This week, we saw another victory for law enforcement against the evil lurking in the deep, dark web, or to be more specific, the DeepDotWeb. This past Wednesday, the United States Department of Justice announced a guilty plea from one Tal Prihar. The Israeli citizen, who is currently residing in Brazil, has been identified as a co-owner and co-operator of the DeepDotWeb website.

The site was arguably the most popular hub for dark web market news, market statuses, links and more. Operated by Prihar and another individual, Michael Phan, the site took nearly $8 million by providing direct and referral links to other sites selling illicit goods.
As a result of the referrals, other highly-successful marketplaces would provide a payment (kickback) to Prihar and Phan. These markets specialized in the peddling of automatic weapons, malware and exploits, along with pharmaceuticals and hard drugs, and included notorious dark web sites such as Dream Market, Valhalla, Abraxas, Agora and Alpha Bay. As such sites aren’t indexed by search engines and consequently are difficult to find, DeepDotWeb effectively provided an entrypoint for internet users to discover sources of illicit trade.
In order to obfuscate the trail of Bitcoin payments received for their referrals, Phan and Prihar laundered the funds through bank accounts for shell corporations, as well as crypto wallet anonymizer services.
Both individuals have pleaded guilty to conspiracy to commit money laundering and each faces a maximum sentence of 20 years. This is a significant law enforcement victory, and one of the more significant takedowns in dark web history!
The Bad
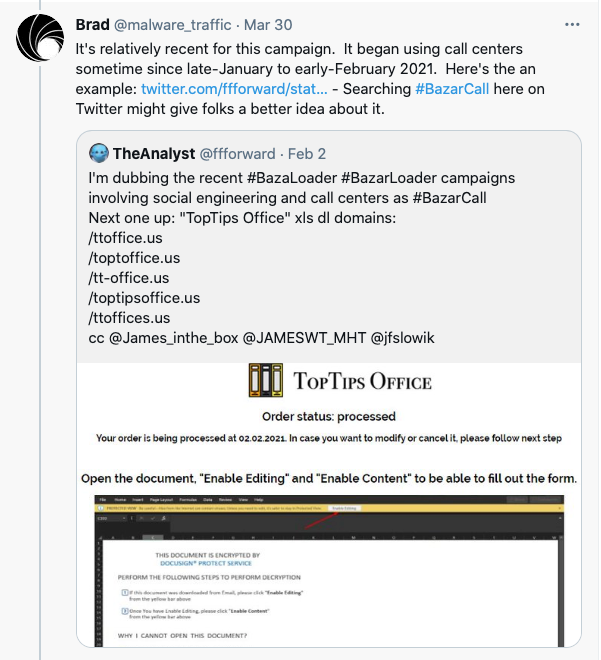
This week more details emerged of a recent malware campaign called BazarCall. By the name, you might guess that BazarLoader will appear somewhere in the infection chain, and you would be correct. However, the actual delivery of the desired payload takes a somewhat roundabout trip towards its intended targets and is coordinated via a threat-actor controlled call center.
The BazarCall campaign begins with a spray of phishing emails to corporate addresses which entice the recipient to phone a call center in order to complete the cancellation process for some fictitious subscriptions.
When the victim contacts the number provided, they are asked for a unique ID contained in the phishing email. This ID allows the individual on the other end of the phone to identify if the caller is truly part of the targeted organization. If they are, the user is instructed to visit a specific, malicious web page to proceed with the process.
At this point, the victim will be prompted to download and open a maliciously-crafted MS Office document. Under the correct conditions, the opening of this document will further lead to the install of BazarLoader malware, which itself may be a precursor to threats like TrickBot, Ryuk, Conti or IcedID.
This shows us (once again) just how much threat actors behind modern malware are willing to go to further their cause and maximize their footprint. To fully staff a call center, focused on intake for high-volume phishing attacks, is somewhat impressive for a non-nation state actor. Researchers believe that the call center infrastructure may be operating as a distribution-for-hire service to multiple clients, and it’s quite possible that we will see other malware strains take advantage of this novel and apparently quite effective distribution method.
The Ugly
The last year has been monumental when it comes to historic data breaches. As of late, names like SolarWinds and Accellion have taken on a much darker connotation than those companies would prefer. In fact, for many people in the security industry, those two incidents are going to fully occupy their time for many months ahead. This week the pain continues as one of the world’s largest corporations, Royal Dutch Shell, has seen its data leaked on the internet by the FIN11 hacking group after being affected by the recently discovered vulnerabilities in Accellion’s FTA.

The leaked data reportedly included “passport copies, an evaluation report and a document written in Hungarian” and was found on a dark net website associated with Clop ransomware leaks.
The attackers were reportedly able to access “various files during a limited window of time” and that other stolen files could contain personal data and sensitive data from Shell subsidiaries and stakeholders.
Only time will tell what the real ramifications are, but this is yet another example of how one small chink in the supply chain can result in disastrous costs for any enterprise.
We encourage all to review their environments, and ensure that they have full visibility into the various applications and services running and exposed. It may not always be easy to patch or update resources, but weighing the cost between that and disaster recovery, there is always incentive to patch. This is especially true in the current threat landscape where criminals are taking advantage of any new vulnerability in nearly no time at all.
For the latest information on these vulnerabilities, please see Accellion’s website and statement.