Venus ransomware has been launching data encryption attacks across the globe since at least August 2022. Last week, the Health Sector Cybersecurity Coordination Center issued an advisory stating that at least one healthcare entity in the United States had fallen victim to Venus ransomware, prompting wider warnings for healthcare and other organizations to be on their guard.
In this blog post, we provide further analysis, indicators of compromise, and TTPs associated with Venus ransomware to help organizations and security teams better understand and defend against this threat.

Overview
Venus ransomware, also known as Goodgame, has been attracting attention since August 2022 and related samples have been known since at least mid-2021. There are sufficient markers and other metadata present in Venus samples to suggest a genealogy with Zeoticus ransomware, which dates back to early 2020.
Venus ransomware is in the tradition of what now might be termed the “legacy ransomware” model: a file locker sold on underground markets as a standalone package rather than on a subscription or “ransomware-as-a-service” model. The package includes a compiled binary and access to decryptors. Unlike more modern data extortion schemes, there is no public data leak site or double extortion methods known to be associated with operators of Venus ransomware at this time.
Underground adverts offering Venus ransomware for sale began appearing in May 2022.
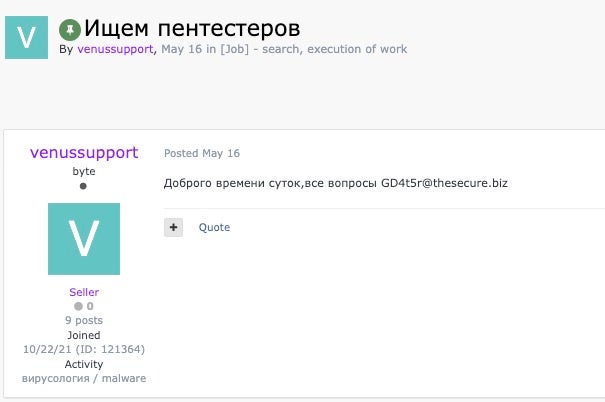
Translated, the message shown in the image above states “We are looking for pentesters”, a common euphemism for ransomware in the wake of a crackdown on overt ransomware discussion in many forums after certain high profile attacks brought unwanted attention.
Aside from HC3’s warning last week of a healthcare organization being compromised by Venus ransomware operators, there is little indication that targets are industry or sector-specific. Initial access is reportedly publicly-exposed and vulnerable RDP (Remote Desktop Protocol) services, a common weakness found across many different types of organizations, regardless of industry or sector. Cybercriminals discover such vulnerable RDP services through tools like Shodan, direct scanning, COTS/Open-source tools, or by purchasing access from an Initial Access Broker.
Venus Ransomware | Technical Analysis
On launch, Venus ransomware samples will spawn a UAC (User Access Control) prompt in an attempt to elevate privileges before continuing execution.
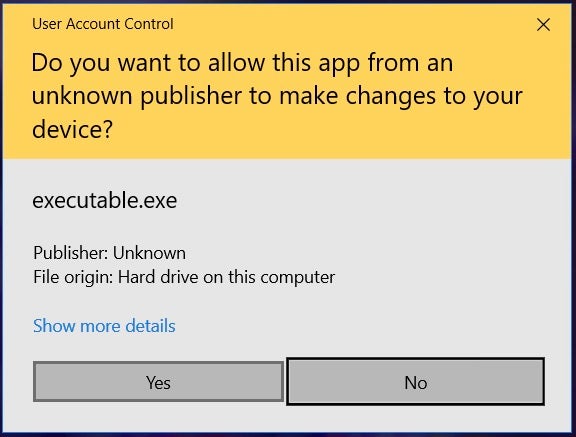
Subsequently, the malware launches a child process with the following syntax:
file.exe g g g o n e123
In common with Zeoticus, the ransomware then uses the ping to achieve a delay before deleting its own first-stage binary and hiding the console window from victims.
/c ping localhost -n 3 > nul & del C:\Users\[user]\Desktop\file.exe
Following this stage, a hardcoded list of processes is compared against what is running on the target and any applicable processes are shutdown via taskkill.exe. A full list of processes targeted mirrors the hardcoded list found in Zeoticus samples.
agntsvc.exe agntsvc.exe agntsvc.exe agntsvc.exe dbeng50.exe dbsnmp.exe encsvc.exe excel.exe firefoxconfig.exe infopath.exe isqlplussvc.exe msaccess.exe mspub.exe mydesktopqos.exe mydesktopservice.exe mysqld-nt.exe mysqld-opt.exe mysqld.exe ocautoupds.exe ocomm.exe ocssd.exe onenote.exe oracle.exe outlook.exe powerpnt.exe sqbcoreservice.exe sqlagent.exe sqlbrowser.exe sqlservr.exe sqlservr.exe sqlwriter.exe synctime.exe tbirdconfig.exe thebat64.exe thunderbird.exe winword.exe wordpad.exe xfssvccon.exe
Persistence is achieved by adding an entry for the ransomware payload in the registry (Windows run key). For example:
Write Value HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\352.exe
Once encrypted, affected files will be appended with the .venus extension. Note that .TXT files are not always encrypted by Venus ransomware.
The malware also changes the icons of encrypted files with an image written to %Windir%\ in the early stages of execution. The user’s Desktop wallpaper is likewise replaced by a .jpg image written to %temp%. Both are given file names with a random 20-character string that conform to the regex \d{20}, for example:
- 16773516481972502376.jpg
- 34004731821972527219.jpg
- 28604229151972527219.jpg
Once all files have been processed, the malware uses registry modification to change the wallpaper.
\REGISTRY\USER\[USERIDENTIFIER]\Control Panel\Desktop\Wallpaper = "C:\\Users\\[user]\\AppData\\Local\\Temp\\\\[20char string)].jpg"

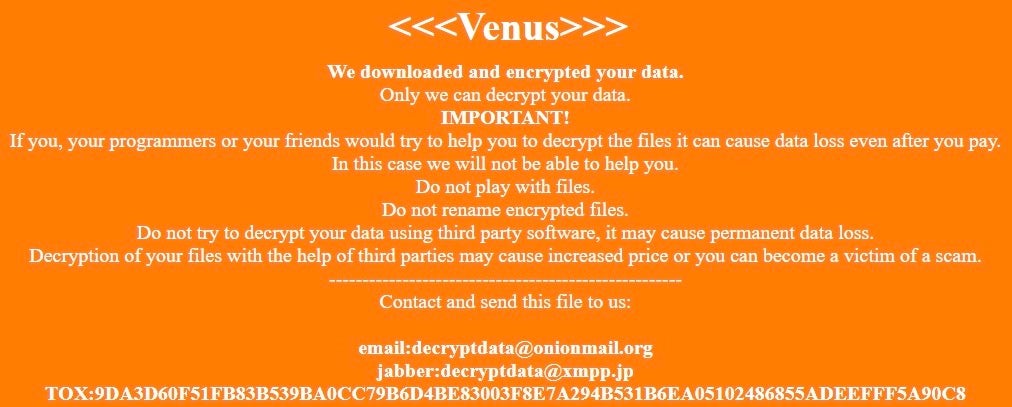
After the Desktop wallpaper is updated, the ransom note is displayed to the user. The ransom note is an .HTA file similarly written to %temp% with a 20-character string of digits for the file name.
During the course of execution, the malware attempts basic local discovery such as finding the machine name and OS. Venus ransomware traverses available network shares via NetShareEnum and wNetOpenEnum.
Some variants of Venus will utilize WMI to query or redirect additional system services and details. The following command is one launched by Venus ransomware:
wmi - start iwbemservices::execquery - root\cimv2 : select __path, processid, csname, caption, sessionid, threadcount, workingsetsize, kernelmodetime, usermodetime, parentprocessid from win32_process where ( caption = "msftesql.exe" or caption = "sqlagent.exe" or caption = "sqlbrowser.exe" or caption = "sqlservr.exe" or caption = "sqlwriter.exe" or caption = "oracle.exe" or caption = "ocssd.exe" or caption = "dbsnmp.exe" or caption = "synctime.exe" or caption = "mydesktopqos.exe" or caption = "agntsvc.exe" or caption = "isqlplussvc.exe" or caption = "xfssvccon.exe" or caption = "mydesktopservice.exe" or caption = "ocautoupds.exe" or caption = "agntsvc.exe" or caption = "agntsvc.exe" or caption = "agntsvc.exe" or caption = "encsvc.exe" or caption = "firefoxconfig.exe" or caption = "tbirdconfig.exe" or caption = "ocomm.exe" or caption = "mysqld.exe" or caption = "mysqld-nt.exe" or caption = "mysqld-opt.exe" or caption = "dbeng50.exe" or caption = "sqbcoreservice.exe" or caption = "excel.exe" or caption = "infopath.exe" or caption = "msaccess.exe" or caption = "mspub.exe" or caption = "onenote.exe" or caption = "outlook.exe" or caption = "powerpnt.exe" or caption = "sqlservr.exe" or caption = "thebat64.exe" or caption = "thunderbird.exe" or caption = "winword.exe" or caption = "wordpad.exe")
In addition, the following commands are commonly used across Venus variants in order to inhibit or disable system recovery and backup systems.
vdsldr.exe -Embedding
cmd.exe (wbadmin.exe) delete shadows /all /quiet && bcdedit.exe /set {current} nx AlwaysOff && wmic SHADOWCOPY DELETE
wbadmin.exe delete catalog -quiet
vssadmin.exe delete shadows /all /quiet
mshta.exe [name].hta) - "C:\Users\[user]\AppData\Local\Temp\16773516481972502376.hta" {xxxxxxxxx-F1C3-4B2E-88BF-xxxxxxxxxx}{1E460BD7-F1C3-4B2E-88BF-xxxxxxxxxx}
WMIC.exe SHADOWCOPY DELETE
bcdedit.exe /set {current} nx AlwaysOff
Venus Ransomware’s Connection to Zeoticus
Like Zeoticus, Venus instructs users to reach out via email and TOX in order to engage with the ransomware operators and does not use C2 servers for data exfiltration or backdoors.
As noted above, there are certain code similarities between the way Zeoticus and Venus use the ping command.
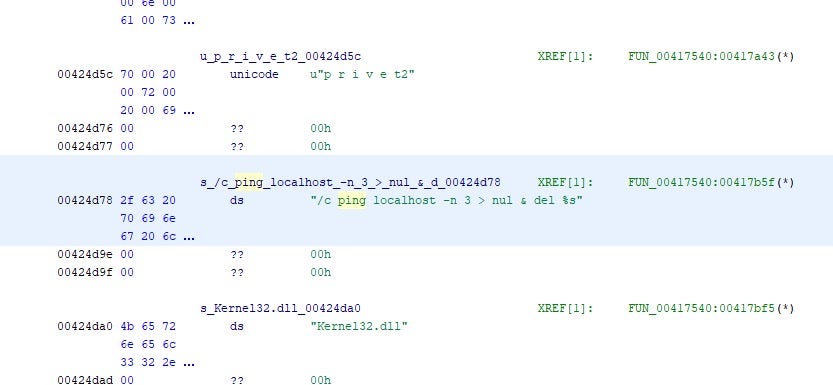
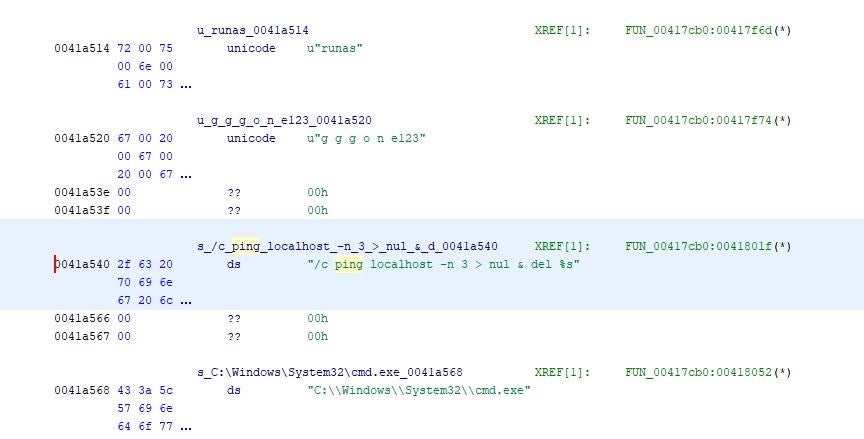
Also note how the p r i v e t2 marker in Zeoticus is paralleled by the g g g o n e123 marker in Venus.
Command line syntax for persistence, task termination and various ‘housekeeping’ tasks between the two families is almost identical, and both malware families hardcode the same list of processes to target for termination.
Like Venus, Zeoticus is also offered as a complete standalone package rather than a RaaS and is not associated with a leaks site.
The ransom notes and Desktop backgrounds have similar stylistic overtones, and both malware variants write copies to mounted Recovery volumes.
Neither family is particularly sophisticated, and both use hardcoded strings within the malware with no attempt at obfuscation or anti-analysis.
SentinelOne Protects Against Venus Ransomware
SentinelOne Singularity™ fully detects and prevents payloads, behaviors, and artifacts associated with Venus and Zeoticus ransomware families.
Conclusion
Organizations are right to be concerned about the uptick in activity of this ransomware variant. Insofar as organizations leave vulnerable RDP services exposed to the public internet or fail to protect endpoints with a reliable Next-Gen security solution, attackers need not invest resources in sophisticated malware. Venus ransomware may not be specifically targeting healthcare organizations, but public service and critical infrastructure organizations may be symptomatic of those that most need to up their game to combat threats such as these.
Indicators of Compromise
SHA1
026ce3bceb3a82452f0fc38c0b9abfa90f2c9d87
06757be6174bdc9ef8fe899bcbe5e6e5547dc059
0d0bbcecc80ea3b1712678b24ba925ac2903531f
102b8625e5662c89efe4547dc2cb173be8b08851
10f2ed474a9e0065fed2afebbfe81dc596f46542
13315ee0ba756ac3e7edf2b9a4028b7649ece754
1482e7fdbab29c3e8a2f3ccd1c6ddd48a54c06b0
14d031138fb0aad2432cadf2e0d241ca75b2dfbb
1970f6c17567d56c3e7840fe33a6959dd887fca2
1992336a5d752187c979e24a95a871d8932ade6d
1cb7e2ab7012990bd5051120c3ef8a438035aa88
1fb9b8115d74cf38d6a90b9049c73ea6eb743643
326dc3ca63d10968054153305a9564fac2a37ba3
5166d17d8e9a91a3a36b5edaf168699b03bb13de
5d1229ece791a55823f60298cb7dcf9c0494f3ee
62383813a6ca85fc9c70051c361e0273e135593d
6bf35f44a2267755c2646c89c836bd618c4e964c
6e530c9a3eddabc29c2f8f6aca6c6f786ae052d6
7f4bcc7d13bf3ebab836a770718cc8273470d660
7f8cd9947f9c2bddd9586868c181b4c6a86f10a5
88433f6f33d7b81178815412111d146185b9a857
895eb3047e7a28ce219fdd7e7ad5ce2a61312d93
969a91d0038c10599f0f1f647cf0da869b5ded34
ac1c4cb8a6920bb7276dbf1435040f4003f8580c
ac348c2673f9c66d695bc75b65cbe32adc7887a6
ba145483608a4ea567ed3c3c2b7e396098f5386a
c40909226c102ceb3cf97e9037c590f1623af013
c7a16493be181dbe5ec8d993883bbc1759d22131
c91f54077b8ad8dd8e3f5807181b941124a4e971
da452698643d21a0212d62bd293e0c250f684b14
e044edce8646124ddc39906e6fb6f02eaff16161
e47eefdacf2b1190d2c95cb2800628429bfa115b
ec11f6abf13044a438a7f363bda2c9d5709d2475
fd30e7fcce4c1c372981cde822ba36ded96b7614
ff8747471c9641b17543038433137d7c0ffbcbb7
SHA256
04d75593f6acdfe0c959345b8d6702166537d7533abfeb4b568339dee1986b5e
0a4e5832841ffff9f8d27ce8216d655c8743b682fff0f90dee6bd3ea83dec028
0dc0da0739b227a9dae83be93d1b232c645dbffc7499709ae05c4ffa1bf44000
223f6c995c3de7613fd6e317ff88683999f43225d4ece6640cc752fd1f60ddbc
260ddec8adb08c4f1a3fa3cf75f8faf8b70f40cf49d4965ac15b60929350294c
261286c526153f77f317b0ecb015836aed4ab3a69f0bdfbd189836f209f896e7
2e2cef71bf99594b54e00d459480e1932e0230fb1cbee24700fbc2f5f631bf12
380791c0b797096fee3013ef5666e9c965b93d6cd203d0445132bac3cab5f7c4
49fd52a3f3d1d46dc065217e588d1d29fba4d978cd8fdb2887fd603320540f71
52f7ace0de098c3c820416b601d62c4f56c9b20b569fa625bf242b625521f147
59b05789e5ac3d47c0a3d0f3e4ccacb2667cb7367e42adb9a3cbb108a538fc77
65524db4cc14954481961341c72aa8cf00f78144915cd9eb357c99c3ab669b52
6a52b9cd66ae94e8d27eb0bc3a63e6bd2c3ba6903637533a554d786e00af2404
6d8e2d8f6aeb0f4512a53fe83b2ef7699513ebaff31735675f46d1beea3a8e05
79f3aca3bd4e35948db577c9c0b0949c93c9869df6151889aa95b2ef9b8fae17
7b42fa7abdb7e2cfdbb3001e18cf09f62aefd0607684b956aa02c866c12539ac
7d703d0266823347ead7b3333e5e7ac5dd9d36231da62edfe407159aec0afbc9
7e2201b3fd0cf8a6e550ad4af3419e8955bb4ebbca15e11f8ba7a9f4d48cc88c
8045ad5cda6c42e5669cf52e492c004d842c7ae6f8a09522134834d0f57347eb
91845c398b06ddad405f15c1ff73c0ba6c2d27aca46bb04449f1b0855a5fd243
969bfe42819e30e35ca601df443471d677e04c988928b63fccb25bf0531ea2cc
9aa3826da16367166ac01379dd79eab4f0925a6f9b23eab87df6c498bce987c4
a3fa331e4a1e6171cfbda8739513b9477596400b283f32479f4342a1a4d21469
a558d293b26621888f71149c977cc9b68383f0e4cf039d09910f0a97892d7b33
aa0cfdc539cb2db1109606802d6b09a0652c9d60396faa7829ee692df580561f
c54f9afbcf5ed31373855154e8d2f8c2511c76cbbcbed325b30b98ddf3049f98
d6098f0d579273528b28b0b49c8b72b6f9908aef9e1ba0ec5da0874fa8c92266
d9aa454dc2c5d430ac2585f170fcd1ba7a3d31ba80dcc6f22676673c50919865
de6547c284800a6153f79e8518db48a41cc7841550bfdb699f084e988355c952
e844cf44b04c924730626cf2a0342890606d55386f757e99871092bbfc585044
ee036f333a0c4a24d9aa09848e635639e481695a9209474900eb71c9e453256b
f7fe602573c1c9df594ae7d29ddcad56332001005ae5d7786ce3cb452d381d54
fa7ba459236c7b27a0429f1961b992ab87fc8b3427469fd98bfc272ae6852063
faee1c99d47e9dc02bce9a89363817b94200d8a825e3bce0bc4e98f4e0feb2c0
MITRE ATT&CK
S0106 – cmd.exe
T1005 – Data from Local System
T1012 – Query Registry
T1018 – Remote System Discovery
T1070.004 – Indicator Removal: File Deletion
T1082 – System Information Discovery
T1112 – Modify Registry
T1120 – Peripheral Device Discovery
T1202 – Indirect Command Execution
T1486 – Data Encrypted for Impact
T1490 – Inhibit System Recovery
T1491.001 – Defacement: Internal Defacement
T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
T1555.003 – Credentials from Password Stores: Credentials from Web Browsers
T1564.003 – Hide Artifacts: Hidden Window


