The Good | CVE & CWE Programs Receive Funding from CISA to Ensure Continued Operation
Up until a few days ago, the global cybersecurity community was bracing for widespread disruption – U.S. government funding for the Common Vulnerabilities and Exposures (CVE) and Common Weakness Enumeration (CWE) programs was set to expire on April 16, 2025. Without renewed funding, both programs would have faced an abrupt shutdown. Both of these projects are maintained by MITRE and are critical for tracking and communicating software vulnerabilities in an accurate and standardized manner.
CVE is more than a database, it’s the common language for cybersecurity, assigning standardized identifiers (CVE IDs) to vulnerabilities. This shared vocabulary allows cybersecurity defenders, vendors, and threat researchers around the globe to coordinate efforts and respond swiftly to threats. Not only is CVE deeply integrated into various cybersecurity tools, vulnerability management systems, and incident response operations for critical infrastructure, it is a long-established global library of cybersecurity knowledge.
Fortunately, CISA extended MITRE’s contract before the expiration, ensuring uninterrupted service for at least the next 11 months. CISA also reaffirmed CVE’s priority status and secured incremental funding to keep the program running. With the near-interruption triggering a broader conversation about CVE’s long-term sustainability, members of the CVE Board have since announced the launch of the CVE Foundation, a nonprofit aimed at transitioning CVE to a more independent and globally neutral model.
— Cybersecurity and Infrastructure Security Agency (@CISAgov) April 16, 2025
With funding extended and momentum for governance reform growing, the outlook has shifted from uncertainty to cautious optimism. What’s next is a critical opportunity to solidify CVE’s future, moving beyond stopgap funding toward a more resilient, community-driven framework that can keep meeting the needs of a rapidly evolving threat landscape.
The Bad | Attackers Abuse Popular AI-Based Presentation Tool to Enhance Phishing Campaigns
As the adoption of AI continues to climb across industries, cybercriminals are leveraging these tools to enhance the effectiveness of their phishing and spam campaigns. Most recently uncovered is a case involving the abuse of Gamma, an AI-powered presentation tool, in a phishing campaign targeting Microsoft users.
Attackers were observed sending phishing emails, sometimes from compromised legitimate accounts, that included a PDF attachment. Instead of containing a legitimate document, the PDF linked to a Gamma-hosted presentation prompting users to review the ‘secure’ documents.
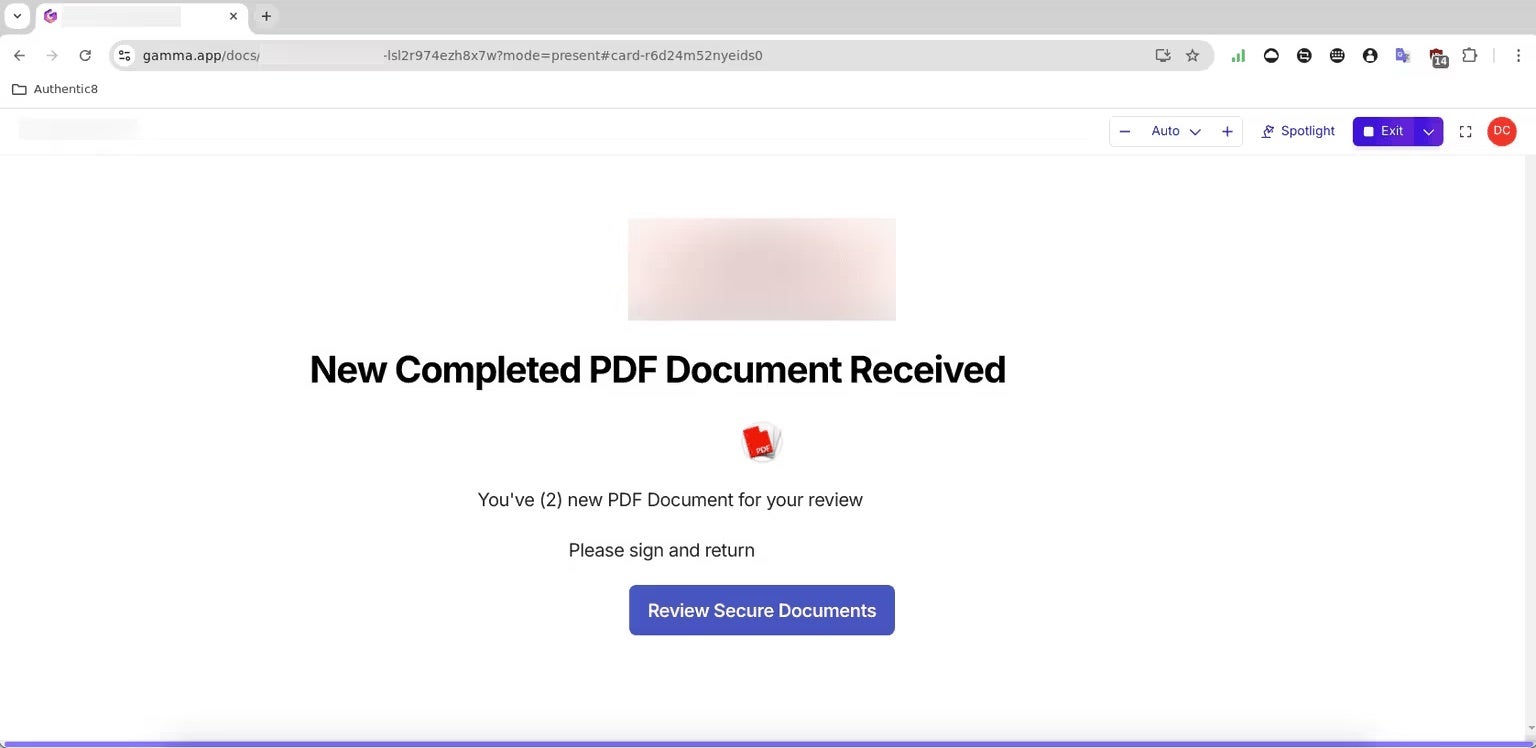
Clicking the prompt redirected victims to a spoofed Microsoft splash page protected by a Cloudflare Turnstile CAPTCHA, thus adding credibility and thwarting automated scans. From there, users were led to a fake SharePoint log-in page. Incorrect password attempts trigger real-time validation errors, indicating the use of an adversary-in-the-middle (AiTM) setup to harvest credentials. By abusing trusted platforms like Gamma and Cloudflare, the attackers were able to bypass email security checks such as SPF, DKIM, DMARC, by using a living-off-trusted-sites (LOTS) strategy to stay under the radar.
This trend parallels another AI-abuse campaign involving AkiraBot, a Python-based framework that recently targeted over 400,000 websites within the last 7 months via OpenAI-generated messages to flood contact forms and chat widgets with dubious SEO service promotions.
Together, these campaigns are a snapshot showing how AI is transforming the cyber threat landscape – not just in content generation, but also delivery tactics and evasion techniques. Whether it’s phishing via polished AI presentations or spam via LLM-crafted outreach, attackers are rapidly adapting to popular tools and platforms quickly being adopted by global organizations.
The Ugly | China-Linked Mustang Panda Launches New Tools to Target Myanmar
A recent cyberattack targeting an organization in Myanmar is now linked to Chinese-based APT, Mustang Panda (aka Bronze President, Earth Preta). The attack uses an updated backdoor and a suite of previously unreported tools, highlighting the group’s continued efforts to enhance its malware capabilities and evade detection.
Zscaler researchers present the second part of a series on Mustang Panda tools. This time they analyse two new keyloggers, PAKLOG and CorKLOG, as well as an EDR evasion driver (SplatCloak). https://t.co/ni8tV0XVIH pic.twitter.com/841bhFetTp
— Virus Bulletin (@virusbtn) April 17, 2025
In a two-part analysis, security researchers noted all-new variants of TONESHELL – Mustang Panda’s bespoke next-stage backdoor. Of the three variants, the first acts as a basic reverse shell, the second downloads and injects DLLs into legitimate processes, and a more advanced third variant communicates with a remote server via a custom TCP-based FakeTLS protocol.
Mustang Panda has also been observed leveraging a new tool dubbed StarProxy, which enables lateral movement and traffic proxying between infected devices and command and control (C2) servers. A post-compromise tool, it allows attackers access to internal workstations while using custom XOR encryption and command-line configuration for stealthy communication.
The attack also showed use of two new keyloggers known as PAKLOG and CorKLOG. Both monitor and collect keystrokes and clipboard data but lack built-in data exfiltration. CorKLOG, however, encrypts stored data using RC4 and ensures persistence through scheduled tasks or services. Finally, rounding out the toolset is SplatCloak, an EDR evasion kernel driver deployed via SplatDropper. Mustang Panda attackers used this to disable security mechanisms in Windows Defender and Kaspersky, bypassing detection by removing hooks and callbacks.
Mustang Panda has been active since at least 2012, and known to frequently target governments, NGOs, and minority groups in East Asia. Known for techniques like DLL sideloading and customized PlugX malware, the group continues to evolve its toolkit, blending their operational effectiveness with a strong emphasis on obfuscation and stealth. A list of IoCs can be found here.


