Tis the season, and as I look at what gifts are trending on various sites, I am amazed at the amount and variety of connected, IoT devices. I also had a personal epiphany when asking family what they were hoping to receive from Santa Claus. Each of my parents wanted a smart photo frame so they could cycle through up to date photos of family and especially the grandchildren. They, for some reason, needed a WIFI enabled display device with the ability to link to the latest cloud photos and social media to display on their desks at work.

This led me to think about how many devices like these will end up in the office in January. Devices to help find keys, wallets and cars, devices to better organize our days and remind us of our loved ones during tough days. Not to mention facilities managers unveiling the new smart coffee machine, vending machine or smart fridge added to the corporate network.
How Do Security Professionals Securely Maintaining IT Hygiene with All These Devices?
As we head for this post-holiday IoT apocalypse, how do security professionals support the advance in productivity, engagement and enjoyment in the workplace whilst safely maintaining IT hygiene and control so not to expose the enterprise to vulnerabilities and disaster?
The answer lies in three things:
- Constantly know what devices are on your network, where and why
- Immediately tell the difference between IT, IoT and OT devices
- Have confidence that your cyber hygiene process can accommodate this influx
IoT devices, smart devices and industrial control, deliver business growth and profitability, but there is no real way to secure them using traditional means. Because these devices often fly under the radar of your traditional control, device security, vulnerability management and IT hygiene, “point in time” scans will no longer suffice and gaining this awareness and inventory through manual processes is simply impossible.
It is also important to note that the existing scanning methods may be too heavy for some devices and may harm these devices which may actually turn out to be critical OT devices.
To avoid mistakes like these you need the ability to fingerprint different devices on your network to tell whether they are smartphones, Ip enabled cameras or critical Industrial control devices. This also allows you to understand the risk associated with their capabilities and whether you can bring them into management, add security software and scan for significant vulnerabilities ripe for exploiting.
Once you have visibility of your network, you know who’s who and what’s what. You can now assess the potential risks associated with decisions and you can create or easily review good cyber hygiene policies. You understand your estate and you can implement and adjust network segmentation.
What if this could include AI automation to further reduce manual processes? What if this could be achieved without buying extra equipment or agents?
Introducing SentinelOne’s Ranger
Introducing SentinelOne’s Ranger, the industry’s first solution that allows machines to autonomously protect each other and notify security teams of vulnerabilities, rogue devices, and anomalous behaviour.
SentinelOne Ranger uses your managed endpoints to discover and protect other devices.
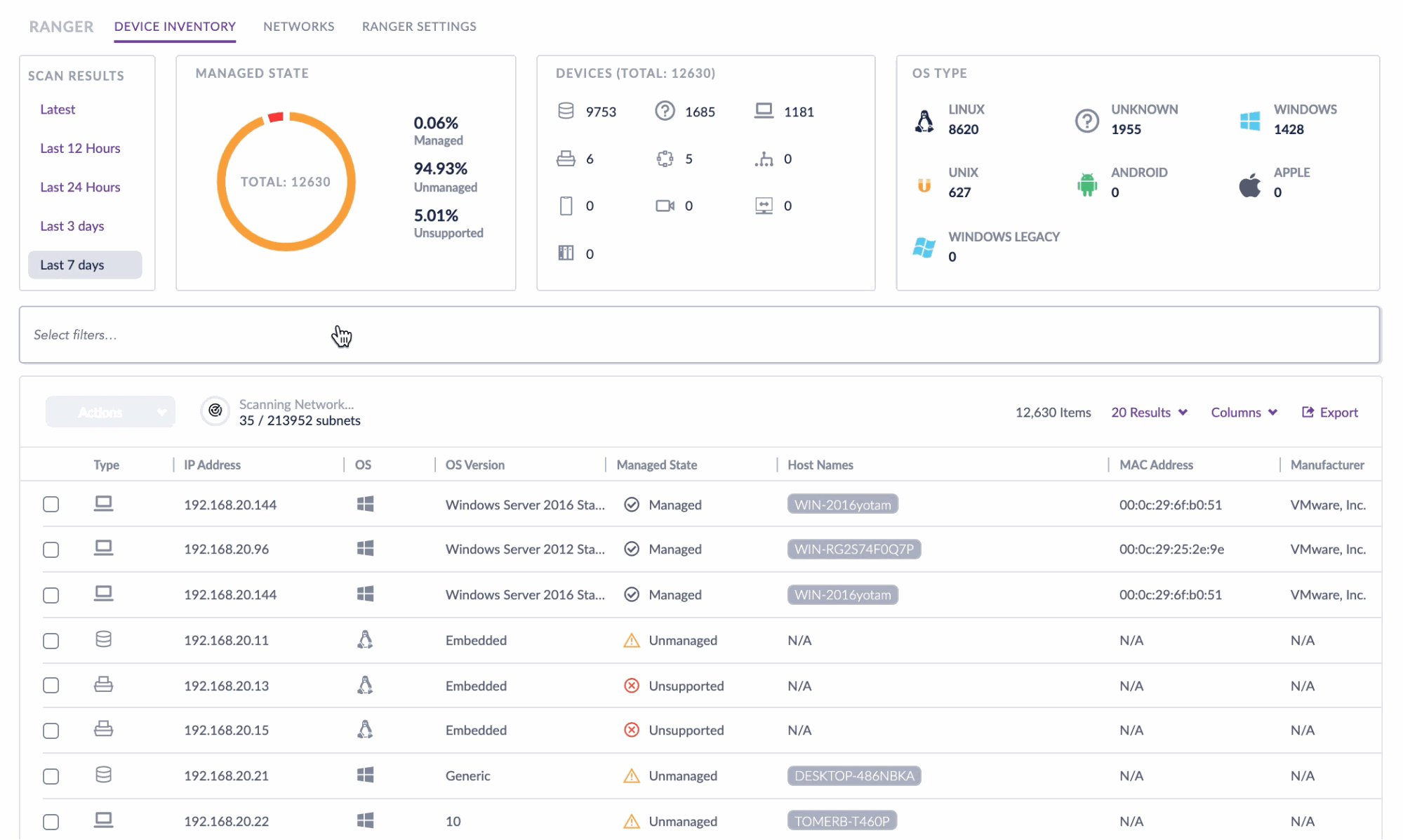
Your endpoints become environmentally aware and fend off attacks from one another, without human intervention. The technology enables constant environment visibility with fingerprinting, profiling and categorization of devices at discovery. It uses AI to monitor and control the access of every IoT device and enable immediate action, ultimately solving a problem that has been previously impossible to address at scale.
Want to learn how? Read our datasheet


