Overview
Ransomware is a great source of income for many crime groups and we have seen many examples that are quite sophisticated and employ strong encryption techniques. Sophisticated ransomware typically signals a larger operation is behind the strain with a whole backend infrastructure that includes “support staff” that can provide decoding services once a ransom has been paid.
But not all ransomware is created equal and in many cases, ransomware can be created and deployed on the cheap – requiring very little investment from the attacker or attacker group. vCrpyt1 is one such example – it doesn’t include any stealth infection techniques, but rather uses social engineering in the form of a scary text file with instruction and a very basic XOR of the files content. Even in its simplicity, it can still prove to be very profitable.
As for backend support, vCrypt1 simply uses an email address that can be used to negotiate the “decryption” of the victims’ files. It is also possible that the perpetrators are installing vCrypt1 as a service from dark-net providers or they are renting botnets to send mass phishing emails. All of which is very inexpensive for the attacker.
As we can see from the examples below, given that the ransom message and accompanying files are in Russian, it is likely that this particular strain was developed to attack Russian targets, by Russian attack groups.
Method
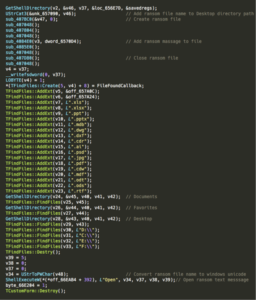
Once the sample is executed it starts scanning for the following directories:
- Documents
- Favorites
- Desktop
It then starting scanning the following drives:
- D:\
- C:\
- E:\
- F:\
The sample is looking for the following file types:
- doc
- docx
- xls
- xlsx
- ppt
- pptx
- mdb
- dwg
- dxf
- cdr
- ai
- psd
- jpg
- cdw
- mdf
- odt
- ods
- rtf
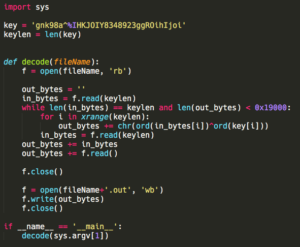
Each matching file is opened and read in 32-byte blocks and xored against a 32-byte-string “gnk98a^%IHKJOIY8348923ggROihIjoi”.
Only the first 100K bytes of the file are XORed, which is enough to render the file useless and makes the execution time of the sample shorter. The file’s name is then changed to include a “vCrypt1” extension.
After searching the local drives the sample writes the ransom text file to the desktop and opens it using the default text editing program. The sample ends it execution by closing it’s form (the sample is written in Delphi and uses a timer event for the main form to execute the search, which is invisible to the user).
Conclusion
SentinelOne Endpoint Protection Platform version 1.8.4 and above can successfully block vCrypt1.
While vCrypt is very simple we are sure that it’s creators are able to generate revenues from people that need their files and don’t wish to risk them by looking for solutions to decode the files.
Ransom message
Если Вы читаете это сообщение, значит Ваш компьютер был атакован опаснейшим вирусом-шифровальщиком vCrypt1!
Вся ваша информация (документы, базы данных, бэкапы и другие файлы) на этом компьютере была зашифрована с помощью
криптоалгоритма RSA2048. Восстановить файлы можно только зная уникальный для вашего ПК пароль и имея соответствующий дешифратор.
Подобрать ключ невозможно. Смена операционной системы ничего не изменит. Ни один системный администратор не решит эту проблему, не зная ключа.
Ни в коем случае не изменяйте файлы, иначе расшифровать их будет невозможно даже нам!
Ваши действия должны быть следующими:
- Сделайте резервную копию всех ваших файлов.
- Напишите нам письмо на адрес [email protected], чтобы узнать как получить ключ и дешифратор.
К письму можете приложить любой файл с известным Вам содержимым, мы вышлем в ответ расшированную копию.
Это докажет, что мы действительно обладаем возможностью расшифровать Ваши файлы.
Среднее время ответа нашего специалиста 3-24 часов.
Письма с угрозами будут угрожать только Вам и Вашим файлам!
НЕ ЗАБУДЬТЕ! Только МЫ можем расшифровать Ваши файлы!
e-mail: [email protected]
Translated
If you are reading this message, then your computer was attacked by the most dangerous virus-encryptor vCrypt1!
All your information (documents, databases, backups and other files) on this computer has been encrypted using
Cryptoalgorithm RSA2048. You can recover files only knowing a unique password for your PC and having the appropriate decoder.
You can not find the key. Changing the operating system will not change anything. No system administrator will solve this problem without knowing the key.
Do not change the files at all, otherwise it will be impossible to decipher them even to us!
Your actions should be as follows:
- Make a backup of all your files.
- Write us a letter to [email protected] to find out how to get the key and decoder.
To the letter you can attach any file with the content known to you, we will send an expanded copy in response.
This will prove that we really have the ability to decrypt your files.
The average response time of our specialist is 3-24 hours.
Threatened letters will threaten only you and your files!
DO NOT FORGET! Only we can decrypt your files!
E-mail: [email protected]
Appendix A: Pseudocode of the file search function:
Appendix B: File decode python script