Spending on cybersecurity is growing and, according to Gartner, is expected to hit the $124 billion mark by end of 2019. This creates an incentive for even more vendors to join the race with alternative security solutions. How should one select a product that will answer an organization’s security needs, be suitable for the enterprise, won’t require too many hands to manage, and provide piece-of-mind from cyber threats? IT managers don’t want persistent complaints from users about their AV software, and the business can’t afford a security solution that impacts productivity. If you find yourself selecting security products, here are some of the common pitfalls many buyers make when evaluating them.

1. Overlooking What Users Are Saying
The first major pitfall to avoid is not knowing what the market thinks. If you don’t have the resources to test yourself, see what real customers are saying – the most credible place to check that out is Gartner Peer Insights for Endpoint Protection Products and Endpoint Detection and Response solutions, where you can find a dedicated score and real users comments for both EPP and EDR.
Tip: Go with products with the most reviews on well-established platforms like Gartner Peer Insights. Gartner also publishes an in-depth report on Endpoint Solutions called the Magic Quadrant.
2. Evaluating Without Clear Success Criteria
Success may look different to different enterprises. One might care about supporting legacy devices as they have a long tail of unpatched devices, others may care more about macOS security and visibility while a third may want to ensure the current IT workforce can handle the solution with ease.
Tip: Define your success criteria carefully, so if a vendor meets it, buy it and get all your needs fulfilled.
3. Relying On Claims That Promise the Earth
The cybersecurity market includes many solutions that were designed to solve different problems but to survive some may claim more than they deliver. The result is too many products claim to protect you from any threat, any attack vector, and without any impact on your users. In the midst of all that, there is the buyer, who in some cases needs guidance rather than an all-inclusive pitch.
Tip: Invest some time and define your needs. Then, find the best product that can resolve them.
4. Believing A Breach Won’t Happen To You
For enterprises hoping to safeguard their critical data, the question is not if they are going to get hacked—but when. According to the Verizon Data Breach Investigations Report (DBIR) 2018, 76% of breaches were financially motivated and showed little regard for the circumstances of the victim. EMA’s Security MegatrendS 2019 report, sponsored by SentinelOne, makes the reality even more clear: 73% of respondents have been affected by some form of endpoint attack, and only 58% of organizations are highly confident they could detect an important security incident before it caused significant impact.
Given that the majority of organizations will face a security breach over their lifetime, it is incumbent on organizations to have a fallback position.
5. Expecting It To Solve All Needs
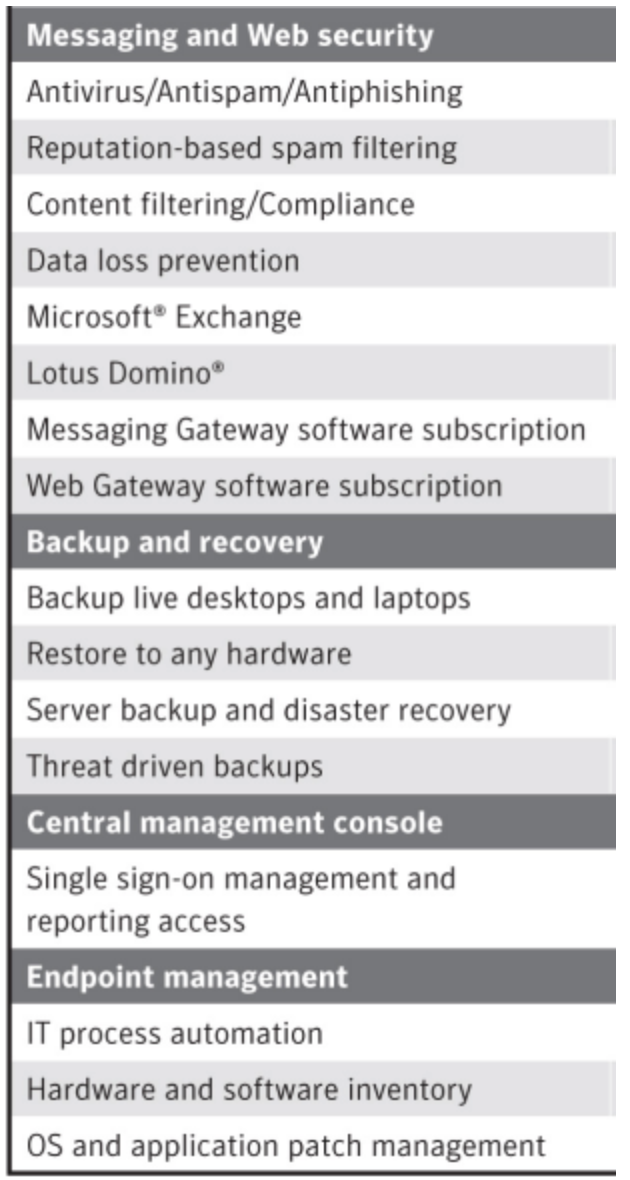
In the spring of 2014, Brian Dye, Symantec’s senior vice president for information security, famously said that AV is dead. In fact, Dye told WSJ that he estimated traditional antivirus detected a mere 45 percent of all attacks. Considering that one data breach is enough, how can it be that Symantec has over 25% of the market share and legacy AV is still sold on the market?
One of the trends that helped these security solutions to survive was to provide additional features. Hence, the “AV Suite” was born. Offering many additional features that address a mixed-bag of IT needs suits these vendors as it makes replacing their legacy AV a complex process.
The “AV Suite” increased the attachment rates for legacy solutions, but do you really want to risk your enterprise with a less effective security solution because it also offers a backup solution bundle? The reality is that some IT needs will not – arguably, should not – be answered by your endpoint vendors.
Tip: Choose a solution that doesn’t compromise on security.
6. Setting an Unrealistic Budget
The lack of efficiency from legacy AV vendors also triggered a reduction in security budgets. If something does not work, why should one pay so much? In the era of zero-trust networks, you can still see cases where the budget for network security is higher than protection for endpoints. Nobody wants to waste money on an ineffective solution.
The question is: can you get an effective solution that won’t keep you awake at night and will secure your most important assets for as little as the cost of a cup of coffee? For a year?
7. Failing To Integrate
Cyber Security is not a one-trick pony. The risks come in different shapes and sizes and staying on the safe side requires more than one product. Network security, emails, access control, logging, and SIEM usually live under the same roof. If your security products do not talk to one another and cannot contribute to each other’s efficiency, that’s a bad sign. What you want is a solution that can integrate with all the parts of your security apparatus, making each more effective. For example:
- When your firewall gateways determine a file as malicious, you want to immunize your endpoints from it, as they are not always behind a firewall.
- When the endpoint solution identifies a bad URL, you want to block it across your gateway protection.
- When malicious activity is detected, you want to consolidate all the related information from all your security products to ease the process of identifying the impact and implementing the steps to follow.
For all that to happen, you need solutions that can be automated and which have APIs to facilitate that. There are two basic approaches vendors takes in regards to APIs:
- Build the product first, see it mature and then scramble to implement API calls at the request of customers. Ad hoc approaches like this typically lead to bugs.
- Build the APIs and the product on top – this way, all APIs are working and functioning, are constantly updated with new capabilities, and the overall integration gives you the means to automate everything.
8. Testing Only File-based Malware
There’s more to modern malware than just malicious files. In the early days of viruses, most malware came in the form of executables, and malware authors needed to use social engineering techniques to trick users into running them. Such techniques are widely used even now and are still a highly effective way to compromise devices. However, malware authors have found ways to get code running without having to trick users. As a result, a growing number of malware campaigns are now file free, either using lateral movement techniques or sometimes documents running macros. This is expected to grow due to the effectiveness of such techniques to compromise at scale.
9. Testing Only Known Malware
There is a difference between downloading a piece of malware from a public source and malware that has never been seen before. When testing known malware, consider that any security product can run a query against public repositories like VirusTotal and return those results as their own, so detection of known malware is a low barrier for a product to pass. Testing malware that is unknown may indicate that this solution can handle novel threats that may be seen in the future.
The challenge starts when you want to find such malware to test, as samples by definition will not be publicly available, and most enterprises don’t have cybersecurity experts to create their own proof-of-concept malware.
The little secret here is that most reputation engines rely on the exact hash of a file. What is a hash? A digested footprint or signature that represents a file using algorithms such as MD5 or SHA. The nature of a hash is that no two non-identical files should resolve to the same hash, so if a security product deems a file to be malicious by its hash, there is no risk of blaming a benign file and producing a false positive.
For security engines that rely on hashes, there’s an easy way for adversaries (and product testers) to produce fresh malware samples. If you download a file-based malware, it’s enough to append a single char to the end of it, and… you got a new hash, a malware that is “unknown” to reputation services like VirusTotal and others.
Tip: Modifying a file’s hash is a good way to differentiate between solutions relying on signatures and those using behavioral AI (changing the hash should not affect AI detection).
10. Skip Testing Benign Applications
Another mistake to avoid is assuming that a candidate solution will recognize all your company software as safe. Let your IT users run a candidate solution on their devices as well as run it on your own. It is not uncommon for large enterprises to run their own software, sometimes even signed by a valid certificate authority. Then you can really see what the solution is worth. No one else is knowledgeable of your network as your own employees.
11. Trusting Samples from Security Vendors
Every security software on earth can be programmed to block specific files, malicious or not. If you take samples from a vendor, and magically find that they are the only ones who detect it, beware. Samples tailor-made to be detected by a single engine are easy to create, and a good sign that your prospective vendor may not be trustworthy.
12. Not Testing With Real-World Deployment Settings
Feasibility tests usually involve some malware testing, comprising of test criteria and a review by IT and the cyber experts in the organization. Cyber experts will try their most advanced scenarios, but you should remember that the solution will be enabled on all your devices, on all your users, all of the time. While protection is the most important aspect of implementing endpoint security products, your users must be able to work with it without interruption and be able to do their jobs.
So, while a test may look impressive when everything is set to trigger alerts by default, will your organization be able to live with those settings on a daily basis. It’s fairly easy for a product to prevent malware when it’s set to its strictest settings. Everything that is new, or running from the downloads folder or unsigned can just be blocked from running. But such strict policies aren’t always suitable for an organization’s day-to-day needs and can lead to a negative impact on productivity.
As vendors want you to test their solutions and are incentivized to meet your requirements, they might be willing to offer some public repository links. As long as they are not links to files created by the vendor themselves, that’s a good sign of the integrity of that vendor.
13. Counting On The Number Of Alerts For Success
A solution that overwhelms you with hundreds of alerts for a single attack isn’t effective or usable. The idea that more alerts equal more security is a misconception. Ask Target, who suffered a major breach while an alert was hiding in a pile of others, and as such remained undetected for over 120 days.
There’s nothing worse than drowning in alerts and not being able to see real threats through the noise. Do you want hundreds of alerts for one attack or one alert that shows you the hundreds of linked processes? While detection is cheap, prevention will take its toll as your IT team struggle to piece together the whole attack story.
Tip: invest in positive testing. How will the solution work in the day-to-day running of your organization? How will it fit in with your IT team’s workload and practices?
14. Overburdening Your Current IT Team
Managing Cyber Security products can be a real pain. People need to be trained, understand all the bells and whistles and learn how to manage the solution effectively in the context of your organization. In fact, the complexity of managing such solutions causes some products to have a blank policy, just to avoid the hassle of managing it, and that is dangerous.
Tip: Look for a solution that you can manage with your existing team, which can be deployed quickly and does not require much training.
15. Overlooking Ongoing Maintenance
Antivirus signatures, MS updates, and all the ongoing maintenance can be painful, especially if your organization is not using a single image. Different OSs add more dimensions to the complex task of keeping everything up to date and take their toll on your IT staff members.
AV solutions that require user interaction to perform updates or download emergency patches doesn’t contribute to effective problem management. Installing buggy patches can also result in disruptions and lost productivity, and may require yet more intervention from your IT team.
Tip: Look for solutions that have a consistent upgrade cadence and which can self-manage maintenance from the cloud.
Conclusion
Evaluating security software isn’t easy, and there are no shortcuts to ensuring you get the right endpoint detection and response product that will fit your organization’s needs, staffing levels, and budget. Buying “off-the-shelf” is sure to lead to headaches down the line. The key to everything we’ve said here is to do your own research and do your own tests. Treat vendor claims with a healthy dose of skepticism until you’ve proven them in your own real-world setting.


