The Good
Let’s clap for Romania’s cyber cops this week as they arrested a gang of criminals for targeting hospitals with notorious Locky ransomware, among a number of other misdemeanours. The Directorate for Investigating Organized Crime and Terrorism (DIICOT) raided houses in Romania and Moldova, arresting four people allegedly involved in the crimes and calling themsleves “Pentaguard”.
Aside from putting lives in danger by targeting healthcare services, the “Pentaguard” gang were also suspected of compromising and defacing websites belonging to public and government bodies as well as financial services and education providers.

The Bad
“This is why we can’t have nice things” is one of those memes that seems to be everywhere these days, and is particularly apt to the news that advanced hacking group Winnti are targeting their sophisticated malware at…games developers. At first blush, that might seem an odd target group for malware that takes considerable skill and effort to create and comes with the risk of being ‘burned’ (i.e., known to security solutions) shortly after use. Typically, such resources are only expended on highly valuable, corporate or organizational targets where the threat actors know the prize will far outweigh ‘the cost of doing business’ and deliver guaranteed ROI.
However, Winnti has something of a track record in this regard, and this week’s reports suggest that the malware, which persists by leveraging Windows printer drivers that run on every boot, may be used not only as part of a supply-chain attack but also to profit by manipulating in-game currencies. As one forum commenter astutely noted, massive multiplayer online games platforms have an install base of hundreds of millions of users, run software at highly privileged levels and deploy forced or automatic updates that users rarely if ever scrutinize. From a malware author’s or botnet builder‘s point of view, what’s not to like?
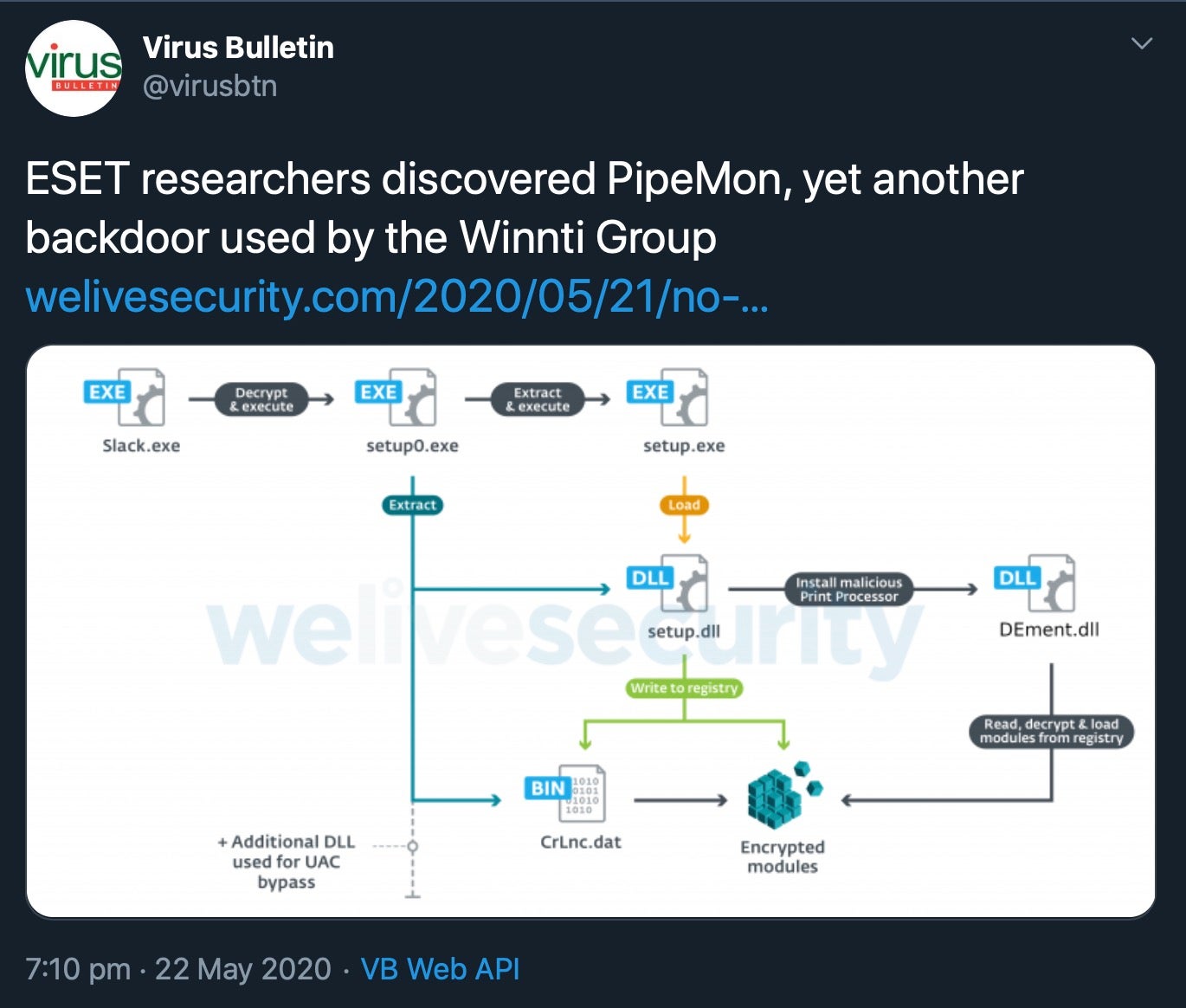
The new Winnti malware uses a novel backdoor, dubbed PipeMon on account of the numerous pipes it uses to communicate between modules. PipeMon itself was seen to be installed with a legitimate Windows signing certficate stolen from Nfinity Games in a hack dating back to 2018. Despite the long interval since then, the stolen code-signing certificate had still not been revoked.
The Ugly
It’s time for this week’s Ugly breach news, starting with UK aviator, EasyJet. Britain’s largest airline has leaked something in the region of 9 million customer email addresses along with their travel data, it was revealed this week. Among the leaks, an estimated 2,208 customers also had their credit card details exposed, so this is likely a lucrative payday for the cyber criminals. EasyJet say they have complied with local breach notice regulations and all customers who have been affected will receive notice by May 26th. In light of the breach, EasyJet customers should be extra vigilant for phishing emails and pay close attention to credit card statements for signs of fraudulent transactions.
 Credit: Getty
Credit: Getty
Meal-kit delivery specialists Home Chef were the latest to confirm a data breach this week that was first announced by previously unheard of darknet data broker ShinyHunters. The group have been teasing a number of large data breaches throughout May on various criminal forums, but some of their early leaks proved to be of little value. The claim to have 500GB of Microsoft source code, for example, was met with skepticism when the 1GB sample they publicly dropped turned out to be little more than material that had been scheduled for publication.
However, Home Chef and a string of other well-known sites have started offering confirmations to back up some of the ShinyHunters’ other claims. Researchers suspect that ShinyHunters’ sudden appearance as a “big league” player in the murky world of criminal data trading is evidence of an experienced operator trying on a new identity. Regardless, such breaches will undoubtedly serve to pile on the worry for affected customers while causing unfortunate reputational damage to the breached organizations.


