Gartner predicted that by the end of 2020 about 25% of attacks on enterprises will involve IoT devices. But investment in IoT security will not measure to this risk level and is only expected to account for 10% security spending, as organizations will likely prefer usability over security. The characteristics of traditional IoT security solutions will also hamper the adoption, as these are usually cumbersome, expensive and don’t scale well.

IoT Devices Add to the Existing Number of Endpoints
If predictions by Gartner about future trends seems vague, instead look at the recent warning made by Microsoft about Russian Hackers breaching secured networks using simple IoT devices. And this is just the beginning. Today, there are 27 billion IoT devices. This number is expected to increase to 125 billion by just 2030.
Many of these IoT devices will find their way into enterprises and onto enterprise networks, in the form of smart assistances (Alexa), IP cameras, smart thermostats and other devices, all aimed at increasing convenience and productivity. However, these devices also significantly increase the organizations’ attack surface, adding to the burden of securing the most common IT devices – the endpoint.
The Challenges of Securing IoT devices in the Corporate Environment
IoT devices and endpoints are similar in some ways – they are connected to the enterprise network, they have an IP address, and some computing power (depending on the type and functionality). But unlike endpoints, IoT devices are usually not deployed in the same planned and organized manner, they are not built with security in mind, and they cannot be installed with proper endpoint protection solutions due to their limited nature (memory size, type of OS, computing power).
Often, these “smart” devices are “rogue” or “shadow IT” devices, which means they are brought from outside the organization without the IT department’s knowledge or supervision, and are connected to the network by Wi-Fi, Bluetooth or other communication protocol, which makes them “transparent” to network monitoring tools. So the first challenge is to discover all these devices. The second challenge is to enforce organizational security and privacy policies regarding these devices (which is impossible to do if you haven’t even detected them). Last but not least, the organization needs to monitor these devices, identify suspicious behavior and then respond if such activity is detected.
Existing Solutions fall short
Existing security products on the market try to tackle these challenges either by monitoring the traffic or by installing software agents on the devices themselves. The first approach usually requires adding physical appliances to the network and directing traffic there. Other products require capturing the traffic and uploading the logs to a server for processing. Both of these methods are difficult to implement and don’t scale well for organizations with multiple sites and network types. Deploying software agents on the devices themselves is even more impractical – it is possible only for very limited types of devices (security cameras), is not scalable, and does not cater for the “shadow” element in which users bring unsupervised devices into the network.
SentinelOne solution – “IoT discovery and enforcement”
Aiming to increase the security of enterprises from the threat of IoT devices, SentinelOne took a different path: leveraging existing endpoint security agents as sensors, effectively turning every protected endpoint into a network detection device capable of identifying and controlling every IoT and connected device on a network. Utilizing endpoint security agents obviate the need for installing additional equipment, hence facilitating deployment. Once in use, the Ranger IoT security module identifies all the connected devices and presents them to the security analysts. Every new device connected to the network is identified and added to the monitored devices’ list.
Since it’s not enough to simply know you have a device on your network, the system fingerprints the devices according to operating system and the device’s role. The devices are then presented according to categories (printers, mobile devices, Linux servers, and so on). Fingerprinting also allows alerting when a device is unmanaged or compromised as it will act differently than other devices of the same category.
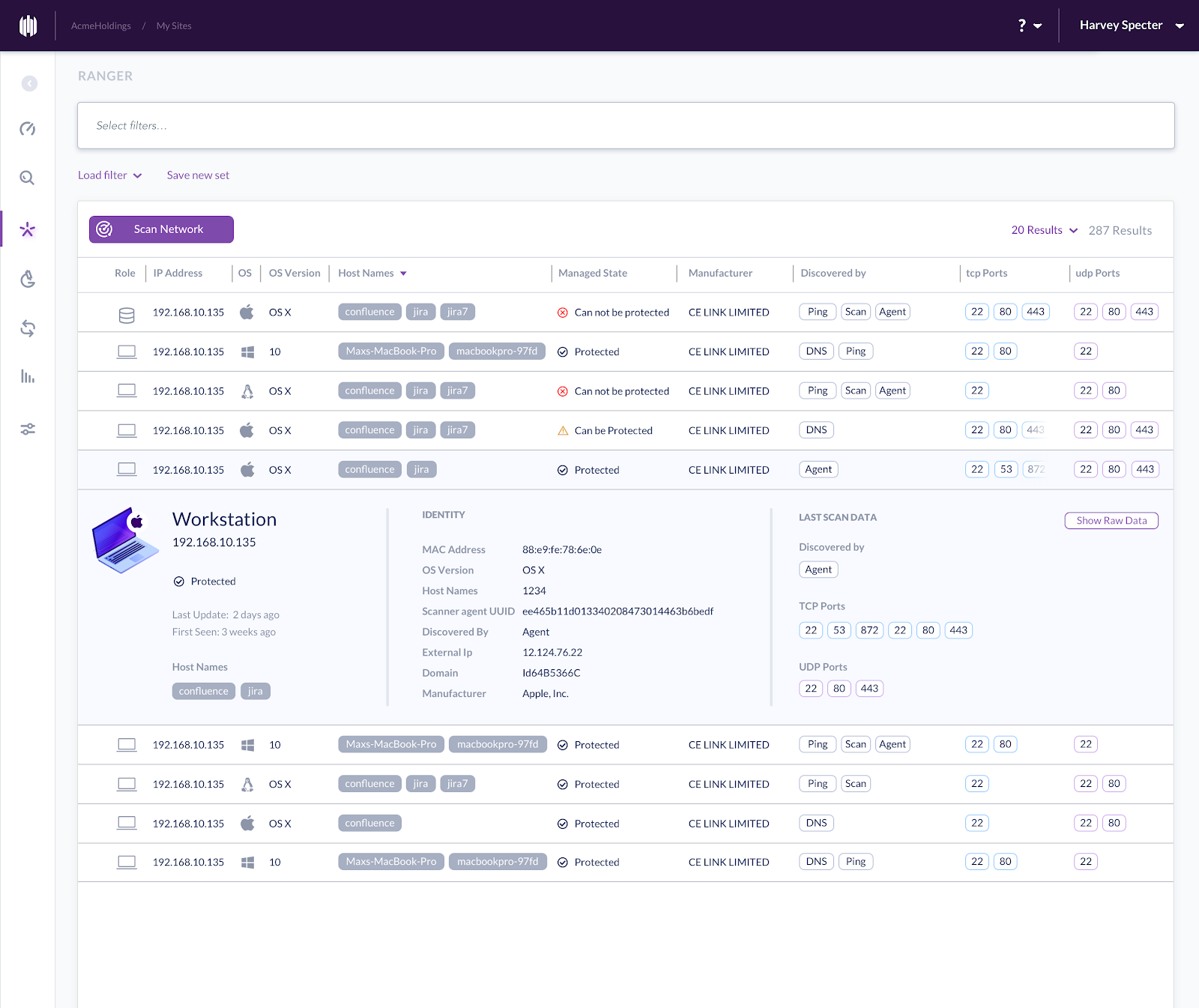
Providing security teams with complete visibility, categorization and alerting regarding rogue devices and vulnerabilities, all from the same management console and without having to install addition systems, is the best way to ensure that enterprises proactively prepare themselves to the imminent threat presented by IoT devices.


