We’re happy to announce our new version, introducing the simplified policy, improved prevention, detection, and response, and many more features, fixes, and enhancements. Our customers have been telling us which improvements they want to see in our product, and we are responding. Let’s go over the most significant changes.
Simple Policy
SentinelOne’s policy was never complex – Yet, we simplified it further by removing any setting that was not 100% clear to our clients.
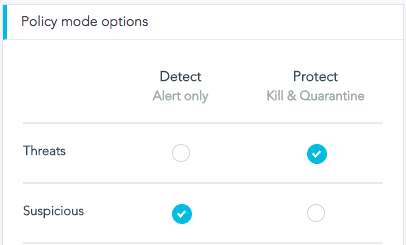
The new policy of 2.0 is a simple selection between “Protect” and “Detect”.
Choosing “Protect” means complete automation and autonomy – we take responsibility for preventing and mitigating all threats. Choosing “Detect” means that you are running in EDR mode.
Another option you will find useful is the differentiation between Threats – high confidence detections, and Suspicious activity, so you can assign them different policy modes. Try it out.
Controlling Engines
Under the hood of our SentinelOne agent, multiple engines are running and ensuring full visibility and detection of any malicious activity. We recommend running all of our Static and Behavioral AI engines, but allow administrators to control them, based on policy.
Prevention, Detection, and Response at Scale
Many have tested our capabilities, and the results are available:
- Our Static AI prevents malicious files and variants from ever being executed on your devices.
- Our Behavioral AI specializes in catching zero-day and unknown attacks based on their behavior, including file-less and other new means to evade traditional AV solutions.
And we are always working on improvements. In the wild, we see more and more campaigns that don’t need to use files (WannaCry, EternalBlue, etc’). The reason is obvious – why expend effort on a file that will become a blocked signature in few days? For instance, it is common for attackers to find a weak host on a network and utilize it to compromise other devices on the same network. We invested further in our behavioral AI engines to improve detecting of such flows. When we detect a risk, we already have the full context: users, processes, command line arguments, registry, files on the disk, external communication, and more.
Forensics Analysis Improvements
Once detected, it is helpful to identify the full context of the attempt, where it came from, and what it tried to do, even if it was automatically mitigated by “Protect” mode. To make this easy, we improved what you see and what you can do. Starting in 2.0:
- You can see:
- Which of our engines detected it.
- A link to VirusTotal entry (for known threats) and to a Google search.
- More forensics information, including the username, and the full command line arguments used by all processes during the incident.
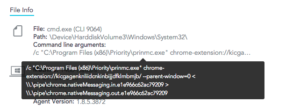

- You can do:
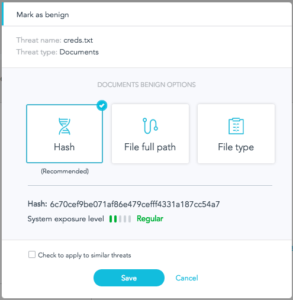
- More exclusion options: by hash, path, certificate, file type, or browser type.
- Quickly and easily exclude for each specific incident directly from the forensics analysis view.
Full Disk Scan
Many of our customers asked for the option to scan a device and Full Disk Scan is now available for our Windows and macOS agents. Whether you are worried about dormant malware or concerned with issues of audit and compliance, you can choose a group from the console and initiate a scan, or just install using a flag that triggers the full disk scan. This is a great way to get value on day one.
More improvements starting in 2.0
- Performance improvements (cross-platform)
- Click-through EULA
- SSO support for the management console login.
- VSS disk space does not exceed 10% (unless configured by the administrator to a different limit).
- Support tools and remote troubleshooting options for your agents.
- Additional proxy options, including failover to direct connection (for roaming devices) and authenticated proxy
- The Auto-immune flow is improved and now works on verified threats only.
- Document names are not sent to the console, unless malicious.
- Support for Windows agent on a single core.
What’s next?
Our team is already working on the next release, planned for later this year. It will have improved deployment flows, more reporting options, Agent configuration and more policy options, initial scan support (no reboot needed), and static detection indicators, for a better understanding of detection reasons.
Stay tuned!

