The Good | Joint Advisory Reveals Top Ten Common Misconfigurations Found in Global Organizations
This week, the NSA and CISA released a joint advisory rounding up the top ten most common cybersecurity misconfigurations that plague organizations around the world. The advisory outlines the tactics, techniques, and procedures (TTPs) that threat actors often use in their attacks and includes best practices for building a strong network security posture.
You can learn from NSA’s experience working Red and Blue team engagements. Bad actors will look for easy opportunities to exploit vulnerabilities and compromise networks. Here are the top 10 cybersecurity misconfigurations we see:l along with @CISAgovhttps://t.co/in63ZwXCTs pic.twitter.com/P1Low2GRBk
— Rob Joyce (@NSA_CSDirector) October 5, 2023
Based on data collected by NSA and CISA red and blue teams during defensive testing, the list of misconfigurations calls to attention a pattern of weaknesses found in many large-scale organizations. While threat actors use novel methods to gain access and move through networks, attacks are often due to common misconfigurations. Issues stemming from default credentials, service permissions, improper segmentation, and poor patch management all create opportunities for attackers to break into sensitive systems.
The advisory also highlights the role of software manufacturers in particular, explaining how integral they are to establishing secure-by-design principles from inception. By taking ownership to improve their customers’ security, software manufacturers can reduce the trend of common misconfigurations by design and help ensure the integrity, availability, and confidentiality of data across critical industries.
Security is a shared responsibility though, and organizations can be proactive with their defense strategy. Other than applying the recommended cyber best practices, NSA and CISA note the importance of learning from industry case studies and keeping up to date with cybersecurity trends. Cyber threats are constantly evolving, and learning from real-world incidents helps organizations adapt and fortify their defenses in the long term.
The Bad | Qakbot Operators Return With Phishing Campaigns Despite International Takedown
One of the longest-established malware and botnet operators, Qakbot, has returned to the cyber threat ecosystem just months after a joint global operation dismantled their server infrastructure. Despite the major disruption, the threat actors behind Qakbot are now reportedly linked to an ongoing phishing campaign that has distributed Remcos remote access trojan (RAT) and Ransom Knight ransomware since August.

According to security researchers, ‘Operation Duck Hunt’ likely impacted QakBot operators’ command-and-control (C2) servers rather than their spam delivery infrastructure. While there is moderate confidence in attributing recent activity to QakBot, there is no evidence indicating that operators have resumed distributing their malware loader since the September takedown.
The recent activity associated with QakBot involves the use of malicious LNK files likely distributed through phishing emails. When these files are executed, they trigger the infection process, ultimately leading to the deployment of Ransom Knight ransomware; a recent rebrand of the Cyclops ransomware-as-a-service (RaaS) scheme. The ZIP archives containing these LNK files have also been observed to include Excel add-in (.XLL) files, which serve to propagate the Remcos RAT. This RAT provides the attackers with persistent backdoor access to compromised endpoints. Some of the file names used in this campaign are in Italian, indicating a potential focus on targeting European users.
Even though QakBot distribution hasn’t been observed post-takedown, the malware is likely to remain a threat in the future. Since the operators are still active, they may opt to rebuild the QakBot infrastructure, potentially resuming their previous activities in the near future. The situation underscores the importance of ongoing vigilance and innovative cybersecurity measures to combat evolving threats.
The Ugly | Released PoC of Critical WS_FTP Vulnerabilities Accelerate the Need to Patch
Ransomware operators are actively exploiting recently fixed vulnerabilities associated with WS_FTP Server, a file-sharing application by Progress Software also known for its MOVEit file transfer tool. A critical zero-day vulnerability found in MOVEit made headlines this summer and has reportedly affected over 600 organizations and 40 million people, with numbers still mounting.
Out of the eight fixed WS_FTP Server vulnerabilities, two were given critical severity ratings. First, CVE-2023-40044 (CVSS score 10) is a .NET deserialization flaw that allows attackers to execute malicious code remotely without requiring authentication. CVE-2023-42657 (CVSS score 9.9) affects directory traversal, permitting remote code execution (RCE) on files outside of their authorized folder path. This flaw, however, requires prior authentication. Shodan currently shows over 2000 devices running WS_FTP Server that are vulnerable to exploitation.
Signs of active exploitation emerged last Friday with attackers attempting to establish a permanent presence on compromised servers since. Subsequently, a proof-of-concept (PoC) exploit began circulating online, furthering the risk of compromise as customers continue to apply patches.
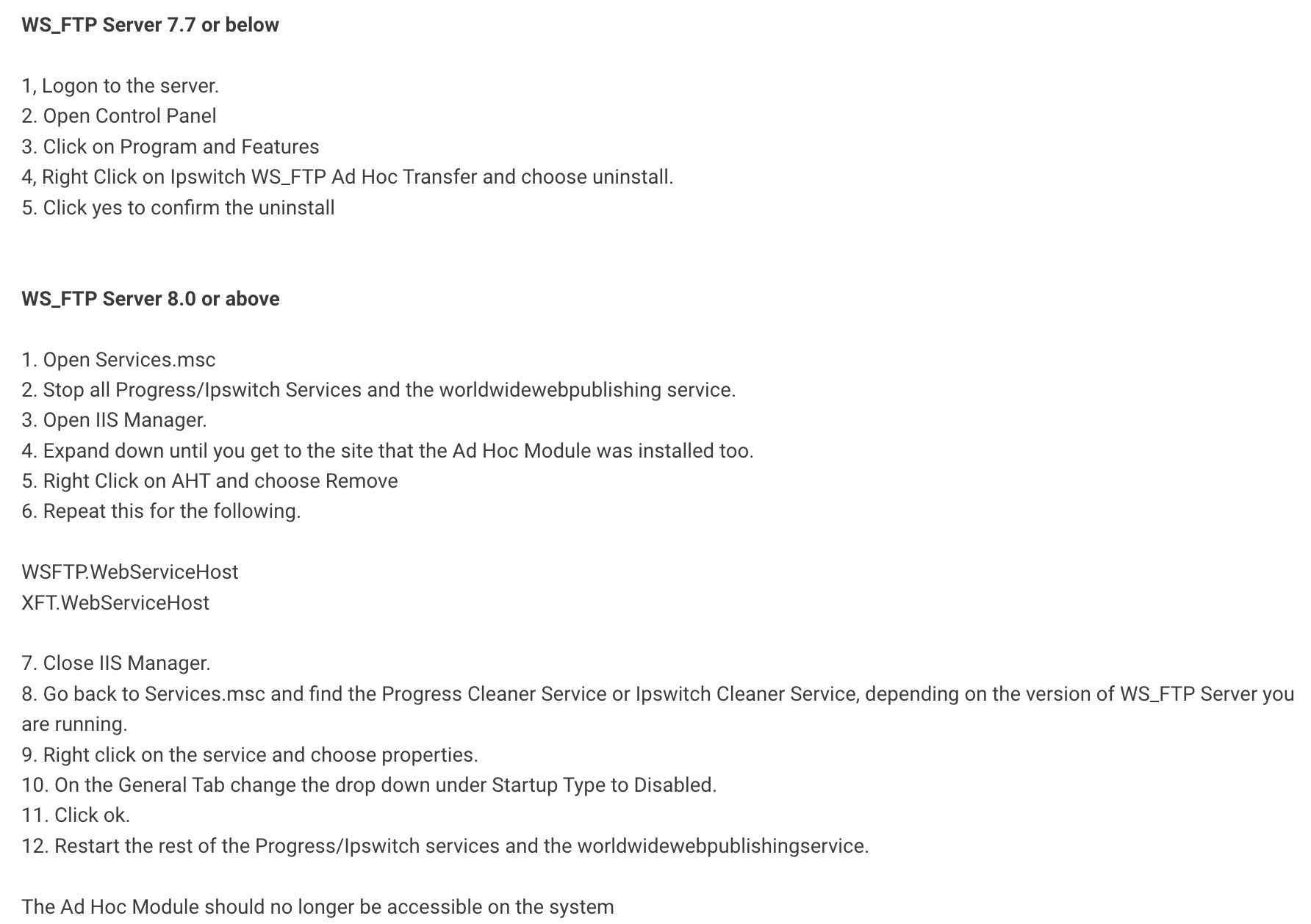
File transfer tools have become a favored target of ransomware attackers as they are often integrated into organizations’ core infrastructure and transmit sensitive data. This raises the stakes for the victim. To avoid data loss and business disruption, victims may give into paying the ransom to quickly regain access. Compared to the MOVEit file transfer vulnerability, the WS_FTP Server vulnerabilities may be less widespread since fixes were made available before exploits began. Still, admins are advised to prioritize patching, disable server-ad hoc transfer mode if immediate patching is not feasible, and thoroughly monitor for signs of compromise.