The Good | White House Launches AI-Centric Cybersecurity Contest to Protect US Entities
The Biden-Harris administration this week announced a new hacking challenge with the purpose of using artificial intelligence (AI) to protect critical US infrastructure from growing cybersecurity threats. In collaboration with tech companies such as OpenAI and Anthropic who are making their technology available for the competition, the “AI Cyber Challenge” (aka AIxCC) offers up to $20 million in prizes for participating hackers. AIxCC will be led by the Defense Advanced Research Projects Agency (DARPA) who have made an additional $7 million available for SMBs looking to compete. The challenge was announced at Black Hat USA 2023 cybersecurity conference in Las Vegas in line with this years’ theme of generative AI.
I’m excited to announce the AI Cyber Challenge, a major, two-year @DARPA competition challenging the best and the brightest in cybersecurity and AI to secure the systems on which all American rely.https://t.co/mZR4ZNSiaM pic.twitter.com/VF1LiSGijh
— Perri Adams @ Black Hat and DEF CON (@perribus) August 9, 2023
The challenge is a practical exercise in demonstrating the potential benefits of AI in securing various software used across all industry verticals. Described by White House officials as being a “clarion call” for organizations to strengthen the security of their critical software, AIxCC plans to leverage the winning code to protect federal and critical infrastructure immediately. As part of the administration’s 2021 executive order on improving the nation’s cybersecurity posture, AIxCC is the latest effort in exploring AI-based security and innovation to mitigate the severe damage and costs associated with modern cyber risks.
The challenge also calls to attention the notion that AI holds potential in helping security professionals remain steps ahead of increasingly sophisticated cyber threat actors only if used safely and responsibly. Earlier this year, NIST launched an AI risk management framework and last month, the administration secured voluntary commitments from leading AI companies to manage the risk posed by the budding popularity of the technology.
Semi-finalists of the challenge can expect to compete at DEF CON 2024 with the final leg of the competition to be hosted the following year at DEF CON 2025.
The Bad | High-Severity RCE Vulnerability Threatens Windows Print Management Software
Earlier this week cybersecurity researchers uncovered a critical vulnerability in a print management software for Windows called PaperCut. Tracked as CVE-2023-39143, the path traversal and file upload flaw allows potential attackers to upload, read, or delete arbitrary files leading to remote code execution (RCE) of the application server.
Exploitation of this vulnerability requires the external device integration to be enabled, which is a default configuration for specific installations of the software. According to the researcher, they estimate that the vast majority of PaperCut installations currently run on Windows with this particular setting turned on. They also note that this vulnerability, though severe, involves multiple issues that must be chained together before server compromise is successful.
The company has strongly recommended their users to patch their installations to version 22.1.3 or later. To check if a server is vulnerable to CVE-2023-39143, use the following command:
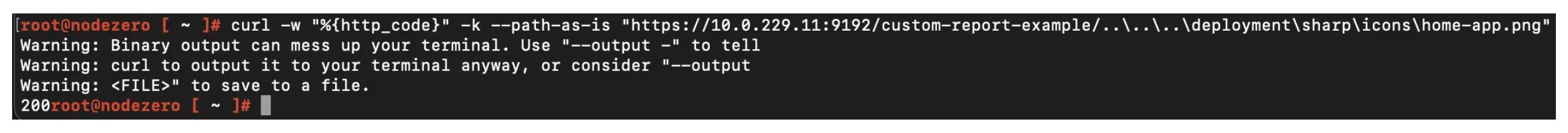
CVE-2023-39143 is the latest in a string of vulnerabilities afflicting the PaperCut software this year. In April, two similar vulnerabilities, CVE-2023-27350 (an RCE flaw) and CVE-2023-27351 (an information disclosure flaw), came under widespread use by ransomware affiliates, most notably Cl0p and LockBit, to deliver Cobalt Strike and ransomware. Nearly two weeks later, the same vulnerabilities were exploited by Iranian-backed threat actors to gain access into targeted networks and exfiltrate corporate data.
SentinelOne customers are automatically protected against both Cl0p and LockBit 2.0 and 3.0 through the Singularity XDR platform which identifies and stops any malicious activities related to either ransomware affiliate.
The Ugly | DPRK-Backed Hack Group Breaches Russian Missile Makers
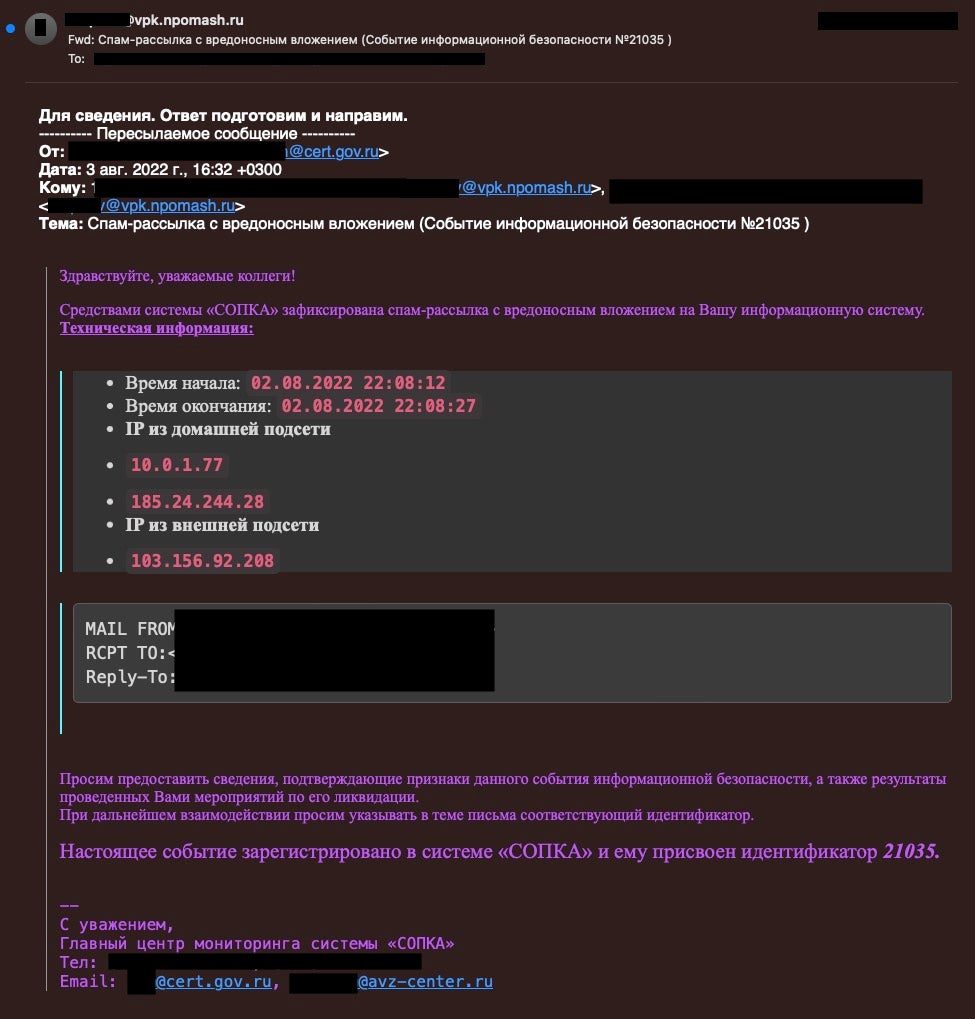
North Korean state-sponsored hacking group, ScarCruft (aka APT37), has been identified as the culprit behind a cyberattack on NPO Mashinostroyeniya, a Russian organization known for designing space rockets and intercontinental ballistic missiles. Despite being sanctioned by the U.S. Department of Treasury due to its involvement in the Russo-Ukrainian war, NPO Mashinostroyeniya fell victim to the attack, which involved planting an ‘OpenCarrot’ Windows backdoor for remote network access.
According an analysis by SentinelLabs, ScarCruft specializes in cyber espionage, targeting and exfiltrating data from various entities as part of its operations though the motives for this campaign are still unclear. The breach was initially discovered when leaked emails from NPO Mashinostroyeniya revealed suspicious network communications and a malicious DLL file installed on internal systems. This prompted further investigation by SentinelLabs, uncovering a more extensive intrusion than the missile makers initially realized.
The backdoor, ‘OpenCarrot,’ is associated with the Lazarus Group, another North Korean hacking entity. While collaboration between ScarCruft and Lazarus hasn’t been confirmed, it’s not uncommon for different North Korean threat actors to share tools and tactics. The ‘OpenCarrot’ backdoor boasts an array of functionalities, including reconnaissance, file and process manipulation, and reconfiguration of command-and-control communications.
Based on SentinelLabs’ assessment, this campaign underscores North Korea’s proactive mission to advance their mission development programs. The collaboration amongst various DPRK-based hacking groups suggests a unified strategy to continue a diverse range of threat campaigns aiming for profound and global consequences.


