The other day, bleepingcomputer wrote about a new malware in the wild named Thanatos.
This malware is unique because of two aspects:
- It’s asking for Bitcoin cash. This is a split from the main Bitcoin that tries to make peer to peer exchange.
- It creates encrypted files, without saving the keys which are essential for decrypting them back. This means that even if you pay the ransom, it’s unlikely that the developers of the malware will ever be able to decrypt your data.
The good news is that SentinelOne protects against Thanatos the moment the file is saved to the file system. By using machine learning techniques, SentinelOne technology detects it as harmful and prevents it from executing after classifying it as Ransomware.
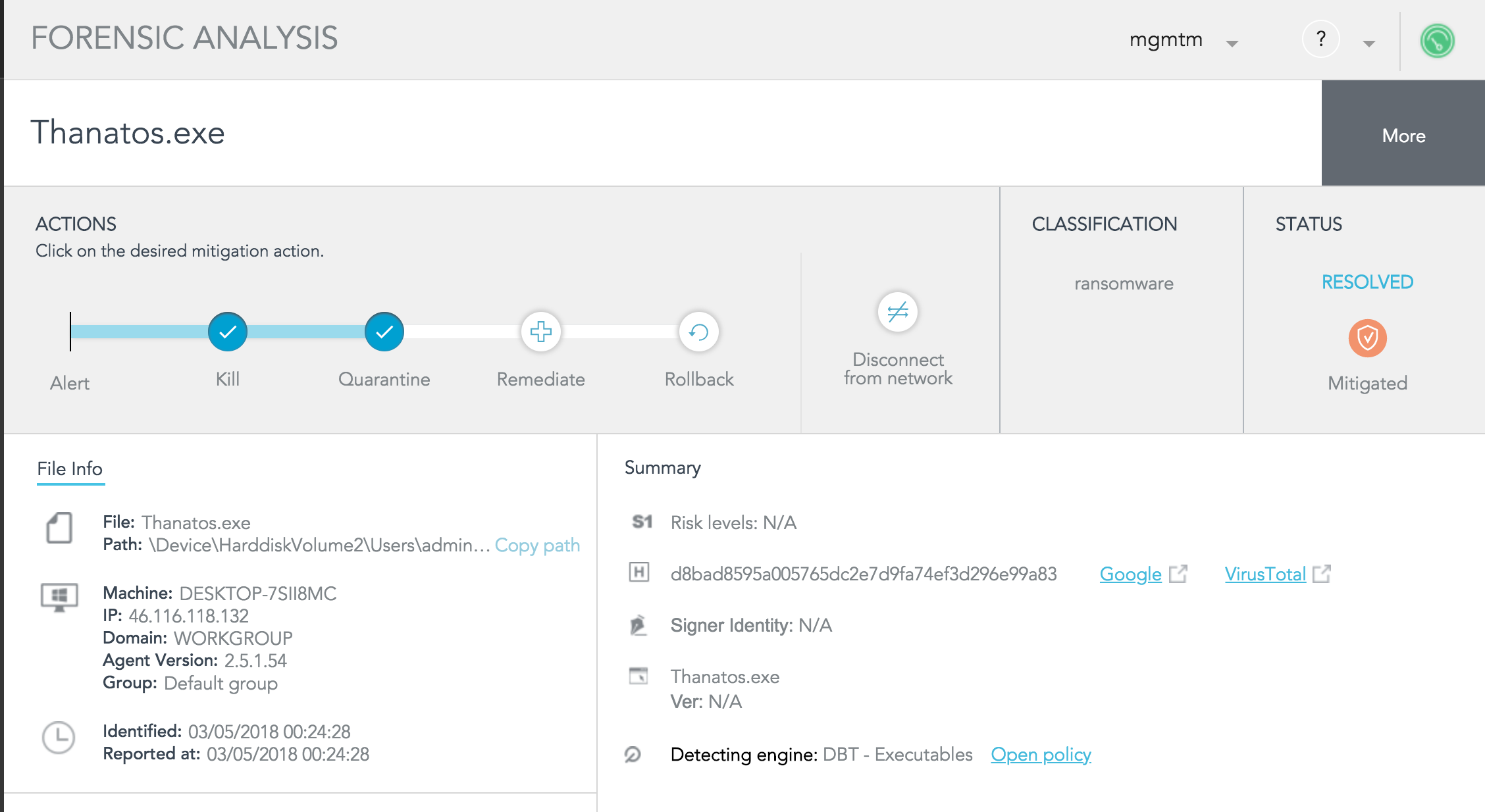
Demo
In this video, you can notice how SentinelOne blocks the Thanatos Ransomware even when offline. The logic that is capable of detecting and blocking the threat resides on the agent side, making the time from detection to mitigation be friction of a second.
- We downloaded the Thanatos Ransomware sample in a zip format from VirusTotal.
- The policy is the default policy, without any change.
- Once the zip is copied to the disk, we disconnected the network by enabling airplane mode. This comes to illustrate that the SentinelOne agent does not rely on connectivity for detection.
Subscribe to our YouTube channel
Technical explanation
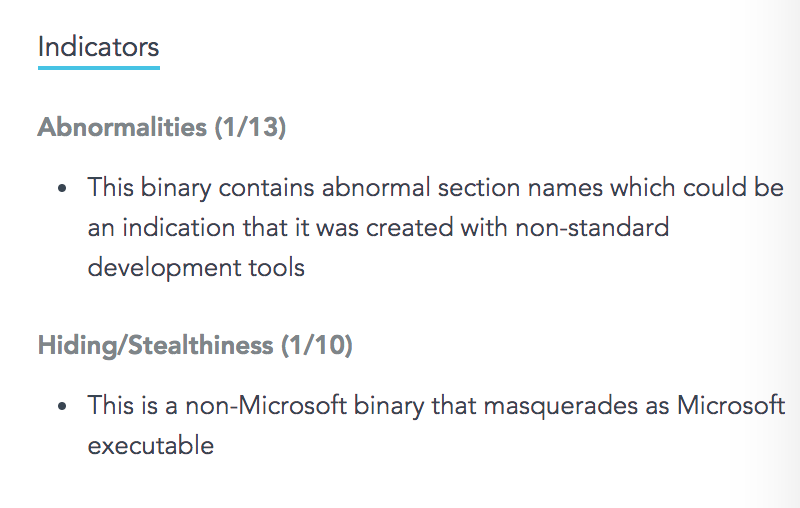
Let’s dive into how SentinelOne technology can detect this. For this, we changed the policy to detect only and reviewed what it is trying to do. First, let’s examine the indicators we’ve seen before allowing it to run:
If later allowed to run, you can find the attack overview. It indicates Anti-Detection, Exploitation, and System Manipulation.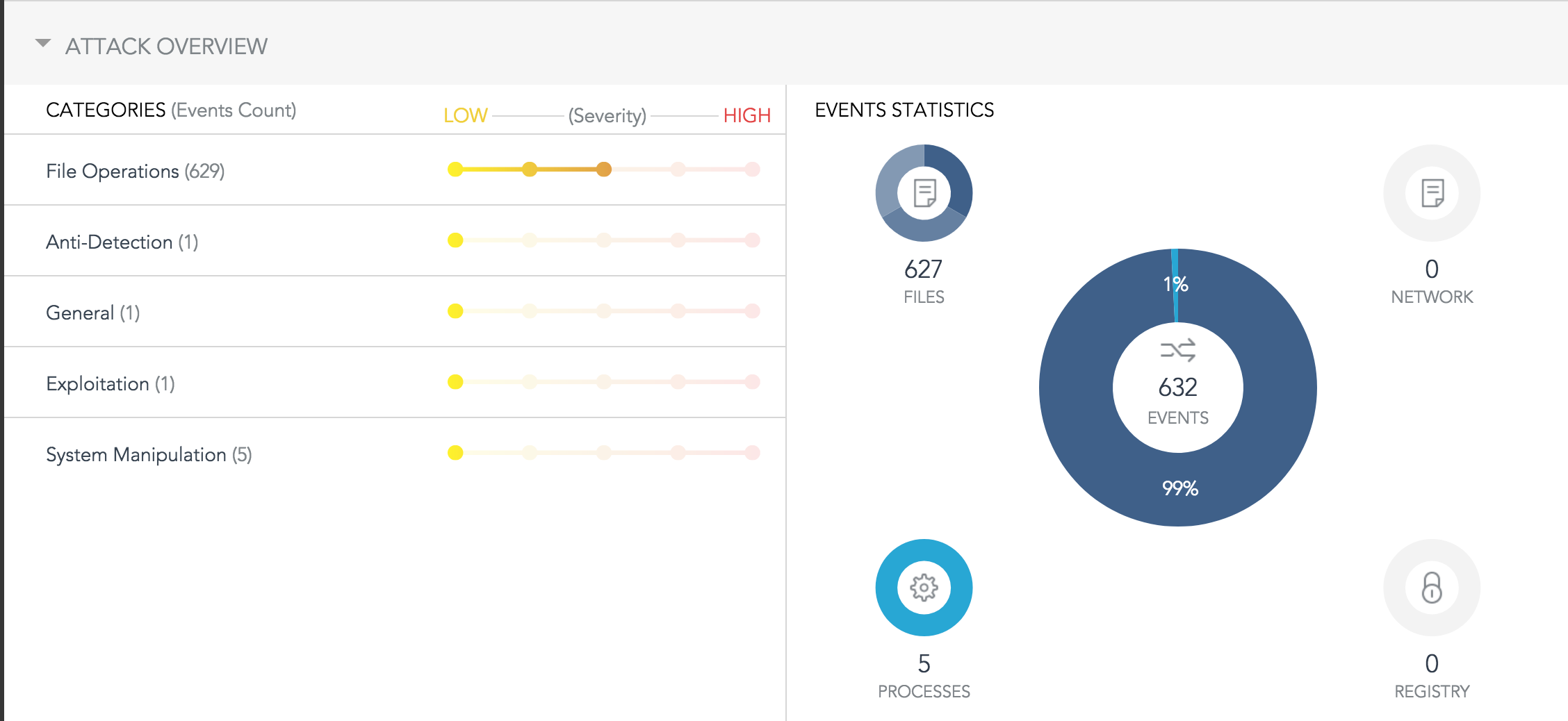
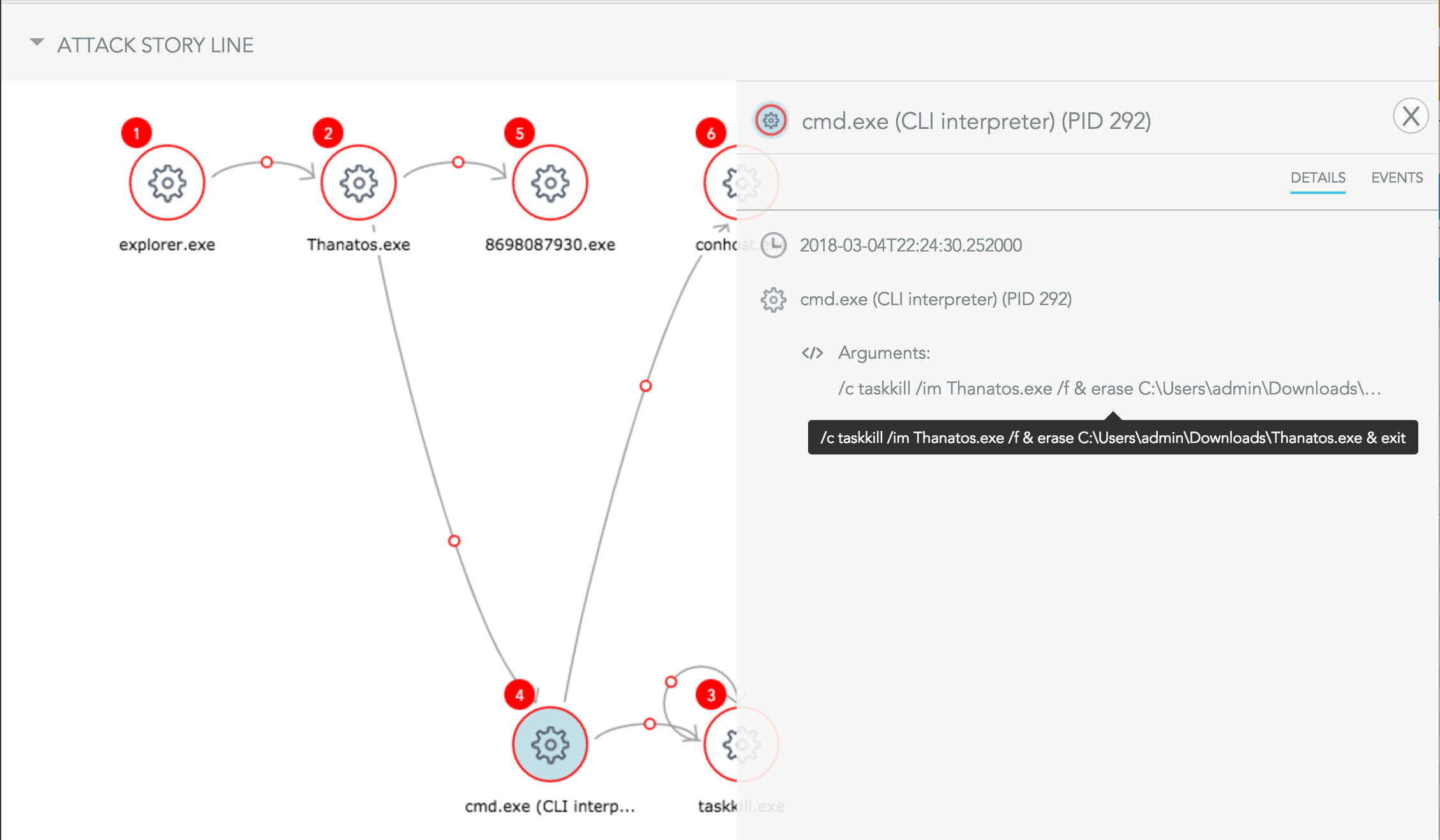
When examining the storyline, you can observe the entire impact. Using SentinelOne behavioral AI it was able to terminate the ransomware before it had the chance to encrypt anything. You can also see more indicators, like deletion attempt using a cmd command and then spawning a system process to make harm. It’s demonstrated in the image below.
Conclusions
Advertisers do not QA their code. In such cases, where encrypting files may become irreversible, you need an automated solution that will mitigate such cyber threats regardless of connectivity. This how SentinelOne is capable of saving time.


