The current conflict between Israel and the Hamas militant group has begun an onslaught of hacktivist-level activity carried out in the name of both sides. Amongst the ongoing fighting, numerous hacktivist groups and ‘lone wolves’ have taken the opportunity to maneuver into the cyber arena, deploying an array of malicious activities including Distributed-Denial-of-Service (DDoS) attacks, cyber defacement, doxxing, and custom malware launches.
So far, the use of novel malware/scareware and tools such as Redline Stealer and PrivateLoader by these threat actors continue to target Israeli citizens, businesses, and critical sector entities, causing data leaks and widespread disruptions. This write-up serves as a roundup of tactics and techniques we are observing in the Middle East, allowing security practitioners to stay informed and on top of developing threats stemming from the war.

Analysis of Data Leaks & Stealers
Haghjhoyan
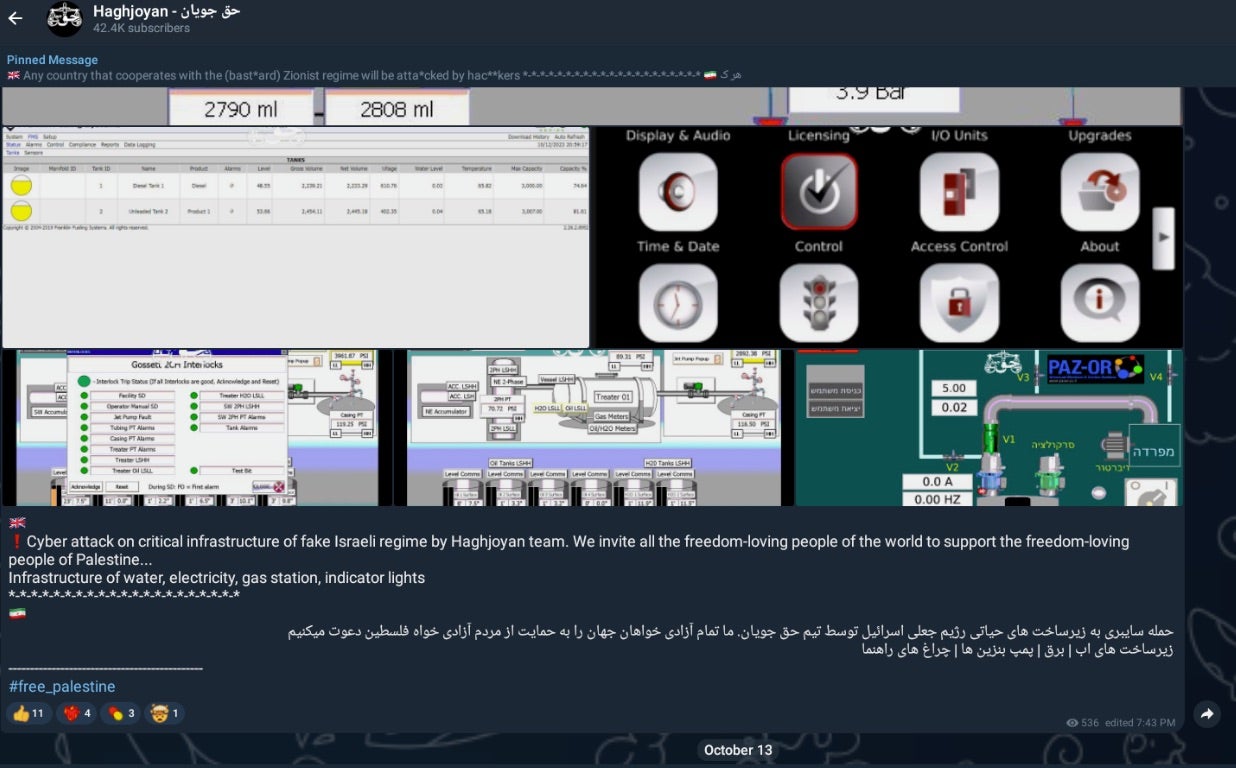
Haghjhoyan, known also as the “Peace Seekers”, first emerged in October 2023. It is characterized as a pro-Iran hacktivist group, which has been leaking small archives of Israeli citizen data through their recently established Telegram channel. On October 8th, the group announced an infiltration of the Israeli Red Alert Emergency System. This was followed by the October 13th, 2023 announcement of the group’s infiltration of multiple critical infrastructure targets across Israel during which Haghjhoyan shared screenshots of their virtual network computing (VNC) sessions in a variety of utility-centric targets. ‘Proof’ files associated with this breach were also shared in the Haghjhoyan Telegram channel.
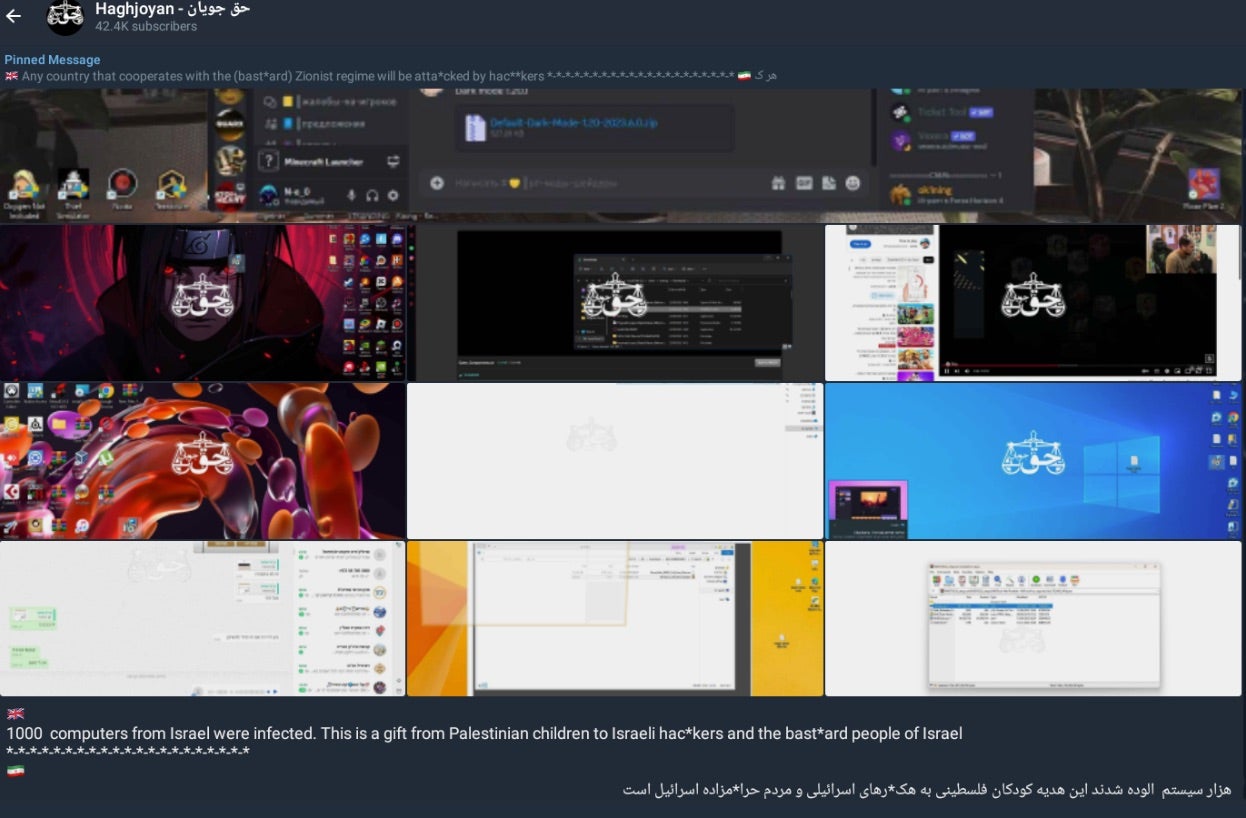
Between October 15th and October 19, 2023, the group continued to announce new leaks and attacks, including the claim of infecting “1000” Israeli computers. The full message shared is as follows: “1000 computers from Israel were infected. This is a gift from Palestinian children to Israel hac*kers and the bast*ard people of Israel”.
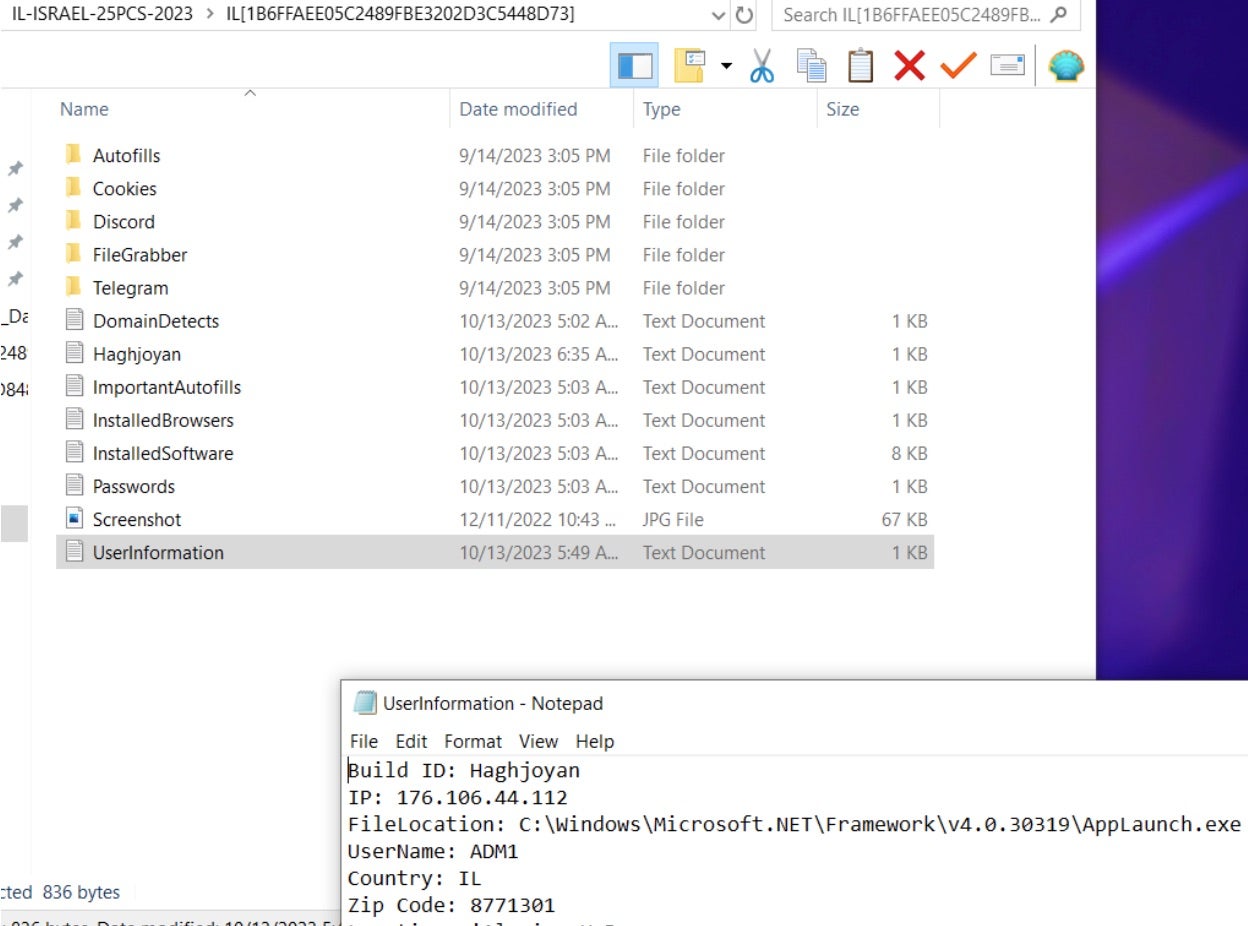
Screenshots shared in the Haghjhoyan Telegram channel show filenames that hold ‘clues’ potentially pointing towards the use of malware. Further, there is indication of potential social engineering lures used by the group to encourage the download and execution of trojanized applications.
In the image above, the following file names are of special interest:
- Frosty Mod Manager 1.0.6.0 (Beta 4) (FIFA 19)
- Subinfeudated Oat.exe
- Default-Dark-Mode-1.20-2023.6.0.zip
The ‘Frost Mod’ and ‘Default-Dark-Mode’ file names are references to the games FIFA and Minecraft respectively. From the data shared by the threat actor, it appears as though they are using these games as social engineering lures, manipulating targets through social media platforms like Discord, Whatsapp, and Telegram into launching trojanized versions of the applications. Targeting users of extremely popular games like Roblox, Minecraft, and FIFA with possible free ‘mod’ packages is an effective way to target a large portion of the general public.
We can also glean some information from the leaked data itself. For example, the stealer log output from the ICS targets contained in the leaked file “IL-ISRAEL-25PCS-2023.rar” is formatted in such a way that may suggest the use of Redline Stealer, or similar malware.
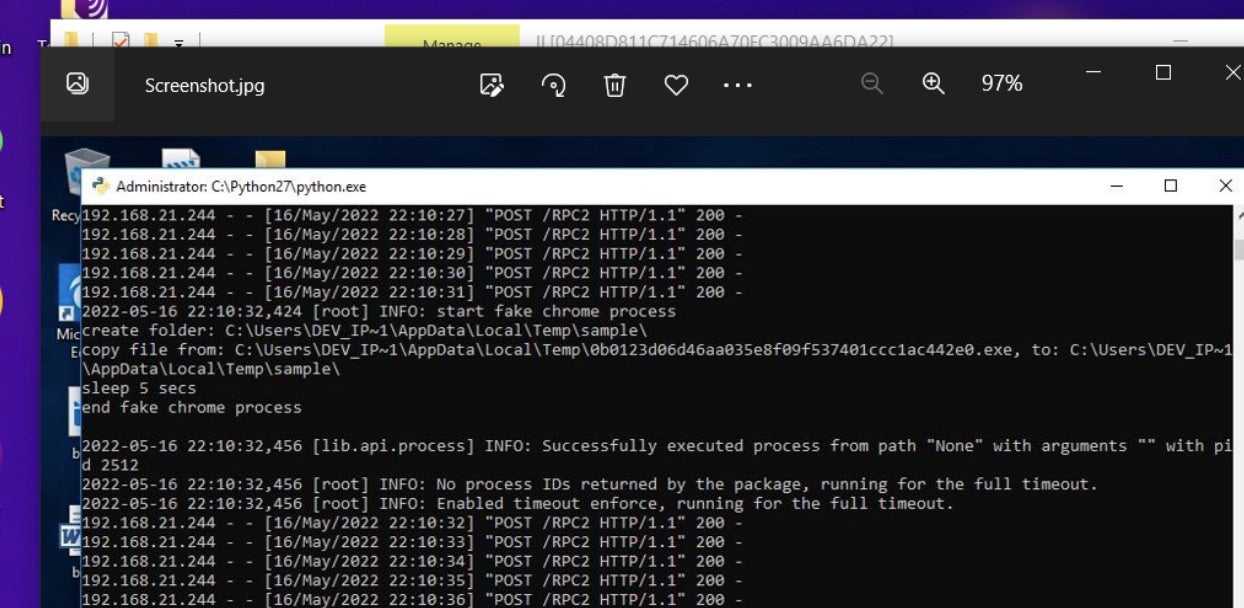
This is further solidified if we look at another leaked screenshot from the threat actors. The following screenshot shows the malware being executed. The file name on the launched executable also happens to be the SHA1 hash of the malware. SHA1 hash (0b0123d06d46aa035e8f09f537401ccc1ac442e0) is a public sample of Redline Stealer originating from 2019 and it is not exclusive to these attacks and campaigns.
In a separately-shared screenshot from Haghjhoyan, there are clues pointing to the use of another malware tool called PrivateLoader.
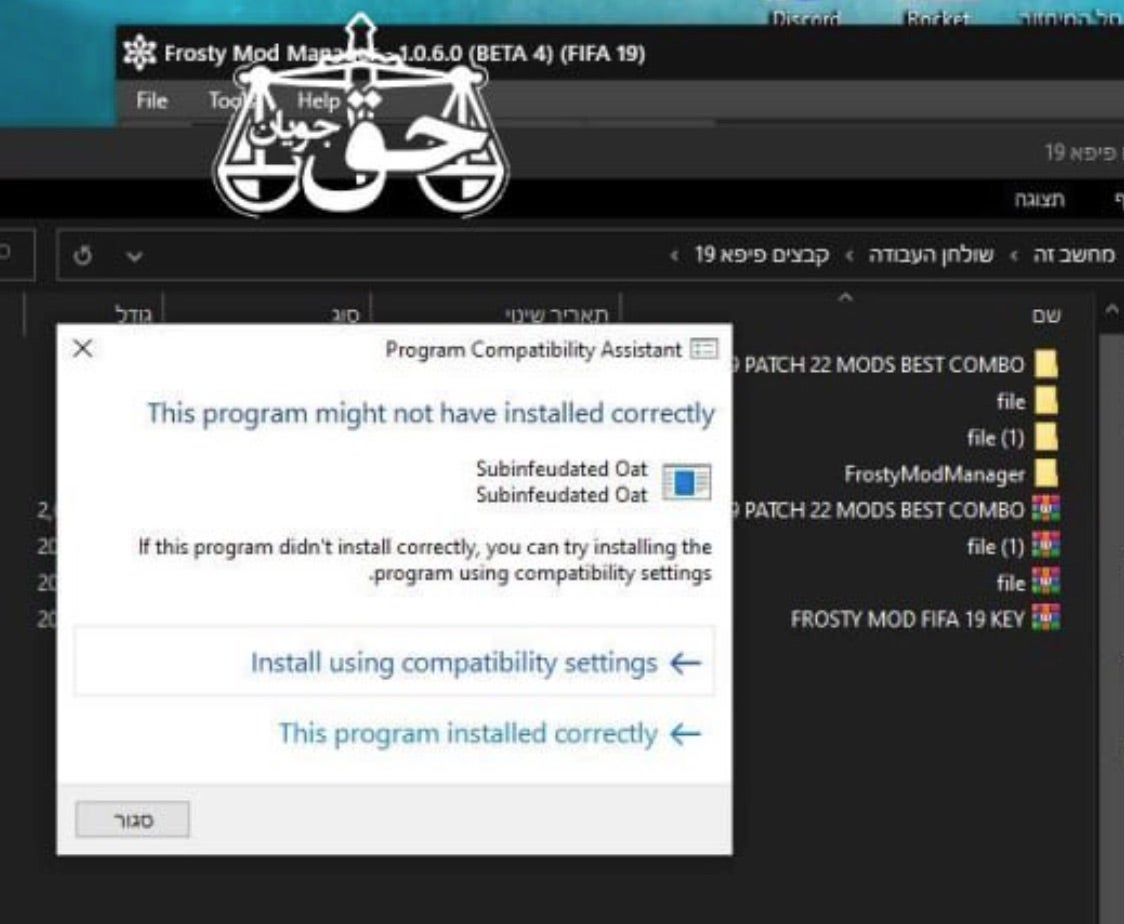
The “Subinfeudated Oat.exe” in the above image is a sample of PrivateLoader. Something of a commodity tool, it is often used as a method to download and launch additional malware payloads. Loaders such as this or Smoke Loader allows lower-tier actors evade basic detective controls like legacy antivirus (AV).
Through these two examples we can tie the use of PrivateLoader and Redline Stealer to these anti-Israel malware attacks driven by Haghjhoyan. Current intelligence indicates that the data being leaked by Haghjhoyan acquired via Redline is fresh and valid, not having been leaked in the wild prior. It should also be noted that Haghjhoyan made their Telegram channel private on October 24th, 2023.
Soldiers of Solomon
Another malicious hacktivist group going by the moniker, Soldiers of Solomon, has also made bold claims around the infiltration and infection of critical infrastructure in Israel. They have also claimed ownership of a customized ransomware called Crucio. On October 18th, 2023, the Soldiers of Solomon announced their attack via the resurrected BreachForums.
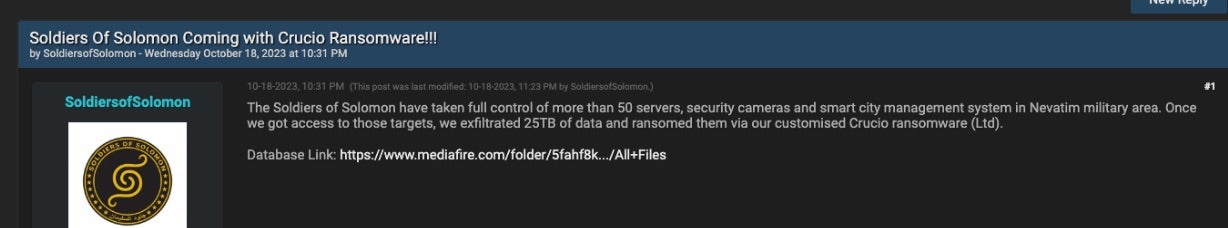
The Soldiers of Solomon also announced this effort via their public Telegram channel. The full message reads as follows: “The Soldiers of Solomon have taken full control of more than 50 servers, security cameras and smart city management system in Nevatim military area. Once we got access to those targets, we exfiltrated 25TB of data and ransomed them via our customised Crucio ransomware (Ltd). Database Link: https://www.mediafire.com/folder/5fahf8k…/All+Files”.
The ‘proof’ package, hosted on MediaFire, consists of the same screenshots provided in their Telegram channel.
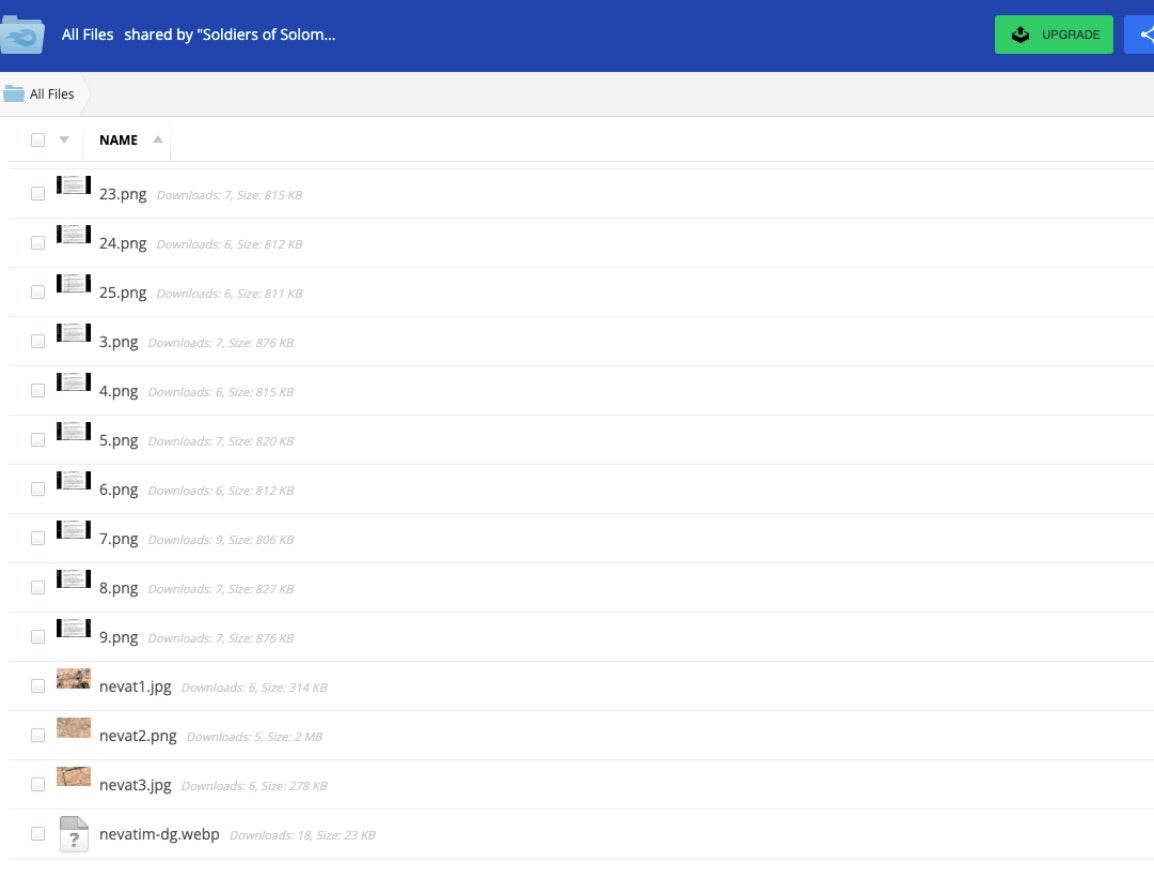
The bulk of these images show a Windows desktop with a document (.jpg image) displayed with the Soldiers of Solomon’s anti-Israeli messaging.
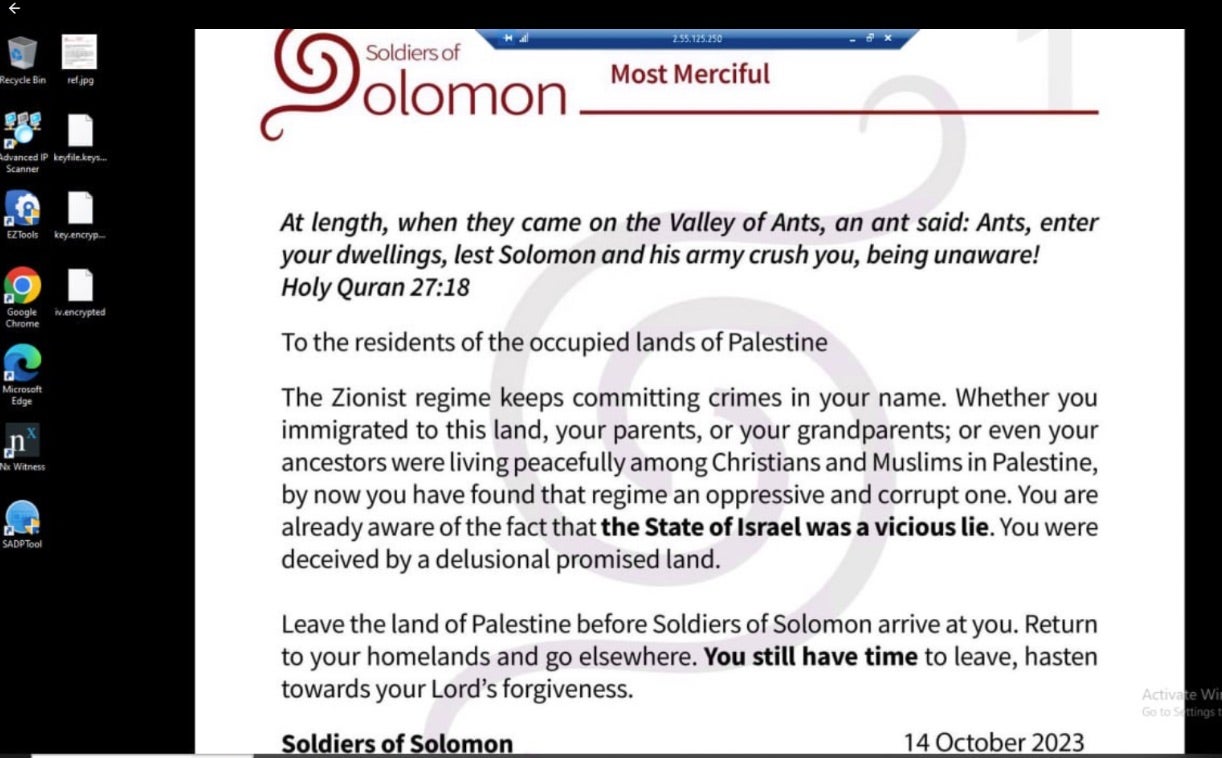
From these images, we can see that the filename for the document displayed is “ref.jpg”.

Analysis of the Crucio ransomware deployment is ongoing and full details are not yet corroborated. That said, we can state that it is not outside the realm of possibility that these groups would repackage an existing or leaked malware builder or kit and use that as a payload to get their message out and cause disruption.
Cyb3r Drag0nz Team
Cyb3r Drag0nz Team is a hacktivist team with a history of launching DDoS attacks and cyber defacements as well as engaging in data leak activity. They are now taking credit for multiple leaks and DDoS attacks against Israeli targets. This includes a DDoS attack against the official website of the Israeli Air Force.
Cyb3r Drag0nz Team claims to have leaked data on over a million of Israeli citizens spread across multiple leaks. To date, the group has released multiple .RAR archives of purported personal information on citizens across Israel.
The Cyb3r Drag0nz Team has been observed taking full advantage of various social media platforms to announce their targeting and intrusions. They post updates via Instagram, Twitter, and Telegram as well as FaceBook and Youtube.
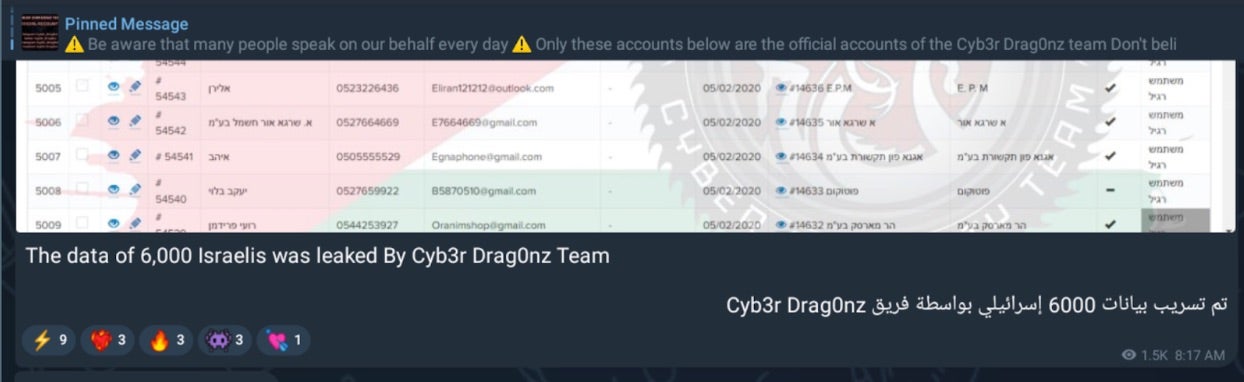
Most recently, the group claims to have stolen the data of more than “1 million” Israeli citizens.
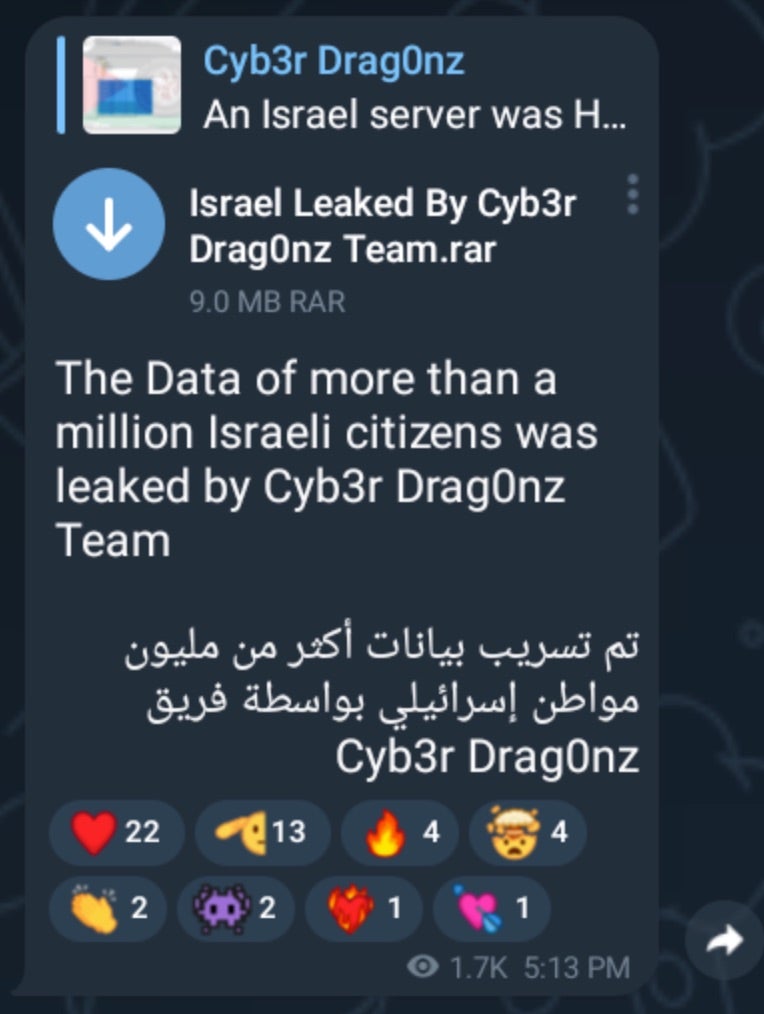
This announcement was accompanied with a RAR archive named “Israel Leaked By Cyb3r Drag0nz Team.rar”. Current analysis of data being leaked by Cyb3r Drag0nz Team shows a varying level of ‘freshness’. Some of the sample leaked data has appeared in prior leaks or dumps from other groups while other data appears to be new.
Conclusion
The hacktivist groups currently active in the Israel-Hamas conflict are ramping up in both intent and skill level. Though these groups are still relatively small, it is clear that they are carrying out successful attacks and putting ordinary citizens at risk. This class of criminal activity is often viewed as being of a lower tier, however, ongoing fighting in Gaza has provided a springboard for these groups to leverage political chaos to further their malicious cyber goals.
We believe that these groups are of relatively low-sophistication and financial resources. The malicious actors’ use of tools like Redline and PrivateLoader speak to their position of having to use what is at their disposal. This is bolstered by the example of using in-the-wild Redline samples with known hashes, revealing that the actors are not making the effort to modify or customize the older malware.
That said, these groups continue to impact ordinary civilians, putting their identity and data at risk to reach their goals. As the war continues to escalate across multiple arenas, these small-yet-effective attacks are expected to only increase.
We recommend the following the best practices that can help strengthen any existing cybersecurity measures:
- Focus on awareness and practice overly-diligent cyber hygiene. Take any opportunity to spread information about basic protection. Be vigilant against unexpected links, practice link validation, and do not engage in any unauthorized chats across popular social media platforms, particularly on Discord, Whatsapp, Telegram, and X.
- Some of the malicious tools mentioned in this post are known to be disguised as mods for popular games. In some cases, we saw FIFA 19, Minecraft, and Roblox being used as social engineering lures. Be aware of this potential lure style and think twice before downloading game mod packages, or take extra precautions when doing so.
- Update all security software and ensure it is properly configured. Use modern and reputable security solutions and software and look out for patches and fixes.
- Monitor all endpoints in your controls, whether at home or in an office, for signs of compromise. Having a robust XDR solution can provide deep visibility across endpoints in a system as well as automated detection and response capabilities.
Indicators of Compromise (IoCs)
Redline Stealer (SHA1)
0b0123d06d46aa035e8f09f537401ccc1ac442e0
PrivateLoader (SHA1)
a25e93b1cf9cf58182241a1a49d16d6c26a354b6
8ade64ade8ee865e1011effebe338aba8a7d931b


