The Good | FBI Shares 42,000 Phishing Domains After LabHost PhaaS Platform Takedown
Since dismantling one of the world’s largest phishing-as-a-service (PhaaS) platforms, the FBI has shared 42,000 domains tied to it, helping cyber defenders identify IoCs and enhance their detection capabilities.
LabHost operated from November 2021 until April 2024 and offered phishing kits that primarily targeted U.S. and Canadian banks. Subscriptions ranged from $179 to $300 per month, with features like advanced two-factor authentication bypassing, SMS-based victim interaction, and real-time management dashboards. Though active since 2021, LabHost saw a surge in popularity in late 2023, pushing it to becoming a dominant player in the PhaaS space. Authorities estimate it facilitated the theft of over 1 million credentials and nearly 500,000 credit card records.
The crackdown last April was a globally-coordinated effort, with actions taken by law enforcement across 19 countries, resulting in 37 arrests during raids on 70 locations. LabHost reportedly served around 10,000 clients globally at the time.
While the shared domains are likely inactive now, they still offer up critical information for cybersecurity teams. These domains can be added to blocklists to prevent future reuse, aid in retrospective log analysis to detect past breaches, and support threat intelligence and phishing model development. The list can also help uncover domain patterns and support further attribution efforts.
While the FBI cautions that the list may contain unverified entries given that it is raw data from LabHost users and is not exhaustive, the released domains can help investigators reveal associated ones that are active. Major takedowns like these help enhance collective defenses and play a part in preventing future abuse by exposing the infrastructure, tools, and methods cybercriminals use to operate.
The Bad | PurpleHaze Campaign Highlights China-Linked Espionage & Supply Chain Risks
A new SentinelLABS report exposes a cyberespionage campaign led by China-linked threat group, PurpleHaze, which attempted to probe SentinelOne’s infrastructure and its customers. The campaign first came to light following a 2024 compromise of a third-party logistics provider that previously handled hardware distribution for the company.
PurpleHaze is believed to have loose ties to the China-nexus APT group APT15 (aka Nylon Typhoon). In October 2024, the group targeted a South Asian government-aligned entity using a backdoor named GoReShell based on reverse_ssh to establish reverse SSH connections. They also deployed an Operational Relay Box (ORB) network, a fast-expanding infrastructure tactic designed to evade attribution.
Earlier, in June 2024, the same South Asian entity was targeted with ShadowPad, a malware widely shared among China-based threat actors. In this case, ShadowPad was obfuscated with a custom compiler, ScatterBrain, and linked to attacks against over 70 organizations. Many of these attacks exploited an n-day vulnerability in CheckPoint gateway devices. One affected organization was the hardware logistics provider previously used by SentinelOne, though the latter confirmed no direct compromise of its systems.
SentinelOne emphasized that defending against real-world attacks is part of daily life for security vendors. In recent months, the company has also thwarted ransomware operators attempting to test or purchase software, state-backed hackers, and even DPRK workers posing as IT job applicants.
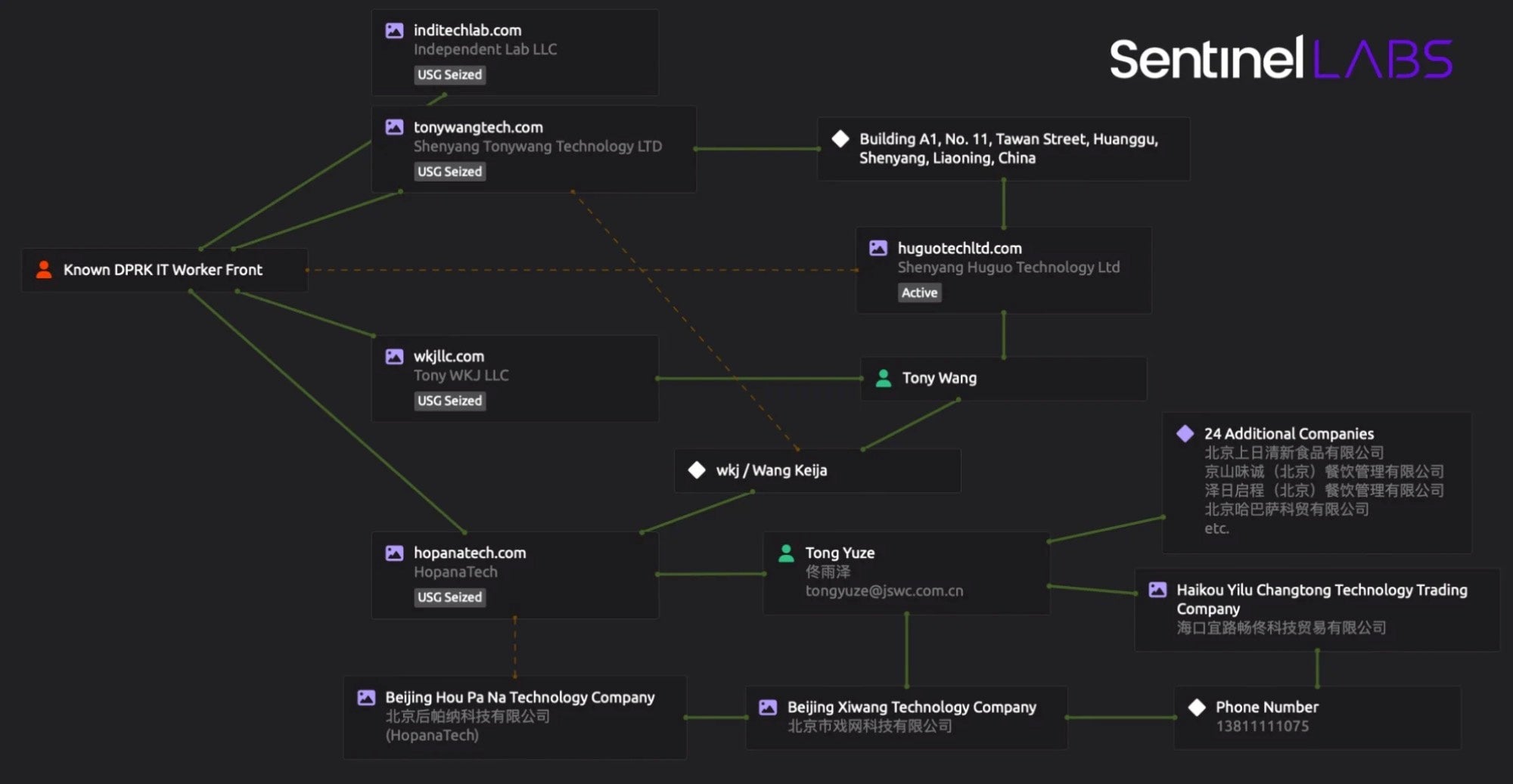
By spotlighting the reality that security vendors themselves face, organizations are encouraged to factor in supply chain exposure, asset tracking risks, and proactive intelligence sharing. SentinelLABS’ post offers critical lessons in the importance of resilience, readiness, and the evolving responsibilities of today’s security vendors.
The Ugly | Trojanized Word Processor Used in Targeted Espionage Attack Against Uyghur Activists
Senior members of the World Uyghur Congress (WUC) are currently being targeted in a cyberespionage campaign that uses a modified version of UyghurEdit++ to deliver Windows-based spyware.
Investigations began in March after several WUC members received state-sponsored phishing attempts. The phishing emails were designed to impersonate trusted contacts and included links to Google Drive that led to password-protected RAR archives containing a trojanized UyghurEdit++ installer. Once opened, the malware profiled the infected system and sent data to an external server (tengri.ooguy[.]com). It also featured the ability to download further malicious plugins and execute commands – likely only after confirming the victim was a high-value target.
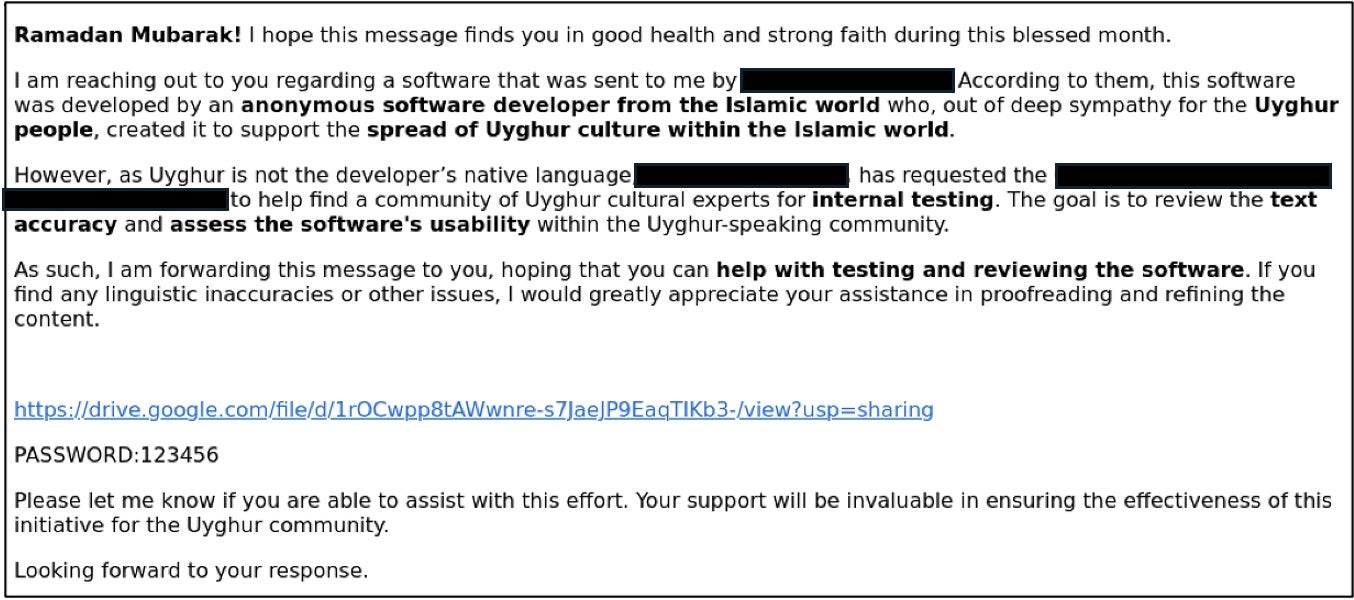
Cyber researchers report that while the malware itself is not technically sophisticated, its delivery is highly customized for the Uyghur diaspora. UyghurEdit++ is an open-source tool designed to support word processing and spell checking of the Uyghur language – a key cultural resource for a marginalized and heavily surveilled community. Given the software’s role in preserving Uyghur linguistic and cultural identity, its exploitation is especially high-risk as it blends into legitimate workflows, increasing the likelihood of successful compromise.
The incident is part of a broader pattern seen in digital transnational repression, particularly against the Uyghur community. While the exact perpetrators in this campaign are unknown, the attackers demonstrated deep familiarity with the community and employed tactics consistent with PRC state-sponsored activity. The findings from the campaign highlight ongoing attempts to extend state surveillance beyond borders via digital means, monitoring and suppressing pro-Uyghur activism abroad, disrupting communication about human rights conditions in Xinjiang, and curtailing global advocacy efforts.



