The Good
We are barely a month into 2021 and it is safe to say it has already started off with a bang. Emotet has been at the top of many ‘most wanted’ lists for several years. Initially launching in 2014 as a modest but functional banking trojan, Emotet has evolved into a complex, multi-tiered framework. The Emotet infrastructure is vast, fault tolerant, and has proven to be a power vector for the delivery of additional and equally problematic malware such as Trickbot, Ryuk, and Qakbot. However, all that appears to be changing.
This week, Europol executed on a long-term, collaborative, project to disrupt Emotet. Working with additional law enforcement agencies and industry partners, the Emotet infrastructure was disrupted from the inside. Traffic across all tiers of the Emotet infrastructure has been seized and redirected to systems controlled by law enforcement. Making this specific takedown even more unique, it appears that a custom module was introduced as part of Operation Ladybird that will force Emotet to automatically remove itself on April 25.
This takedown is more thorough than many others we have seen recently, including that of Trickbot. While it is possible that Emotet will eventually retool and bounce back, it will take much more time and a great deal of investment in new systems and infrastructure. Time will tell, but for now we should all take some comfort in the fact that one of, if not the, most problematic and prolific malware families has been dealt a serious blow.
The Bad
What kind of week would it be without some discussion of ransomware? By now we are all familiar with the double-whammy of modern ransomware families. That is, they hit you with both the encryption payload as well as the potential for your data to be leaked to the public in the event that you do not comply with the attackers’ demands. However, we are now seeing an increasing number of ransomware families adding the threat of DDoS (Distributed Denial of Service) attacks to the equation. In addition to the previously mentioned ‘double-whammy’, victims also face the possibility of their public websites being attacked directly through a denial of service attack.
Among those adopting this new tactic are Ragnar, Avaddon RaaS, and a small group of other families. Threatening victims with a DDoS attack is meant to encourage the victims to contact the attackers rather than attempt to quickly restore from backup or try some other means of circumventing the attacker’s demands.
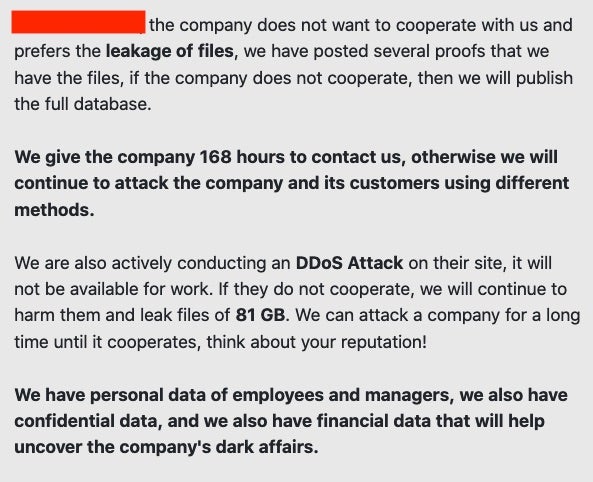
There is no doubt that the continued adoption of this additional layer of extortion is both threatening and problematic. However, this does also serve to reinforce the importance of prevention. The only true defence, and the only way to ensure full and proper continuity of business is to prevent these attacks before they happen. Modern and forward-thinking endpoint security controls are a prerequisite, of course, but they must also be properly managed and configured.
The Ugly
This week, two worrisome bugs were revealed in relation to the venerable Unix sudo command. First up, sharp-eyed researcher Rich Mirch noticed that a fix for an earlier CVE in sudoedit, CVE-2021-23240, which had been patched in sudo v1.9.5, actually opened up a new privilege escalation vulnerability. After reversing the patch, Mirch was able to find and exploit a new bug that makes it possible for a low-privileged user to gain a root shell.
Mirch’s bug was promptly fixed in 1.9.5p1, but a research team from Qualys gave the developers and Unix admins further headaches by identifying another, long-standing but unnoticed critical flaw affecting that version and many earlier versions, too.
CVE-2021-3156 is a heap-based buffer overflow that, upon exploitation, allows any user (regardless of their presence in the sudoers file) to achieve root-level access. The flaw lies in improper handling of unescaped characters provided in the sudo command syntax.
According to the disclosure from Qualys, the flaw can be invoked “either through the -s option, which sets sudo’s MODE_SHELL flag” or “through the -i option, which sets Sudo’s MODE_SHELL and MODE_LOGIN_SHELL flags”.
What may be slightly more alarming is that this bug was introduced into the sudo program code in July of 2011. The flaw affects stable versions from 1.9.0 to 1.9.5p1 as well as all ‘legacy’ versions from 1.8.2 to 1.8.31p2. Needless to say, all users are advised to patch to v1.9.5p2 immediately.