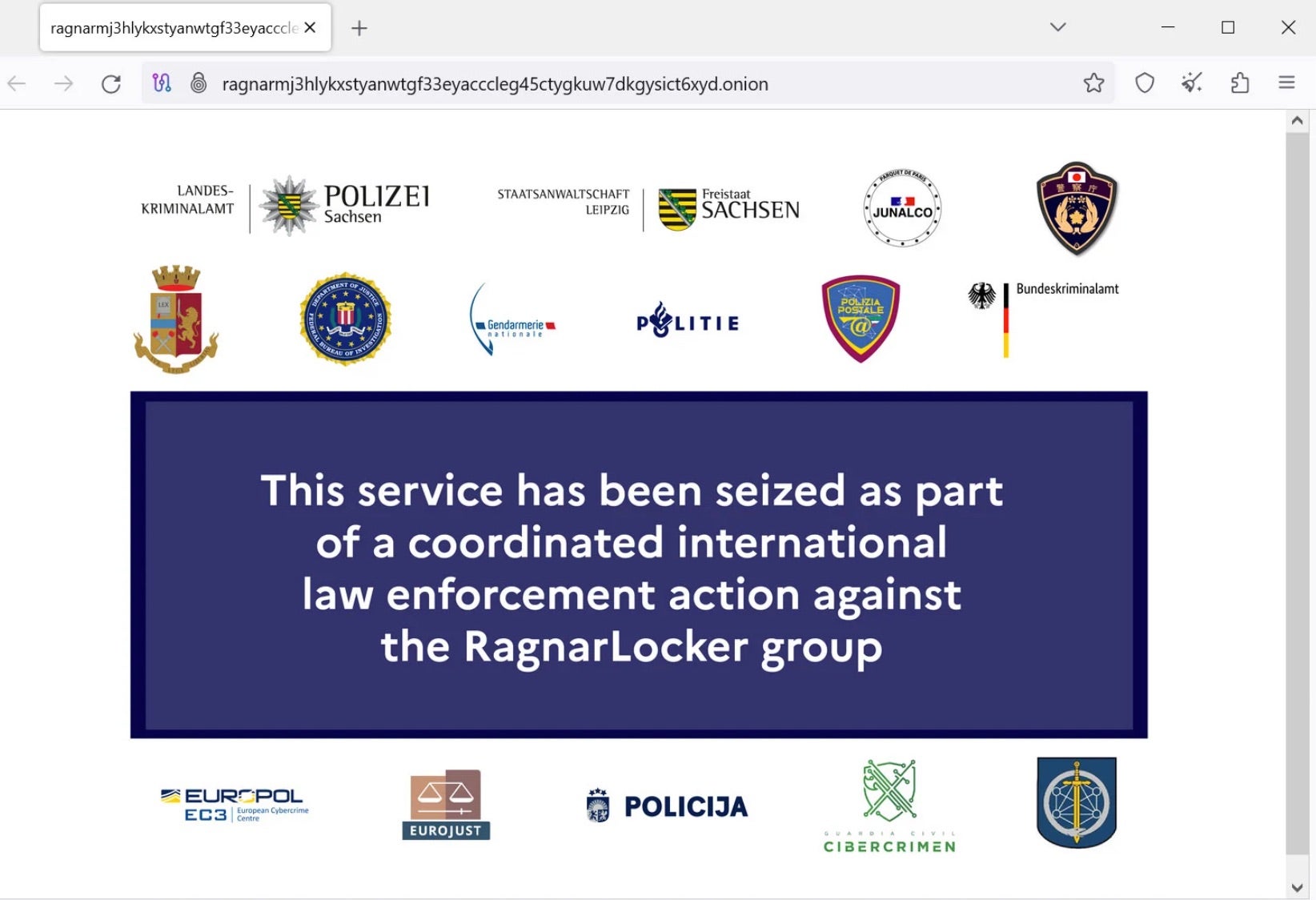
The Good | Ragnar Locker’s Tor & Leak Sites Taken Down In International Seizure
Ragnar Locker took a serious blow this week when authorities seized the ransomware operation’s Tor negotiation and data leak sites. This is the latest takedown coordinated across over a dozen international authorities. Now, visitors to the once-infamous sites are greeted with a seizure message.
Standing as one of the longest-running ransomware operations to date, Ragnar Locker activity began in late 2019 with a primary focus on infiltrating enterprises. In that time, Ragnar Locker has been highly successful at infiltrating corporate networks, moving laterally through systems, harvesting sensitive data, and encrypting computers within compromised networks. Encrypted files and stolen data are powerful bargaining chips in the operations’ double extortion schemes.
While many similar operators have moved to a Ransomware-as-a-Service (RaaS) model, Ragnar Locker has remained semi-private. It has refrained from promotion and recruitment instead working with external operators to breach networks. Ragnar Locker is also known for pure data theft attacks, eschewing the file locking techniques that are characteristic of most ransomware operations.
In March 2022, the FBI published a flash alert warning that at least 52 organizations across 10 critical infrastructure sectors had fallen victim to Ragnar Locker. Over the years, Ragnar Locker’s rap sheet has boasted numerous high-profile victims, including Energias de Portugal (EDP), Capcom, Campari, Dassault Falcon Jet, ADATA, and the City of Antwerp, Belgium. The seizure this week marks a significant win for cybersecurity law enforcement and reinforces the ongoing global effort to dismantle cyber threat infrastructures.
The Bad | Critical CI/CD RCE Flaw Actively Exploited By DPRK-Based Threat Actors
DPRK-based threat actors linked to the Lazarus Group are actively exploiting a critical security vulnerability in JetBrains TeamCity this week. Tracked as CVE-2023-42793 (CVSS score 9.8), the authentication bypass and remote code execution (RCE) flaw affects JetBrains’ continuous integration and continuous delivery (CI/CD) solution. The company reports a customer base of nearly 16 million developers globally, including several Fortune 100 companies. Security researchers have attributed the recent attacks to two factions within the Lazarus Group, which they refer to as Diamond Sleet (aka Hidden Cobra) and Onyx Sleet (aka Andariel).

Diamond Sleet has been observed employing two distinct attack methods. The first involves breaching TeamCity servers, followed by deploying an implant from previously compromised legitimate infrastructure. The second approach leverages the initial foothold to introduce a malicious DLL through DLL search-order hijacking. This facilitates the execution of a subsequent payload or a remote access trojan (RAT).
Onyx Sleet’s intrusions exploit the flaw to create a new user account likely to impersonate a Kerberos Ticket Granting Ticket. This account is then added to the Local Administrators Group before the attacker performs system discovery commands. Afterwards, a custom proxy tool is deployed, establishing a persistent connection between the compromised host and attacker-controlled infrastructure.
Since 2009, the Lazarus Group has earned a reputation for its sophisticated and persistent cyberattacks, namely financial crimes, espionage, and supply chain attacks. JetBrains urges users to apply patches and thoroughly monitor networks for signs of compromise. The U.S. National Security Council (NSC) believes that the revenue generated from these illicit activities funds North Korea’s missile program and the recently increasing number of launches.
As much of the world’s attention has been focused recently on the cyber threats emanating out of first the Russia-Ukraine war and now the Israel-Hamas war, these intrusions serve as a timely reminder that there are ongoing and diverse cyber threats posed by North Korean and other state-sponsored actors that still require our constant vigilance.
The Ugly | Cisco IOS XE Under Attack By Unpatched, In-The-Wild Zero-Day Flaw
Thousands of vulnerable enterprises are facing potential compromises this week from in-the-wild exploitation of CVE-2023-20198; a critical vulnerability affecting Cisco’s IOS XE software. This zero-day flaw is rated the maximum CVSS severity score of 10.0 and rooted in the web UI feature. The bug affects enterprise networking equipment when the feature is enabled and accessible over the internet or untrusted networks.
According to Cisco’s advisory, the vulnerability allows remote, unauthenticated attackers to create an account with privilege level 15 access on a compromised system. This account can then be used to gain full control of the system. The issue affects both physical and virtual devices running Cisco IOS XE software with the HTTP or HTTPS server feature enabled.
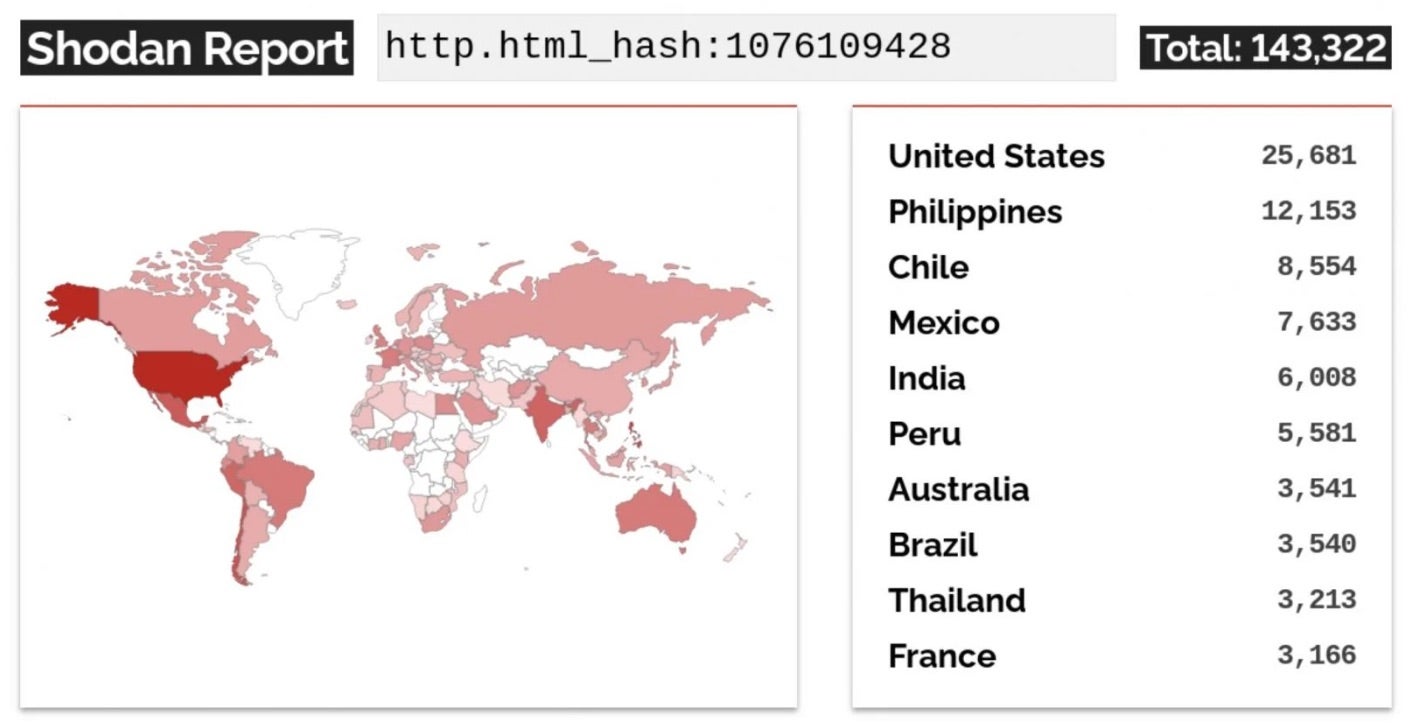
Latest reports tracking CVE-2023-20198 are finding that the flaw has given attackers privileged access, potentially allowing them to monitor network traffic, pivot into protected networks, and execute Man-in-the-Middle (MiTM) attacks. Shodan scans show that over 14,000 internet-exposed devices with the web UI feature enabled are currently vulnerable to attack.
While the exact origins of the threat actor behind these attacks are unclear, Cisco suggests that the initial cluster of activity seen in September may have been the actor’s testing phase, while October activity reflects an expansion of operations, including the establishment of persistent access. This has prompted CISA to issue an advisory, BOD for government organizations and add the zero-day to its Known Exploited Vulnerabilities (KEV) catalog.
Though there is currently no available patch at the time of this writing, Cisco recommends disabling the HTTP server feature on all internet-facing systems and using the copy running-configuration startup-configuration command to save the running-configuration. This should ensure the HTTP server feature is not unexpectedly enabled in the event of a system reload, Cisco said.


