Since early September, SentinelLabs has been tracking the rapid rise of a new malware loader that previous researchers have dubbed “SquirrelWaffle”. The tool has been utilized in multiple global attacks since then and is being likened to Emotet in the way it is being used to conduct massive malspam campaigns.
In this post, we explain how SquirrelWaffle works, what to look out for and how to protect your business from the latest malspam loader.

What Is SquirrelWaffle Malware?
SquirrelWaffle is a recent malware loader that is distributed through malspam – malicious spam mail – with the purpose of infecting a device with second-stage malware such as cracked copies of the red teaming tool Cobalt Strike and QakBot, a well-known malware that started life as a simple banking trojan but has since evolved into a multi-functional framework with RAT (Remote Access Trojan)-like capabilities.
Researchers have noted how the infection chain may begin with an email reply chain attack, in which a threat actor neither inserts themselves as a new correspondent nor attempts to spoof someone else’s email address. Instead, the attacker sends the malicious SquirrelWaffle email from a hijacked account belonging to one of the participants. Since the attacker has access to the whole thread, they can tailor their malspam message to fit the context of an ongoing conversation. Given that the recipient likely already trusts the sender, there’s an increased likelihood of the target opening the maldoc or clicking the link. Email reply chain attacks were a hallmark of Emotet campaigns and contributed a great deal to its success.
SquirrelWaffle first appeared in early September and defenders have noticed an uptick in incidences of infection since then. SentinelLabs researchers have also noticed that the malware drops unique payloads even from the same infection chain and that file path patterns are continuing to evolve.
How Does SquirrelWaffle Infect Devices?
Initial delivery of SquirrelWaffle as a first stage loader often comes courtesy of a phishing email with either a malicious MS Word or Excel attachment or embedded link leading to a zip-compressed malicious document download. These maldocs contain VBS macros which execute PowerShell to retrieve and launch the SquirrelWaffle loader.
The initial SquirrelWaffle files are written to disk as prescribed by the malicious PowerShell script responsible for their retrieval. For example, early clusters of malicious documents dropped SquirrelWaffle using this set of file names:
C:\Datop\test.test C:\Datop\test1.test C:\Datop\test2.test
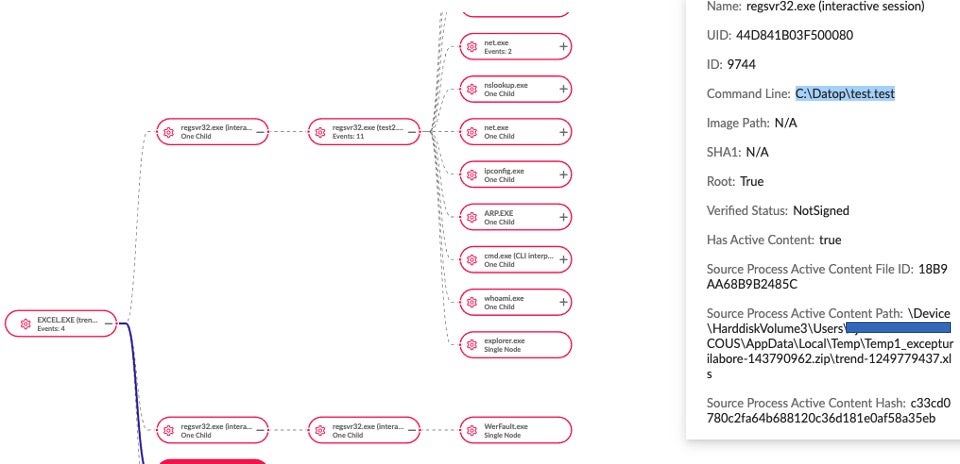
Importantly, no two runs of the same malicious document will produce the same SquirrelWaffle payloads. On each execution, the payloads written to disk will have unique hashes.
"C:\Users\<redact>\AppData\Local\Temp\Temp1_natusut-1501184.zip\grade-2086577786.xls" C:\Datop\test.test - 8d7089f17bd5706309d7c6986fdd1140d6c5b4b2 C:\Datop\test1.test - 52452f6f0ab73531fe54935372d9c34eb50653d8 "C:\Users\<redact>\OneDrive - folder, Inc\Desktop\grade-2086577786.xls" C:\Datop\test.test - bce0e9e1c6d2e7b12648ef316748191f10ed8582 C:\Datop\test1.test - 8ba7694017d1cea1d4b73f39479726478df88b20 "C:\Users\\OneDrive - folder, Inc\Desktop\grade-2086577786.xls" C:\Datop\test.test - 8aec96029b83d3b226c8c83dd90f48946ee97001 C:\Datop\test1.test - 8262cd7029f943a7b6199b5a6c51ec19e085c3b7
SquirrelWaffle has been observed using more conventional file name patterns as well, such as those with .dll extensions:
ww1.dll ww2.dll ww3.dll ww4.dll ww5.dll
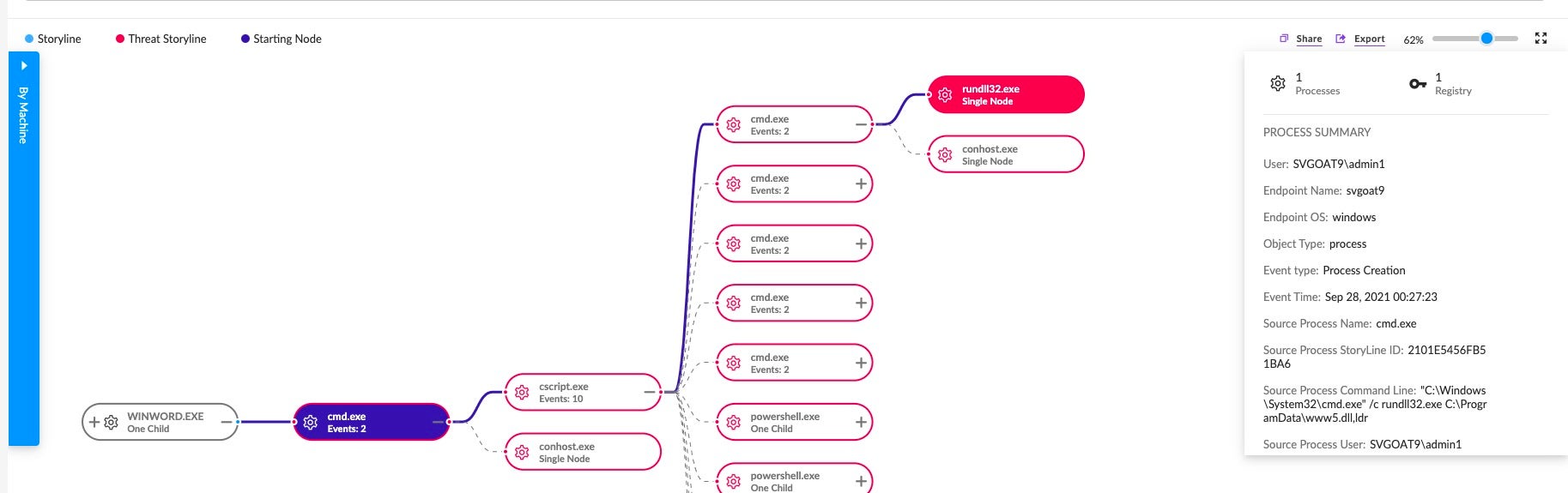
In early November, we observed yet another pattern, indicating that the malware authors are continually iterating:
good.good good1.good good2.good
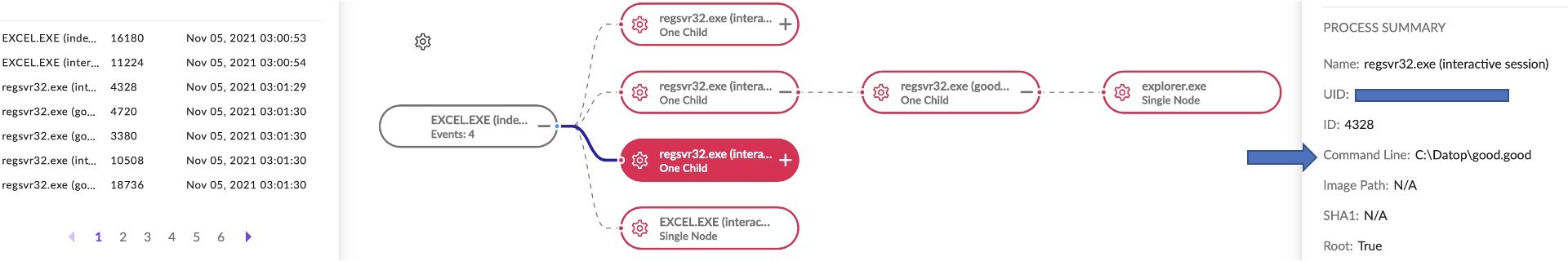
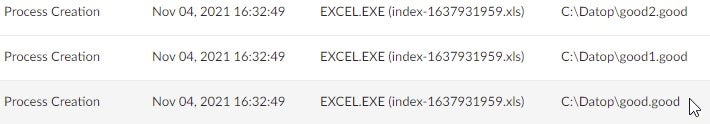
SquirrelWaffle Shares Code With Other Attack Frameworks
SquirrelWaffle, in common with many other malware samples, uses a custom crypter. Doing so is attractive for many reasons, not the least of which are obfuscation and anti-analysis to prevent researchers from developing strong indicators of compromise for detection.
Researchers have shown that SquirrelWaffle uses the same custom crypter as other well-known attack frameworks including Ursnif, Hancitor and Zloader. This is used, among other things, to hide the malware’s Command and Control (C2) URL.
Upon infection, SquirrelWaffle can download a Cobalt Strike payload with .txt extension and execute using the WinExec function. The other likely payload that may be downloaded by current SquirrelWaffle infections is Qakbot.
Below we can see process injection into explorer.exe from a SquirrelWaffle infection.
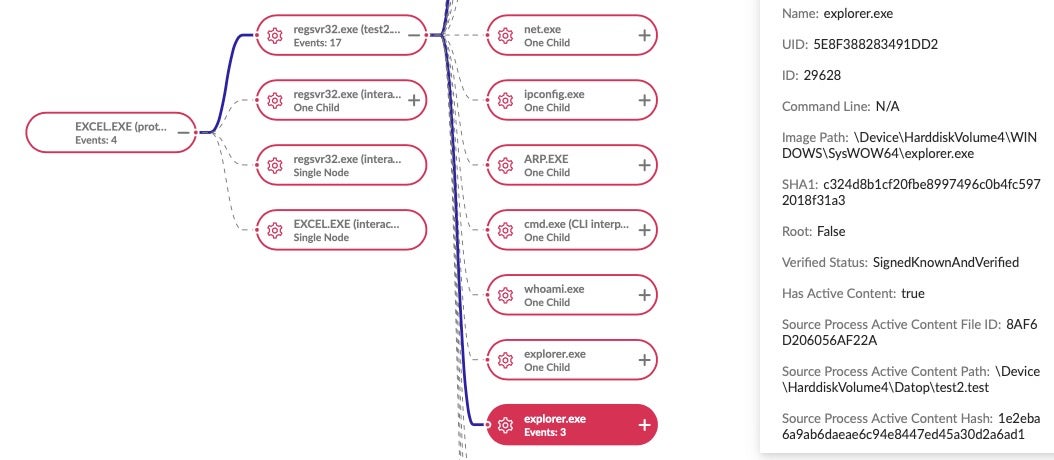
If infected with Qakbot, the malware will attempt to extract email data from the host.
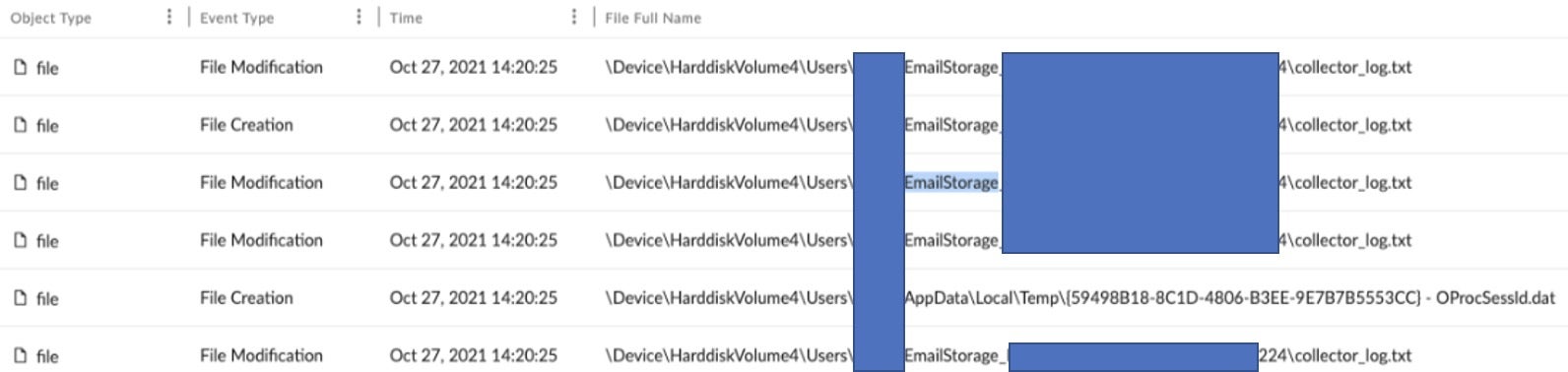
From the above image, we can see the C:\Users\<user>\EmailStorage_<hostname>_<username>_<timestamp> pattern. The “collector_log.txt” contains a record of the malware’s enumeration and exfiltration process.
How To Protect Against SquirrelWaffle
The SentinelOne platform detects and protects all customers against SquirrelWaffle infection. In the video demonstration below, we set the agent policy to ‘Detect Only’ to observe the infection in action. In ordinary circumstances, customers would use the Protect policy to prevent execution.
Conclusion
Cybercriminals are quick to come up with new loaders to team up with other groups that will help deliver a variety of payloads to achieve maximum financial gain. SquirrelWaffle is the latest such loader, currently being used to deliver Cobalt Strike and Qakbot but which can easily pivot to dropping any payload the operators wish. While SquirrelWaffle is certainly not yet anywhere near as prevalent as Emotet in its heyday, all the hallmarks are there of a campaign and infrastructure looking to grow.
If you would like to know more about how SentinelOne can protect your business against SquirrelWaffle and other threats, contact us for more information or request a free demo.
Example SHA1 Hashes
8d7089f17bd5706309d7c6986fdd1140d6c5b4b2
52452f6f0ab73531fe54935372d9c34eb50653d8
bce0e9e1c6d2e7b12648ef316748191f10ed8582
8ba7694017d1cea1d4b73f39479726478df88b20
8aec96029b83d3b226c8c83dd90f48946ee97001
8262cd7029f943a7b6199b5a6c51ec19e085c3b7


