Tensions between Greece and its neighbor, Turkey, are nothing new. Conflict in the Aegean extends back to the days of Homer, who described how a Greek army decimated the town of Troy, located near Hisarlik in Turkey. The animosity between these nations may date centuries into the past, but the weapons and tactics used in the conflict today are cutting edge cyber tools.
Greece and Turkey are now engaged in a diplomatic conflict focused on the maritime boundaries surrounding the Greek island of Crete. The row comes after Turkey and the Libyan government agreed to seek to map out a boundary that would potentially reduce Greece’s maritime territory. This conflict raises patriotic tensions on both sides, some of which have become manifest in cyberspace.

Turkish “hacktivists” last week claimed responsibility for cyber attacks on Greek government sites, including those of the Greek National Intelligence Services (EYP), Greek Parliament, the Greek Ministry of Foreign Affairs and the Greek Ministry of Finance among others. Turkish hackers AnkaNeferler said these were in retaliation for the Greek government’s stance on the Turkish agreement with Libya (the Turkish government is providing military support and plans to send its military troops).
Meanwhile, Greece is furious at the pact between Turkey and Sarraj’s government as it threatens to skim the Greek island of Crete, which Greece and its allies say is contrary to international law.

Greek hackers have not stood idly by. According to different reports, a group called Anonymous Greece retaliated with a cyber-attack of their own just hours after the original Turkish attack.
“As the Turks hit yesterday, so do we the day after in response. Let it be known that the attacks have just begun. For every new attack, we will posting a new article. We will now show what we have hit in a matter of hours“, wrote Anonymous Greece on their website.
The list of Turkish websites that have been hit:
- 112 Emergency Call number
- Sabah Email Service
- Hurricane Email Service
- 112 Emergency Email Service
- Turkish Police (EGM) Email Service
- Saglik Email service
- Economics Email service
- Enerji Email service
- SIP-VOIP of Turkish Energy
- MIT Email service
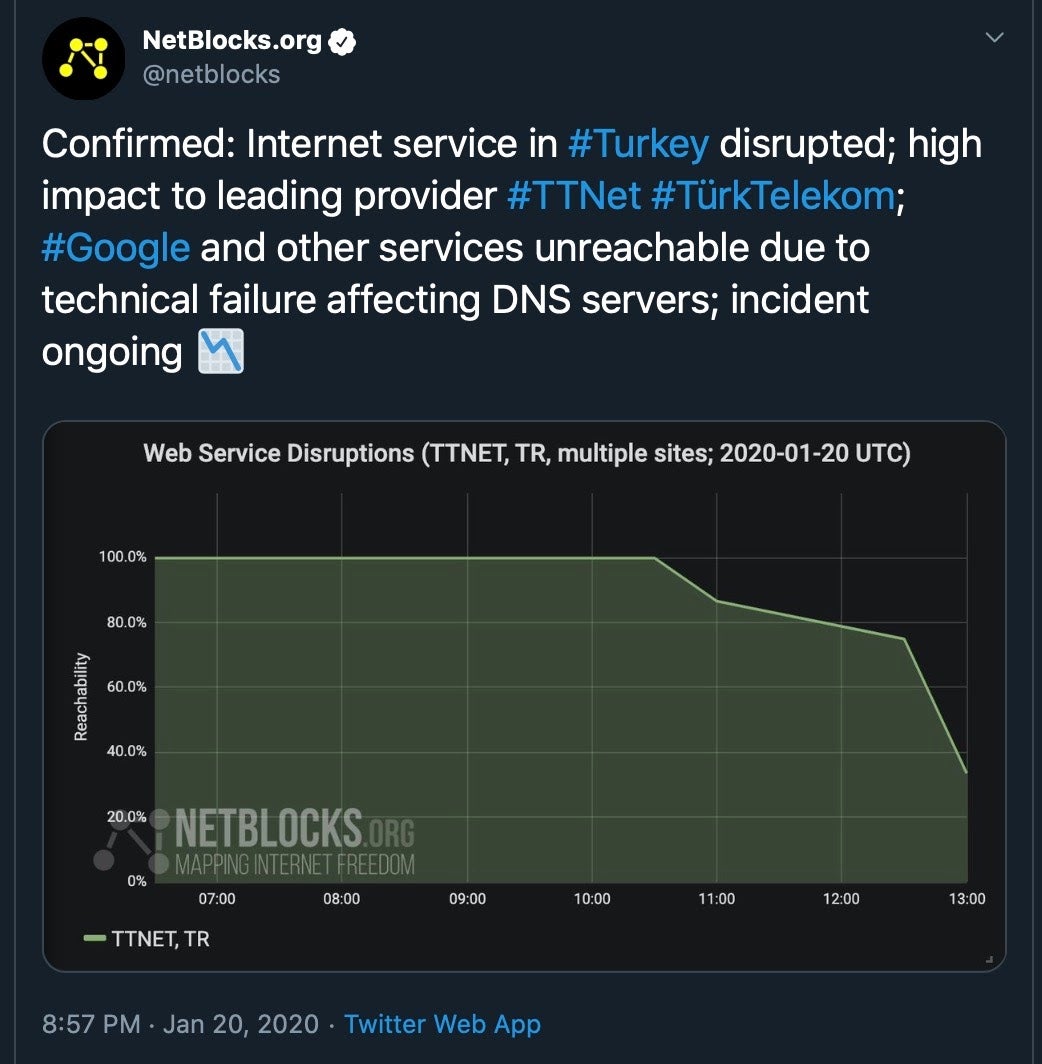
But these attacks were rather insignificant in comparison to what happened next. Yesterday, it was reported that Turkey’s telecommunications giant Türk Telekom was hit by a cyber attack that caused hours-long problems with Internet access throughout the country.
Who’s Doing What?
It is unclear at this point if any of these attacks had any affiliation to the authorities on either side. It is also unclear what type of attacks have occured. The first attacks were thought to be DDoS attacks, then DNS hacks, but it seems that at least some of these attacks included one or more malware infections. According to sources, all Greek embassies and diplomatic missions such as Consulates faced major communication problems as the server of the Ministry of Foreign Affairs went down for several days.
What Should Enterprises Do?
Given the nature of these conflicts and the way businesses operate today, it is highly conceivable that hostilities won’t stop any time soon and that some enterprises will be hit as collateral damage. And while there is not much an enterprise can do if an ISP (Internet Service Provider) service is disrupted, there are many things it can do to reduce risk.
Past conflicts have demonstrated that as long as these conflicts last, more juvenile hacking groups enter the game and try to wreak havoc on the opposing nation’s side. In the process, they target anything and anyone they can (as long as these are affiliated with the opponent’s flag). They also utilize much more common tools and techniques, looking for quick psychological wins. So the the best way to reduce the risk would be to ensure that standard defenses are all intact.
Disable unnecessary ports and protocols. A review of your network security device logs should help you determine which ports and protocols are exposed but not needed. For those that are, monitor these for suspicious, command & control-like activity.
Log and limit the use of PowerShell. If a user or account does not need PowerShell, disable it via the Group Policy Editor. For those that do, enable code signing of PowerShell scripts, log all PowerShell commands and turn on Script Block Logging. Learn more from Microsoft.
Set policies to alert on new hosts joining the network. To reduce the possibility of rogue devices on your network, increase visibility and have key security personnel notified when new hosts attempt to join the network.
Backup now, and test your recovery process for business continuity. It is easy to let backup policies slide, or fail to prove that you can restore in practice. Also, ensure you have redundant backups, ideally using a combination of hot, warm and/or cold sites.
Step up monitoring of network and email traffic. The most common vectors for intruders are unprotected devices on your network and targeted phishing emails. Follow best practices for restricting attachments via email and other mechanisms and review network signatures.
Patch externally facing equipment. Attackers actively scan for and will exploit vulnerabilities, particularly those that allow for remote code execution or denial of service attacks.
Conclusion
It’s too early to predict where this cyber conflict is heading. It is possible that we’ve seen the apex of offensive activities, or perhaps it is only the beginning. Regardless, enterprises, organizations and individuals face increasing risk of becoming accidental victims caught in the cyber crossfire of this conflict. CISOs are advised to take precautions as to minimize this risk.