Colonial Pipeline, one of the largest pipeline operators in the United States, had to shut down operations on May 8th, 2021 after becoming the victim of a ransomware attack. The FBI confirmed that the DarkSide ransomware group was responsible for the attack on the Colonial Pipeline infrastructure.
Darkside is human-operated ransomware that uses various post-exploitation tools (such as Cobalt Strike, Metasploit framework, Bloodhound, etc.) to perform Active Directory enumeration, identify paths to high privilege targets, and deploy ransomware organization-wide.
Prior IR (Incident Response) engagements of organizations infected with Darkside ransomware have seen that the group targets the organization’s domain controllers after getting initial access.
“We observed Darkside payload (e.g., azure_agent.exe.exe) staged on the domain controller in a network-shareable folder (e.g., C:WindowsIMEazure), followed by the establishment of a scheduled task (e.g., WindowsSYSVOLdomainPolicies{L0NGMGU1D}UserPreferencesScheduledTasks) set with Group Policy and instructing hosts to obtain and execute the payload. This resulted in a fully automated enterprise-wide deployment less than 24 hours after data was exfiltrated.”
Source: https://www.areteir.com/darkside-ransomware-caviar-taste-on-your-big-game-budget/
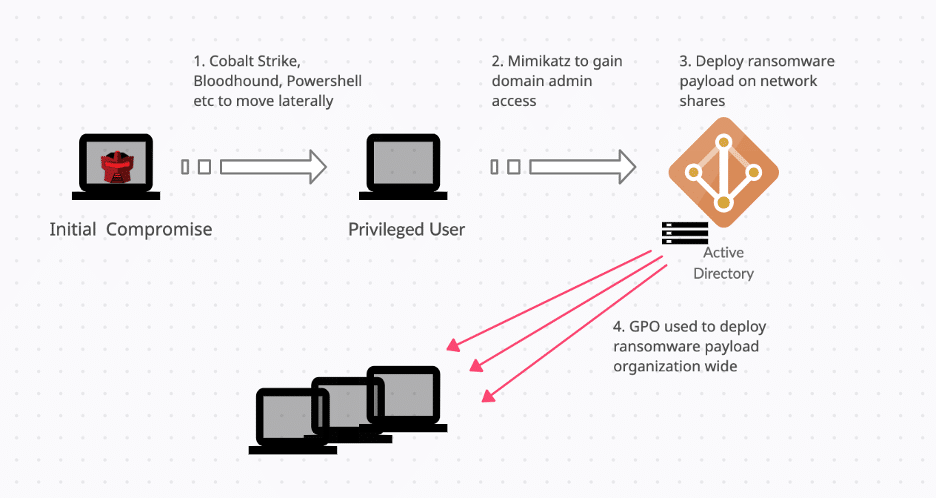
The following are some of the methods the threat actors used to gain domain dominance after the initial compromise.
- Use tools such as Cobalt Strike, Metasploit framework, Bloodhound, Powershell Empire, etc., to perform Active Directory enumeration and move laterally from the initially infected system to escalate privileges.
- Use Mimikatz to dump credentials and gain domain administration access.
- Deploy ransomware payload to a network shared folder that is accessible to all computers in a domain.
- Deploy ransomware payload across the organization by creating GPO scheduled tasks.
How organizations can protect against human-operated ransomware operators
The Attivo Networks ThreatDefend® platform prevents attackers from moving laterally and stops ransomware from encrypting or exfiltrating data at multiple stages of the attack cycle.
Step 1: The Attivo Networks ADSecure solution restricts Active Directory enumeration access on an as-needed basis, preventing attackers from discovering privileged Active Directory users or group permissions.
Attackers must perform domain reconnaissance to discover:
- Domain Controllers
- Local Administrator Account discovery and exploitation
- Privilege Users
- Discover Domain Administrators
- Discover Backup Operators
- Discover Enterprise Administrators
- Discover Account Operators
They must also perform SMB Net session enumeration to discover the systems of privileged users.
Step 2: The Attivo Networks ADSecure solution detects attacker attempts to dump credentials, extract tickets, and elevate domain credentials to perform Golden Ticket and DC Sync Attacks.
Step 3: The Attivo Networks ADSecure solution prevents attackers from discovering and gaining access to the organization’s domain controllers.
Step 4: The Attivo Networks DataCloak function hides and denies access to local files, folders, and network or cloud shares from ransomware payloads. Files are not visible to malicious ransomware processes, and they can’t exfiltrate or encrypt files that are not visible.
The Darkside ransomware attack on Colonial Pipeline caused significant damage to the company and disrupted pipeline operations for much of the east coast of the United States. Organizations can limit the damage these attacks can cause by implementing the Attivo ThreatDefend® platform.
About Attivo Networks:
Attivo Networks®, the leader in preventing identity privilege escalation and detecting lateral movement attacks, delivers a superior defense for countering threat activity. ThreatDefend® Platform customers gain unprecedented visibility to risks, attack surface reduction, and speed up attack detection. Patented innovative defenses cover critical points of attack, including at endpoints, in Active Directory (AD), in the cloud, and across the entire network. Concealment technology hides critical AD objects, data, and credentials. Bait and misdirection efficiently steer attackers away from production assets, and deception decoys derail lateral movement activities. Attivo has won over 150 awards for its technology innovation and leadership. attivonetworks.sentinelone.com.


