The Good | Co-Founder of Criminal Crypto Exchange Pleads Guilty to Money-Laundering Schemes
Anatoly Legkodymov (aka “Gandalf” or “Tolik”), co-founder of the Bitzlato cryptocurrency exchange, has pleaded guilty to his role in aiding ransomware gangs and other cybercriminals in laundering over $700 million. Legkodymov has agreed to disband Bitzlato and forfeit his claim to approximately $23 million in seized assets, according to the terms of his plea agreement.

Bitzlato reportedly saw widespread illicit activity on its platform. The exchange promoted a user registration process with minimal identification requirements, explicitly stating that neither selfies nor passports were necessary. According to the DoJ, this lax approach led to Bitzlato becoming a haven for criminal proceeds and funds intended for a variety of malicious activities.
Reports on cryptocurrency-related illicit activity revealed that Bitzlato conducted over $2 billion in cryptocurrency transactions between 2019 to 2021 alone. Nearly 48% of this amount, approximately $966 million, was associated with high-risk cryptocurrency transactions and deemed illicit. The exchange received funds totaling $206 million from darknet markets, $224.5 million from scams, and $9 million from ransomware attackers.
The crypto exchange was also known to be particularly entwined with the Hydra Market, facilitating more than $700 million worth of cryptocurrency exchanges until the dark market was shut down by U.S. and German law enforcement in April 2022. The exchange also received millions in ransomware proceeds, despite repeated warnings to Legkodymov that the routed cryptocurrency represented the proceeds of crime and was intended for illicit transactions.
Dismantling Bitzlato’s digital infrastructure and the subsequent seizure of its domains was a collaborative effort from Europol and authorities in France, Spain, Portugal, and Cyprus. After his initial arrest in Miami earlier this year, Legkodymov now faces a maximum sentence of five years in prison for his role in the illicit activities associated with Bitzlato.
The Bad | APT28 Actors Re-Use Old Outlook Vulnerability to Access Polish Exchange Accounts
Security researchers have identified the Russian state-sponsored actor, APT28 (aka Fancy Bear or Sofacy), exploiting a recently-patched flaw (CVE-2023-23397) in Microsoft Outlook to gain unauthorized access to accounts within Exchange servers. Before it was fixed in March, targets spanned critical sectors in the United States, Europe, and the Middle East. Based on the new wave of attacks, Polish Cyber Command’s (DKWOC) reports that the attacker’s goal now is to obtain unauthorized access to mailboxes belonging to public and private entities that have yet to patch their instances.
CVE-2023-23397 is a critical-level (CVSS score: 9.8) elevation of privilege (EoP) vulnerability triggered by a specially-crafted email message that is sent to a targeted user. Once the message is opened, the user’s Net-NTLMv2 hash is transmitted to the attacker, allowing them to manipulate the access permissions of specific mailboxes and steal sensitive information and/or credentials.
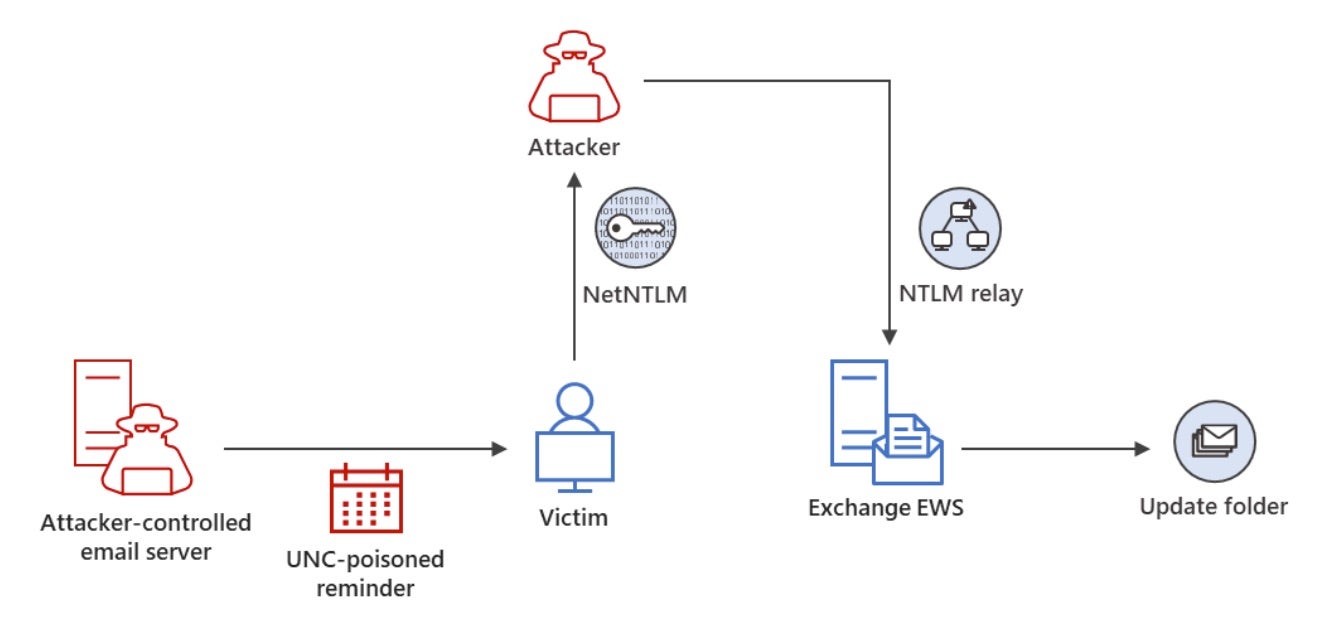
The state-sponsored group linked to APT28 has been active since 2008, known most widely for interfering in the 2016 U.S. presidential election and their engagement in various hack-and-leak operations. Their victims are typically high-value, coming from governments, military, and private sectors. Just two months ago, the National Cybersecurity Agency of France (ANSSI) pinned a cluster of attacks on agencies, universities, think tanks, and research institutions onto the threat group, where they leveraged a combination of flaws, including CVE-2023-23397, to deploy stealers in prominent web browsers.
APT28 commonly employs other known vulnerabilities as part of their attack methods, such as CVE-2023-38831 or CVE-2021-40444. The recent incidents underscore the persistent challenges posed by sophisticated state-sponsored threat actors and the importance of promptly applying security patches to mitigate the risk of exploitation.
The Ugly | Unidentified Actors Exploit Adobe ColdFusion Flaw to Breach U.S. Government Servers
Threat actors are actively exploiting a high-severity vulnerability found in Adobe’s ColdFusion to gain initial access into U.S. government servers. According to CISA’s latest warning on the mounting attacks, the flaw tracked as CVE-2023-26360 presents an improper access control issue that could lead to arbitrary code execution.
The advisory highlights two incidents of exploitation where CVE-2023-26360 was utilized to compromise federal agency systems. Both instances involved outdated server software vulnerable to various CVEs, with threat actors leveraging the vulnerability to deploy malware through HTTP POST commands to the ColdFusion-associated directory path.
During the first incident, attackers breached a server running Adobe ColdFusion v2016.0.0.3. They performed process enumeration, network checks, and installed a web shell for code injection into a ColdFusion configuration file to extract credentials. The attackers then followed with tactics such as file deletion and creation in specific directories to conceal their activities.
The second incident involved attackers exploiting the flaw on a server running Adobe ColdFusion v2021.0.0.2. After gathering user account information, they deployed a remote access trojan in the form of a text file. Attempts were made to exfiltrate Registry files and security account manager (SAM) information, utilizing security tools to access a directory on domain controllers. Fortunately, both attacks were detected and thwarted before any data exfiltration or lateral movement occurred, with compromised assets removed from critical networks within 24 hours.
CISA categorizes these incidents as reconnaissance efforts, although it remains uncertain whether the same threat actor is responsible for both intrusions. To mitigate risks, CISA recommends updating ColdFusion to the latest version, implementing network segmentation, configuring firewalls or web application firewalls (WAFs), and enforcing policies for signed software execution.


