macOS Mojave’s restrictions lock down user data, but pre-approval gives admins a ‘backdoor’
At WWDC 2018, Apple announced a raft of new user-level security features for the upcoming release of macOS 10.14 Mojave. Among these was a hardening of access to certain folders in the user’s Library, which will now require approval when applications try to traverse them. This change doesn’t affect just 3rd party apps, but native macOS apps like the Terminal, too. So, for example, if an admin user wants to use the command line to move around in, read, write or copy from something in a user’s Safari support folder, that’s going to require approval.
Without approval, even an admin running as root on the command line won’t be able to access any of the newly-protected folders. The full list of protected categories was published at WWDC 2018 and is shown in this slide:

The last item in the slide – Time Machine Backups – will prevent use of the tmutil utility, so some routine admin tasks like listing and thinning snapshots will be ruled out if Terminal hasn’t been authorized first.
Approval can take the form of an app presenting a dialog request, but if you’re working on the command line, that may not be seen. Apple are aware that, since it’s common for many apps to access one or more of these newly-protected areas, there’s a usability issue to consider:
“apps that traverse the user’s Home folder could trigger multiple approval prompts…So user[s] can pre-approve such apps by adding them to the new System Application Data category in the System Preferences Security and Privacy pane. By doing so, the user preauthorizes those apps to access all of their privacy-sensitive data without prompting.”
[WWDC 2018: Your Apps and the Future of macOS Security]
This solves the problem of working on the command line, too, so long as Terminal.app has been pre-approved in System Preferences. However, as we’ll see later in this post, that is likely to undermine some of the protections Mojave is trying to put in place. In order to see why, let’s try to understand the thinking behind Apple’s new lock down of user data.
Leaky Library
This isn’t the first time Apple has tinkered with the user Library: to the consternation of many power users, Apple took the step of hiding the Library from the Finder by default in OSX 10.7. The rationale was to protect the Library from unintentional harm by uninitiated users. After all, so the argument went, most users rarely need access to the Library, which is primarily used as a backing store for application data.
The changes coming in 10.14 Mojave are of a different nature entirely. The lock down isn’t aimed at keeping the user out, but keeping the data in. As things stand on macOS, it’s a simple matter for a process to gain access to a user’s most personal information – emails, chat messages, browser history, even phone number – without authorization. Here’s a few examples.
If an app wants to know what your favorite Youtube video is, or whose page – or photos – you like to visit most often on FaceBook, it’s just a simple sqlite3 query away:
sqlite3 ~/Library/Safari/History.db "select visit_count, url from history_items order by visit_count asc"
Let’s drill down on FaceBook visits:
sqlite3 ~/Library/Safari/History.db "select visit_count, url from history_items where url like '%facebook.com%' order by visit_count asc"
If you’re not familiar with the widespread use of SQL databases on macOS, the richness of the data might surprise you.
Apple’s chat app, Messages, is equally vulnerable to snooping in all current releases of macOS. Here, we view the database located at ~/Library/Messages/chat.db in the free utility DBBrowser for SQLite:
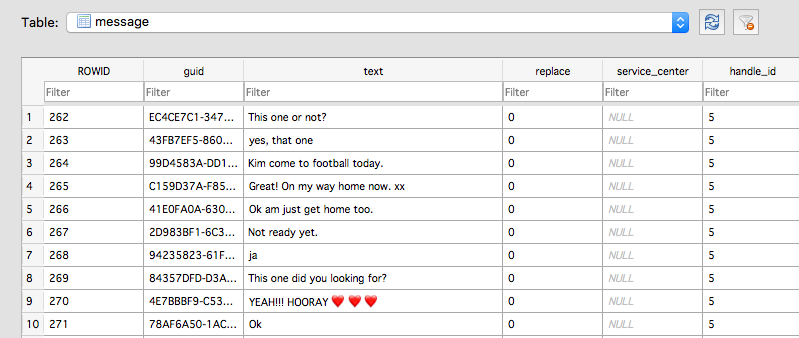
And of course, if you or your users were ever tempted to share a username or password over Messages, confident in its end-to-end encryption, well that’s there for the plucking by 3rd-party processes, too.
Another example of just how exposed user data is can be seen by traversing into the Suggestions folder. While it’s expected that a user’s Mail messages are going to be exposed in the Mail folder, that folder isn’t easily navigated for juicy material due to its structure. No matter, Suggestions helpfully throws all your most recent email messages into one conveniently accessible database, the snippets.db.
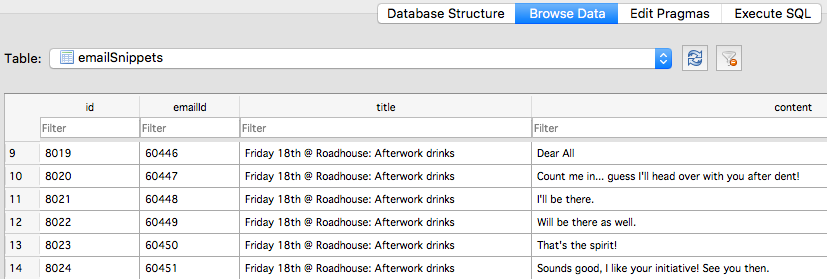
It’s a welcome relief, then, that 10.14 Mojave will restrict access so that this kind of sensitive user data cannot be easily exfiltrated by applications and processes.
One Approval Rules Them All
But there’s a catch. Although the exact details of the implementation of these security features in Mojave won’t be known until the OS goes public, there are concerns based on what we know about the way Security privileges have been handled in macOS up to now.
Choices made in ‘System Preferences’ aren’t always system-wide, despite the name. While options in Sharing, Network, the Firewall or Gatekeeper obviously apply across the board, others do not. Think: ScreenSaver, Wallpaper, Dock, Mouse and Trackpad settings, all of which are user-specific.
When it comes to that all-important ‘Privacy‘ tab there is some inconsistency that’s not always obvious.
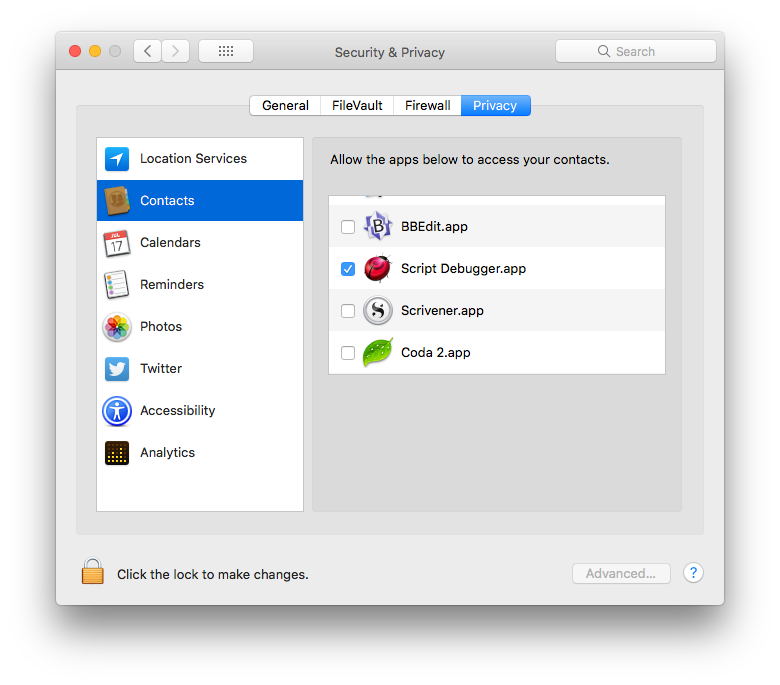 Clearly, users may have different feelings about allowing certain apps access to their Contacts, Calendars, Reminders, Photos and so on. The text in the pane signals Apple’s intent by referencing the particular user:
Clearly, users may have different feelings about allowing certain apps access to their Contacts, Calendars, Reminders, Photos and so on. The text in the pane signals Apple’s intent by referencing the particular user:
“Allow the apps below to access your contacts”.
Click down a little to Accessibility and note the text has a minor variation:
“Allow the apps below to control your computer”.
It’s a subtle but important difference.
The first setting is per-user, but the second is system-wide. This change in language reflects the fact, of course, that it’s the same computer for all users, but it’s subtle enough not to be noticed by many. And if one user happens to set an opposite preference to another, the last change naturally takes precedence for all.
We can see how this affects security on macOS 10.13 and earlier. As an administrator, I may be happy to add apps like Terminal and Script Editor to my Privacy pane. I may well have specific needs as an admin for giving those apps permission to do things on my behalf. The problem is that in so doing, I’ve now given those apps permission to control the computer when any of my less-privileged users are logged in also.
Although details of how this will be implemented in Mojave are not yet public, if Apple follow the same policy then applications added to the ‘Application Data’ category will also be system-wide.
This is both a good thing and a bad thing. For admin users it will be a welcome relief. The challenge of ‘user approval’ is no more than approval in the admin’s own account. That will make maintenance tasks such as using tmutil – the Time Machine utility we mentioned earlier in the post – unproblematic. On the other hand, making this setting global somewhat undermines Apple’s intention to protect individual user’s data.
What this means for Mojave’s new user protections is that private data is either inaccessible to an app for every user or for none. And since most admins are going to need to add Terminal and no doubt a bunch of other useful utilities to their Preferences for their own use, they will be giving those access to every user’s private data at the same time.
Takeaways
Mojave’s new user-protections are a welcome hardening of the OS but they will have an impact on admin users and ordinary users alike.
In particular, those who aren’t prepared for the changes are going to be surprised when familiar command line tools – everything from ls, find and cat to tmutil and python – mysteriously appear not to work as before. While the solution of adding Terminal to the ‘Application Data’ category of System Preferences is straightforward enough, admins need to be aware that, based on how similar Privacy preferences have been implemented in the past, any apps added there are likely being granted permission for all users on the system.
This may also not be obvious to your users. Apple will be heavily touting these new protections when Mojave is released. A little education might be in order to ensure your users are not operating under the mistaken belief that their data is now protected simply because the OS has been upgraded to 10.14. If an admin user has made the kind of changes discussed above, their users’ data can be just as exposed on Mojave as it was under previous versions of macOS.
Read more about macOS Security
Calisto Detected installing Backdoor on macOS
The Weakest Link: When Admins Get Phished | MacOS “OSX.Dummy” Malware
OSX.CpuMeaner: New Cryptocurrency Mining Trojan Targets MacOS

