Calisto is a backdoor trojan for macOS believed to be a forerunner of the Proton family of malware. Although Calisto is written in Swift, it uses a number of similar techniques to its Proton offspring. Notable is the choice of a fake AntiVirus product as an installer. Whereas a recent Proton trojan picked on Symantec, Calisto targets Intego users instead.
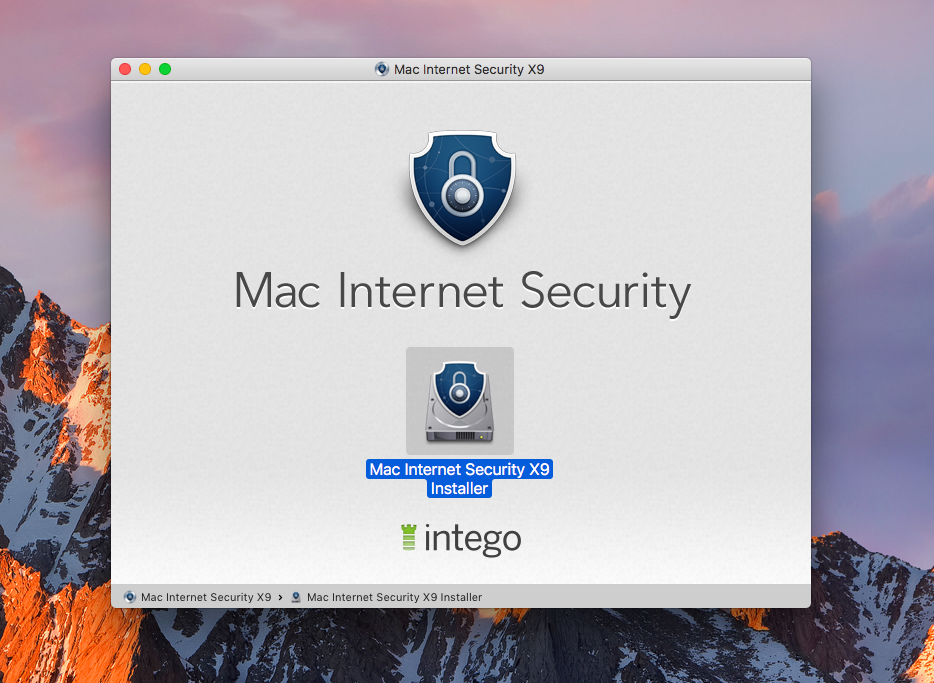
Calisto appears to be able to run on macOS versions as far back as 10.9 Mavericks, but its behaviour varies depending on both the operating system version and the device’s settings.
SIP Takes Out the Sting
On execution, the malware attempts to copy itself to the CoreServices folder hidden deep within the System Library folder. As of 10.11 El Capitan onwards, this location cannot be written to if System Integrity Protection (SIP) is enabled, which it is by default on all Macs shipped since late 2015.
Also, at this point, the trojan attempts to insert itself into the TCC.db. This location, which among other things controls which apps have Accessibility authorization, became protected under SIP in 10.12 Sierra, so again the malware will fail at this point on SIP-protected machines running Sierra or later.
Calisto programmatically enables Remote Login and Remote Management services on the computer using the systemsetup command. This goes unnoticed by the victim unless they happen to open System Preferences and check the Sharing pane. Also, hidden from most average user’s eyes is the fact that the malware tries to enable the root user. Essentially, the malicious code is setting up the means by which the attacker can later login and control the device remotely.
With SIP enabled, most of these attempts will fail. The malware is unable to move past the fake authorization dialog and eventually the frustrated user will have no option but to choose ‘Cancel’.
So, Where’s the Danger?
However, the malware hasn’t been thwarted entirely. There are still two parts of its behavior that will execute even on the latest SIP-protected versions of macOS. First, an attempt at persistence is made by writing and loading a LaunchAgent to the device’s LaunchAgents folder. This will succeed, but since the path the LaunchAgent points to in CoreServices may have been blocked by SIP, the agent won’t find anything to execute when it loads unless the user has disabled System Integrity Protection themselves. While not common and certainly not recommended, users wishing to run certain software that requires installation in a SIP-protected folder are known to disable SIP for this and other reasons.
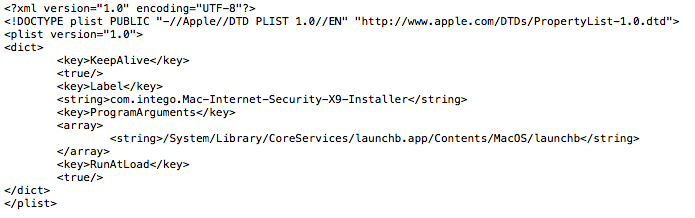
Second, and more worryingly, despite the fact that SIP-protection may prevent Calisto achieving persistence or setting up remote management, it still compromises the user’s security: the user name and a plain-text copy of the login password are written to a file called “cred.dat”. A dump of the system and user keychains are successfully created and compressed in “KC.zip”, while the network configuration is written to a text file, “network.dat”. All these are stashed away in an invisible folder in the victim’s Home folder, “~/.calisto”.
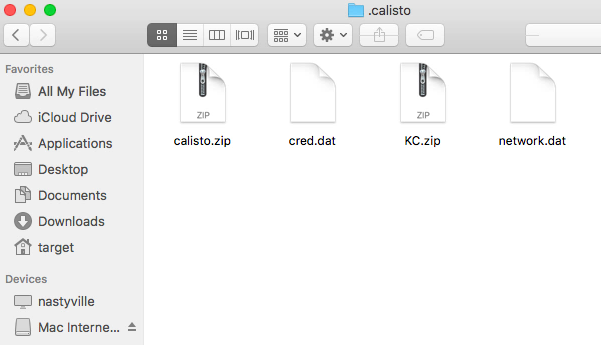
This hidden cache is a treasure trove that offers any other malicious processes the keys to the kingdom should they stumble across it. It is vital for anyone who may have been exposed to Calisto, even on the latest, SIP-protected versions of macOS, to ensure that this hidden folder is removed.
Read more about macOS security:
The Weakest Link: When Admins Get Phished | macOS “OSX.Dummy” Malware
Sentinelone macOS Agent Receives Perfect Score (6/6/6) in Latest AV-Test Evaluation
OSX.CPUMEANER: New Cryptocurrency Mining Trojan Targets macOS
How SentinelOne Deals with Calisto
For endpoints protected by SentinelOne, Calisto is blocked from the outset, so there’s no risk of any data being stashed away by the malware. As always, it’s safest to have your SentinelOne endpoints use the ‘Protect’ policy to ensure that threats are killed and quarantined automatically. In the demo video, we show how SentinelOne deals with Calisto using the weaker Detect-only policy. In neither case is the malware able to execute its code or exfiltrate the user’s data into a hidden folder.
Indicators of Compromise
/Users/user/.calisto /System/Library/CoreServices/launchb.app /Library/LaunchAgents/com.intego.Mac-Internet-Security-X9-Installer.plist
File Hash
0ec3b65534ef09f83b3f43d93b015a7a2cc2534c5f7f251400c5227fd1cabad9
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Want to see how SentinelOne can help improve your macOS security? Get a Demo Now

