In the first half of 2022, there has been no let up in the number of attacks on businesses by ransomware operators. Conti, LockBit, BlackCat and the LAPSUS$ group may have been generating most of the prime-time cyber headlines, but there are a number of smaller players that have emerged or developed over recent months that are quietly infiltrating companies, stealing their data and demanding high-dollar sums for file decryption and a promise not to leak sensitive company data.
In this post, we provide a high-level overview of three new ransomware threats that have recently emerged–Zeon, HelloXD, and Dark Angels–and provide technical indicators for each to aid threat hunting and intrusion detection teams.

1. Zeon Ransomware
Zeon ransomware was first observed in late January 2022. The group does not currently advertise its victims or data via a known public blog, although the dropped ransom note makes the usual threat of such public exposure for non-compliant victims, stating “We’ve downloaded a pack of your internal data and are ready to publish it on out [sic] news website if you do not respond”.
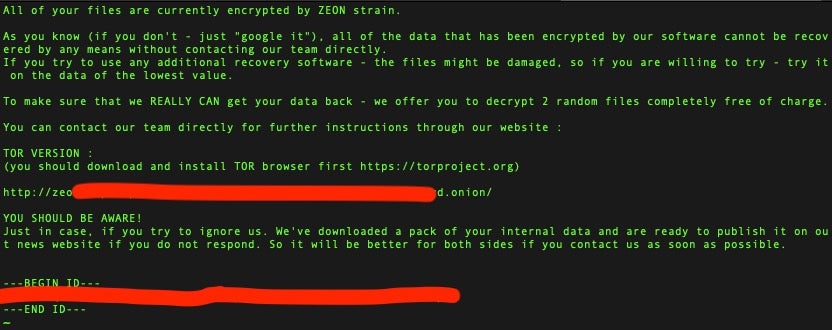
The ransom note further prompts victims to visit a TOR-based payment portal to proceed with the payment. According to one source, victims must pay in XMR or BTC, with a fee of 25% in case of the latter.
Observed Zeon payloads are Python-based executables packaged via pyInstaller and further obfuscated via pyArmor.
On execution, Zeon ransomware payloads attempt to stop any services or processes that could inhibit the encryption process. These include common backup processes and utilities as well as well known security products. For example, Zeon will attempt to stop known processes from McAfee, Sophos and Kaspersky.
The ransomware uses both taskkill.exe and net.exe to terminate the prescribed processes. The following table provides a full list of affected processes.
| mfevtp | backup | EPUpdate | acronis |
| MBAM | vmcomp | W3S | MsDts |
| Back | IISAdmin | Monitor | EsgShKernel |
| Smcinst | vmwp | RESvc | Endpoint |
| bedbg | swi_ | Veeam | PDVF |
| CCSF | TrueKey | task | xchange |
| IMAP4 | Afee | mfemms | ESHASRV |
| mms | vss | SmcService | FA_Scheduler |
| DCAgent | NetMsmq | ntrt | sql |
| VeeamTransportSvc | Report | Sophos | UIODetect |
| veeam | VeeamNFSSvc | EPSecurity | wbengine |
| Backup | ekrn | Eraser | Enterprise |
| POP3 | KAVF | klnagent | WRSVC |
| SNAC | Antivirus | SMTP | AVP |
| AcrSch | Exchange | EhttpSrv | tmlisten |
| mfefire | McShield |
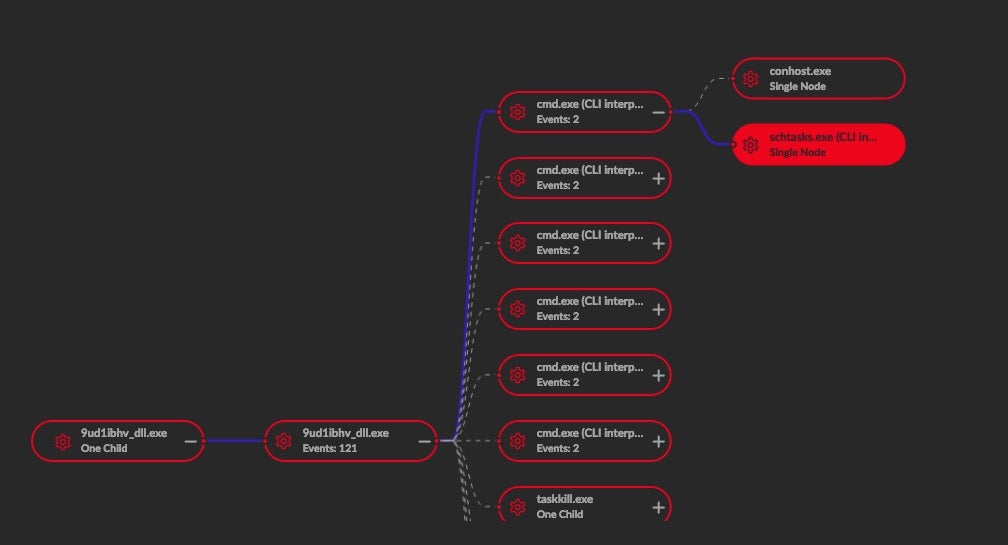
Zeon achieves persistence via Scheduled Task. The ransomware generates and executes its scheduled task via cmd.exe.
The following command output can be observed upon execution:
cmd.exe /c schtasks.exe /Run /TN zE0xO6us
schtasks.exe /Create /TN zE0xO6tMpus /TR "CMD.EXE DEL /F /Q "{PATHIM}" >> NUL" /sc once /st 00:00 /RL HIGHEST
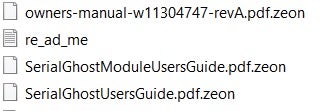
Once encrypted, the .zeon extension will be added to all affected files and the ransom note is dropped as “re_ad_me.html” on the Desktop.
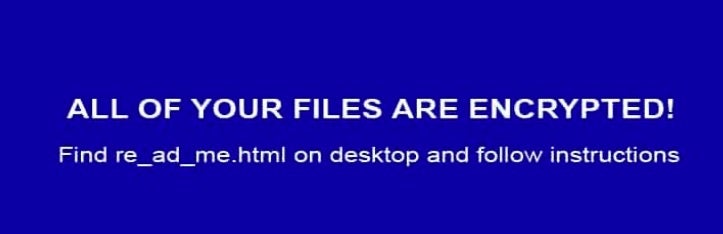
The ransomware also changes the victim’s desktop wallpaper.
2. HelloXD Ransomware
HelloXD is a new ransomware family that first appeared towards the end of 2021. It is another in a long line of families derived from the various Babuk source code leaks. As such, both Windows and Linux variants of HelloXD have been observed.
Like Zeon, HelloXD does not currently host a public blog or victim shaming site. The ransom note instructs victims to engage the attackers via TOX chat as opposed to a direct chat link, .onion TOR website or standard email.
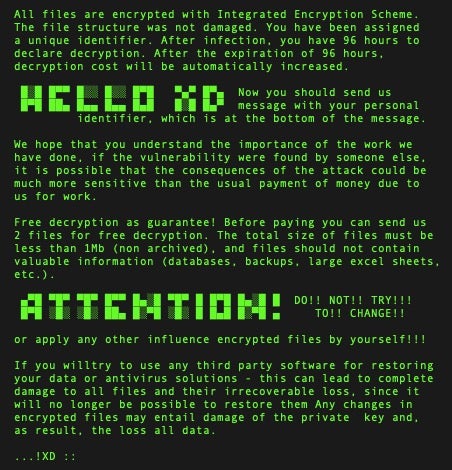
HelloXD is under rapid development, and many versions have been observed in the wild, with the author making continuous efforts to improve upon the malware’s obfuscation and file encryption routines. Initial samples of HelloXD were encrypted with a version of UPX, and some early versions also used a combination of HC-128 and Curve25519-Donna. Later examples of HelloXD ransomware have built additional layers onto the modified UPX packing, as well as updated the file encryption routine, swapping out HC128 for Rabbit Cipher.
We have observed that HelloXD payloads attempt to inhibit recovery via deletion of shadow copies:
vssadmin.exe delete shadows /all /quiet
Analyzed payloads have a rather noisy way of incorporating delays into the execution of the malware using the following:
PING.EXE 1.1.1.1 -n 1 -w 3000
Upon encryption, files are given the .HELLO extension.
Recent examples of HelloXD also install copies of MicroBackdoor, which provides the threat actors with additional RAT-level access to breached systems.
HelloXD has, for a time, been openly discussed and sold in darknet crime forums. Alongside that, the actor behind HelloXD has been receiving some unwanted attention around the exposure of HelloXD as well and mocked for being exposed by security researchers.
3. Dark Angels Ransomware
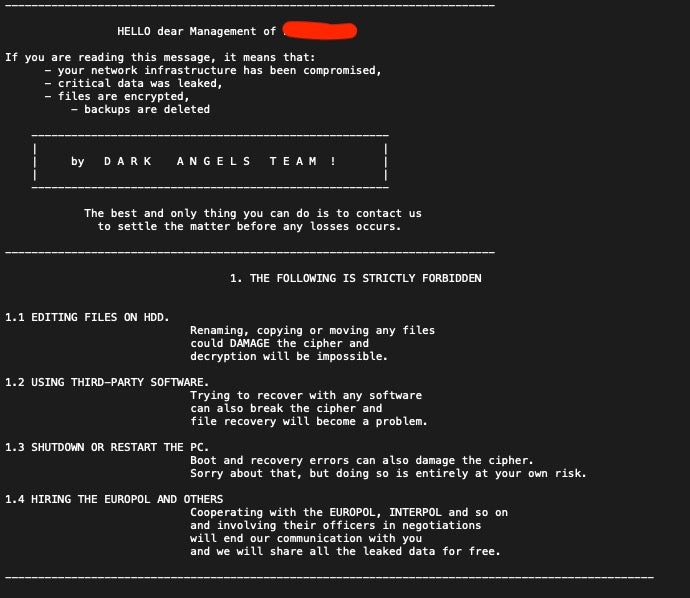
In May 2022, researchers found another Babuk-derivative that behaves very similarly to HelloXD called ‘Dark Angels’ (aka DarkAngels). Early reports on Dark Angels suggest that each ransomware sample is targeted specifically for a given organization, not unlike Mindware and SFile, which we reported on previously.
Dark Angels’ victims are instructed to communicate with the threat actor via TOR-based chat portal and are given the (now) usual warning about not attempting to contact law enforcement, engage recovery teams or hire negotiators.
The ransomware attempts to stop the following services upon execution:
| memtas | mepocs | sophos |
| veeam | backup | GxVss |
| GxBlr | GxFWD | GxCVD |
| GxCIMgr | DefWatch | ccEvtMgr |
| ccSetMgr | SavRoam | RTVscan |
| QBFCService | QBIDPService | Intuit.QuickBooks.FCS |
| QBCFMonitorService | YooBackup | YooIT |
| zhudongfangyu | sophos | stc_raw_agent |
| VSNAPVSS | VeeamTransportSvc | VeeamDeploymentService |
| VeeamNFSSvc | veeam | PDVFSService |
| BackupExecVSSProvider | BackupExecAgentAccelerator | BackupExecAgentBrowser |
| BackupExecDiveciMediaService | BackupExecJobEngine | BackupExecManagementService |
| BackupExecRPCService | AcrSch2Svc | AcronisAgent |
| CASAD2DWebSvc | CAARCUpdateSvc |
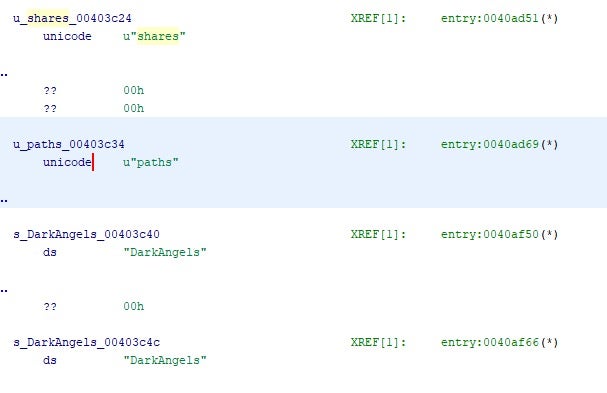
Dark Angels payloads have the ability to spread to available network shares and can accept associated parameters. The ‘paths’ and ‘shares’ command line parameters are both available. The method of share discovery can vary depending on the option provided.
In the absence of any command line options, the malware enumerates all local drives and encrypts all targeted files. Upon encryption, files are given the .crypt extension.
Conclusion
Ransomware is continuing to evolve and pivot in an ever-evolving race to gain illicit profits by attacking data on businesses’ computer systems. Threat actors know they must constantly work to stay ahead of both the legal system and the ongoing influx of inhibiting technical controls. Staying abreast of the latest developments in the evolving crimeware scene can help your security and IT teams keep your business secure.
SentinelOne Singularity detects and prevents attacks by Zeon, HelloXD and Dark Angels as well as all other known ransomware families. For more information about how SentinellOne can protect your business, contact us or request a free demo.
Indicators of Compromise
Zeon SHA1
66535700bbce7f90d2add7c504bc0e0523d4d71d
51d18417b2593bb946e08d436692e26da44cfa48
c45d82da884285100ce067bb004a3f1e31e151f5
Zeon SHA256
c860bf644bd5e3d6f4cae67848c4fc769184ae652fcb41cac670042b185d217a
8ff189783dc0646513c791421df723187b614f6dbfafad16763e3c369c5dfa2a
fb57abf08a85f1d7ca0a6fdcd76b04ccf964a5b05f2f784492083994773e4590
HelloXD SHA1
4a2ee1666e2e9c40d372853e2203a7f2336b6e03
7a1b6d3ccf9429a5a5c03ce1e6db91c3095e9f34
9785231ebf3d00216aa979f8c705e2513568802e
9c8feeab65f71344713d63f4879e247aba49dce4
4d65559a14bca55f6cca722d09d80ba3e262053d
0ddf8c9a59f5fe5337e65d1e5b2e22381c3ce7e2
1758a8db8485f7e70432c07a9e3d5c0bb5743889
HelloXD SHA256
435781ab608ff908123d9f4758132fa45d459956755d27027a52b8c9e61f9589
ebd310cb5f63b364c4ce3ca24db5d654132b87728babae4dc3fb675266148fe9
65ccbd63fbe96ea8830396c575926af476c06352bb88f9c22f90de7bb85366a3
903c04976fa6e6721c596354f383a4d4272c6730b29eee00b0ec599265963e74
7247f33113710e5d9bd036f4c7ac2d847b0bf2ac2769cd8246a10f09d0a41bab
4e9d4afc901fa1766e48327f3c9642c893831af310bc18ccf876d44ea4efbf1d
709b7e8edb6cc65189739921078b54f0646d38358f9a8993c343b97f3493a4d9
Dark Angels SHA1
529e24c81ede5dfcedcc4fbc7d0030f985c67af1
Dark Angels SHA256
38e05d599877bf18855ad4d178bcd76718cfad1505328d0444363d1f592b0838


