Credentials Harvesting is an attack technique adversaries employ after establishing a foothold inside an organization. The technique is to harvest or amass numerous credentials (username/password combinations) for reuse. It helps adversaries move internally to higher-value assets while gaining access to protected data and applications. Such lateral movements are difficult to detect with standard security controls because they are legitimate user account activity seen in the enterprise.
Every enterprise that employs Windows Active Directory also uses it for many operational tasks. These range from configuring environment variables or common network shares to ensuring every computer in the domain has a baseline configuration guaranteeing a minimum level of security controls. Organizations achieve these through a collection of Group Policy client-side extensions that deliver preference settings to domain-joined computers running Microsoft Windows desktop and server operating systems.
Group Policy relies on a share available on Domain Controllers called SYSVOL. It is a share accessible to all domain users without any specific privilege. Just like any other user, an adversary establishing a foothold will also have access to this share.
SYSVOL share is one of the most sought-after locations adversaries look for after moving onto an enterprise system through one of the initial access techniques such as phishing. It includes two folders:
1.Policies
Default location: %SystemRoot%SYSVOLsysvolPolicies
2.Scripts
Default location: %SystemRoot%SYSVOLsysvolscripts
The “Policies” folder is where AD defines all the group policies for a domain, while the “scripts” folder stores all the logon scripts. The “scripts” folder is also popularly called the “Netlogon” share and holds common content used by 3rdparty deployment solutions or Group Policy.
Attackers seek out the SYSVOL share because Group Policy XML files store an encoded password within them, while it is quite common that a password exists in cleartext as part of one or a few of the logon scripts under the Netlogon share.
Attackers can reach the SYSVOL or Netlogon folder from a compromised endpoint using “%Logonserver%Sysvol” or “%Logonserver%netlogon”. Below is an example of a Group Policy XML file containing a password in the SYSVOL folder.
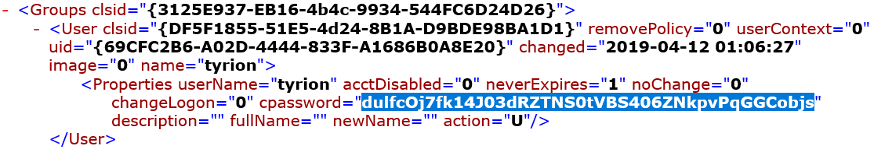
Attackers can easily retrieve the plaintext password from a Group Policy Preference using tools like the PowerSploit function “Get-GPPPassword”. It recovers the plaintext password and other information for accounts that AD uses to push Group Policy Preferences. Here is an example of a simple PowerShell script “GPPDecrypt.ps1” that attackers can use to decrypt AES-256 bit encrypted password.

It is also pretty commonplace for logon scripts stored in netlogon shares to contain passwords in cleartext. Most of these scripts run at the logon time and typically either mount standard network folders, start a few services, schedule a task, or sync up configuration and data. Invariably they tend to need data or access to resources that require credentials to authenticate. The passwords get stored in scripts such as a BAT file, VBS, or Java for operational efficiencies.
There have been incidents where malware extracted passwords from network shares. A recent example of such malware is Emotet that scans the infected computer’s hard drive, network drives, and shared folders for files containing usernames and passwords. Adversaries also use publicly available tools like PowerShell Empire or SearchOpenFileShares that scan file shares for passwords.
Mitigations
Organizations can mitigate these vulnerabilities with the following procedures:
- Remove vulnerable Group Policy Preferences. Microsoft has released the security bulletin MS14-025, which addresses the vulnerability by removing the ability to configure and distribute passwords that use certain Group Policy preferences extensions.
- Install KB2962486 on every computer used to manage GPOs, preventing new credentials from being placed in Group Policy Preferences.
- Delete existing GPP XML files in SYSVOL containing passwords.
- Identify script files in Netlogon and Sysvol shares and remove any passwords stored or reversible to plaintext. Modify the script to run in the context of the User or System without requiring pass the credentials.
Conclusion
Attackers find ways to harvest credentials from SYSVOL share and NetLogon folders. With continuous monitoring solutions, organizations can detect risks associated with credential harvesting from domain shares and avoid advanced attacks against Active Directory.
Singularity™ Ranger AD is a cloud-delivered solution designed to uncover vulnerabilities in Active Directory and Azure AD. Get additional AD attack detection and conditional access capabilities to protect enterprise identity infrastructure with Singularity Ranger AD Protect.


