Released March 31, 2022, the MITRE Engenuity ATT&CK® Evaluations covered 30 vendors and emulated the Wizard Spider and Sandworm threat groups. For the third year in a row, SentinelOne leads the test which has become widely accepted as the gold-standard test for EDR capabilities.

What are Wizard Spider and Sandworm?
Wizard Spider is a financially motivated criminal group that has been conducting ransomware campaigns since August 2018 against a variety of organizations, ranging from major corporations to hospitals, and deploying tools such as Ryuk and TrickBot.
Sandworm is a destructive Russian threat group that is known for carrying out notable attacks such as the 2015 and 2016 targeting of Ukrainian electrical companies and 2017’s NotPetya attacks. According to MITRE, these two threat actors were chosen based on their complexity, relevancy to the market, and how well MITRE Engenuity’s staff can fittingly emulate the adversary. MITRE Engenuity tested our product, Singularity XDR, evaluating both detection and protection.
How Did SentinelOne Perform on the MITRE Engenuity ATT&CK® 4th Evaluation?
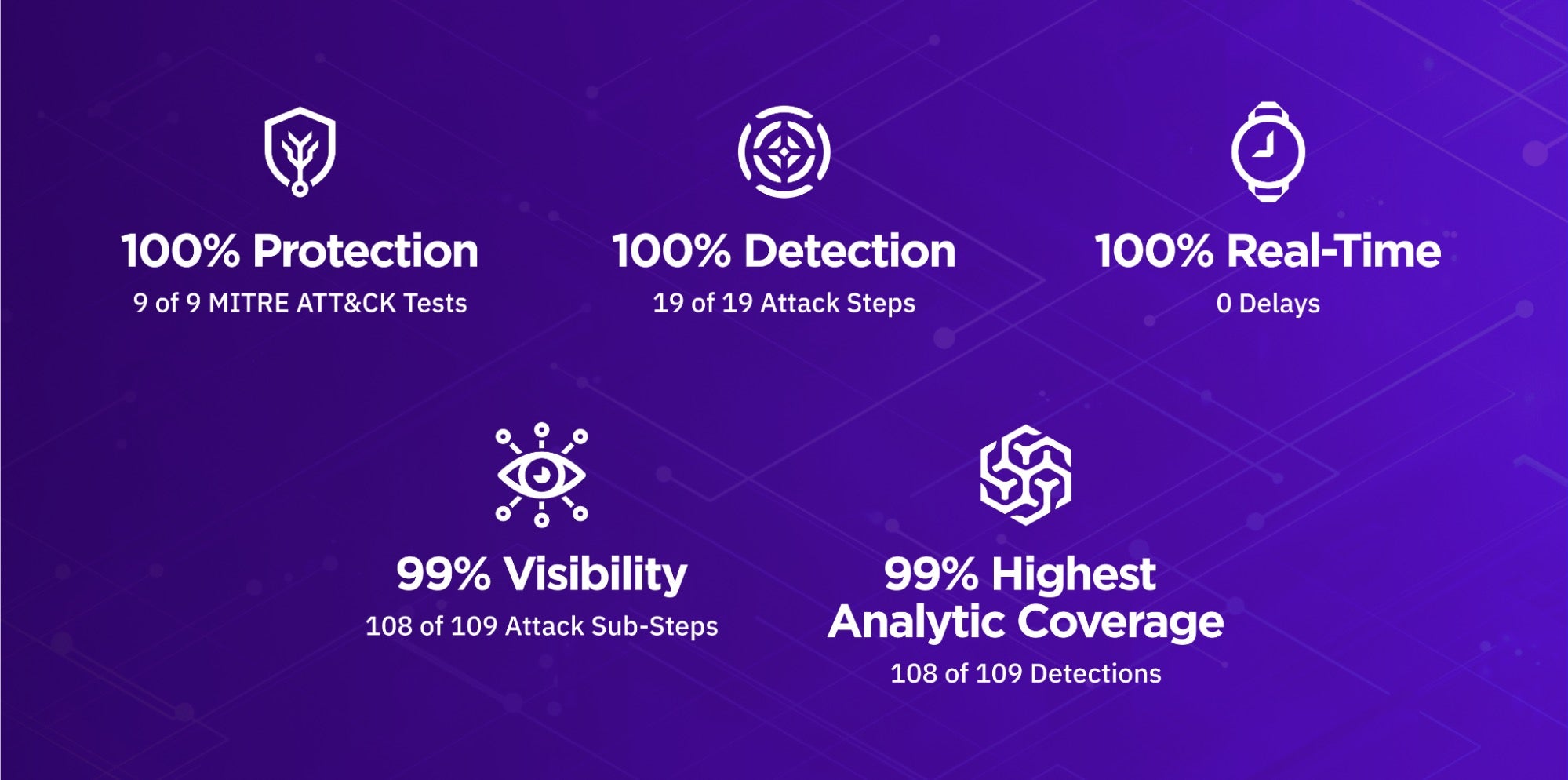
Let’s let the data answer that question:
- SentinelOne delivered 100% Protection: (9 of 9 MITRE ATT&CK tests)
- SentinelOne delivered 100% Detection: (19 of 19 attack steps)
- SentinelOne delivered 100% Real-time (0 Delays)
- SentinelOne delivered 99% Visibility: (108 of 109 attack sub-steps)
- SentinelOne delivered 99% – Highest Analytic Coverage: (108 of 109 detections)
Autonomous Protection Instantly Stops and Remediates Attacks
Security teams demand technology that matches the rapid pace at which adversaries operate. MITRE Protection determines the vendor’s ability to rapidly analyze detections and execute automated remediation to protect systems.
SentinelOne delivered the fastest protection. With its real-time protection, Singularity XDR provided the MITRE ATT&CK Evaluation with the least amount of permitted actions in the kill-chain for attackers to do damage. The ATT&CK results reveal our commitment to preventing and protecting against every possible threat and keeping our customers safe from most adversaries.
The Most Useful Detections are Analytic Detections
Analytic detections are contextual detections that are built from a broader data set and are a combination of technique plus tactic detections. This produces a detailed view of what took place, why, and how. Having access to high-fidelity, high-quality detections saves operator time, maximizes response speed, and minimizes dwell time risk.
SOC teams often find themselves with too many alerts and not enough time to investigate, research, and respond. Alerts for the sake of alerts become meaningless: unused and unnoticed. Pinpointed alerts that are actionable with pre-assembled context maximize EDR effectiveness and use.
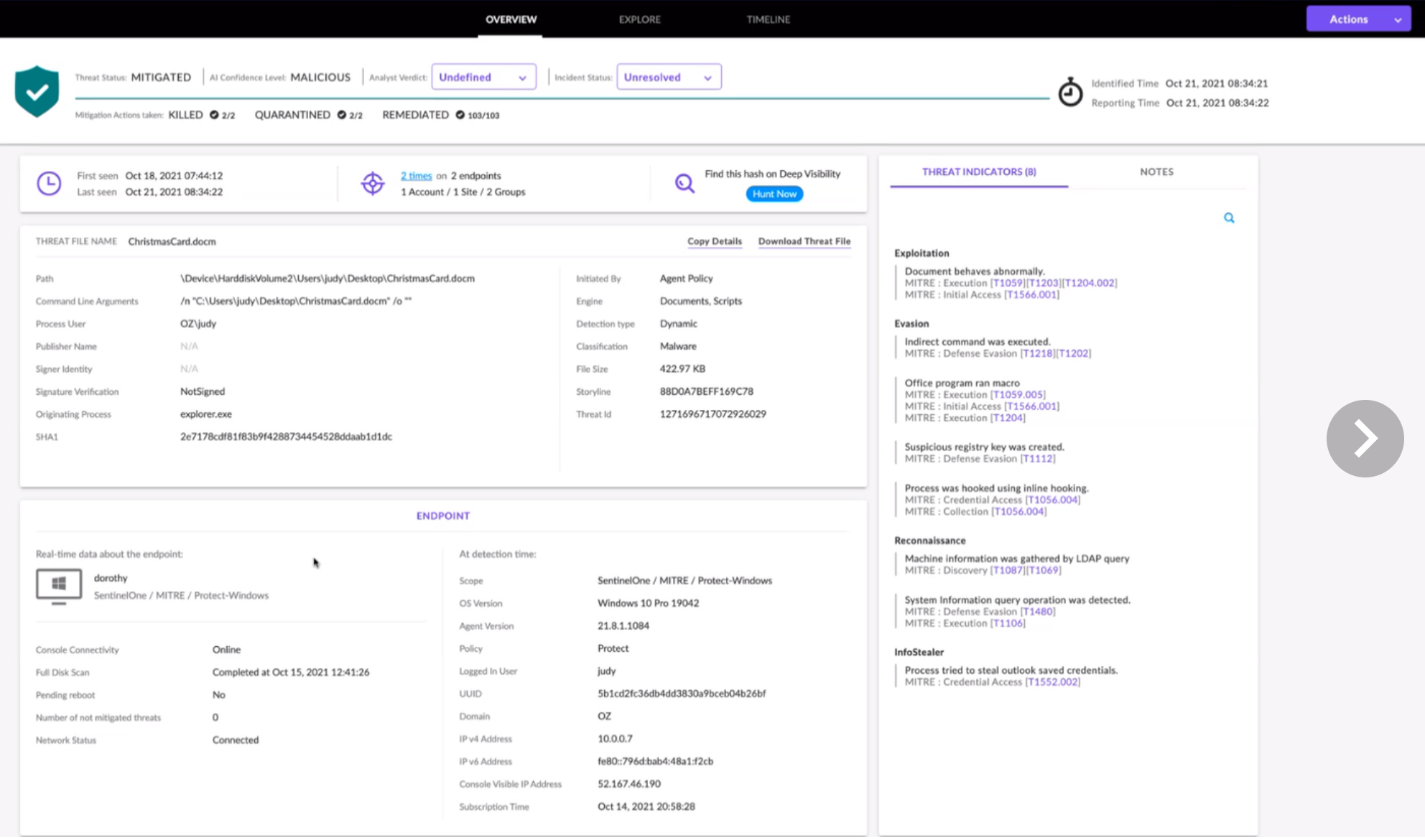
SentinelOne’s patented Storyline technology percolates every event happening in real-time, providing a fulling indexed, prefabricated map for each alert. All this work happens on the agent side, resulting in a massive advantage compared to technology or teams that try to figure out what happened after everything happened – when it’s too late. The power of autonomous cybersecurity is that it happens in real-time, where and when the action is taking place, on the attack surface itself.
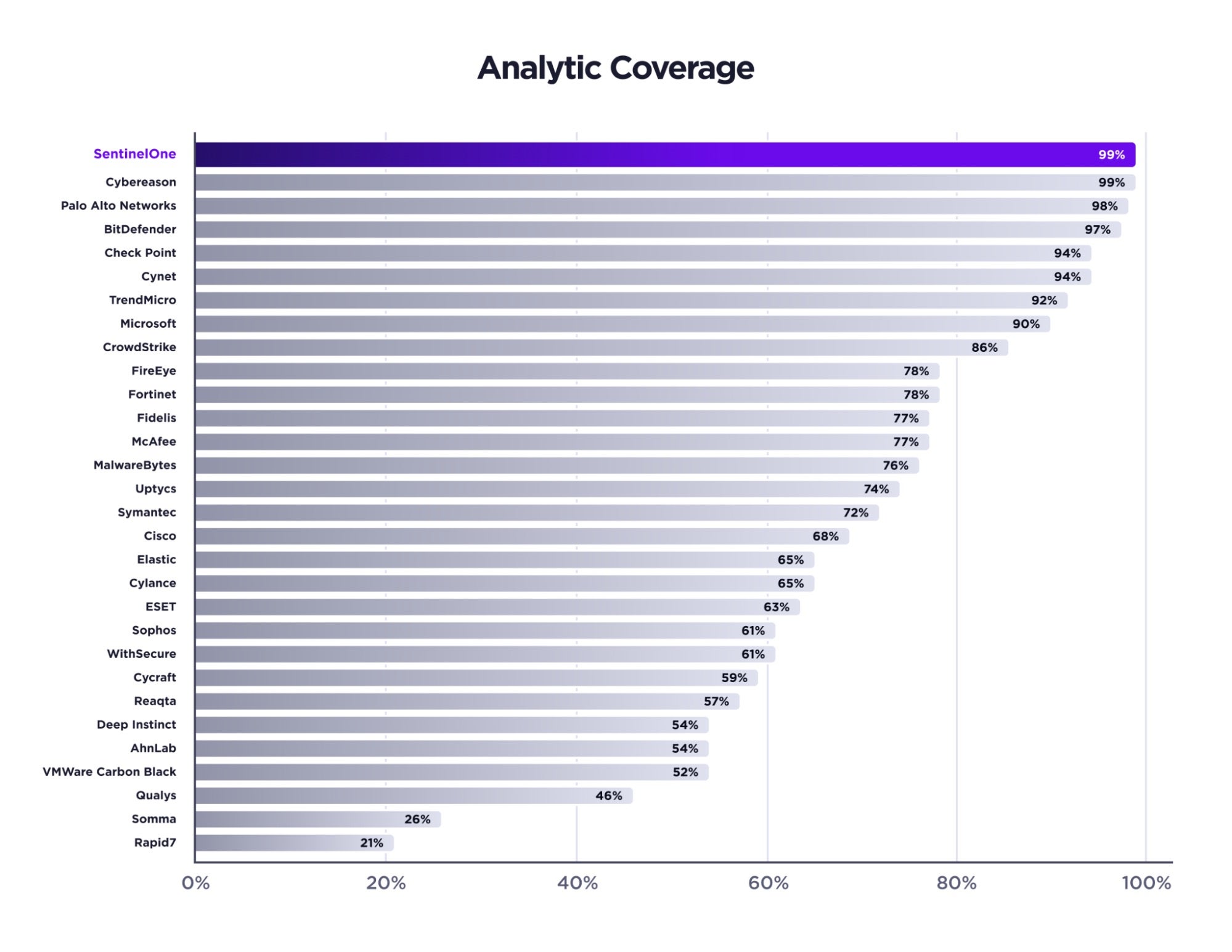
According to MITRE Engenuity’s published results, SentinelOne recorded the highest number of analytic detections for this year’s evaluation and the last three years out of all participants in this evaluation.
Visibility Ensures That No Threats Go Undetected
Visibility is the building block of EDR and is a core metric across MITRE Engenuity results. In order to understand what’s going on in the enterprise as well as accurately threat hunt, cybersecurity technology needs to create a visibility aperture. The data needs to be accurate and provide an end-to-end view of what happened, where it happened, and who did the happening regardless of device connectivity or type.
During the ATT&CK Evaluation, the TTPs used by Wizard Spider and Sandworm were grouped into 19 attack steps and SentinelOne Singularity detected all of them. This allows a comprehensive view of the entire enterprise, minimizing incident dwell time and reducing risk.
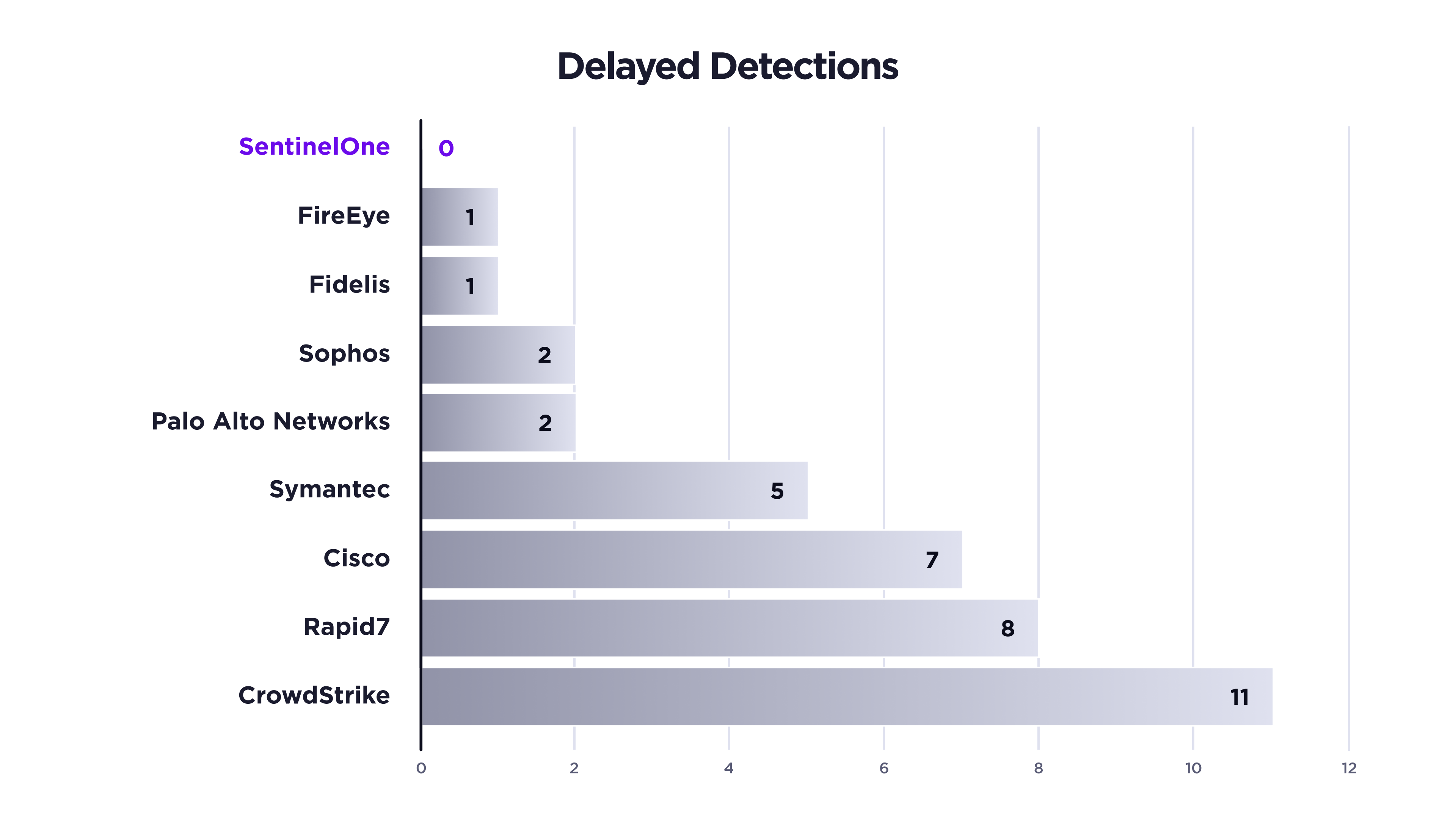
Detection Delays Undermine Cybersecurity Effectiveness
Time plays a critical factor whether you’re detecting or neutralizing an attack. Organizations that want to reduce exposure need to have real-time detections and automated remediation as part of their security program.
A delayed detection during the evaluation indicates that the EDR solution uses a legacy approach, and requires a human analyst to confirm suspicious activity due to the inability of the solution to do so on its own. The solution typically needs to send data to the cloud for more investigation, to sandbox solutions to give their verdict or other 3rd party solutions. Aside from the time lag that this necessarily involves, it relies on humans to respond quickly, resulting in a window of opportunity for the adversary to do real damage.
Adversaries operating at high speed must be countered with machine speed automation that’s not subject to the inherent slowness of humans. Real-time detections translate to faster response and reduced risk to your organization.
SentinelOne’s automated AI approach delivered 100% real-time detection with zero delays.
Simplicity Drives Effectiveness and Reduces Risk
More signal and less noise is a challenge for the SOC and modern IR teams who face information overload. Rather than seeing alerts on every piece of telemetry within an incident and fatiguing the already-burdened SOC team, cybersecurity teams benefit from a solution that automatically groups data points into consolidated alerts: A solution with a sweet spot on an axis where the number of false alerts is low and the true positives are accurate and pinpointed. This reduces the amount of manual effort needed, helps with alert fatigue, and significantly lowers the skillset barrier of responding to alerts.
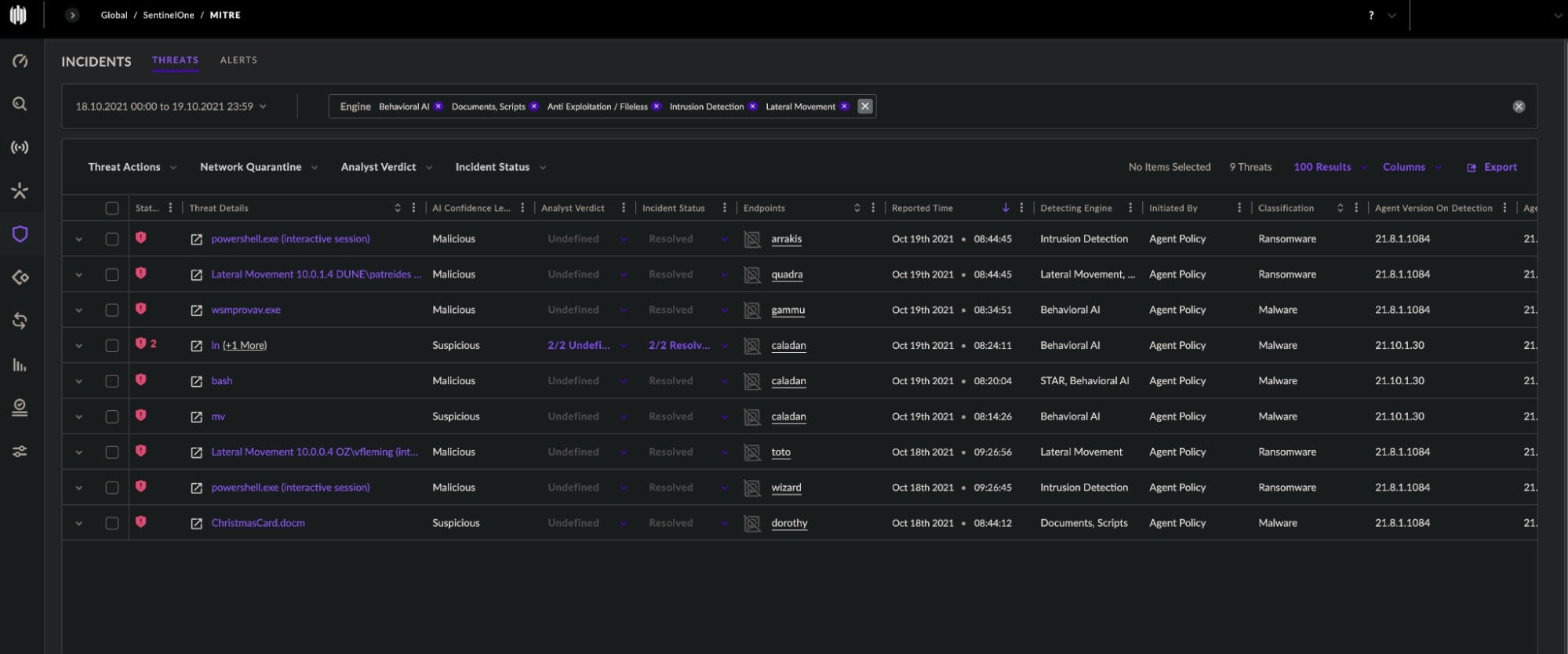
Consolidating hundreds of data points across a 48-hour advanced campaign, SentinelOne correlated and crystallized the attack into one complete story. SentinelOne provides comprehensive insights within seconds rather than having analysts spend hours, days, or weeks correlating logs and linking events manually.
SentinelOne Singularity XDR summarized two days of testing into nine campaign-level console alerts, showcasing the platform’s ability to correlate, contextualize, and alleviate SOC burdens with machine speed.
Why SentinelOne? Why Should It Matter To You?
The results from all four years of the ATT&CK Evaluations highlight how the SentinelOne solution maps directly to the ATT&CK framework to deliver unparalleled detection of advanced threat actor Tactics, Techniques, and Procedures (TTPs). Organizations can immediately benefit from exceptional protection and detection capabilities and autonomous and one-click response options to stop and contain the most advanced cyberattacks.
As evidenced by the results data, SentinelOne excels at visibility and detection and, even more importantly, in the autonomous mapping and correlating of data into fully indexed and correlated stories through Storyline™ technology. The superior visibility, actionable context, and the ability to defeat adversaries in real-time sets Singularity XDR apart from every other vendor on the market.
To learn more about SentinelOne’s results on the fourth round of MITRE Engenuity ATT&CK® evaluations, visit: https://www.sentinelone.com/lp/mitre/.


