The Good | Global Authorities Disrupt Major Botnet, Ransomware Actor & Dark Web Marketplace
In a wave of cybersecurity wins, recent actions by international law enforcement have disrupted several long-running cybercrime operations, arrested key suspects, and dismantled major infrastructure used in global attacks.
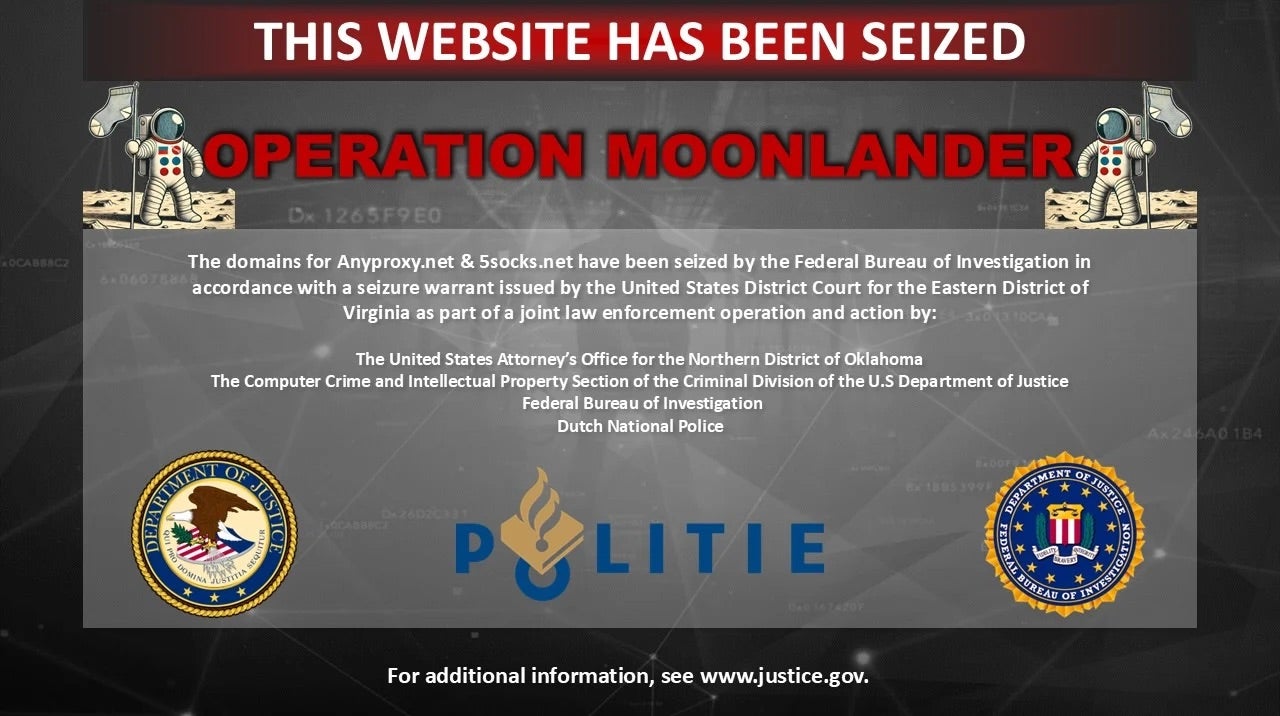
U.S. and international authorities have dismantled a botnet active since 2004 responsible for infecting thousands of routers to create two illegal residential proxy services: Anyproxy and 5socks. Four individuals were indicted for operating and profiting from the scheme, which earned over $46 million. The botnet, controlled via malware-infected routers, provided anonymous access for cybercriminals engaged in ad fraud, DDoS attacks, and other crimes. All part of joint “Operation Moonlander”, the network is now offline and the suspects face charges in the U.S.
In Moldova, authorities arrested a 45-year-old foreign national linked to the 2021 DoppelPaymer ransomware attack on Dutch organizations, including the Dutch Research Council (NWO), which suffered €4.5 million in damages. The arrest was part of a joint operation with Dutch law enforcement and an extradition process to the Netherlands is currently underway. DoppelPaymer, tied to the Evil Corp gang, used stolen data to extort victims and rebranded multiple times while continuing attacks through 2022.
Kosovo national Liridon Masurica, also known as @blackdb, has been extradited to the U.S. to face charges for operating BlackDB.cc, a cybercrime marketplace active since 2018. Arrested in December 2024 and extradited on May 9, Masurica has appeared in court to face charges of access device fraud and conspiracy. BlackDB.cc sold stolen credit card data, account credentials, and personal information used for fraud and identity theft. If convicted, he faces up to 55 years in prison. His arrest follows broader international efforts to dismantle illegal cybercrime markets.
The Bad | Malicious NPM Package Hides Multi-Stage Malware in Unicode & Google Calendar
Security researchers have uncovered an attack involving a malicious NPM package named os-info-checker-es6 that is disguised as a benign operating system information utility. Initially harmless when published on March 19, 2025, it was modified a few days later to include obfuscated install scripts and platform-specific binaries, before a new version was published on May 7, which began delivering malicious payloads.
The attack uses invisible Unicode characters (U+E0100 to U+E01EF) in a preinstall.js file to hide code that ultimately reaches out to a Google Calendar event short link. The link acts as a dead drop resolver, directing infected systems through redirects until a valid response is received. The payload’s final URL is hidden in the data-base-title attribute of the calendar event, encoded in base64.
The decoded link points to a command and control (C2) server – an evasion tactic leveraging Google’s infrastructure to obscure attacker activity. The malware then uses the JavaScript eval() function for execution and includes a basic persistence mechanism to avoid multiple instances running simultaneously. While the final payload couldn’t be retrieved during analysis, researchers believe the campaign is either dormant, selectively active, or still under development.
So far, the malicious package is now at v1.0.8 and has been downloaded approximately 655 times per week. It is also listed as a dependency in four other suspicious packages: skip-tot, vue-dev-serverr, vue-dummyy, and vue-bit. Despite the findings, the packages remain live on the NPM registry. This campaign highlights growing attacker sophistication in the open-source ecosystem and serves as a reminder for developers to vet all third-party packages.
The Ugly | Cyberspies Leverage Zero-Day in Enterprise Messaging App to Target Kurdish Military
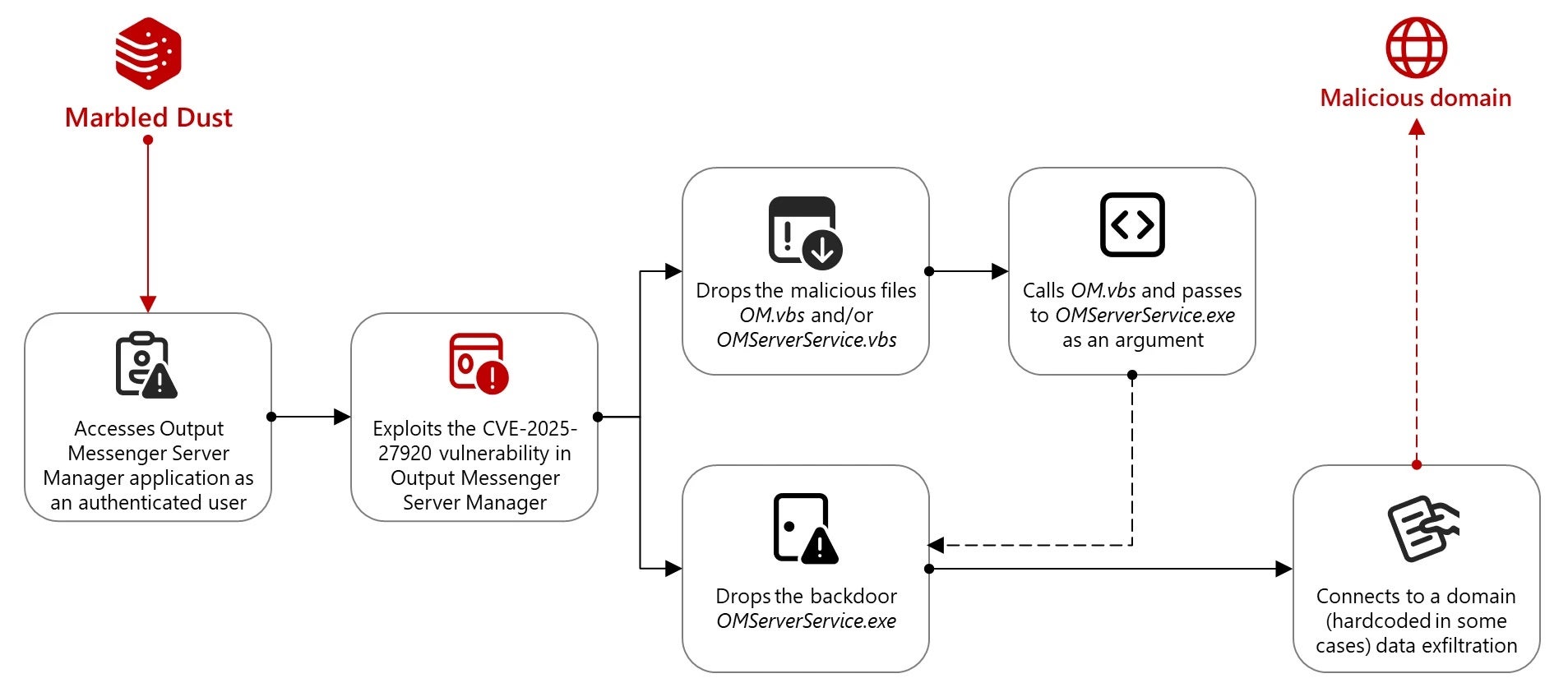
Türkiye-based cyberespionage group Marbled Dust (aka Sea Turtle, UNC1326, and Silicon) is exploiting a zero-day vulnerability in Output Messenger to target users associated with the Kurdish military in Iraq. The campaign has been operating since April and is consistent with the threat actor’s tendency to target government, IT, and telecom sectors across the Middle East and Europe, with a particular focus on Kurdish entities.
The vulnerability (CVE-2025-27920) is a directory traversal flaw in version 2.0.62 of Output Messenger that allows authenticated users to access or execute arbitrary files outside intended directories. Research indicates that the group likely gained access through DNS hijacking or typosquatted domains to intercept credentials before using the Output Messenger Server Manager interface to drop malicious payloads on targeted systems.
After securing access, Marbled Dust deploys a Golang-based backdoor (OMServerService.exe) that communicates with a C2 server (api.wordinfos[.]com) to exfiltrate data and issue further commands. In one case, the malware archived and transmitted files to an attacker-controlled IP address shortly after installation. A second backdoor, OMClientService.exe, was also used on client devices. Although the app’s developer Srimax addressed the vulnerability several months ago, unpatched systems allowed Marbled Dust attackers to access user communications, impersonate users, and cause operational disruptions.
While their core tactics, such as DNS hijacking and credential theft, remain unchanged, the use of a zero-day exploit reflects a significant boost in Marble Dust’s technical capabilities. This campaign also signals a shift in urgency or strategic focus, suggesting that their objectives may now involve higher-value targets or more time-sensitive intelligence collection.