The Good
On May 3, 2022, the United States Security and Exchange Commission (SEC) announced that it is adding twenty roles to their specially focused Crypto Assets and Cyber Unit.
The SEC formed its Cyber Unit in 2017, and recently renamed the division to reflect a new focus on investigating securities law violations as they relate to crypto asset offerings and exchanges, crypto-lending and staking products, and digital assets, along with up-and-coming platform offerings like non-fungible tokens (NFTs), decentralized finance (DeFi) platforms and stablecoins.
According to a statement by SEC chair Gary Gensler, “As more investors access the crypto markets, it is increasingly important to dedicate more resources to protecting them.”
The statement also noted that the Crypto Assets and Cyber Unit has already brought dozens of cases against SEC registrants and public companies that sought to take advantage of investors in crypto markets and failed to maintain adequate security measures.
Gensler added, “By nearly doubling the size of this key unit, the SEC will be better equipped to police wrongdoing in the crypto markets while continuing to identify…issues with respect to cybersecurity.”
In other news, CyberWire announced that it will be releasing CISA Flash cybersecurity alerts in audio form. The alerts are available in downloadable or podcast form on the CyberWire website. Many thanks to CyberWire for providing this free public service. It is a great example of community members working for the greater good of the threat landscape.
The Bad
Sixt, a large player in the car rental and ride-hailing industry with approximately 2,000 locations in over 100 countries, disclosed that it was heavily impacted by a ransomware attack this week.
Reports indicate that an attack occurred on April 29, 2022. As a result, Sixt was forced to restrict access to all but the most critical IT systems.
Since then, the company has been working to remedy the disruption that Sixt employees and customers are facing. While the company claims they kept all outages to a minimum, Sixt cautioned that their customer care centers and branches could see temporary disruptions as remediation continues.
Reports indicate that Sixt was responding to phone inquiries with a recorded message stating that services were unavailable due to technical issues, and prompted callers to send their questions via email. In the interim, the company has also had to resort to processing bookings and transactions through pen and paper.
At the time of publication, there is little public information with regards to attribution or the source of the attack.
In other bad news this week, security experts noticed the emergence of Mindware, a new ransomware variant. Samples were observed as early as April 4th. The group responsible launches multi-pronged attacks, encrypting, extorting and publicly posting victims’ data.
The Ugly
According to a recent report from the Internet Crime Complaint Center (IC3), Business Email Compromise (BEC) still looms large as a major presence in the threat landscape.
The IC3’s newest data indicates that BEC accounts for the highest total victim losses across multiple categories of cyber crime. The report also states that BEC campaigns increased 65% between mid 2019 and the end of 2021, with yearly losses reaching approximately 26 billion USD.
The IC3 also detailed how BEC threat actors have evolved to get around existing preventative measures. To provide one example, the IC3 discussed a case where fraudsters leveraged virtual meeting platforms to hack emails, spoof business leaders’ credentials, and initiate fraudulent wire transfers. The transferred funds were immediately directed to cryptocurrency wallets and quickly dispersed, complicating recovery efforts.
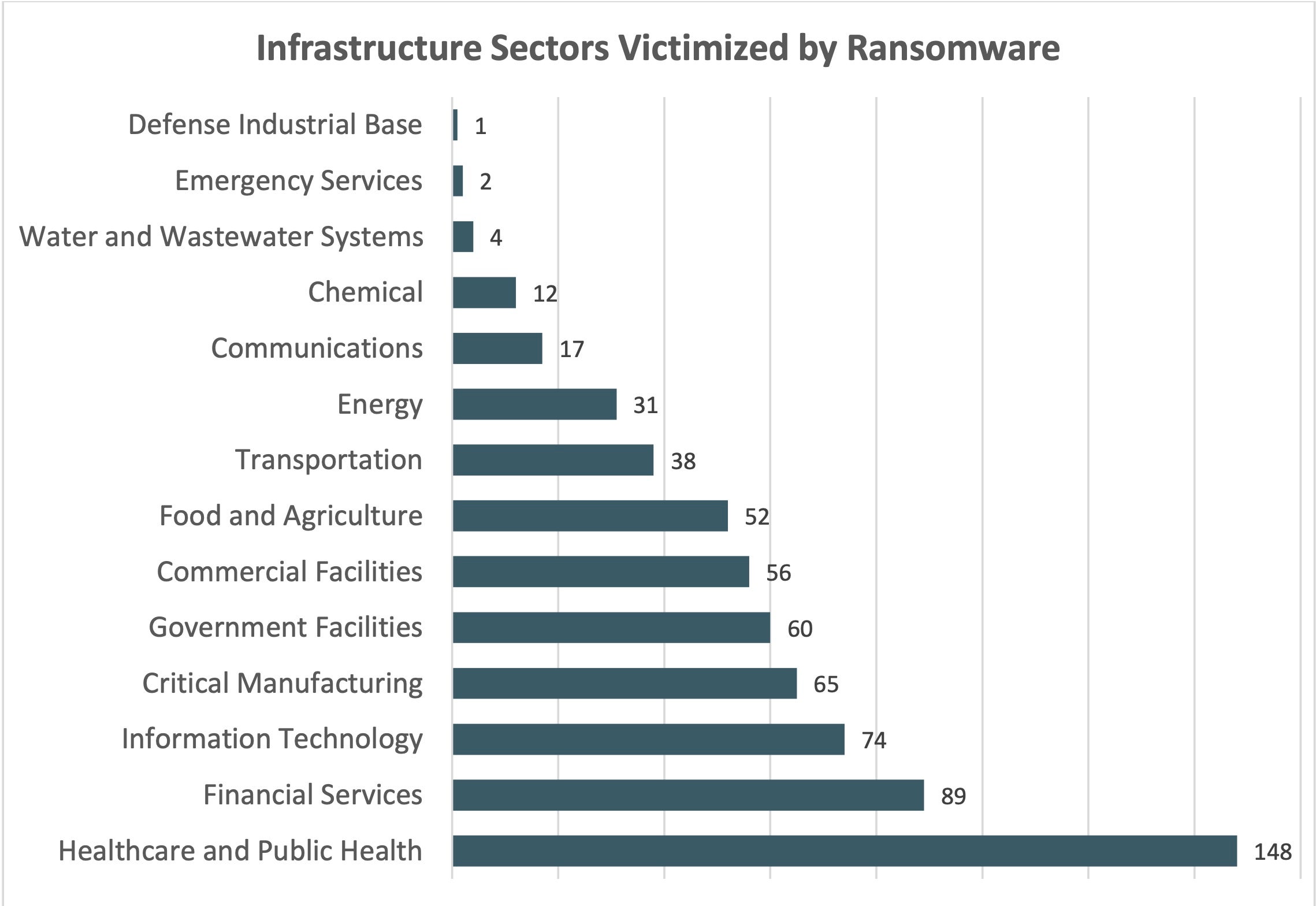
There are a number of startling and unsettling results in this report. For example, the IC3 found that healthcare, public health, financial services, government facilities and critical manufacturing are the top targeted infrastructure verticals victimized by ransomware.
The IC3’s report goes on to indicate that Hong Kong and Thailand appear to be the top “final destinations” for fraudulently acquired funds. The report also provides updates on how attackers are using RATs more aggressively, as well as the ongoing use of COVID-19 as a social engineering lure.
The updated 2021 Internet Crime Report is currently available from the IC3 website. We encourage all to review the report and take any necessary action.