DNS hijacking is a cyber attack that redirects users from legitimate websites to malicious ones. This guide explores how DNS hijacking works, its potential impacts, and strategies for prevention.
Learn about the importance of secure DNS configurations and monitoring. Understanding DNS hijacking is essential for safeguarding online assets and protecting users from phishing attacks.
 Refresher: What’s DNS Again?
Refresher: What’s DNS Again?
The world of cybersecurity is complex, so here’s a quick reminder of the terminology we’re dealing with. DNS or Domain Name System is the means by which a human-readable domain name like, say, www.yourcompany.com gets turned into the numerical IPv4 or IPv6 number system that is actually used by browsers, routers, and servers to serve up web and email content.
The older IPv4 addresses are the familiar 32-bit addresses you have likely seen before, consisting of four segments separated by periods. For example:
168.192.1.1
The newer IPv6 addresses are 128-bit addresses written in hexadecimal, split into 8 segments and separated by colons, which may look something like this:
a8:c0:00:00:00:00:01:01
But also may not! In IPv6 addresses, a double colon can be used to omit sequential zeroes, and zeroes at the beginning of a segment can also be removed, so you can see IPv6 addresses that have quite variable lengths. The above address would actually be represented like this:
a8:c0::1:1
So how does all this magic happen? How do domain names become IPv4 and IPv6 numerical addresses? When your browser or other networking device is given a domain name, a process of DNS lookups occurs, starting with local caches and progressing through a number of lookup servers: recursive resolvers, root nameservers, top-level-domain servers and authoritative nameservers. At the end of this process, an IP address is delivered to the client for the specified domain.
What is DNS Hijacking?
At any one of these points, and indeed at any of the caches along the way, an attacker can hijack the DNS server or poison the cache in a way that is invisible to the client making the request.
If you don’t manage your own DNS, it’s entirely possible that the third-party entity that does manage it for you (and who is that, again?) could have been hacked without your knowledge. When an attacker hijacks your DNS, they are able to intercept your entire web traffic and email communications.
“half of the top 20 banks ranked by total assets don’t manage their own DNS, instead leaving it in the hands of a potentially hackable third party.” (Source)
There’s a few ways that this can happen. Suppose you registered your site with an internet registrar, I’ll use a fictional one, let’s call it GoMummy.com. The GoMummy registrar sells you a domain name, yourcompany.com and registers that name against unique IPv4 and IPv6 addresses. Your domain name has the top-level domain (TLD) of .com, and there’s an authoritative nameserver that holds an A-Record containing your unique IP address.
In this scenario, an attacker might hijack your DNS at several points. If they compromise the authoritative nameserver, they could change your IP address to another address so that the DNS lookup for yourcompany.com points to their own servers. Then everyone who typed yourcompany.com into a browser would go to the attacker’s website and not yours. There, your visitors might find a site that is an exact clone of your site, except it’s controlled by the attackers and could be used to steal login credentials, deliver malware or distribute false and damaging information about your company. In such a case, you might have around 4 hours – the time-to-live for a DNS lookup is typically 14400 secs – to spot and correct the hijack before it starts propagating across the internet.
Real-World Cases of DNS Hijacking
Some real-world cases of DNS hijacking include:
- The 2018 SamSam ransomware attack: In this attack, hackers targeted several US healthcare organizations, using DNS hijacking to redirect traffic from legitimate websites to malicious domains that delivered ransomware payloads.
- The 2019 Cloudflare DNS hijacking: In this incident, hackers used a vulnerability in Cloudflare’s DNS infrastructure to redirect traffic from several websites, including coinbase.com, to a malicious domain that delivered a cryptocurrency mining payload.
- The 2017 Exim vulnerability exploit: In this incident, hackers exploited a vulnerability in the Exim mail server software to gain control over the DNS records of several hosting providers, allowing them to redirect traffic from legitimate websites to malicious domains.
Hijacking A-Records appears to be what happened in an attack that affected Twitter, the New York Times, and the Huffington Post. What these sites had in common was the same registrar: Melbourne IT. Hacker collective S.E.A. breached their US-based sales partner through a spear-phishing campaign and gained access to the registrar’s servers. From here, the hackers were able to change the A-Records of several sites.
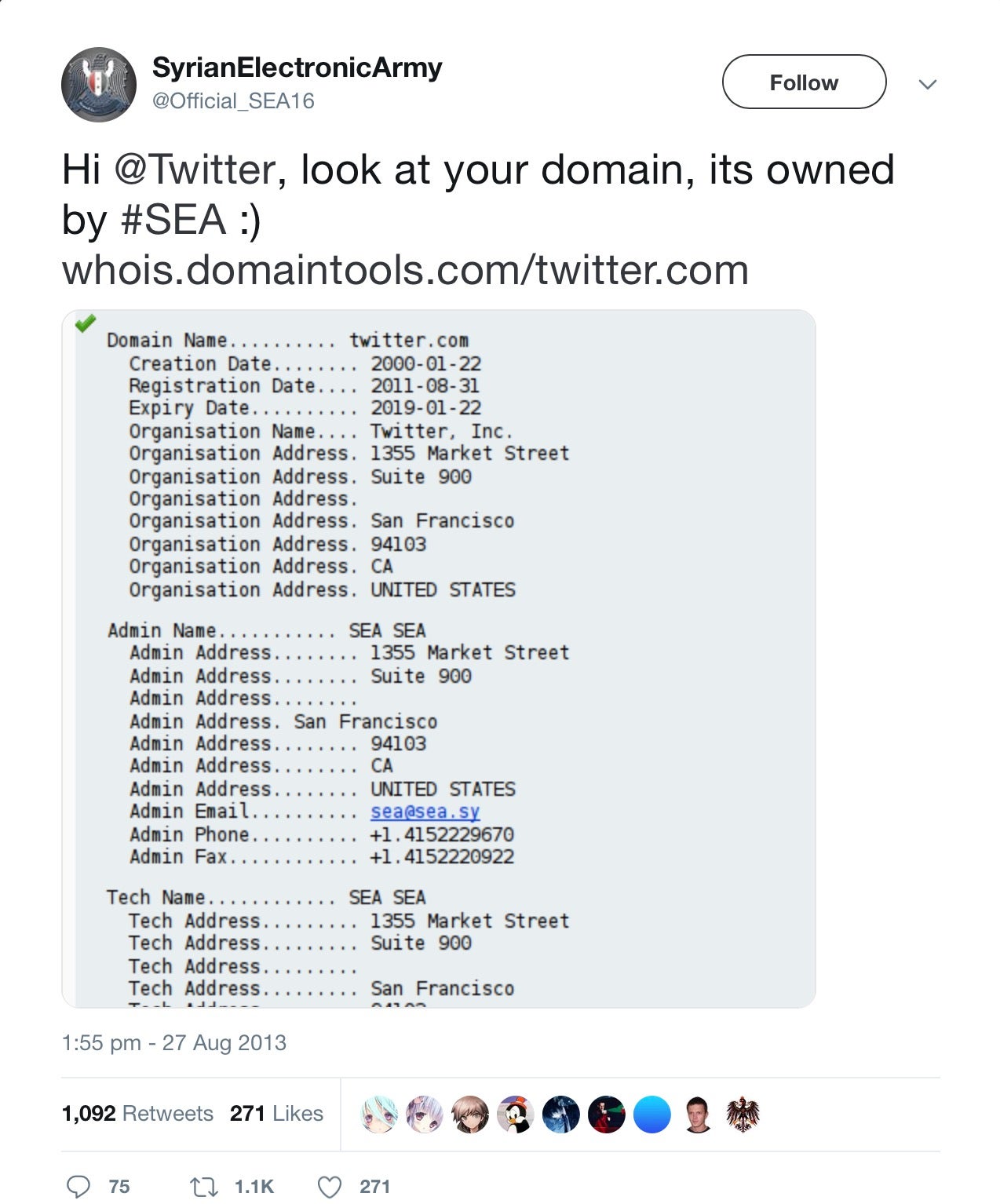
In that particular case, the damage was little more than vandalism, but an attack on the DNS registration of a Brazilian bank was far more serious. The attackers created malicious clones of the bank’s sites, complete with valid https certificates, and had control for around five hours. During that time, every visitor to the bank’s URLs was redirected to the spoofed sites, which also served up banking trojan malware.
More recently, the Sea Turtle campaign appears to be a nation-state-backed DNS hijacking campaign that spans 13 countries and has targeted at least 40 public and private entities. The threat actors behind Sea Turtle’s use changed A-Records to reroute victims to spoofed sites where they then steal login credentials.
DNS Cache Poisoning Attacks
In another scenario, an attacker might not be able to compromise your DNS registrar’s A-record but might instead hijack your DNS through a cache poisoning attack. A rogue or compromised DNS server in-between the user’s computer and the site the user intends to visit could serve up an alternative address to the actual address held in the A-Record.
This, in effect, is exactly the same technique that is used by censors such as the “Great Firewall of China” and other government anti-privacy schemes; it is also a ploy regularly employed by some ISPs to impose geographic restrictions, serve ads, collect data or otherwise control user’s internet browsing.
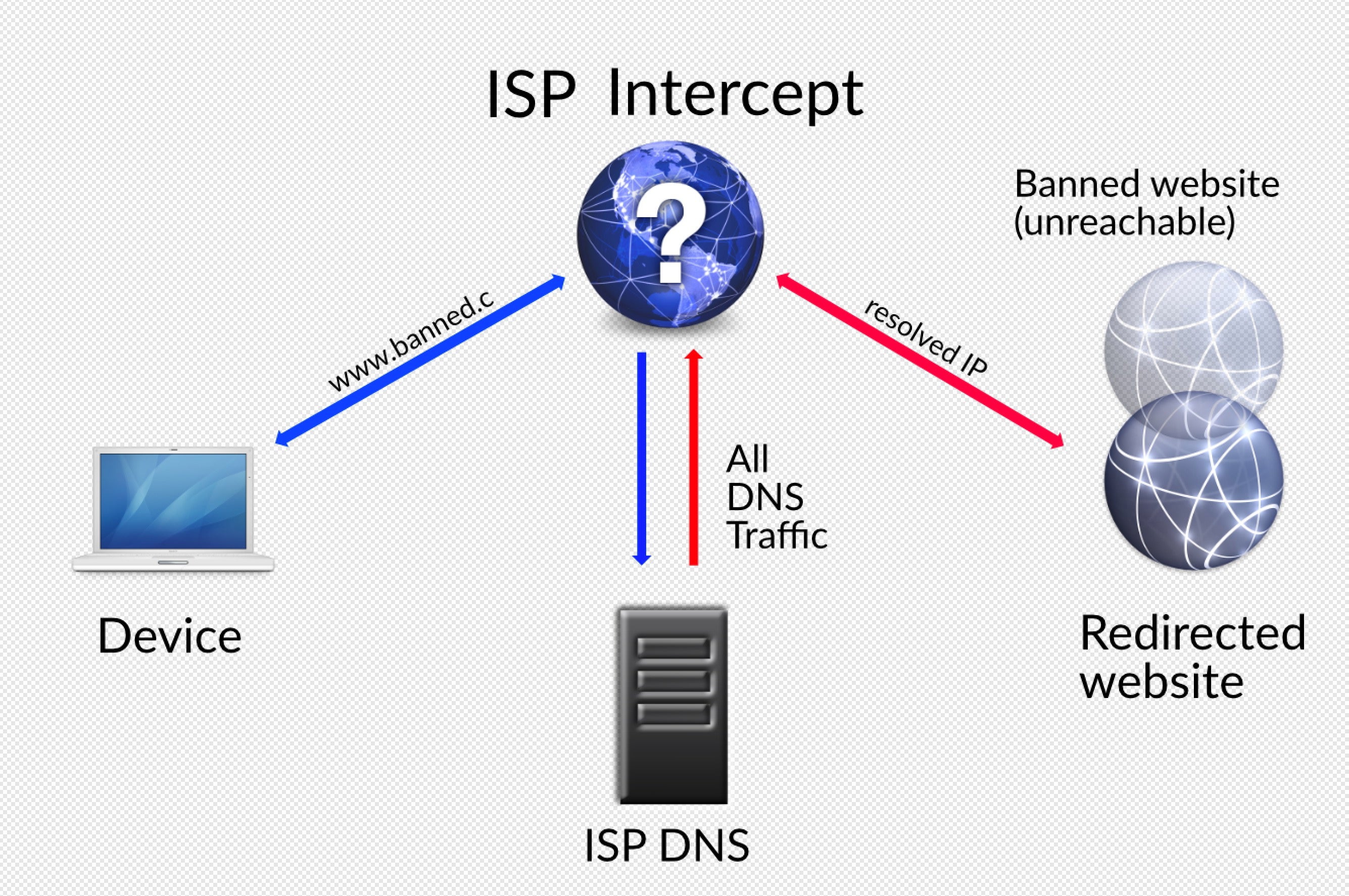
In practice, any DNS caches or lookup servers between the device and the intended site can redirect the user to another address. This can start with the router on the local network – one of the many dangers of using public Wifi services – and reach up to the root name server (aka ‘DNS root server’).
Router & Malware DNS Hijacks
In the above examples, we discussed attacks outside a network you control, but DNS hijacks can also occur inside your network. Malware on a local computer can change the DNS server used by the client, such that a particular machine’s domain names are incorrectly resolved to an attacker’s choice of IP. Similarly, if threat actors can breach the router on your network and change the lookup server addresses there, they can achieve the same effect for every client on that network from a single breach.
One of the easiest ways malware poisons a device’s DNS lookups is to modify the machine’s hosts file. The hosts file has legitimate uses for, among other things, web development, content blocking and VM software, but it also allows attackers to specify custom IP addresses for any domain.
How Can You Tell If Your DNS Is Hijacked?
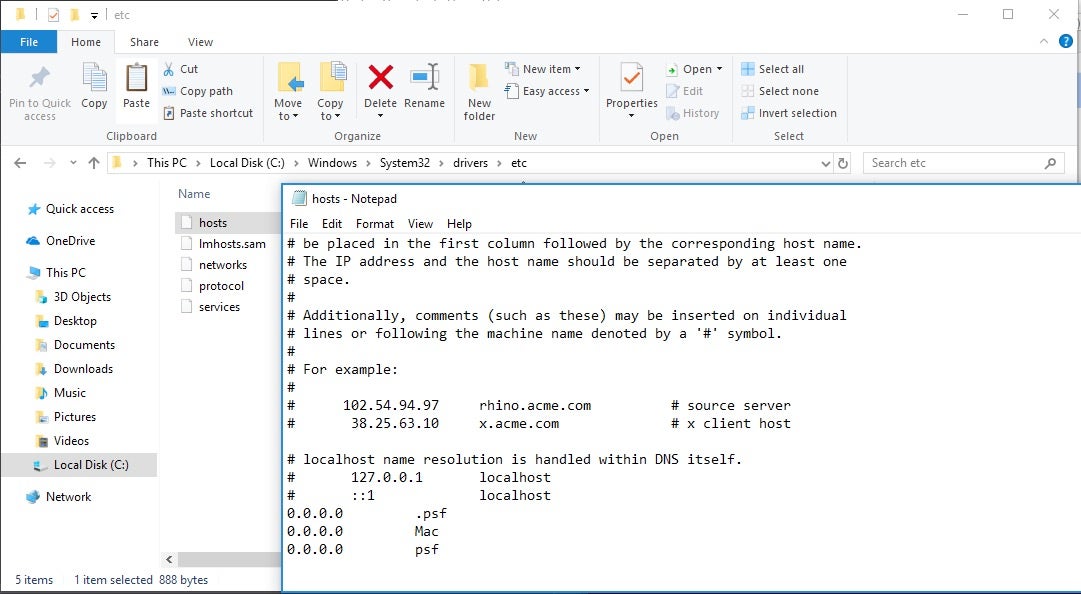
You can and should view the contents of your hosts file regularly. In Windows, you can examine the hosts file using notepad and navigating to the file at C:windowssystem32driversetchosts.
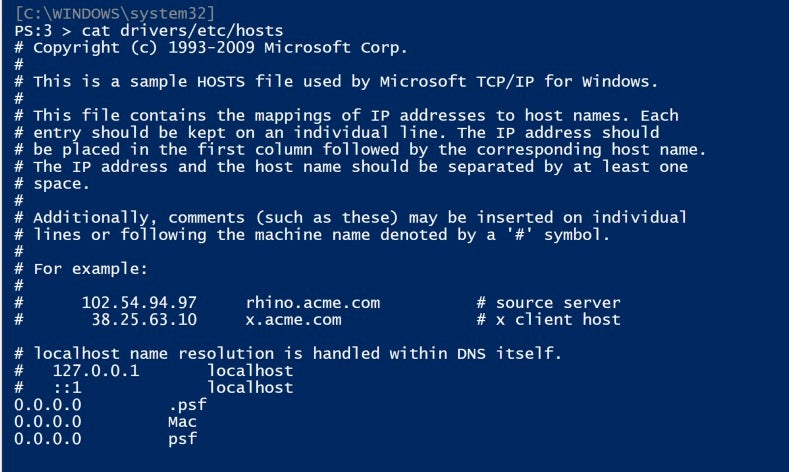
For those comfortable with PowerShell, just execute the cat command on the same filepath:
cat C:windowssystem32driversetchosts
The command
cat /etc/hosts
It should be sufficient on both Linux
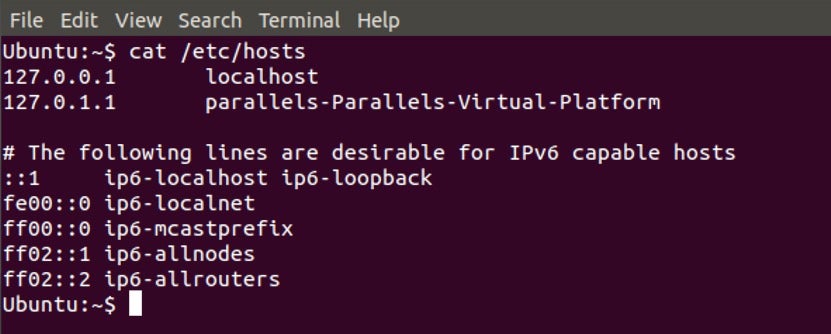
And macOS:
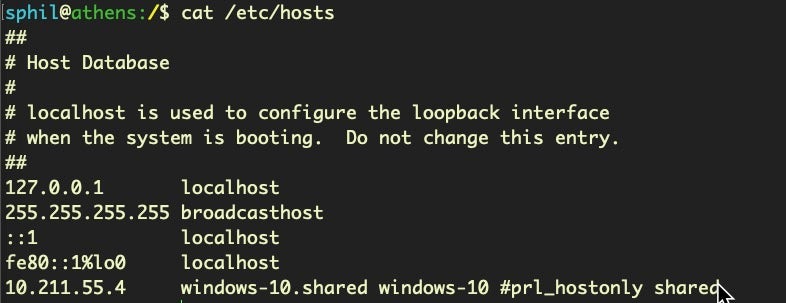
The above images are default hosts files with VM software installed. An attacker would modify the hosts files by adding a line such as
<attackers IP address> google.com
Such a line would resolve all requests google.com on the device immediately to the IP address given, without any further DNS lookups or checks.
Local hacks can also be revealed if you notice slow downs, browser redirects, site unavailabilities, pop-ups or other unusual behaviour when using your browser. Try changing the local DNS settings on your computer to 8.8.8.8 and 8.8.4.4 (Google’s Public DNS) or 1.1.1.1 and 1.0.0.1 (CloudFare’s Public DNS) to see if that helps. At the same time, be sure to use a good security solution that can detect malware that has DNS changing behaviour.
For checking DNS lookups outside of your local network, there are a few tools end users can use. The whoismydns.com site provides a free service that tries to tell you what server is making DNS requests on your behalf when you connect to the whoismydns.com site. While this is a nice idea, we have to recommend caution in using it.
For one thing, there doesn’t appear to be an https version of the site, so there’s no real way you can verify that your connection to the site hasn’t been tampered with enroute. Secondly, if an attacker has control of your DNS traffic, it’s possible that you could be redirected to a fake version of the whoismydns.com site itself!
Pretty much the same cautions apply to this site, which attempts to tell you if your computer is one of the thousands still out there infected with the DNSChanger malware.
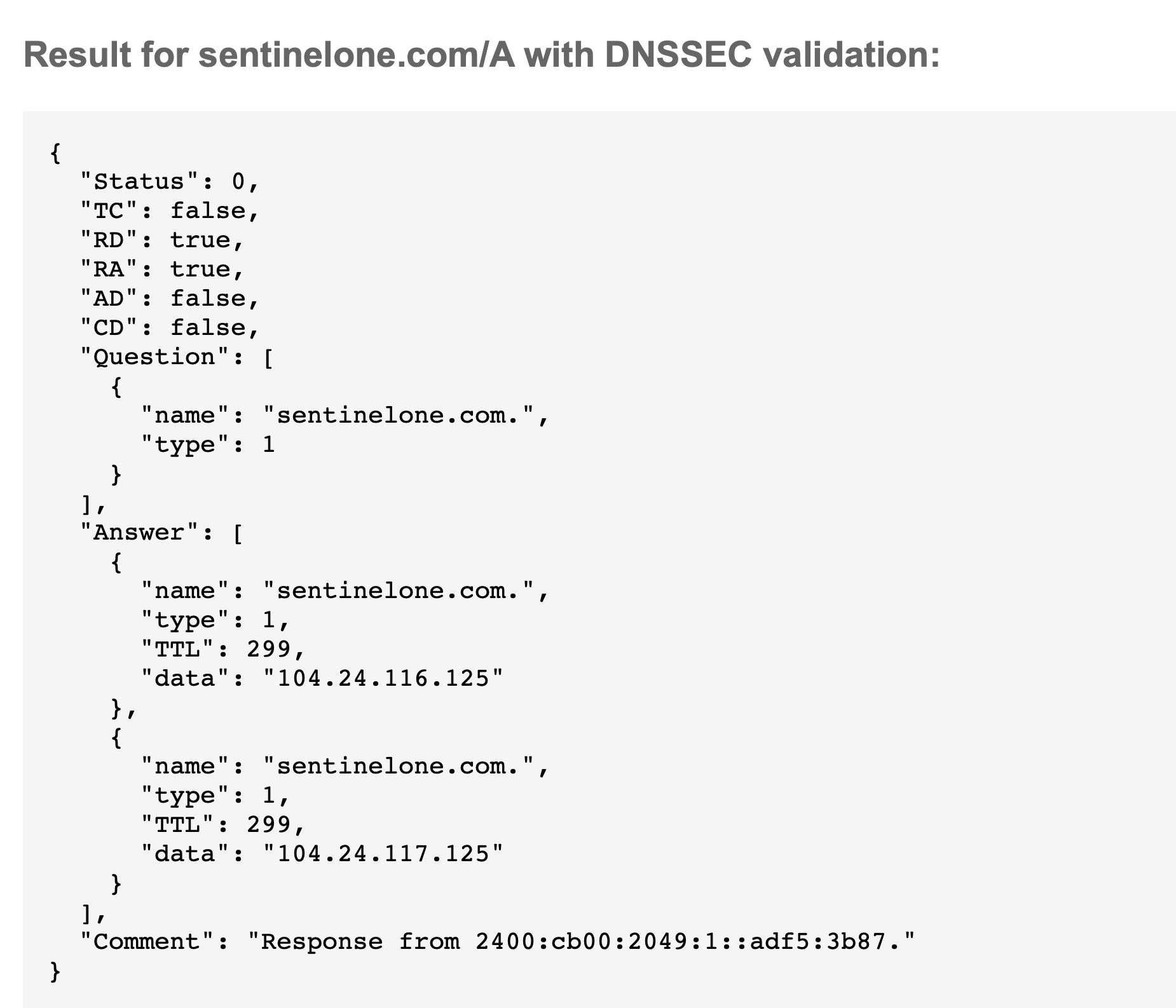
For enterprise and domain name holders, from a known clean device, you can check that your A-Record is what it should be using Google’s DNS lookup service. For example, will the real SentinelOne please stand up:
What Can You Do About DNS Hijacks?
Attackers have noticed that routers are something of a weakpoint in the security chain, not least because they have relatively poor internal protections, are generally shipped with default admin passwords that an unfortunately large number of users never change, and have infrequent (if ever) firmware upgrades. A great checklist of router security tips can be found here, but the essentials boil down to verifying and checking your router’s DNS settings and regularly updating the router password.
In managing your organization’s domain names, the most important step for enterprises to prevent DNS hijacks is to use a registry lock to prevent unauthorized changes. Further, be sure to enable two-factor authorization on your account access.
If your host service does not offer registry locks or 2FA, you should seriously consider changing to one that does as soon as practically possible. Beyond that, enable DNSSEC (Domain Name System Security Extensions) in your site’s control panel. This helps to prevent DNS redirections, cache poisoning, pharming and man-in-the-middle-attacks by authenticating the resolution of IP addresses with a cryptographic signature.
To eradicate the problem of DNS lookups between your distributed endpoints and your organization’s network, enterprises should use a reputable VPN service. Also, be sure to protect your endpoints and network with an autonomous, next-gen security solution.
 Enhance Your Threat Intelligence
Enhance Your Threat Intelligence
See how the SentinelOne threat-hunting service WatchTower can surface greater insights and help you outpace attacks.
Learn MoreConclusion
Resolving domain names into numerical IP addresses, from the endpoint to the DNS root server, is fraught with vulnerabilities for ordinary users and enterprise while offering great opportunities for attackers. The US Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) recently warned that a global DNS hijacking campaign is currently active. With a successful hijack, an attacker can redirect your organization’s web traffic to attacker-controlled infrastructure, complete with valid encryption certificates, and conduct man-in-the-middle attacks. DNS attacks on the device are easily accomplished by changing local DNS settings or poisoning the local hosts file.
To stay protected, follow the advice we outlined in the previous section. If your endpoints are not already protected by a robust security solution like SentinelOne, this free demo will show you how our autonomous endpoint solution can keep your devices and network safe.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- The Enemy Within – Top 7 Most Disturbing Data Breaches in 2018
- 5 Ways a CISO Can Tackle the CyberSecurity Skills Shortage Now
- How Malware Can Easily Defeat Apple’s macOS Security
- What Is Windows PowerShell (And Could It Be Malicious)?
DNS Hijacking FAQs
DNS hijacking is a cyberattack where hackers manipulate DNS queries to redirect users from legitimate websites to malicious ones. Attackers can install malware on your computer, seize control of routers, or hack DNS connections to carry out the attack.
When you type a website address, instead of going to the real site, you get redirected to a fake site controlled by the attacker. This can lead to phishing scams, malware infections, and data theft.
A notable example occurred in 2019 with the Sea Turtle campaign, where attackers hijacked DNS records of telecommunications and media companies to collect sensitive data. Another example happened to The New York Times in 2013, where attackers redirected users to a fake website designed to steal login credentials. In 2022, hackers hijacked Curve Finance’s DNS, redirecting users to a malicious cryptocurrency platform that stole their funds.
There are several types of DNS hijacking. Local DNS hijacking involves malware changing DNS settings on your device. Router DNS hijacking targets home routers by exploiting weak passwords or firmware vulnerabilities. Man-in-the-middle attacks intercept DNS requests between your device and the DNS server.
Rogue DNS server hijacking occurs when attackers compromise legitimate DNS servers themselves. There’s also registrar hijacking, where attackers gain access to domain registrar accounts.
DNS hijacking works by intercepting the normal DNS resolution process. When you type a website address, your device sends a DNS query to find the IP address. Attackers can compromise DNS servers, infect your device with malware, or intercept DNS requests during transmission.
Once they control the DNS resolution, they redirect you to malicious websites while keeping the original URL visible. This makes it hard to detect since everything appears normal in your browser.
You can detect DNS hijacking by watching for several warning signs. Web pages load slowly, and you see frequent pop-up ads on sites that shouldn’t have them. You might get redirected to unexpected websites or receive security certificate warnings. If your internet runs slower than usual or you notice unfamiliar websites appearing, these could be signs of DNS hijacking. You can also use online tools to check if your DNS has been compromised.
DNS spoofing involves injecting false DNS records into caches to redirect traffic temporarily. DNS hijacking is more comprehensive and involves taking control of DNS infrastructure or settings directly. Spoofing typically affects local networks or individual users, while hijacking can affect entire domains globally.
DNS spoofing corrupts DNS cache entries, but DNS hijacking actually changes DNS settings themselves. Hijacking is more persistent and harder to detect than spoofing.
You can prevent DNS hijacking by using strong, unique passwords for your domain registrar and DNS provider accounts. Enable two-factor authentication wherever possible. Use registrar locks to prevent unauthorized domain transfers. Consider implementing DNSSEC to add cryptographic signatures to your DNS data.
Use encrypted DNS protocols like DNS-over-HTTPS or DNS-over-TLS. Keep your router firmware updated and change default passwords. Monitor your DNS settings regularly for any unauthorized changes.
You’ll know your DNS has been hijacked if you can’t access your usual websites or get redirected to unfamiliar pages. Your domain registrar account credentials might stop working, or you notice DNS settings have changed without your knowledge. Users might report receiving strange emails from your domain.
There could be unusual network traffic or unexpected IP addresses resolving for your domain. You might also receive security warnings when trying to access legitimate websites.
Yes, VPNs can help prevent DNS hijacking by encrypting your internet traffic and routing DNS requests through secure servers. A VPN makes it harder for attackers to intercept your DNS requests. However, VPNs aren’t a complete solution because they don’t protect against all types of DNS hijacking, especially those targeting domain registrars or DNS providers.
You should use a VPN alongside other security measures like strong passwords and two-factor authentication for better protection.


