Another day, and another blizzard of worrying posts about a new malware variant that appears to evade your existing solution. Bolstered by scary statistics – with a “sponsored research” disclaimer neatly tucked away in the bottom corner, of course! – you’ll be led to the author’s solution soon enough: typically, a promotion to buy a new product for a problem you were not aware of before reading the post.
The burgeoning industry of threat intelligence fills our need to be on top of cyber-security, but often seems to offer us nothing more than a “throw more money at it” kind of salvation. You already know there is a limit to the budget that can be thrown at these problems, and this is before even considering the overhead of managing yet another security product.
Some new products require training or assigning a team member to take ownership of the solution. Then, you are likely to face another challenge when your expert wants to move up the ladder or try another role, and as you are then stuck with a solution that you advocated internally and received the budget for, but now don’t have the means to manage.

No one Wants to be Reactive When it Comes to Security
As Chief Information Security Officer (CISO), this picture may seem depressingly familiar. Caught between the need to stay on top of ever more sophisticated threats becoming more commonplace on the one hand, and running an efficient, manageable suite of tools on limited resources and staff on the other, you need to be able to prepare for the unexpected, adapt to the reality of finding and maintaining cybersecurity talent, and keep your budget from ballooning out of control.
To see how we might meet these conflicting demands, let’s review three events that shaped the way we perceive risks today and encapsulate the problems a modern CISO has to face.
-
WannaCry
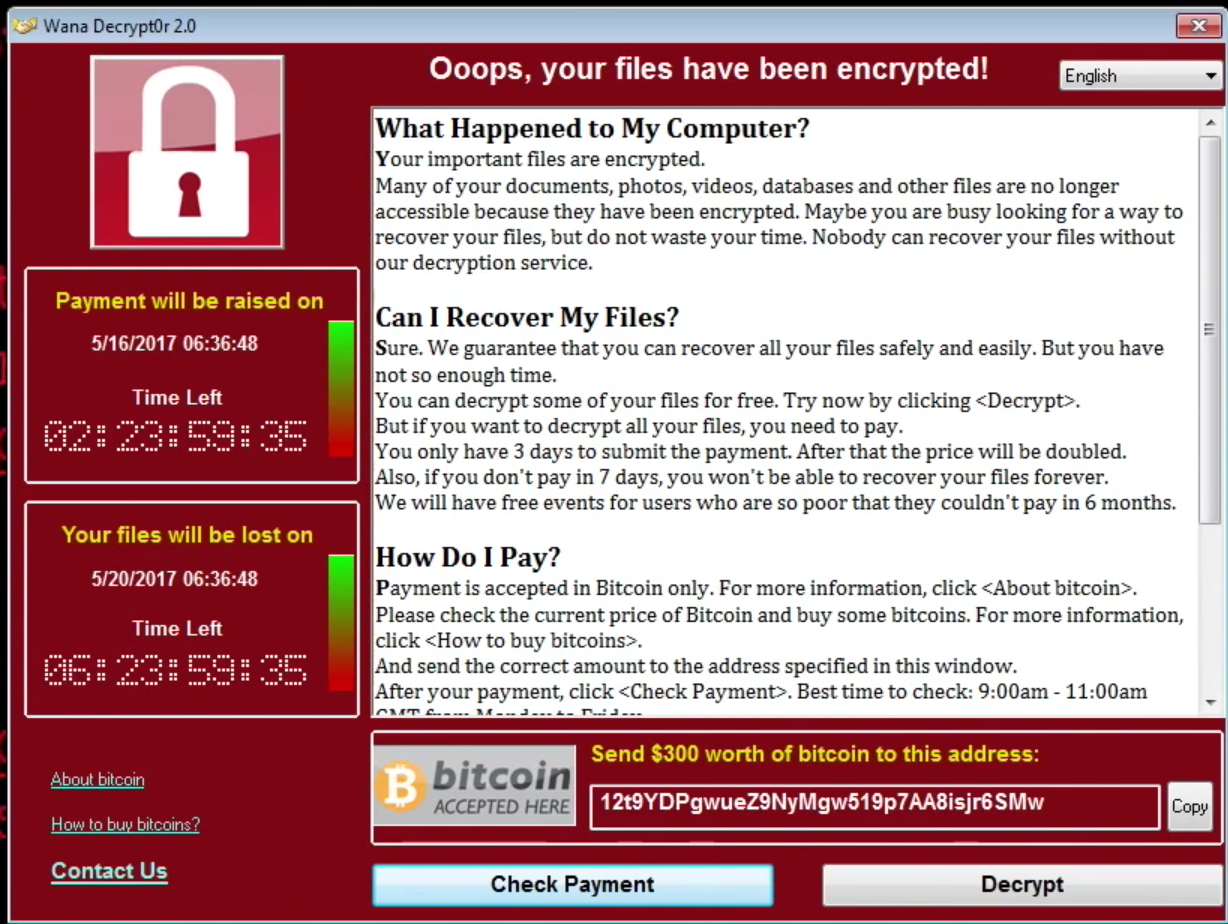
It’s hard to recall a bigger shock to the IT community than WannaCry, “the biggest ransomware offensive in history.” Within 24 hours, WannaCry had infected more than 230,000 computers in over 150 countries.
From a technical point-of-view, it was not particularly sophisticated. In fact, it exploited a vulnerability that had been known for 91 days and that had already been patched by Microsoft. Even so, an estimated 1.3 billion endpoints were eventually infected. In the UK, the National Health Service – a major client for Sophos – had to cancel 20,000 appointments and operations due to the ransomware. Whether any lives were lost as a result of it will never be known, but what is known is that it crippled the country’s health service.
Takeaways
Patch management is widely considered a mainstay of a proactive security policy to help secure your assets. That said, it is clearly not a silver bullet, even for known vulnerabilities. Repeatedly patching a large number of devices can take longer than it takes for rapidly-evolving software to utilize a vulnerability for monetary gain. If an exploit becomes known the following day or shortly after your last patch cycle, it’s pure luck whether you do or don’t get hit before your next round of patches get pushed to your endpoints.
SentinelOne customers were protected from WannaCry because our behavioral AI technology detected the SMB exploit injecting a DLL into lsass.exe and spawning new processes as malicious intent. No update was needed.
-
Ransomware Strikes the City of Atlanta
In March 2018, vital city services in Atlanta – from law enforcement to utility payments – were disrupted to such an extent that in some cases local officials had to revert to using paper records. It took weeks for the city to regain control.

According to reports, the ransomware that was used was SamSam malware. Again, it was not something new to the defense industry, having first been identified as far back as 2015. What made this attack interesting from a security perspective was not so much its technical aspect but its economic one.
The attackers were careful in their choice of target: they often pick victims whose budgets tend to lead to weak security practices, and then set a price that isn’t beyond their means. If the City of Atlanta had chosen to pay the ransom to the criminals, they would need to say goodbye to 52k US Dollars. Fortunately, they did the right thing and refused to pay. However, that ended up with damage estimated to cost taxpayers as much as $2.6M.
Takeaways
Without adequate protection, enterprises face a moral dilemma: to pay or not to pay? Ransomware attacks will inevitably increase as they are easy and cheap to deploy, and they force companies into making difficult decisions. The attackers seem to benefit either way: if the company takes the easy way out, the attackers hit pay day, and if not, headlines like those generated from the Atlanta City case will only strike fear into future victims.
-
CCleaner – a Supply Chain Attack
Another example that shaped the state of security was the case of CCleaner. In September of 2017, SentinelOne received a report on an apparent false positive. The customer mentioned that it was related to one particular version of CCleaner being detected as malicious. A few weeks previously, the attackers had replaced the original version on the official website with their back-doored version. The malicious software had already been downloaded by 2.27 million users.
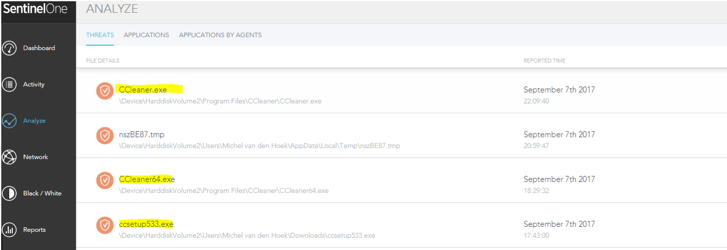
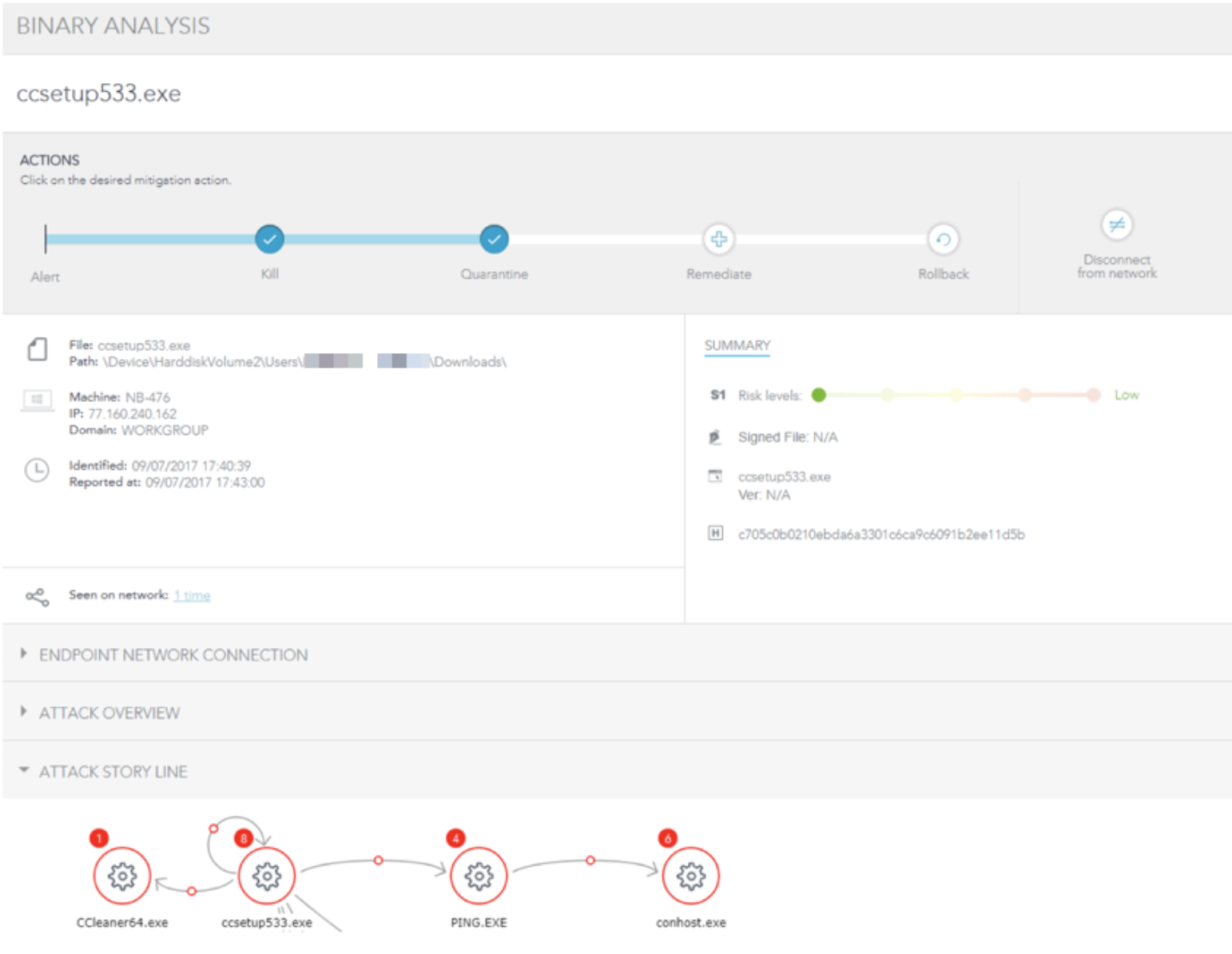
This wasn’t an isolated case. From time to time, SentinelOne reveals cases where an apparently legitimate application is either collecting unauthorized data or has been compromised to include malware.
Takeaways
Too many security solutions rely on a thin-layer of trust: passing over so-called reliable or reputable software to focus on unknown or untrusted files and applications. Relying on “who its from” rather than “what it’s doing” opens the door to supply chain attacks. This is where solutions like SentinelOne, based on behavioral AI detection and layered security, really shine.
“The Only Constant is Change” – Heraclitus
So how do we solve the CISO’s dilemma outlined above? No one wants to have the next big data breach land in their own backyard, and yet there are too many possible security holes to be proactive about them all.
Let’s start by reimagining what it means to be proactive. Rather than attempting the impossible, of actively trying to thwart all threats and to cover every attack vector manually, take advantage of the latest technologies, like AI, to do the work for you. The modern CISO needs automation to prevent and clean up malware attempts rather than tasking staff to monitor and sweep up the debris. AI technologies can do more than just offer post-compromise forensic analysis and are capable of preventing endpoint breaches proactively.
Essentially, being proactive means investing in a security layer that exists across the network. Such protection should:
- Support all your existing OSs, including cloud and VDI; attackers are always looking for your weakest link
- Include several types of technologies that can detect in parallel to achieve separate security layers
- Not rely on a person to run it effectively, including threat prevention
- Integrate with other security solutions on your network – able to benefit and provide security data
- Allow visibility of all your assets: a single view of a device is always weaker than a historical view across your network
- Be able to back up your assets, and test that it is working
Summary
Of course, no one has a crystal ball and we can only guess what new innovations malware authors will dream up next to separate users from their data and their money. With that said, the technology at SentinelOne has proven time after time that it is capable of protecting against zero days vulnerabilities, previously unknown malware, and other advanced exploits, often before they have been acknowledged or identified by other technologies.
The reason SentinelOne is unique is that we have implemented multiple layers of protection and visibility, including AI and automation, into a single agent. This provides both comprehensive protection and ease of use that does not require specially-trained ‘knowledge experts’. Attackers have long been aware of the benefits of automation; it’s time defenders used similar means to stay ahead of the game.

