The Good | Joint Crackdown Disrupts Major DDoS-for-Hire Network & Arrests Four
Polish authorities have arrested four cybercriminals accused of working through DDoS-for-hire platforms to launch thousands of attacks worldwide. The six platforms in total, Cfxapi, Cfxsecurity, neostress, jetstress, quickdown, and zapcut, have all been dismantled as a result of coordinated efforts involving law enforcement from Poland, Germany, the Netherlands, and the U.S.
Distributed Denial of Service (DDoS)-for-hire platforms are often disguised as legitimate testing tools on dark web forums and used to overwhelm websites, servers, and online services with traffic, making them inaccessible. Europol stated that these platforms (aka ‘stressers’ or ‘booters’) offered easy-to-use interfaces that did not require any technical expertise beyond payment. All the buyer had to do was enter a target’s IP address and select their attack parameters for as low a cost as €10.
The data obtained by Dutch authorities from these platforms has been shared with international partners, leading to the arrest of four suspects in Poland. In the U.S., police have seized nine related domains, while German officials continue to identify suspects and exchange intelligence. The Netherlands also took a unique approach by creating fake booter sites to deter potential users.
This latest blow to the DDoS market is attributed to Operation PowerOFF, a long-standing international campaign against such service platforms that kicked off in 2018. The operation has previously led to the takedown of multiple services, including DigitalStress and Dstat.cc, and the seizure of dozens of associated domains. These recent arrests and disruptions mark another step in the ongoing effort to hinder the global reach that DDoS-for-hire gives to illicit buyers.
The Bad | PowerSchool Extortion Escalates as Hacker Targets Individual School Districts
A warning from PowerSchool says that the hacker responsible for its December 2024 data breach is now directly extorting individual school districts, threatening to release sensitive student and teacher data unless additional ransoms are paid.
In response, PowerSchool expressed regret that its customers are being re-targeted and reiterated that the case has been reported to law enforcement in both the U.S. and Canada. Affected schools include North Carolina districts and the Toronto District School Board (TDSB), Canada’s largest. The company continues to work with authorities and school partners to mitigate the fallout and has offered two years of free credit monitoring and identity protection to affected individuals.
PowerSchool acknowledged it had paid a ransom shortly after the December breach, hoping to prevent the release of stolen data. At the time, the attacker provided a video supposedly proving data deletion. However, the current extortion wave suggests the data was never actually erased.
The source of the December breach was traced back to compromised credentials used to access PowerSchool’s PowerSource support portal and its remote maintenance tools. The attackers downloaded extensive data, including names, contact details, social security numbers, grades, and even medical information in the breach. In total, the theft affected over 6,500 school districts and touched millions of student and teacher records.
The FBI and security experts warn that paying ransoms does not guarantee data deletion, highlighting similar incidents where attackers will re-extort their victims despite initial payments. Instead, victims are urged to file a report at ic3.gov and request assistance from their local FBI field office.
The Ugly | Global Crypto Phishing Campaign Drains Wallets via SEO, AI & Free Hosting
Joint research from SentinelLABS and Validin this week pulled back the curtains on a global, long-running cryptocurrency phishing operation dubbed ‘FreeDrain’, which targets digital wallets by exploiting search engine optimization (SEO) and free-tier web hosting services. The campaign is representative of modern and scalable phishing built on exploiting weaknesses in free publishing platforms.
FreeDrain lures victims that are searching for common wallet-related terms by pushing malicious links to the top of search engine results. These links lead to professionally crafted landing pages hosted on trusted platforms such as GitBook, Webflow, and GitHub. Victims are then redirected through several layers to phishing sites that mimic legitimate crypto wallet interfaces before they are tricked into entering their wallet seed phrases. This grants attackers immediate access to drain their victim’s funds within minutes.
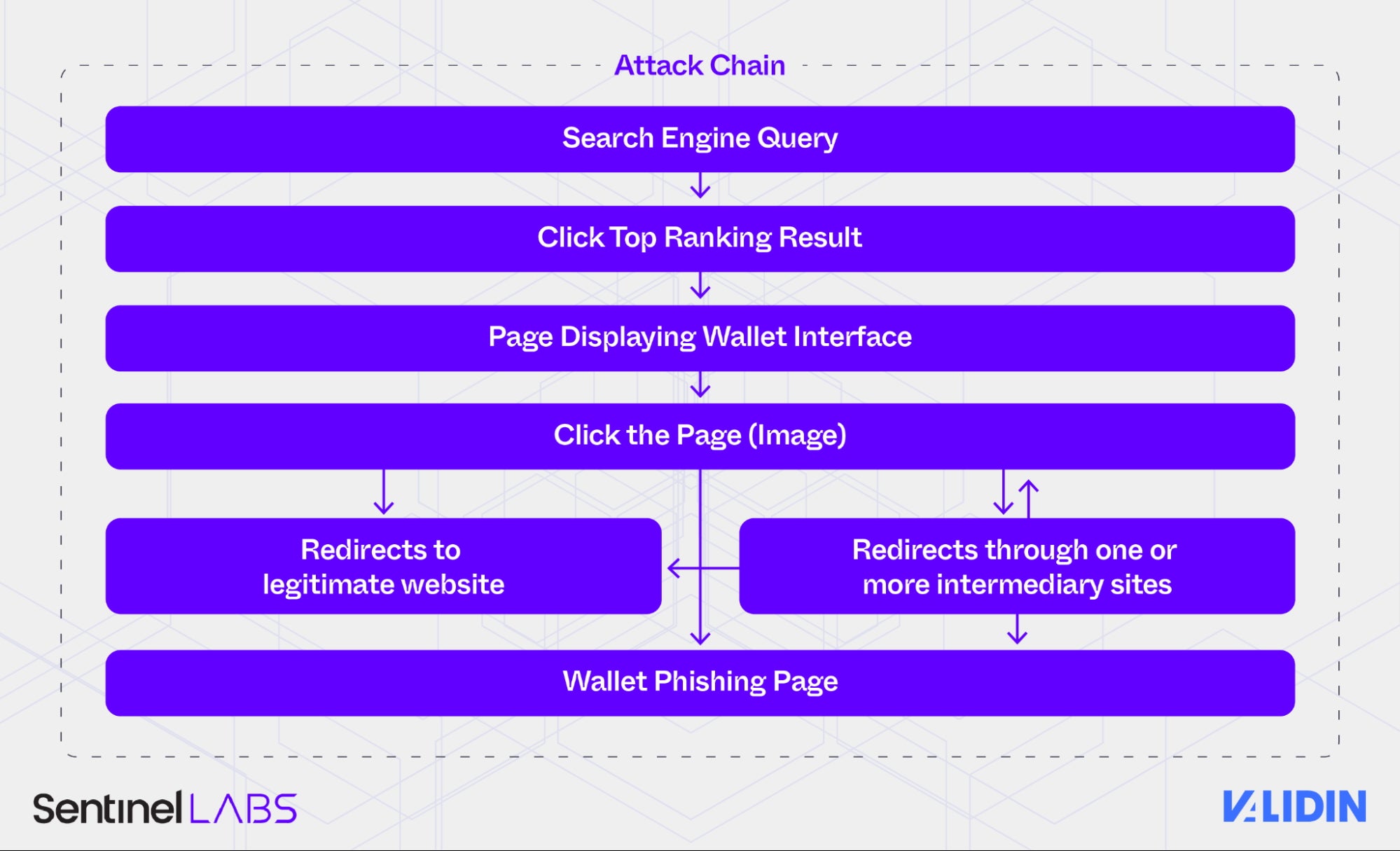
One notable element of the FreeDrain campaign is the use of spamdexing – flooding vulnerable websites with comments to manipulate SEO rankings – and possibly employing AI tools like GPT-4o to generate realistic content. The researchers have identified over 38,000 subdomains used in the campaign, many of which are hosted on cloud infrastructure like Amazon S3 and Azure Web Apps.
Based on commit patterns, the operation appears to be run by actors based in the Indian Standard Time working standard weekday hours. In addition, timeline analysis shows that FreeDrain operators have been active 2022 at least, with a spike in activity starting mid-last year. As of this writing, the campaign is still active across many free hosting and publishing platforms.
Campaigns like FreeDrain reveal how cybercriminals are weaponizing AI, cloud services, and social platforms for large-scale crypto theft. It also exposes a broader industry need for free-tier platforms to implement abuse detection, streamlined reporting, and stronger collaboration with researchers. A full list of IoCs can be found here.




