Cyber Threat Intelligence (CTI) involves collecting and analyzing information about potential threats. This guide explores the importance of CTI in proactive cybersecurity measures and incident response.
Learn about the types of threat intelligence, sources, and how to integrate CTI into your security strategy. Understanding CTI is crucial for organizations to stay ahead of emerging threats.
 What is Cyber Threat Intelligence?
What is Cyber Threat Intelligence?
According to Gartner, threat intelligence is “evidence-based knowledge (e.g., context, mechanisms, indicators, implications, and action-oriented advice) about existing or emerging menaces or hazards to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.”
In cybersecurity, threat intelligence is the data an organization collects, processes, and analyzes to better understand threat actors’ motives, targets, and attack behaviors. Using this information, organizations can make fast, informed decisions to protect themselves against threat actors in the future.
It’s important to note the difference between threat intelligence and threat information: threat information is the data itself without context, while threat intelligence involves analyzing the information and using it to inform any decisions about what steps to take next.
Why is Threat Intelligence Important?
Today, the threat landscape is more dynamic and sophisticated than ever before. Anticipating a threat actor’s next move is incredibly challenging, especially without data to back up any assumptions. Threat intelligence guides an organization’s assessment of threat actors’ past behaviors, what they’ll do next, and where protection is needed.
Threat intelligence has become an increasingly common capability among security tools and is a key component of security architecture that helps security teams detect and investigate threats.
Using threat intelligence, organizations are typically better prepared to:
- Reveal adversarial motives and their tactics, techniques, and procedures (TTPs) to empower cybersecurity stakeholders.
- Understand a threat actor’s decision-making process and help security teams implement incident response.
- Make decisions about cybersecurity investments by illuminating previously unknown information.
- Inform business stakeholders (e.g., executive boards, CISOs, CIOs, and CTOs) about threat actors’ behavior for wiser investments, improved risk mitigation, and more efficient and faster decision-making.
The Threat Intelligence Life Cycle
For most organizations, the threat intelligence life cycle consists of six stages: direction, collection, processing, analysis, dissemination, and feedback. However, the specific activities performed during each phase of the threat intelligence life cycle are often slightly different depending on the organization and are usually determined by a combination of unique factors including use cases, priorities, and risk.
Ideally, key stakeholders will clearly define the organization’s goals and objectives for threat intelligence before any other phases begin to ensure the success of the entire life cycle. Once threat intelligence goals are set, they may be subject to change depending on the data collected and the feedback received. Data is gathered from a wide variety of sources, including internal, technical, and human components, and then used to develop a more complete picture of potential and actual threats.
Most of the time, threat information is compiled into a threat intelligence feed: a continuous data stream that provides information about threats including lists of IoCs such as malicious URLs or emails, malware hashes, and suspicious IP addresses. The data populating threat intelligence feeds is often drawn from several sources, including open-source intelligence feeds, network and application logs, and third-party feeds.
Once enough data is collected, it is turned into actionable intelligence that is both timely and clear to everyone, including key stakeholders who will use the information to improve future threat intelligence life cycles and refine their decision-making processes.
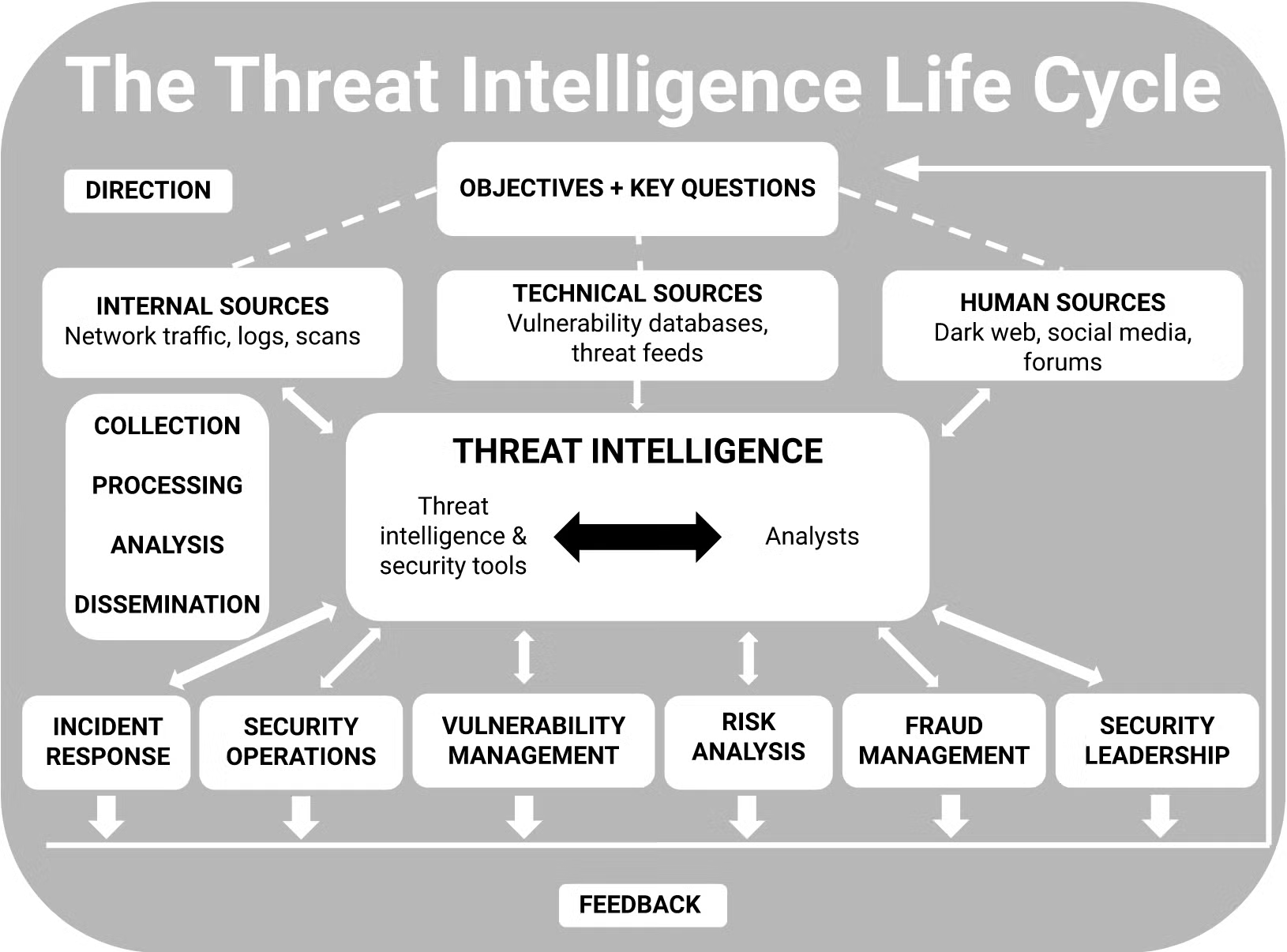
1. Direction
This phase of the threat intelligence life cycle is where stakeholders set goals for the overall threat intelligence program. Direction typically involves understanding and articulating:
- The assets that need protecting
- The potential impact of losing assets or interrupting processes
- The types of threat intelligence required to protect assets and respond to threats
- The priorities about what to protect
2. Collection
This phase of the threat intelligence life cycle involves gathering information that addresses the most important intelligence requirements. Data collected is usually a combination of finished information (e.g., intelligence reports from experts and vendors) and raw data (e.g., malware signatures or leaked credentials).
Collection typically occurs through a variety of sources, including:
- Metadata and logs from internal networks and security devices
- Threat data feeds from industry organizations and cybersecurity vendors
- Conversations and interview with knowledgeable sources
- Open source news and blogs
- Websites and forms
- Closed sources such as dark web forums
3. Processing
This phase of the threat intelligence life cycle involves transforming collected data into a usable format, with different means of processing for different collection methods. For instance, raw data must be processed by humans or machines in order to be considered usable, and all human reports should be correlated and ranked, deconflicted, and checked.
4. Analysis
This phase of the threat intelligence life cycle involves turning processed information into intelligence that can inform decisions. For example, those decisions could involve whether to investigate a potential threat, what actions an organization should immediately take to block an attack, how to strengthen security controls, or how much of an investment in additional security resources is justifiable.
The presentation of this analysis is also important. Organizations may collect and process endless amounts of information and then present it in a way that can’t be understood or used by decision-makers.
To communicate analysis with a non-technical audience, consider the following recommendations:
- Be concise
- Avoid overly technical terms and confusing jargon
- Articulate issues in business terms
- Include a recommended course of action
The format used to present such information will depend on the intelligence itself and the intended audience. Intelligence teams often provide analysis via a variety of formats, including live videos, slide decks, and formal reports.
5. Dissemination
This phase of the threat intelligence life cycle involves distributing the finished intelligence output to the right departments and teams.
For each intended audience, ask the following questions:
- What threat intelligence does the team need, and how can external information support their activities?
- How can intelligence be presented to make it easy to understand and actionable?
- How often should intelligence teams provide updates and other information?
- What media should be used to disseminate intelligence?
- How should teams follow up if they have any questions?
6. Feedback
Regular feedback from a variety of stakeholders and teams enables cyber threat intelligence analysts to adjust the threat intelligence life cycle so it meets the requirements of each team, especially as business goals and priorities change.
This phase clarifies the overall priorities and the requirements of the security teams that consume the intelligence. Ultimately, their unique needs will guide all future phases of the intelligence life cycle, including:
- What types of data to collect
- How to turn that data into useful information
- How to present that information as actionable intelligence
- Who should receive which types of intelligence, how quickly it should be disseminated, and how quickly to respond to follow-up questions?
Types of Cyber Threat Attacks
A cyberattack occurs when there is any type of unauthorized access to a system or network by a third party, carried out by a threat actor. Although various terms are often used interchangeably to describe different types of cyberattacks, there are some important differences worth noting.
1. Threat
A threat is a person or event with the potential for negatively impacting valuable assets. Although a variety of cyber threats may exist at any given time, threats themselves symbolize the possibility of an attack occurring, rather than the actual attack itself.
Threats may pose an imminent danger but do not cause harm until they are acted upon by a threat actor. The term “threat” is often used in reference to a wide variety of malicious activities that seek to damage, steal, or prevent access to data. Once a threat becomes a reality, it is then known as a cyberattack.
2. Vulnerability
A vulnerability is an inherent defect in a network, software, or system’s design that can be exploited by threat actors to damage, steal, or prevent access to assets. The most common types of vulnerabilities include system misconfigurations, out-of-date or unpatched software, missing or weak authorization credentials, missing or poor data encryption, and zero-day vulnerabilities (which are defined below).
3. Exploit
An exploit is a method threat actors use to take advantage of a vulnerability. It might include software, data, or commands that manipulate the vulnerability so the threat actor is free to perform unwanted or unauthorized actions.
Exploits can be used to install unwanted software, gain unauthorized access to sensitive data, or take control of a computer system. They’re frequently used in tandem with other attack methods.
4. Web Application Attack
A web application attack occurs when vulnerabilities in web applications allow threat actors to gain unauthorized access to sensitive data residing on a database server. The most common types of web application attacks are:
- SQL injections occur when a threat actor adds malicious code into an input form which is submitted into the database and changes, deletes, or reveals data.
- Cross-Site Scripting (XXS) attacks involve a threat actor uploading malicious script code onto a website that can be used to steal data or perform other unwanted actions
- Directory/path traversal is when a threat actor injects patterns into a web server hierarchy that allows them to obtain user credentials, databases, configuration files, and other information stored on hard drives
- Local file inclusion involves forcing a web application to execute a file located elsewhere on the system
- Distributed Denial of Service (DDoS) attacks occur when a threat actor targets systems, servers, or networks and floods them with traffic to exhaust their resources and bandwidth. Servers become overwhelmed by catering to the incoming requests and the target website is shut down or slowed down, leaving legitimate service requests unanswered
5. Advanced Persistent Threat
An advanced persistent threat (APT) is a broad term describing an attack campaign in which a threat actor establishes a long-term presence on a network to conduct reconnaissance or collect highly sensitive data. APT attacks typically require more resources than a standard web application attack, and the targets are often carefully chosen and well-researched.
The most common types of APT attack vectors are:
- Phishing: This is a type of social engineering attack wherein a threat actor impersonates a trusted contact and sends the target spam emails. When the target opens the email and clicks on the malicious link or opens the malicious attachment, the threat actor can gain access to confidential information and even account credentials. Some phishing attacks are also designed to trick users into installing malware.
- Malware: One of the most common types of cyberattacks today, a malware attack is when a threat actor uses malicious software to infiltrate a system or network. Malware attacks can include viruses, worms, spyware, ransomware, adware, and trojans. Typically, malware breaches a system or network through a vulnerability and is often executed via phishing emails. When the user clicks a link, installs software, or uses an infected pen drive, the malware is downloaded on the device and can spread.
- Man-in-the-Middle (MITM): Also known as an eavesdropping attack, this occurs when a threat actor positions themselves in between communications between trusted parties (i.e., the attacker hijacks communications between clients and hosts) by interrupting the client-server communication and rerouting it through the attacker. MITM attacks ultimately enable threat actors to steal and manipulate data without the target’s knowledge.
- Zero-Day or N-Day Attacks: These involve the use of previously undisclosed or recently patched security vulnerabilities. The term “zero-day” refers to the idea that the software vendor or developer has had “zero days” to implement a fix since the flaw became known. N-Day vulnerabilities are known bugs that have been recently patched by a vendor (N-days ago) but which remain widespread because software users have yet to update the affected software. Zero-day attacks occur when threat actors successfully exploit a vulnerability before a patch is released to address it. Sometimes, threat actors identify zero-day vulnerabilities before developers do, and in other cases, the developer may actually alert threat actors to the vulnerability’s existence when they announce the flaw to clients and customers.
Fortunately, using cyber threat intelligence can help protect organizations against many of the cyber threats above to prevent cyberattacks.
 Enhance Your Threat Intelligence
Enhance Your Threat Intelligence
See how the SentinelOne threat-hunting service WatchTower can surface greater insights and help you outpace attacks.
Learn MoreTypes of Cyber Threat Intelligence
Cyber Threat Intelligence is a broad term that can be broken down into several subcategories.
1. Tactical Cyber Threat Intelligence
Tactical cyber threat intelligence focuses on the immediate future. Technical in nature, tactical cyber threat intelligence detects simple indicators of compromise (IOCs) and gives a detailed analysis of a threat’s tactics, techniques, and procedures. Using information collected by tactical threat intelligence can help organizations develop defense policies designed to prevent attacks and improve security systems.
Tactical cyber threat intelligence is an easier type of threat intelligence to generate and is almost always automated. However, because this type of threat intelligence is often collected through open-source and free data feeds, it usually has a very short lifespan – IOCs including malicious IPs or domain names can become obsolete in days or even hours.
2. Strategic Cyber Threat Intelligence
Strategic threat intelligence involves looking at long-term, non-technical issues. By creating an overview of the threat environment (i.e., cyber threats and the risks associated with them), the use of strategic cyber threat intelligence can help organizations make more informed business decisions. This information allows decision-makers to invest in tools and processes that will safeguard their business in alignment with their overall objectives.
Strategic intelligence is considered one of the more challenging forms of cyber threat intelligence because it often involves human data collection and analysis. For strategic threat intelligence to be most successful, analysts often have a deep understanding of cybersecurity and the current global geopolitical situation.
3. Operational Cyber Threat Intelligence
Operational threat intelligence is a more technical approach, focusing on the nature, timing, motive, and intent of an attack. Using tactics such as tracking and threat actor profiling, organizations can collect data that helps them detect and understand past attacks and predict future threats more accurately with mitigation in mind.
This approach to cyber threat intelligence is aimed at understanding cyberattacks: the “who” (i.e., the attribution), the “why” (i.e., the intent), and the “how” (i.e., the tactics, techniques, and procedures). Like strategic threat intelligence, operational threat intelligence also includes a human analysis component and is often most useful for cybersecurity experts.
This type of cyber threat intelligence may work in conjunction with other cybersecurity disciplines such as vulnerability management, incident response, and threat monitoring.
Cyber Threat Intelligence Jobs & Courses
Cyber threat intelligence jobs can include:
- Cyber threat intelligence analyst
- Cyber fraud detection
- Cybersecurity solutions architect
- Cyber threat specialist
- Cyber threat intel
- IT Security Analyst
For anyone looking to build a career in cyber threat intelligence, SentinelOne offers the Zero to Hero Course, a 12-part malware reverse engineering and threat intelligence course. This complete guide is one of the best resources for jump-starting a career in cyber threat intelligence.
The course provides:
- Technical overview of injection techniques and persistence mechanisms
- Discovering/recognizing privilege escalation in malware
- Threat actor techniques to gain a foothold on networks
- Deep dive into APTs (advanced persistent threats), eCrime
- Info-stealers and Exploit Kit drive-bys seen in the wild
- Analyzing shellcode usage in malware
- Complete analysis of malware techniques – stealth, persistence, algorithms, communication to a C2 server, and advanced capabilities
Sources of Cyber Threat Intelligence
CTI can be obtained from various sources, each providing unique insights into the threat. Understanding these sources is important for building a CTI program.
Here are the most common sources of CTI:
- Open-source intelligence (OSINT): This involves gathering information from publicly available sources, such as
- Social media: Monitoring social media platforms for discussions about cyberattacks, malware, and vulnerabilities.
- News websites: Reading news reports about cyberattacks, security breaches, and industry trends.
- Forums and blogs: Analyzing discussions on security forums and blogs to identify emerging threats.
- Public databases: Accessing publicly available databases that contain information about vulnerabilities, malware, and threat actors.
- Human intelligence (HUMINT): This involves gathering information from people, including
- Industry experts: Consulting with security researchers, analysts, and experts to gain insights into current threats.
- Threat researchers: Engaging with researchers who specialize in specific threat actors or attack methods.
- Security conferences: Attending security conferences to network with experts and learn about new threats.
- Signals intelligence (SIGINT): This involves gathering information from electronic signals, such as
- Network traffic analysis: Monitoring network traffic for suspicious activity, such as malware communication or data exfiltration.
- Communication interception: Analyzing encrypted communications to identify potential threats.
- Radiofrequency analysis: Analyzing radio frequency signals to detect potential attacks or malicious activity.
- Malware analysis: This involves reverse engineering malicious software to understand its functionality, capabilities, and attack methods. This process helps security teams identify the source of attacks, understand the attacker’s objectives, and develop countermeasures.
- Threat data feeds and reporting: These subscription-based services provide real-time threat information, including
- Indicators of compromise (IOCs): Specific data points that can identify malicious activity, such as IP addresses, domain names, and file hashes.
- Vulnerability reports: Information about newly discovered vulnerabilities and their potential impact.
Threat actor profiles: Information about specific threat actors, their motives, and their TTPs.
Benefits of Using Cyber Threat Intelligence
Cyber threat intelligence can introduce a number of additional benefits for organizations beyond the scope of mitigation, including:
- Risk reduction: Increased visibility across the threat landscape into current threats and emerging cyberattacks may help organizations identify and assess risks with a proactive approach to preparation.
- Improved security posture: Understanding the TTPs used in past attacks can help organizations implement the appropriate security controls to prevent or mitigate future cyberattacks.
- Cost reduction: Cyber threat intelligence is often cost-effective and may lower the overall financial burden of security incidents including data breaches, which can be expensive.
- Regulatory compliance: Organizations that must adhere to various regulations such as GDPR, SOX, HIPAA, etc. can use cyber threat intelligence to help establish and maintain compliance.
- Staffing efficiency: Manual validation and correlation of threat intelligence can be time-consuming and resource-intensive. Security teams are often prone to burnout and fatigue for this very reason, which can lead to human error. With the support of cyber threat intelligence tools, organizations can better equip security teams to detect and respond to threats more efficiently with the use of automation to eliminate tedious manual tasks.
Cyber Threat Intelligence Tools
Cyber threat intelligence tools help protect current vulnerabilities as well as future ones by collecting and analyzing threat information from several external sources.
Here are five features to examine when considering a cyber threat intelligence tool:
- Data-driven: When a malicious attack is initiated, a “fingerprint” or cyber threat indicator is left behind. A cyber threat intelligence tool should gather data from cyber threat indicators to protect in both a predictive and proactive manner.
- Flexible: Most organizations want cyber intelligence tools to be compatible with any IT infrastructure and environment they may have.
- External-focused: Cyber intelligence tools may be integrated with internal systems to assist in threat detection, but they should prioritize scanning external sources like data feeds and repositories for any emerging threats.
- Comprehensive: Cyber intelligence tools must provide complete protection. This means that it should be able to scan large numbers of external feeds from all across the world, including the dark web.
- Extensible: Cyber threat intelligence tools should also be extensible and seamless enough to connect to any cybersecurity landscape. It should be able to co-exist with varying environments, compliance tools, and hardware variants.
Best Practices for Implementing Cyber Threat Intelligence
Implementing a successful CTI program requires a strategic approach and a commitment to best practices. Here are some key recommendations to guide you:
1. Create a CTI Team
Create a dedicated team responsible for CTI operations. This team should consist of individuals with expertise in threat intelligence, security, and data analysis. The team should be responsible for:
- Gathering intelligence—Collecting threat intelligence from various sources.
- Analyzing intelligence—Interpreting threat data and generating actionable insights.
- Disseminating intelligence—Sharing intelligence with stakeholders across the organization.
- Maintaining a CTI library—Building and maintaining a repository of threat information.
2. Integration with Incident Response
Ensure a simple integration between CTI and incident response processes. This means:
- Sharing intelligence—Providing incident responders with relevant threat intelligence during investigations.
- Using IOCs—Using indicators of compromise (IOCs) to detect and identify malicious activity.
- Analyzing attack methods—Using CTI to understand attack methods and develop effective response strategies.
3. Collaboration and Information Sharing
Foster collaboration within the organization and with external partners. This involves:
- Sharing intelligence internally—Sharing threat intelligence among security teams, business units, and relevant personnel.
- Collaborating with external partners—Sharing intelligence with other organizations, industry groups, and government agencies.
- Joining information-sharing communities—Participating in industry forums and information-sharing groups to exchange insights and best practices.
4. Continuous Improvement and Adaptation
Continuously evaluate and refine CTI practices. This involves:
- Measuring CTI effectiveness—Tracking key metrics, such as the number of threats detected, the impact of CTI on incident response, and the reduction in security incidents.
- Gathering feedback—Collecting feedback from stakeholders on the usefulness and impact of CTI.
- Adapting to new threats—Staying informed about emerging threats, and updating CTI processes accordingly.
By following these best practices, organizations can build a CTI program that can help them mitigate threats, improve their security, and protect their valuable assets.
Challenges in Cyber Threat Intelligence
Although CTI offers various benefits, implementing and managing a successful program also comes with challenges. Here are some issues that organizations might face:
1. Data Overload and Management
Managing vast amounts of data from diverse sources can be overwhelming. CTI teams must be able to:
- Filter and prioritize data—Identify and focus on the most relevant and actionable intelligence.
- Organize and structure data—Create a system for organizing and storing large volumes of data.
- Use data analytics tools—Use data analytics tools to automate the analysis and interpretation of data.
2. Attribution of Cyber Threats
Determining the source of attacks and identifying attackers can be challenging. This involves:
- Analyze attack methods—Understand the techniques used in an attack to determine the potential attacker.
- Correlate data points—Connect various pieces of evidence to identify the source of an attack.
- Use threat actor profiles—Use known threat actor profiles and TTPs to attribute attacks.
3. Balance Speed and Accuracy
Maintaining a balance between intelligence delivery and accuracy is important. Organizations need to:
- Provide timely insights—Deliver threat intelligence to stakeholders on time to enable a quick response.
- Ensure accuracy—Verify the accuracy of intelligence before sharing it to avoid false positives and misleading information.
- Use automated tools—Use automated tools to speed up the analysis and dissemination of threat intelligence.
4. Ensure Data Privacy and Compliance
Complying with data privacy regulations and protecting sensitive information is essential. Organizations must:
- Adhere to data protection laws—Comply with relevant data privacy regulations, such as GDPR and CCPA.
- Implement data security measures—Store and manage threat intelligence data to prevent unauthorized access.
- Establish data governance policies—Develop clear policies for data collection, use, and disposal.
Addressing these challenges is important for building a sustainable and effective CTI program.
Case Studies and Real-World Applications
Here are a few real-world examples showcasing the power of CTI:
#1. Health Care
Anthem, one of the largest health insurance companies in the U.S., implemented a strong CTI program following a major data breach in 2015. They now use threat intelligence to identify and mitigate potential threats to their network and customer data.
#2. Finance
JPMorgan Chase, a leading global financial services firm, has made significant investments in cybersecurity and CTI. They’ve established a Cyber Defense Center that uses threat intelligence to monitor and respond to potential cyber threats in real-time.
#3. Government
The U.S. Department of Homeland Security operates the Automated Indicator Sharing (AIS) program, which is a CTI sharing platform. This system allows the department to share cyber threat indicators with federal agencies and private sector partners.
#4. Technology
Microsoft has a dedicated Digital Crimes Unit that uses CTI to combat cybercrime. They use threat intelligence to disrupt botnets and other cyber threats that could affect their products and customers.
#5. Retail
Target, after experiencing a data breach in 2013, has since invested heavily in cybersecurity and CTI. They now use threat intelligence to better protect their customer data and prevent future breaches.
SentinelOne’s Cyber Threat Intelligence Tools
SentinelOne protects organizations of all sizes with advanced cyber intelligence tools that manage processes related to the entire threat lifestyle, allowing users to detect threats across multiple vectors.
SentinelOne’s AI-driven learning uses behavioral analysis tools that constantly monitor and look for signs of a security breach. It quickly responds to threats with its ActiveEDR module and gives insightful data that provides a clearer understanding of the cause of an attack and the steps taken to neutralize it.
With innovative threat detection tools that can integrate with third-party applications including Splunk, Okta, BigFix, and more, SentinelOne monitors systems throughout the network and across platforms for in-depth visibility and analysis throughout the entire enterprise and at every stage of the cyber threat intelligence life cycle.
Discover how SentinelOne helps organizations proactively and holistically protect what matters most. Schedule a demo today.
Wrapping Up
Cyber threat intelligence helps predict future attacks by helping organizations understand, plan, and prepare for potential threats, and react quickly when something goes wrong. Using CTI, companies can save money, protect their reputation, and keep their systems safer. It’s not just about defending against attacks; it’s about being ready before they even happen.
If you’re looking for a good CTI platform, consider using SentinelOne. It uses artificial intelligence to spot cyber threats and automatically fight back. By using SentinelOne, companies can defend themselves by identifying potential attackers and minimizing risks. Try SentinelOne today!
FAQs
Malware, phishing, denial-of-service attacks, and data breaches are some common threats.
Start by setting clear goals, building a team, choosing the right tools, and integrating CTI into your security processes.
These platforms help manage data, automate analysis, improve threat visibility, and make sharing information easier.
Begin by learning about CTI, exploring available resources, starting small, and considering a managed CTI service if you need extra help.



