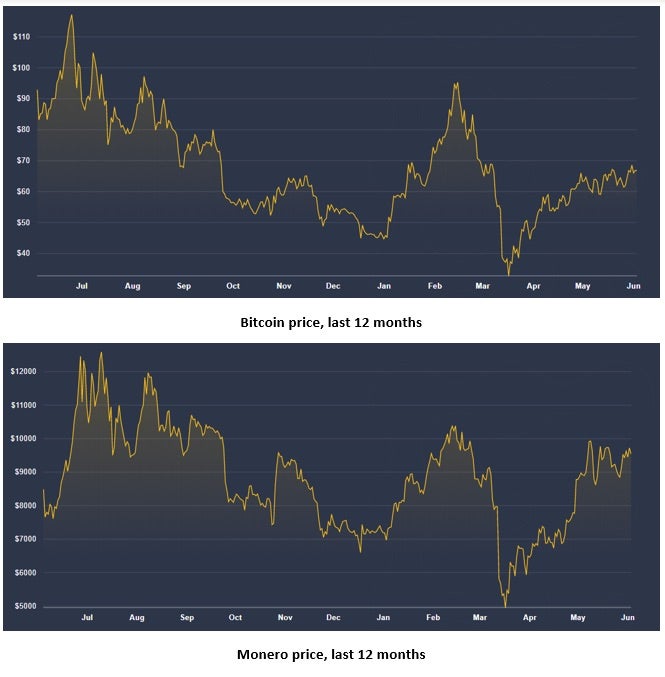
The recent Verizon DBIR suggests that Cryptojacking is declining in popularity, but evidence from the field might suggest otherwise. The intensity of cryptojacking activity usually mimics the price of cryptocurrencies, especially Bitcoin and Monero. The price of Bitcoin has fluctuated greatly during the last 12 months, from highs of $12,000 back in July 2019 to lows of around $5,000 in March 2020. The value of Bitcoin has doubled since that nadir, as has the price of its lesser-known sibling Monero.
With Cryptocurrency rates going up, it would be no surprise to see mining activities, legal and illegal, increase. As several recent incidents have shown, Cryptojacking is still a threat to both enterprises and individuals.

What is Cryptojacking?
Cryptojacking is the criminal manifestation of cryptomining. Cryptojackers use similar techniques as malware to sneak on to an endpoint: drive-by downloads, phishing campaigns, in-browser vulnerabilities, and browser plugins to name a few. There are two main methods of operation for Cryptojacking: the first is to infect the browser with a plugin that consumes some computing power when the victim is online (naturally, without the user’s awareness). The second type resembles classic malware: installed on endpoints and servers, it runs on the local machine (even when the user thinks the computer is turned off) and utilizes the victim’s internet connection to mine cryptocurrency for the attackers.
Miners are designed to operate on all operating systems: Windows, Linux and even macOS.
Where Have All The Cryptominers Gone?
There has been a consensus in the cybersecurity and law-enforcement community over the last 12 months that cryptojacking is on the decline. This is a result of several massive takedowns of mining botnets, like the huge botnet consisting of 850,000 computers that was detected and taken offline by a joint operation of French police and the security company Avast, or the Smominru campaign that hijacked half a million PCs to mine cryptocurrency, or an organized crime scheme in China enslaving computing resources of 9,000 internet cafés throughout the country.
Additional factors are the shutdown of Coinhive, the leading site that dealt with cryptominers. Coinhive provided JavaScript code that websites could incorporate to make visitors’ computers mine Monero, a cryptocurrency that happens to appeal to cybercriminals because it’s difficult to trace. Coinhive’s code was quickly abused: a mining script can also be injected into a website by hackers without the site owner’s knowledge. The site shutdown on March 2019, and with it, the number of site infections went sharply down.
These activities even led to the incarceration of some cyber criminals – a rare occurence in cybercrime, particularly as a result of mining, which is generally considered a low-risk form of criminal activity. However, two Romanian nationals were sentenced to two decades in U.S. prison apiece after their malware mined crypto on 400,000 infected computers. The two were part of the Bayrob Group that developed, deployed and monetized malware for mining Bitcoin and Monero.
But Wait…Cryptojacking Is Hot Right Now!
But as effective as these activities were, the increasing price of cryptocurrencies appears to have lured criminal hackers back into the game.
Last year, around 10% of organizations polled by Verizon reported cryptocurrency malware, but that figure is almost certainly below the actual incidence in the wild. First, the report notes that many organizations likely do not even report cryptocurrency incidents, particularly if the installer has been detected or blocked before the miner manifests itself as a malicious process. Moreover, last year’s figures may not reflect what’s happening now, as several more recent reports have indicated that crimninal cryptomining is still very much in vogue.
In Singapore, for instance, a spike in cryptojacking attempts was observed between January and March 2020, when there were three times more attempts to conduct cryptojacking than the same period in the previous year. The shift to working from home during the Covid-19 era has also aided cyber criminals, who are utilizing Zoom installers to infect victims with cryptocurrency-mining malware inside installers.
Hackers are also eager to exploit vulnerabilities to allow them to mine freely. Blogging platform Ghost has reported that attackers have successfully infiltrated its Salt-based server infrastructure and deployed cryptomining malware.
Another cybercrime group called “Blue Mockingbird” has infected more than 1,000 business systems with Monero mining malware since December 2019. The group’s specialty is exploiting servers running ASP.NET, obtaining administrator-level access to modify the server settings and installing the XMRig application to take advantage of the resources of the infected machines to mine away.
Cybercriminals who wished to utilize even more computing power have targeted several supercomputers across Europe in locations such as Germany, Scotland, Switzerland and Spain. The attackers exploited a Secure Shell (SSH) connection used by academic researchers to log in remotely. Once inside, they deployed cryptocurrency-mining malware on the supercomputers.
In another incident, cryptojacking malware almost caused some physical harm when an enthusiastic gamer felt his machine was not performing to spec, and burned his hand after touching the overheated casing of it’s GPU. It turned out that the gamer had inadvertently downloaded cryptomining malware, which may have been running for three weeks or more before he discovered it.
What Can Be Done To Stop Cryptojacking?
The first and best step would be to avoid getting infected in the first place. Enterprises should employ an advanced EDR solution to ensure that miners are detected either pre- or on-execution. If the malware dropper is not caught pre-execution, automated behavioral detection engines will catch cryptominers shortly after execution as they begin to behave abnormally. Some sophisticated miners might operate in stealth mode to avoid detection by legacy AV solutions, such as throttling CPU usage or mining only when the machine is in a certain state. These can be identified by monitoring for and analyzing any increased network traffic. Features like SentinelOne’s Deep Visibility make this kind of threat hunting simple without special training.
Next, employ a solution to identify and mitigate in-browser cryptominers. SentinelOne utilize sIntel’s Accelerated Memory Scanning (AMS) library, which enables fast memory scanning offloaded to the Graphics Processing Unit (GPU), to seek unique characteristics of cryptominers.
Conclusion
Cryptojacking is far from dead. It continues to exist and remains popular given the increase in cryptocurrency prices. Cryptominers can be stealthy and pose a challenge to security teams, particularly if they are relying on legacy AV solutions that do not possess AI-powered behavioral detection engines. To help keep cryptojackers from stealing your resources, try SentinelOne’s free demo or contact us for more information.


