The Good
While all eyes have been on the U.S. this week and the hotly contested election, some rare good cyber security news came out of Russia, as the Ministry of Internal Affairs there reportedly arrested a malware developer known only by the handle “1ms0rry”.
The unnamed 20 year-old male had the misfortune to cross a red line that most other cyber criminals have learned to steer clear of: allowing his malware to infect computer users across Russia, netting profits in the region of 4.3 million rubles (around $55,000) from over 2000 of his compatriots.

Reports suggest the hacker was involved with a trojan/cryptocurrency miner called 1ms0rry-Miner, as well as the LoaderBot and N0f1l3 trojan and infostealers. His code has also been identified as source for several other more powerful malware strains including Bumblebee, FelixHTTP, EnlightenedHTTP and Evrial, a MaaS (malware-as-a-service) capable of stealing cryptocurrency wallet addresses and other credentials from Windows passwords.
While it’s lamentable that Russian authorities turn a blind-eye to home-grown hackers wantonly attacking non-Russian targets, it’s good to see another malware developer nabbed for whatever reason. Let’s just hope he’s not back on the cyber streets too soon with a better understanding of how to determine language preferences in his code.
The Bad
Resident Evil developers Capcom were hit by a Ragnar Locker ransomware attack on Monday, according to reports, resulting in the theft of around 1TB of Capcom data.
In common with other “leak-and-lock” ransomware operations, the threat actors are threatening to release a smorgasbord of IP and private sensitive data if the company fails to pay up. This ranges from financial documents and client and employee PII, such as passports and visas, to business contracts and private corporate emails and messenger conversations.
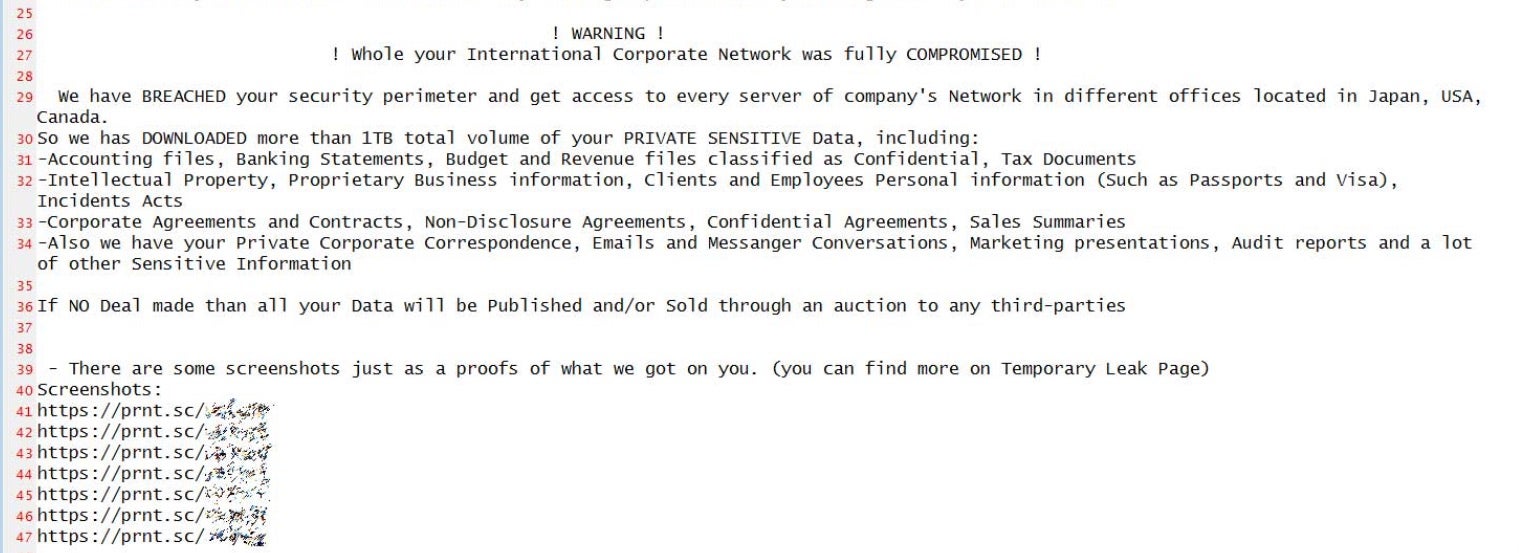
Reports suggest the ransomware has encrypted at least 2000 devices and that the attackers are demanding a hefty $11 million ransom in bitcoins.
The attack comes just a day after Ragnar Locker ransomware also hit drinks vendor Campari with a similar demand for $15 million in ransom.
In both cases, the attackers have leaked samples of the stolen data on their own “temporary Leak page”, a darknet website set up to “show examples and proofs of penetration” to incentivize payment. True to form, they have promised to sell the data to “third parties” if the victims refuse to pay up. At this time, there is no indication that either Capcom or Campari are cooperating with the threat actors.
The Ugly
Misconfiguration of cloud assets is a known security headache for companies transitioning to the cloud, and it doesn’t get any better when attempts to keep things like encrypted passwords safe are undermined by using flawed hashing algorithms like md5. Such are the painful lessons being learned this week by GrowDiaries, an online community of cannabis growers that plugs itself as “100% anonymous and secure”.

Trouble began with two unsecured Kibana apps. Kibana is a charting tool for Elasticsearch and provides a user interface for monitoring, managing and securing an Elastic Stack cluster. Unfortunately, admins for GrowDiaries appear to have left two instances of Kibana apps exposed without passwords since September, potentially allowing hackers access to around 3.4 million user records and passwords.
Worryingly for some GrowDiaries users, it appears from some of the IP addresses exposed that they are resident in countries where growing marijuana is illegal. While the company did secure the data on October 15th, five days after being alerted by cyber security researcher Bob Diachenko, it appears that the data may have been exposed since at least September 22.
It is not known at this point in time whether the data was accessed by malicious parties, but GrowDiaries users should urgently change their passwords as md5 hashes are crackable. Diachenko also notes that members of the community should be aware of targeted phishing attacks as well as account takeovers, as cracked passwords can be used in credential stuffing attacks on user’s other accounts.


