The Good
This week, the Cybersecurity and Infrastructure Security Agency (CISA) released the first, in what is to be a series, of Cyber Essentials Toolkits. The agency plans to release new toolkit updates each month. Each toolkit is designed to align with what CISA has deemed the 6 “Essential Elements” of Cyber Readiness. Through each step and module of the toolkit(s), the goal is to walk business leaders, CISOs, and information owners through the process of developing and implementing proper cybersecurity practices and hygiene. By taking these “bite size” baby-steps, organizations should gain the ability to properly manage and understand risk, as well as properly compartmentalize information and resources to complement the lowering of risk and exposure. The 6 “Essential Elements” as defined by CISA are:
- Yourself
- Your Staff
- Your Systems
- Your Surroundings
- Your Data
- Your Actions Under Stress

The first of these toolkits is focused on the Yourself element and is aimed at cybersecurity leaders as well as IT professionals and service providers. The overall project is aimed at C-level executives. If you would like to learn more about the Cyber Essentials Toolkit and related efforts, we encourage you to visit CISA’s site for ongoing updates to this effort.
The Bad
This week’s ‘Bad’ is a critical vulnerability in VMware Cloud Director, disclosed by researchers who say it could allow attackers to fully take over affected infrastructure.
The flaw lies in improper input handling, leading to a state allowing for arbitrary code injection. The flaw can be triggered via maliciously-crafted traffic by way of the Flex and HTML5-based interfaces, as well as via supplied APIs. The vulnerability, assigned CVE-2020-3956, was discovered during a security audit by researchers at Citadelo.
The impact of this vulnerability goes beyond remote code execution. The researchers were able to show that through this flaw it was possible to gain access to external cloud infrastructure. The flaw could be used to gain full access to a vCloud database, manipulate the credentials of a System Administrator account, and ultimately access all hosted customers with full privileges.
In addition to the posted disclosure, Citadelo has posted a detailed PoC to demonstrate the flaw. VMware has released updates to address the issue. All exposed or concerned customers are encouraged to review the posted materials, and follow the recommended guidelines and fixes.
The Ugly
Actors behind the DoppelPaymer ransomware have announced their breach of Digital Management, LLC, an IT service provider based in Maryland. The victim has a number of Fortune 100 clients including NASA. The NASA relationship is specifically called out on the DoppelPaymer blog site.
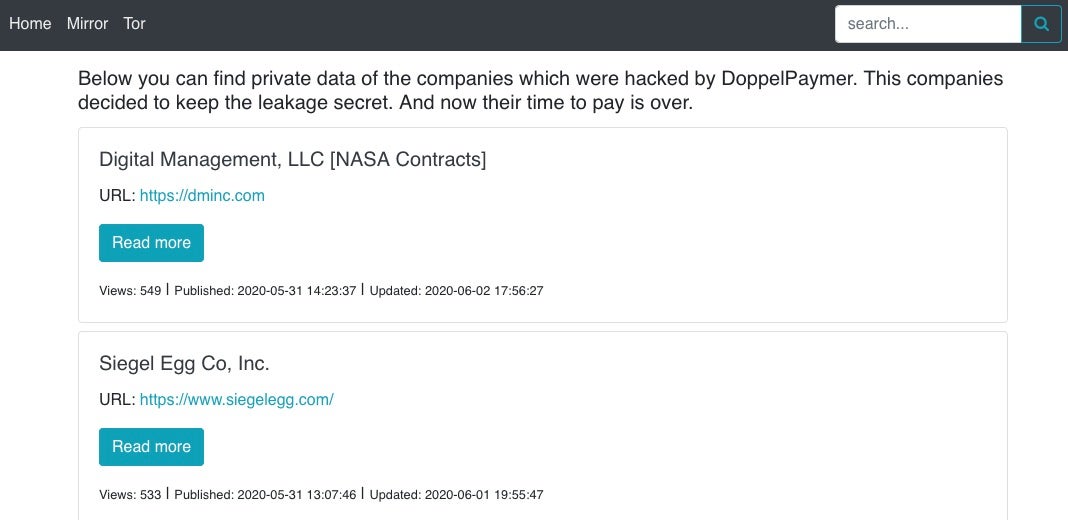
The attackers have posted verified samples of data on the TOR-based blog, and claim to have encrypted 2,583 machines. At the time of writing, the ransomware operators have publicly posted 21 sample files from the hack.
The gang claim to have stolen equipment designs and plans, HR and personnel data, as well as internal documents belonging to both NASA and SpaceX. The sample data appears to span multiple years, from 2016 or earlier to the present day.
Given that Digital Management LLC works within the federal space, compliance and regulatory requirements are much stricter than they are for non-federal entities, so the company could face devastating repercussions both from regulators and from clients. In some ways, these attacks can prove to be as damaging if not more so than many state-sponsored campaigns. While they may lack the stealthy techniques of an APT group, the impact can be just as devastating or even business-ending. Digital Management, LLC are certainly going to find themselves fighting on several fronts as they try to put out the wildfires caused by this breach.


