TxHollower is a loader-type malware that has been found to deliver a variety of payloads including AZORult, FormBook, GandCrab ransomware, LokiBot, NetWire, njRat, Pony, Remcos backdoor and SmokeLoader. Infections attributable to TXHollower have been occurring since early 2018 and have been rising rapidly thanks in part due to TXHollower’s ability to avoid some vendors’ security solutions. In this post, we take a look at TXHollower and give it a spin on one of our endpoints.

What is TxHollower?
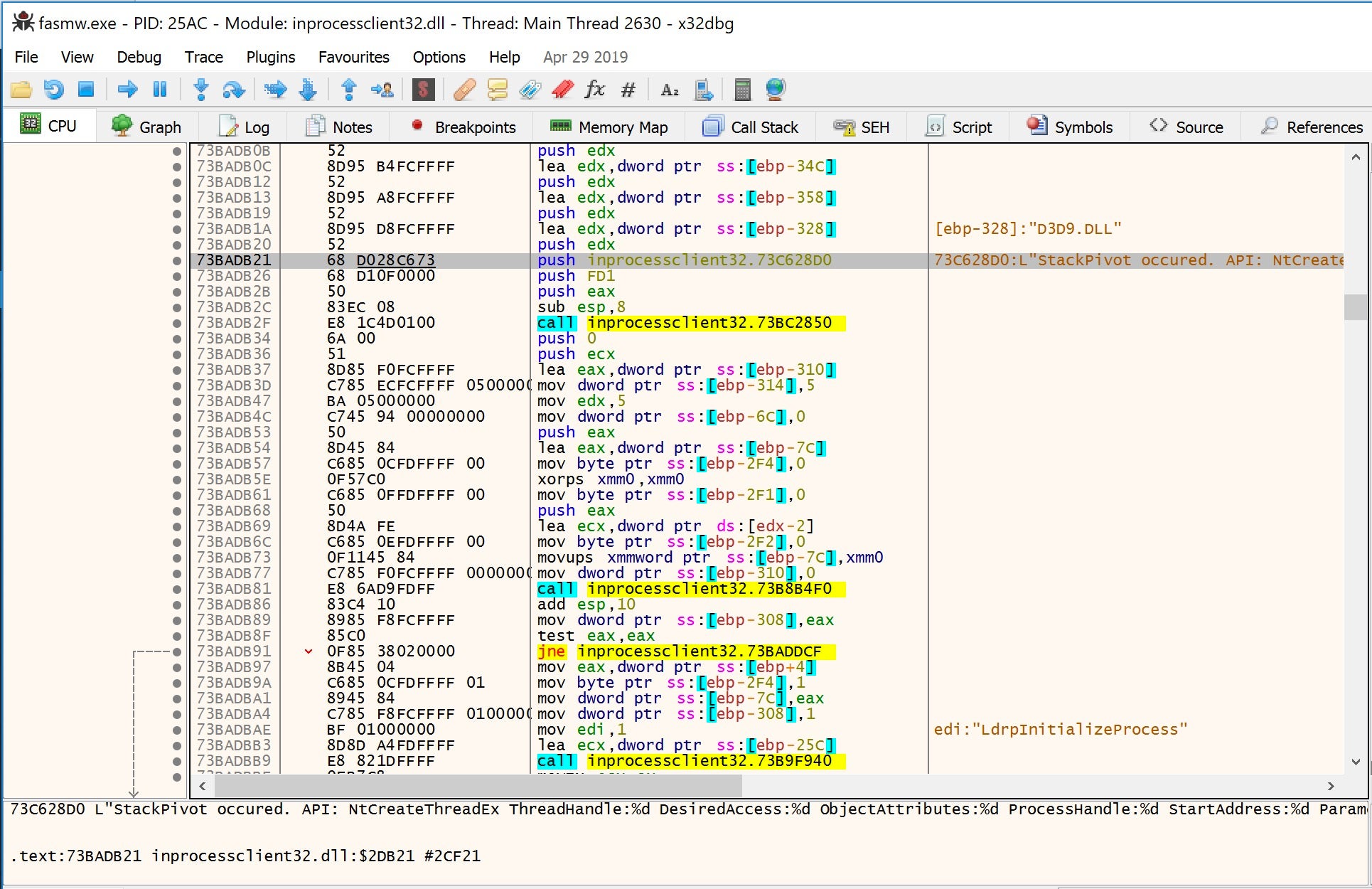
TxHollower leverages Windows’ deprecated Transactional NTSF APIs (TxF) to perform Process Doppelgänging and Process Hollowing, two related threat actor techniques that make it possible to inject malicious code into memory by replacing that of a legitimate process.
Process Doppelgänging also allows TxHollower to avoid detection by some security solutions that over rely on monitoring particular system calls known to be abused by malware such as SetThreadContext and NtUnmapViewOfSection. Instead, TXHollower makes use of lesser known Transactional calls like NtCreateProcessEx and NtCreateThreadEx to perform tricks like stack pivoting to control the flow of program execution.
As a loader rather than a dropper, TxHollower carries encrypted versions of second-stage malware within its own executable, removing the need for calling out to a C2 server to obtain the payload. Loading in this way also serves to avoid another possible failure point for a malware infection. Once C2 IPs are seen in the wild, vendors will quickly update their definitions to alert on those known malicious IPs. TxHollower cuts off this avenue of detection by carrying the payload, which may be ransomware like GandCrab or a remote access trojan like Remcos, within the first stage infection executable file.
Why is TxHollower On the Rise?
Researchers agree that samples of TxHollower found in the wild are unlikely to be from the same origin, in part because of the wide variety of payloads being seen, which suggests different kinds of threat actor objectives and campaigns. Rather, it looks as if the loader malware is being distributed in criminal circles to multiple actors, possibly sold as part of an exploit kit or framework. It’s also been noted that there are a number of variants of TxHollower itself with slightly different configurations and capabilities.
As TxHollower appears to be in use by various actors, that likely explains why no single infection vector has been identified. There has been some suggestion that malicious Word documents expoiting CVE-2017-11882 in Microsoft Office’s Equation Editor may carry the loader malware. As is common with attacks that rely on poisoned documents, these may be associated with fake invoices and receipts.
Can TxHollower Be Detected?
As we’ve noted, TxHollower has been crafted to avoid some security solutions by using lesser known API calls and by carrying an encrypted payload to avoid calling out to a C2 server. Despite these tricks, when we ran a sample on a SentinelOne-protected endpoint, the agent immediately alerted on the threat, both pre-execution and on-execution.
SHA1: f4f56f7830fc71658ddc90f8b39de6fac656682d
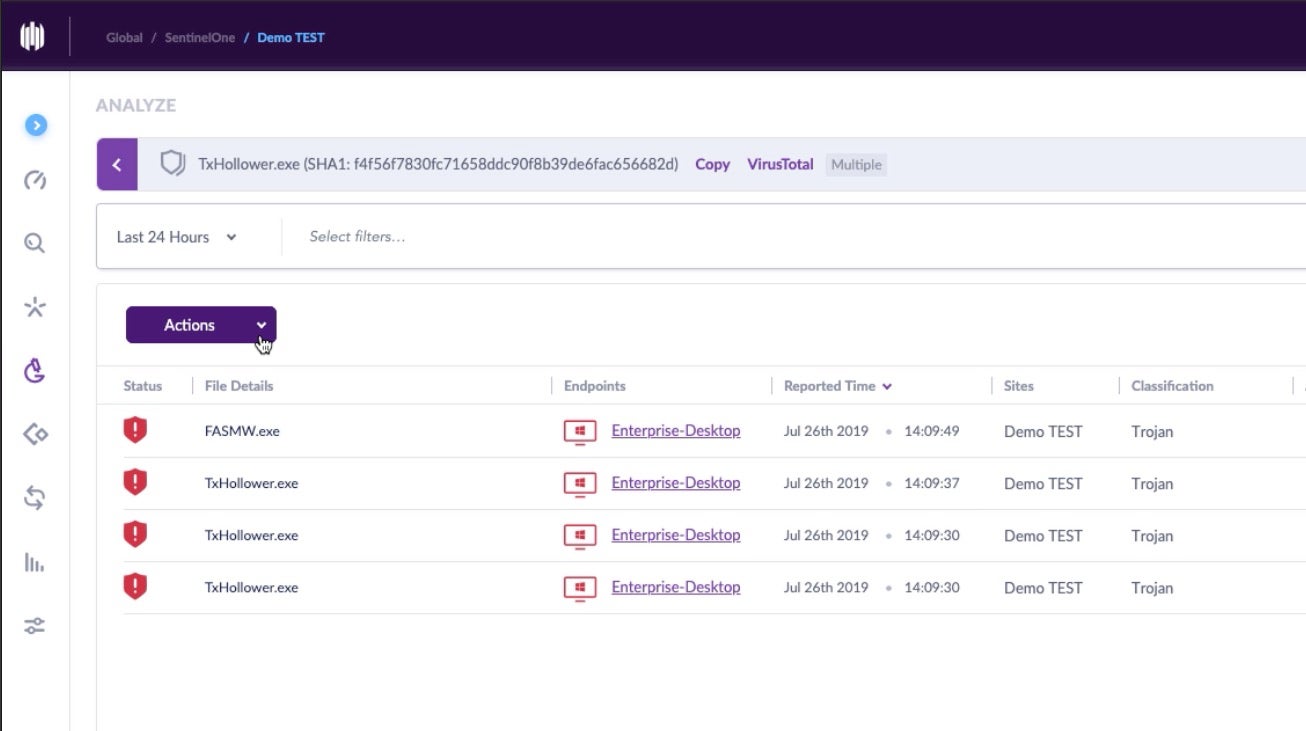
For the purpose of the demo, we set up the agent so that it would alert only in order to observe the malware in action. In a real-life deployment, the Protect policy would alert and block the malware from executing. After testing the malware and observing the detection in the management console, the admin was able to simply remediate the threat remotely to clean up the infected endpoint and return it to a healthy state.
If you’d like to see the full demo in action, check out the video below.
Conclusion
TxHollower is a threat to enterprises that are not sufficiently protected by a security solution that can detect in-memory, fileless malware using process injection techniques. The malware appears to be used as a loader for a variety of threats from ransomware to backdoor trojans and banking malware such as Osiris and Kronos. If your business is not yet protected by SentinelOne’s active EDR solution, contact us for a free demo and see how it can keep your organization safe.


