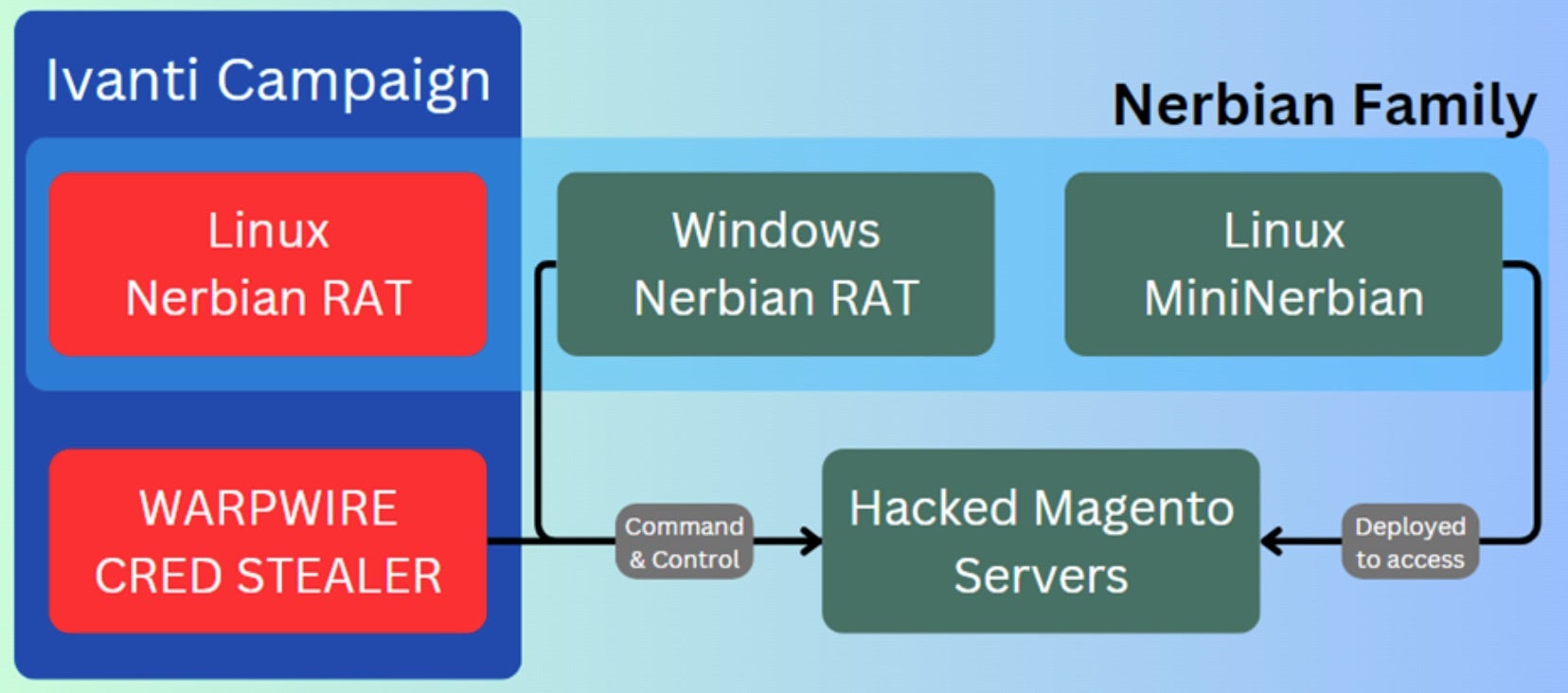
Over the years, the Linux OS has attracted threat actors for its ubiquity, powering a significant portion of servers, cloud infrastructure, and IoT devices which, in turn, provides a large attack surface. Its open-source nature also allows actors to study its codebase, identifying vulnerabilities and developing tailored exploits. With emerging threat actors like Magnet Goblin adding to the threat landscape who take advantage of the chaos that follows released PoCs, having a strict patch management process in place becomes a critical factor in staying ahead of one-day flaws.


