The Total Cost of Ownership (TCO) in cybersecurity encompasses all costs associated with implementing and maintaining security measures. This guide explores how to calculate TCO, including direct and indirect costs, and the importance of budgeting for security investments.
Learn about the impact of TCO on decision-making and resource allocation in cybersecurity. Understanding TCO is essential for effective cybersecurity planning and management.

What is Cybersecurity TCO (Total Cost of Ownership)?
The total cost of ownership (TCO) in cybersecurity refers to the cost associated with implementing, maintaining, and managing a cybersecurity infrastructure. This includes the direct costs of hardware, software, and services and the indirect costs related to business continuity, staff productivity, risk management, and organizational efficiency. Understanding TCO allows organizations to make informed decisions about their cybersecurity investments and allocate resources effectively.
Key Components of Cybersecurity TCO
Direct Costs
- Hardware and Software – The cost of acquiring and maintaining security hardware and software, such as firewalls, antivirus, and intrusion detection systems.
- Services – Expenses related to managed security services, consulting, and support.
- Staffing – Salaries and benefits of dedicated cybersecurity personnel.
Indirect Costs
- Business Continuity – Costs associated with business disruptions caused by cybersecurity events.
- Staff Productivity – The impact of security measures on employee efficiency and effectiveness.
- Risk Management – Expenses related to potential security breaches and their impact on the organization’s reputation, customer trust, and legal liabilities.
- Organizational Efficiency – Costs associated with deploying, managing, and integrating security solutions across the organization.
SentinelOne TCO Calculator
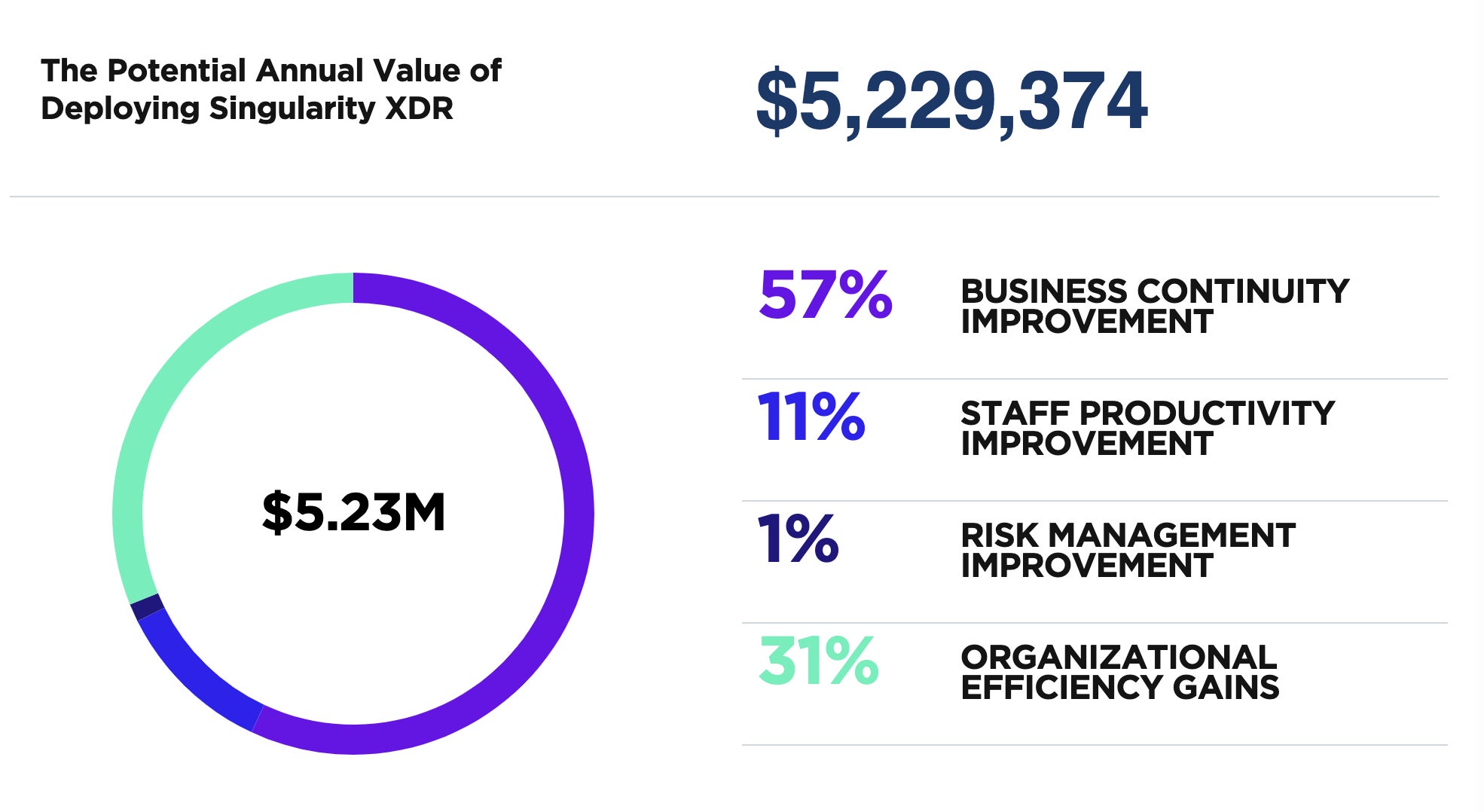
The SentinelOne TCO calculator is a valuable tool designed to help organizations estimate and optimize their cybersecurity TCO. By considering various factors, such as business continuity improvement, staff productivity improvement, risk management improvement, and organizational efficiency gains, the calculator comprehensively analyzes the potential cost savings and return on investment (ROI) of implementing SentinelOne’s Singularity XDR platform.
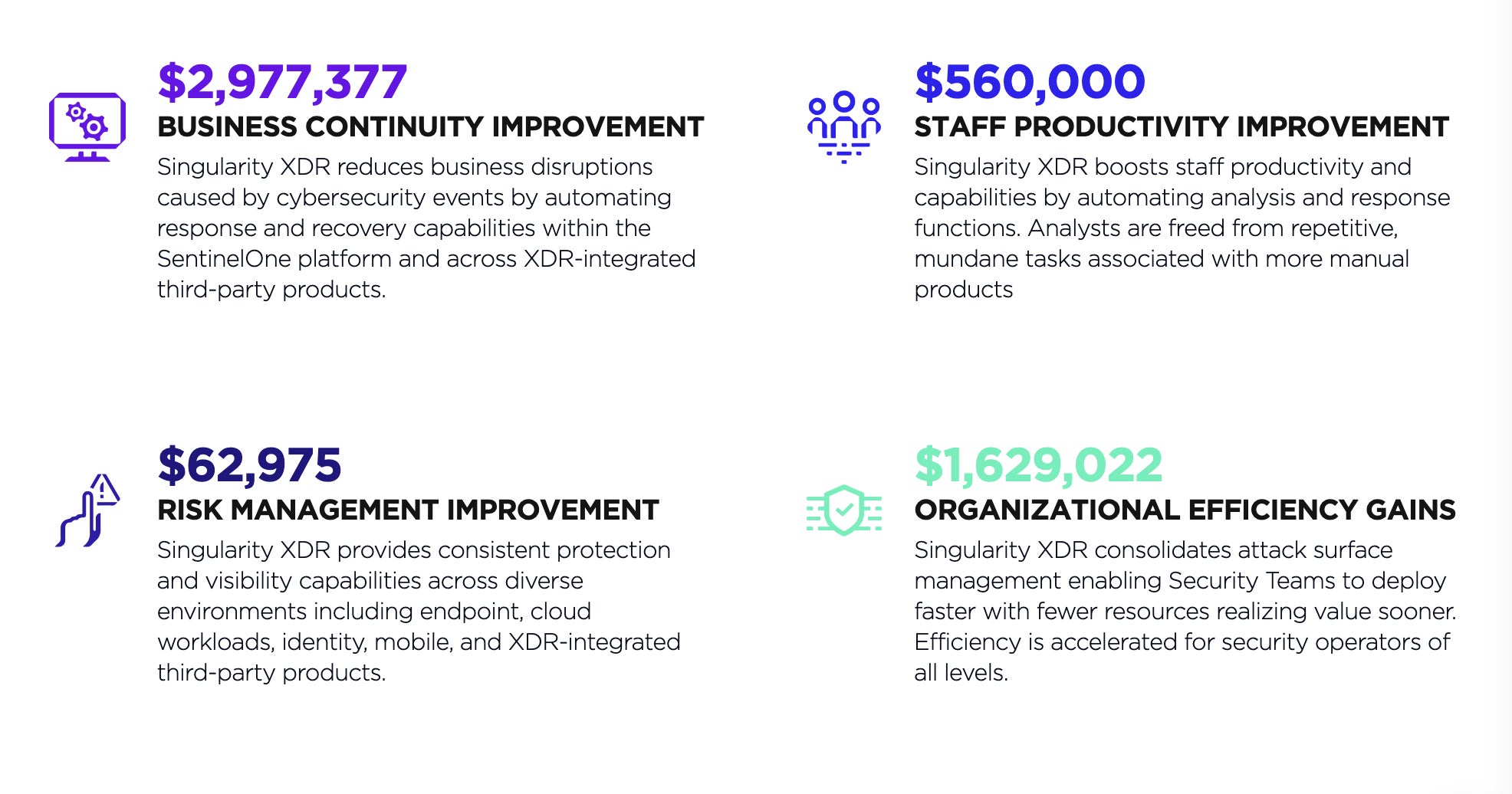
Business Continuity Improvement
Singularity XDR reduces business disruptions caused by cybersecurity events by automating response and recovery capabilities within the SentinelOne platform and across XDR-integrated third-party products. This ensures a faster and more efficient response to security incidents, minimizing downtime and associated costs.
Staff Productivity Improvement
Singularity XDR boosts staff productivity and capabilities by automating analysis and response functions. Analysts are freed from repetitive, mundane tasks associated with more manual products, allowing them to focus on higher-value tasks and make better use of their time and expertise.
Risk Management Improvement
Singularity XDR provides consistent protection and visibility capabilities across diverse environments, including endpoint, cloud workloads, identity, mobile, and XDR-integrated third-party products. This comprehensive coverage reduces the organization’s exposure to security risks and minimizes the potential impact of security breaches.
Organizational Efficiency Gains
Singularity XDR consolidates attack surface management, enabling security teams to deploy faster with fewer resources and realize value sooner. Efficiency is accelerated for security operators of all levels, improving overall cybersecurity effectiveness and reducing TCO.
Assessing Your Cybersecurity Needs
Before using the SentinelOne TCO calculator, it’s essential to have a clear understanding of your organization’s cybersecurity needs. This involves evaluating your current security infrastructure, identifying gaps or weaknesses, and determining the necessary improvements. Consider the following factors:
- Size and complexity of your organization’s network and IT infrastructure
- Types of devices, operating systems, and applications in use
- Regulatory requirements and industry-specific security standards
- The potential impact of a security breach on your organization’s reputation, finances, and operations
- Your organization’s risk tolerance and security budget
By thoroughly assessing your organization’s cybersecurity needs, you can better determine the appropriate security measures and investment levels required to protect your digital assets effectively.
Making the Most of SentinelOne’s TCO Calculator
SentinelOne’s TCO calculator offers a valuable resource for organizations looking to optimize their cybersecurity investments. To make the most of this tool:
- Gather accurate data about your organization’s current security infrastructure, costs, and challenges.
- Use the calculator to estimate potential cost savings and ROI based on your cybersecurity needs and goals.
- Analyze the results and consider how implementing the Singularity XDR platform could improve your organization’s security posture and TCO.
- Discuss the findings with your team and decision-makers to determine your organization’s best course of action.
- Continuously monitor and assess your cybersecurity investments and TCO to ensure ongoing optimization and alignment with your organization’s needs and goals.
By leveraging the SentinelOne TCO calculator and adopting a comprehensive cybersecurity strategy, organizations can effectively manage their security investments, minimize risks, and achieve a more secure and efficient digital environment.
Implementing a Comprehensive Cybersecurity Strategy
Once you’ve determined your organization’s cybersecurity needs and TCO, it’s essential to implement a comprehensive security strategy that addresses all aspects of risk management, staff productivity, and organizational efficiency. This strategy should include:
- Regular security assessments and audits to identify and address potential vulnerabilities
- Adoption of industry best practices and security standards
- Security awareness training for employees to minimize human errors and improve overall security posture
- Implementation of a multi-layered security approach, including endpoint protection, network security, and identity management
- Regular updates and patch management to keep software and systems up-to-date and secure
- Incident response planning and disaster recovery strategies to minimize the impact of security breaches and ensure business continuity
By implementing a comprehensive cybersecurity strategy that considers TCO, organizations can achieve a more secure environment while optimizing resources and maximizing return on investment.
AI-Powered Cybersecurity
Elevate your security posture with real-time detection, machine-speed response, and total visibility of your entire digital environment.
Get a DemoConclusion
Understanding and managing the total cost of ownership (TCO) in cybersecurity is essential for organizations to make informed decisions and allocate resources effectively. The SentinelOne TCO calculator offers a valuable tool for estimating and optimizing cybersecurity investments, ensuring that organizations can achieve the best possible return on investment while minimizing risks and costs.
By taking into account factors such as business continuity, staff productivity, risk management, and organizational efficiency, the SentinelOne TCO calculator provides a comprehensive and actionable analysis to guide decision-makers in selecting the most effective and cost-efficient cybersecurity solutions.
Tco Cyber Security FAQs
Total Cost of Ownership (TCO) in cybersecurity is the full sum you’ll pay over a solution’s life. It covers initial licensing or hardware fees, setup and integration labor, training, and ongoing support or subscriptions. You also include maintenance, upgrades, and eventual replacement costs.
TCO gives you a clear picture of what you’ll really spend, beyond the sticker price, so you can budget accurately.
TCO helps you compare offerings on equal footing. A tool with low upfront fees but high support costs or surprise usage charges can end up pricier than a higher-priced alternative with flat subscriptions and free updates. By evaluating TCO, you avoid budget overruns and select solutions that fit your long-term needs and cash flow, not just your immediate budget.
Core components include license or subscription fees, hardware or cloud compute expenses, and professional services for deployment. You’ll also factor in staff training, ongoing maintenance, and support contracts. Indirect costs—like time spent by IT teams on updates, incident investigations, or vendor management—round out the picture. Don’t forget disposal or replacement expenses when products reach end-of-life.
Direct costs involve: software licenses, hardware purchases, and consultancy fees. Indirect costs show up as time taken by employees for patching or incident response, productivity losses during downtimes, and training hours.
Hidden costs include unplanned emergency support, overtime pay when tools fail, or compliance fines if controls lapse. Together, these indirect and hidden costs can outstrip direct spending.
Start by listing all direct expenses: licenses, infrastructure, professional services. Estimate staff hours for deployment, training, maintenance, and incident handling, then multiply by loaded labor rates.
Add support contract costs and projected upgrade or replacement fees over the tool’s expected lifetime. Sum these to get your TCO. Reviewing actual invoices and time logs helps refine estimates over time.
You should revisit TCO annually or when major changes occur—like adding new services, renewing vendor contracts, or growing headcount. After a significant incident, recalculate to include unexpected response and recovery costs.
Regular reviews catch creeping expenses, validate budget forecasts, and ensure you’re not locked into solutions that become too costly to maintain.
By presenting TCO alongside risk reduction metrics—like fewer incidents or faster response times—CISOs can show cost avoided versus spend. For example, a prevention tool costing $100K a year may pay off by saving $400K in breach response and fines. Tangible comparisons between TCO and incident-related losses make a compelling case for future investments.
Automation cuts repetitive manual tasks—patching, alert triage, threat hunting—so you spend less on labor. Orchestrating routine workflows through scripts or SOAR platforms reduces response times and errors, lowering incident fallout and overtime costs.
Over time, you need fewer analysts for the same coverage, trimming headcount spend and letting your team focus on higher-value security improvements.


