The Good | Police Disrupt Dark Web Fraud, Government Portal Breaches, and Cryptocurrency Theft
U.S. and international law enforcement have seized BidenCash, a major dark market trafficking stolen credit card data and personally identifiable information (PII). The joint operation took down over a hundred domains and confiscated cryptocurrency linked to the marketplace. Since March 2022, BidenCash facilitated over $17 million in illicit transactions and leaked millions of payment cards to boost their visibility in the ecosystem. Even though platforms like this often re-emerge, the takedown significantly disrupts criminal operations and highlights ongoing efforts to combat financial cybercrime.

Two members of the cybercriminal group ViLE have been sentenced for breaching a federal law enforcement portal. ViLE specializes in doxing, using stolen personal details to harass or blackmail individuals, often by impersonating law enforcement and exploiting insider access. Sagar Steven Singh and Nicholas Ceraolo both pleaded guilty for accessing a DEA portal and leveraging victims’ data to issue threats for payment. Authorities continue the investigation on other ViLE members in the extortion scheme, while both Ceraolo and Singh will serve 25 and 27 months in prison, respectively.
Ukrainian police have arrested a suspect who allegedly compromised more than 5000 accounts through an international hosting company to mine cryptocurrency, leading to $4.5 million in damages. Active since 2018, he used open-source intelligence to find vulnerable systems and deployed virtual machines on compromised accounts. After moving around various Ukrainian cities to evade detection, the suspect maintained multiple profiles on hacker forums but was ultimately linked to evidence including stolen credentials, crypto wallets, and mining tools. He faces up to 15 years in prison, with further charges possible as the investigation continues.
The Bad | BladedFeline APT Targets Iraqi & Kurdish Officials in Strategic Espionage Campaign
A new cluster of cyberattacks targeting Kurdish and Iraqi government officials has been attributed to BladedFeline, an Iran-aligned threat actor believed to be a sub-cluster of the OilRig APT group. In operation since 2017, BladedFeline focuses primarily on long-term espionage against the Kurdistan Regional Government (KRG), various entities in Iraq, and government organizations within Azerbaijan.
BladedFeline is known to employ a diverse malware toolkit, including backdoors like Shahmaran, Whisper, Spearal, and Optimizer, each offering remote code execution (RCE) and data exfiltration capabilities. The threat group has also deployed newer implants like Slippery Snakelet and Hawking Listener, as well as tunneling tools Laret and Pinar for persistence. Other than using backdoors, BladedFeline is also often seen using PrimeCache, a malicious IIS module that monitors HTTP requests for attacker commands, highlighting the group’s tactics for maintaining stealth and persistence.
The geographic breadth and technical depth of their most recent campaign is typical for BladedFeline operations as they have simultaneously maintained access to Kurdish diplomatic officials, infiltrated Iraq’s governmental networks, and compromised a regional telecom provider in Uzbekistan. In the latest attacks, operations suggest goals of obtaining diplomatic and financial intelligence to serve Iran’s strategic interests, particularly in countering Western influence. Though initial access methods to reach the Kurdistan Regional Government (KRG) remain unclear, security researchers tracking the campaign suspect exploitation of internet-facing applications.
BladedFeline’s targeting reflects an espionage-centric objective, one focused on gathering intelligence from high-ranking officials in both the KRG and the Iraqi central government. The KRG’s strong diplomatic ties with Western nations and control over valuable oil reserves make it a strategic target for Iran-aligned actors seeking to monitor, influence, or disrupt foreign partnerships in the region.
The Ugly | Attackers Flood Open-Source Repos with Malware to Target Crypto, CI/CD & Developers
A string of supply chain attacks is exfiltrating Telegram API data as threat actors weaponize open-source package repositories including npm, PyPI, and Ruby. After hijacking trusted developer infrastructure and implanting persistent malware, attackers are draining their victims’ cryptocurrency wallets before wiping entire codebases.
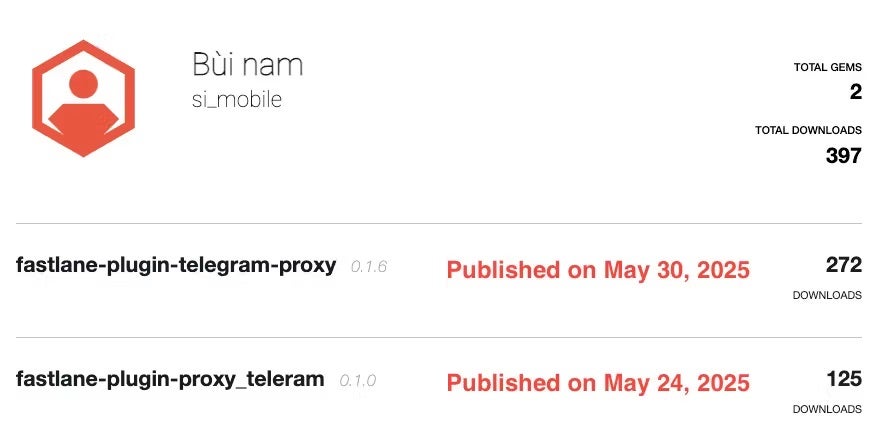
On RubyGems, attackers uploaded clones of a legitimate Fastlane plugin to steal Telegram APIs. These packages work by rerouting communications through a command and control (C2) server under the guise of being proxies following a Telegram ban across Vietnam. Security researchers have linked the campaign to a user operating under several aliases while warning of its broad impact due to lack of geofencing.
Malicious npm packages, such as xlsx-to-json-lh, have also been observed triggering destructive payloads capable of erasing entire project directories. Others, tied to the @crypto-exploit account, drained Ethereum and BSC wallets using obfuscated JavaScript, some having existed for years before removal. On PyPI, attackers published Solana-themed packages under aliases like “cappership”, with payloads that silently steal private keys via runtime function patching. Some malware embedded stolen keys in Solana Devnet transactions for later retrieval.
What’s most notable about the campaign is the use of AI tools to poison the software supply chain, masquerading the malicious PyPI packages as Python software development kits (SDKs). These packages embedded info-stealing payloads inside PyTorch models – a novel delivery method that abuses the insecure deserialization behavior of machine learning (ML) formats. By hiding malware within ML assets and retrieving metadata tied to malicious applications, the attackers can combine social engineering, typosquatting, and targeted telemetry to evade detection and zero in on likely victims.
This approach marks a new edge to supply chain attacks, where machine learning models themselves are becoming the vehicle for compromise.


